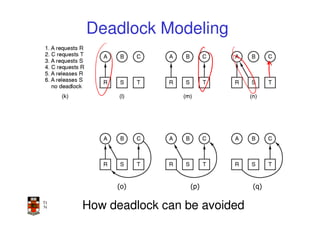
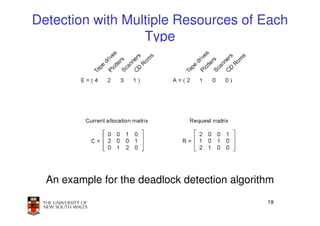
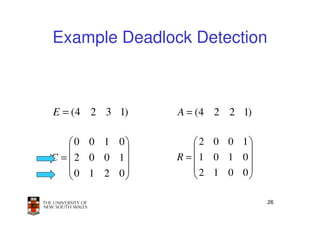
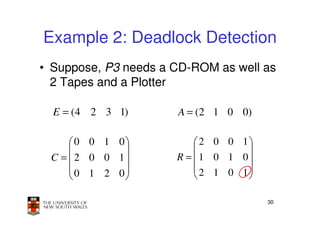
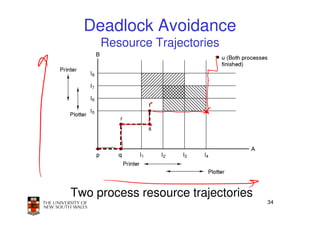
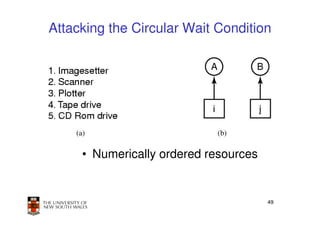
This document discusses deadlocks in operating systems. It begins by defining deadlocks and the four conditions required for deadlocks to occur. It then describes several approaches to dealing with deadlocks, including detection and recovery, deadlock avoidance using the banker's algorithm, and prevention by negating one of the four conditions. The key learning outcomes are understanding what causes deadlocks and different strategies systems can use to mitigate or avoid deadlocks.