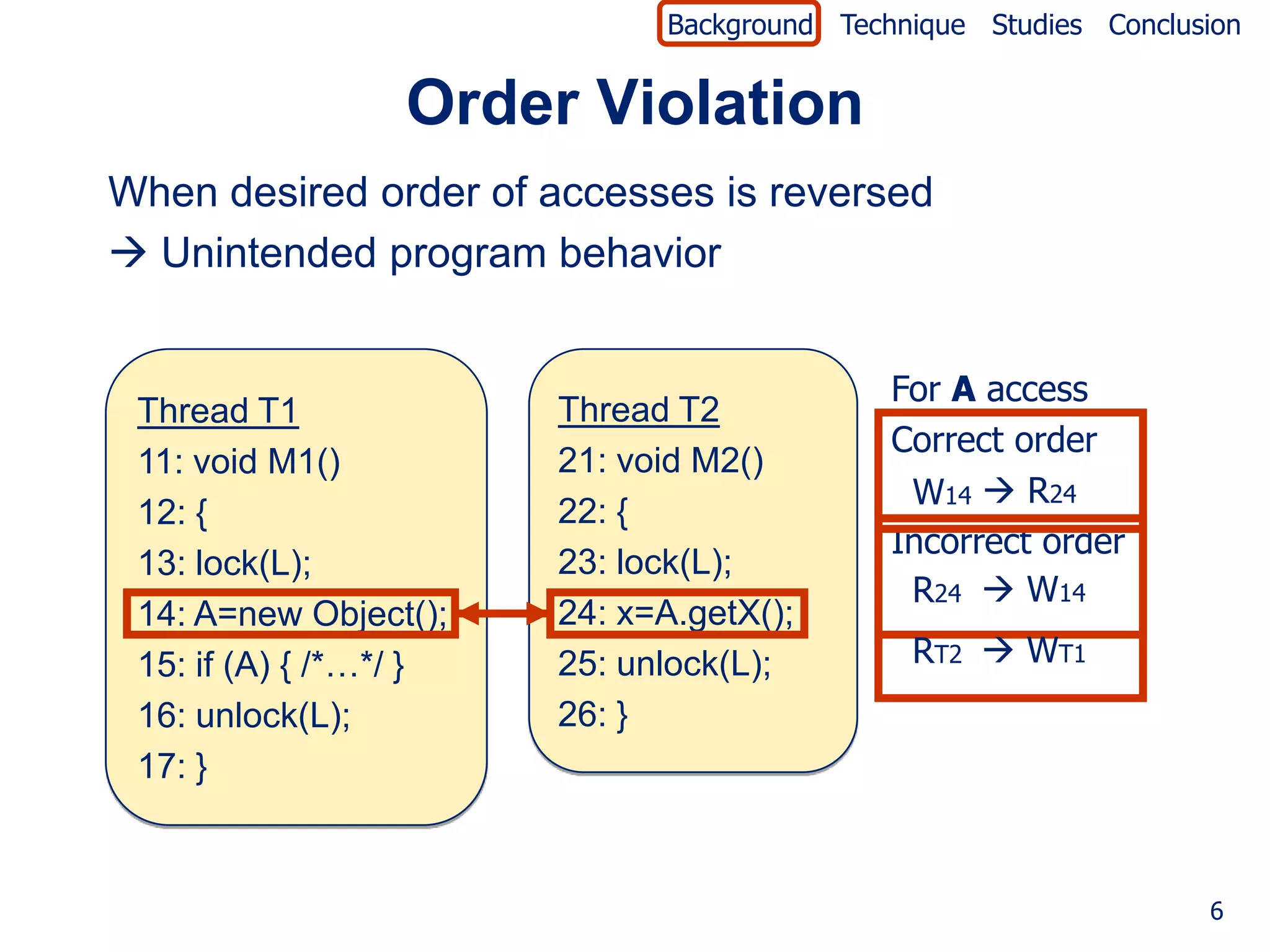
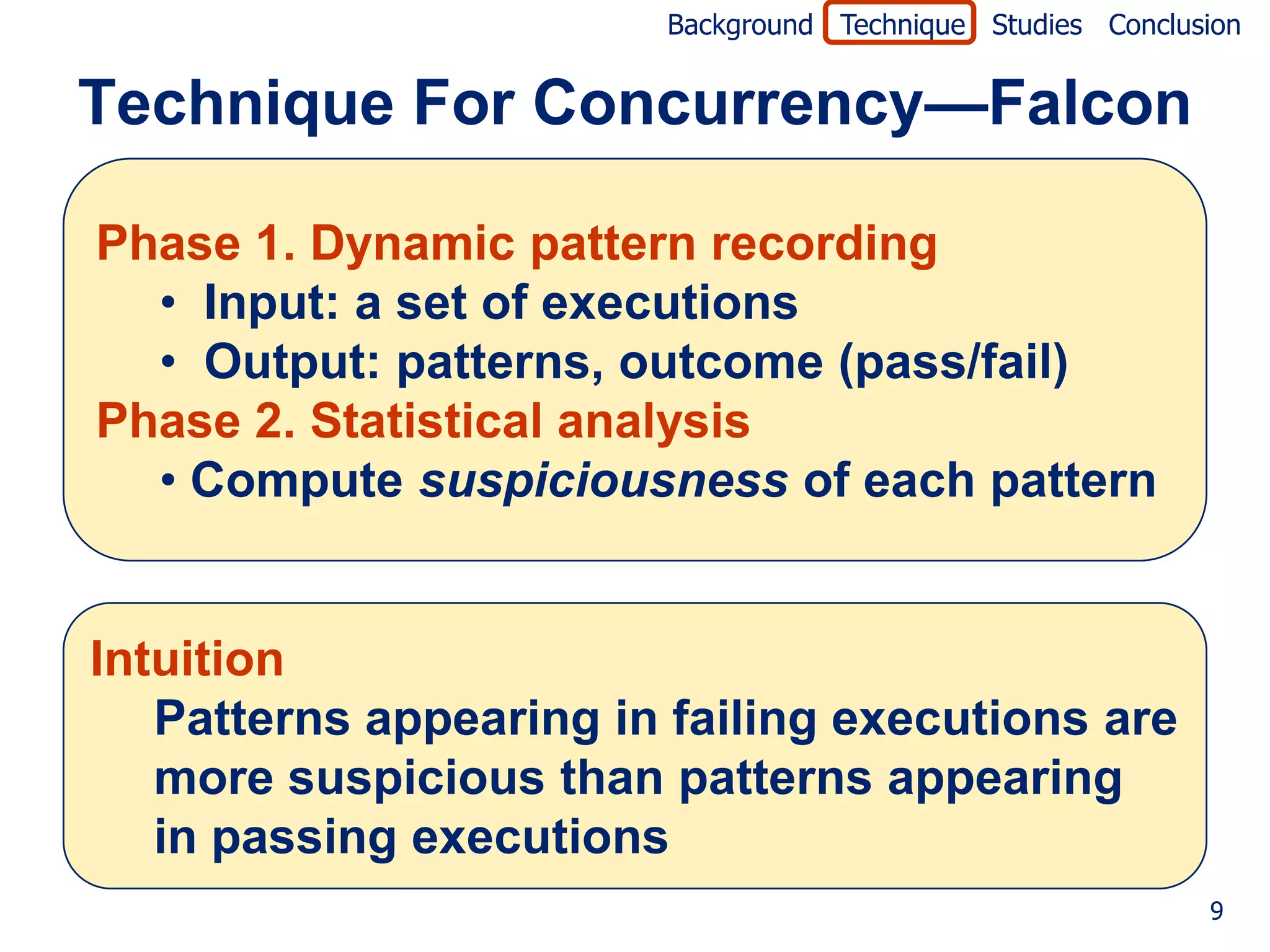
The document describes a technique called Falcon for fault localization in concurrent programs. Falcon uses patterns of variable accesses and thread interactions to identify suspicious patterns. It records patterns dynamically from multiple program executions. It then computes the suspiciousness of each pattern based on whether the pattern appears in passing or failing runs. The most suspicious patterns that appear frequently in failing runs but not passing runs help locate likely faults. The technique is evaluated on concurrency violations like order violations and atomicity violations.

![Background Technique Studies Conclusion
Motivation
• Godefroid, Nagappan Developers
[MSR-TR08]
found that
Handle
concurrency
issues
• Concurrency bugs are difficult to find
• Non-deterministic behavior
• Large thread interleaving space
2](https://image.slidesharecdn.com/icse2010-v4-120406144228-phpapp01/75/Falcon-Fault-Localization-in-Concurrent-Programs-2-2048.jpg)
![Background Technique Studies Conclusion
Existing Techniques
• Bug finding for concurrency bugs
• Static/dynamic data race detection
(e.g., [Ronesse99, Savage97, O’Callanhan03])
1. Techniques target only one type of
concurrency bug
• Static/dynamic atomicity violation detection
2. Techniques report benign (harmless)
(e.g., [Flanagan03, Wang06, Flanagan08])
results along with harmful results
• Dynamic pattern analysis
(e.g., [Lu06, Hammer08])
• Fault localization
• For sequential programs
(e.g., [Jones02, Liblit03, been applied to
Techniques have not Liu05, Baah08])
concurrent programs
3](https://image.slidesharecdn.com/icse2010-v4-120406144228-phpapp01/75/Falcon-Fault-Localization-in-Concurrent-Programs-3-2048.jpg)

![Background Technique Studies Conclusion
Concurrency Violations
Lu et al.’s [ASPLOS08] found that
Others: 3%
Order and
Atomicity Deadlock: 30%
violations:
67%
Both occur due to undesirable
undesirable
memory-access sequences
memory-access sequences
5](https://image.slidesharecdn.com/icse2010-v4-120406144228-phpapp01/75/Falcon-Fault-Localization-in-Concurrent-Programs-5-2048.jpg)
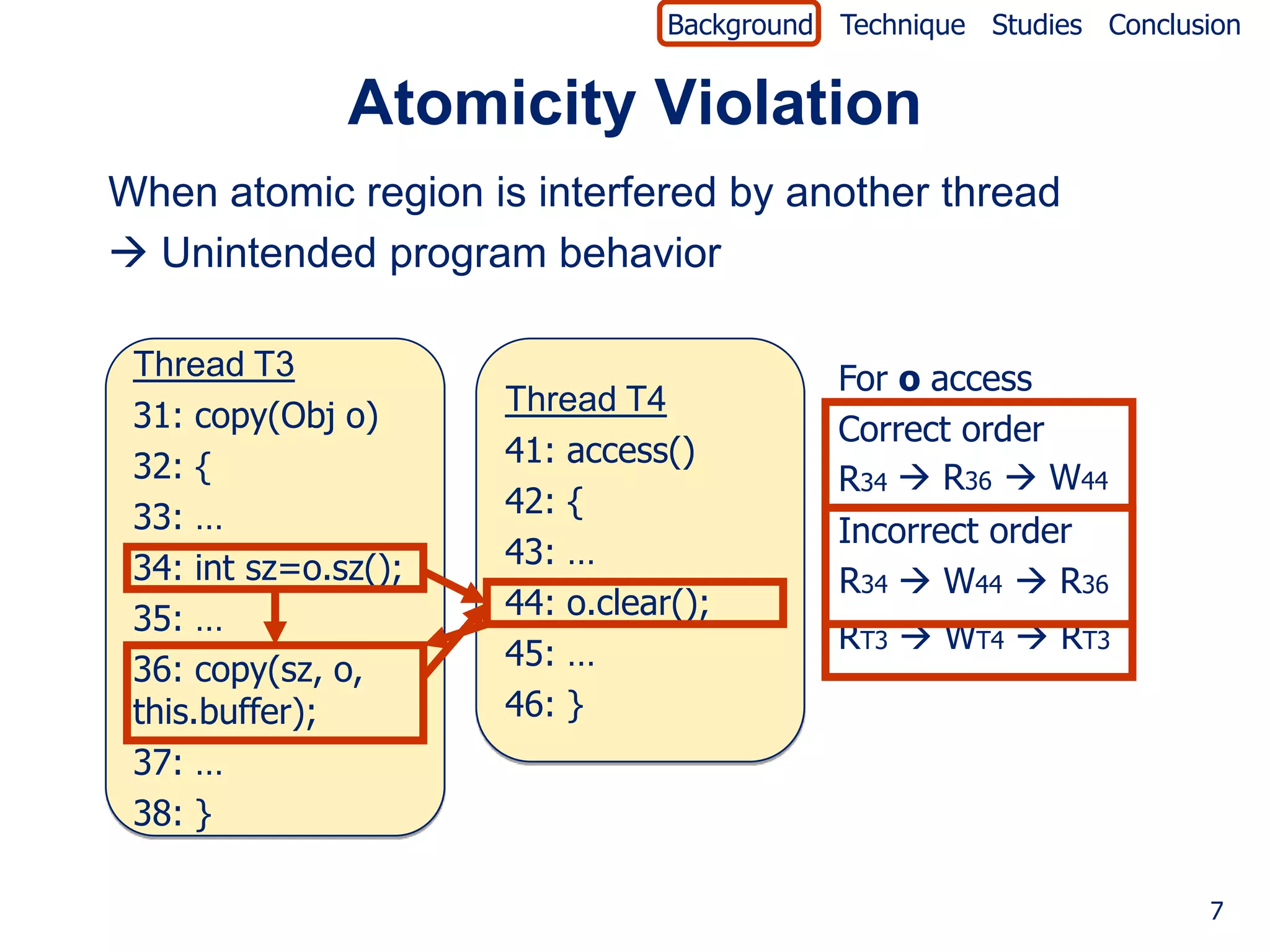
![Background Technique Studies Conclusion
Patterns for Concurrency Violations
Patterns Patterns for atomicity violation
for order violation [PPoPP06, ASPLOS06]
1 RT1 * WT2 1 RT1 * WT2 * RT1
2 WT1 * RT2 2 WT1 * WT2 * RT1
3 WT1 * WT2 3 WT1 * RT2 * WT1
4 RT1 * WT2 * WT1
5 WT1 * WT2 * WT1
Note
• Concurrency violations represented as patterns
• Patterns not always concurrency violations
8](https://image.slidesharecdn.com/icse2010-v4-120406144228-phpapp01/75/Falcon-Fault-Localization-in-Concurrent-Programs-8-2048.jpg)
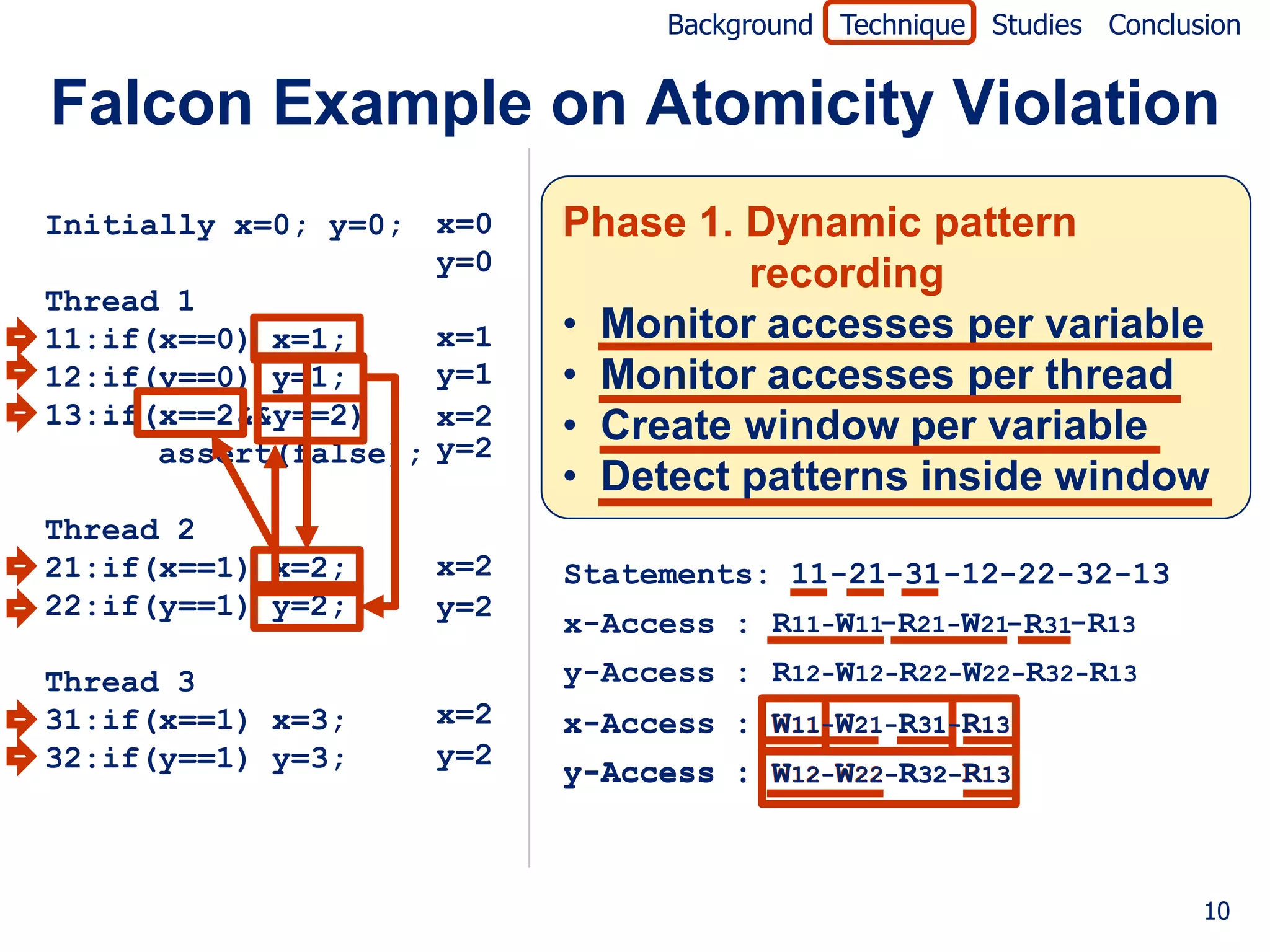
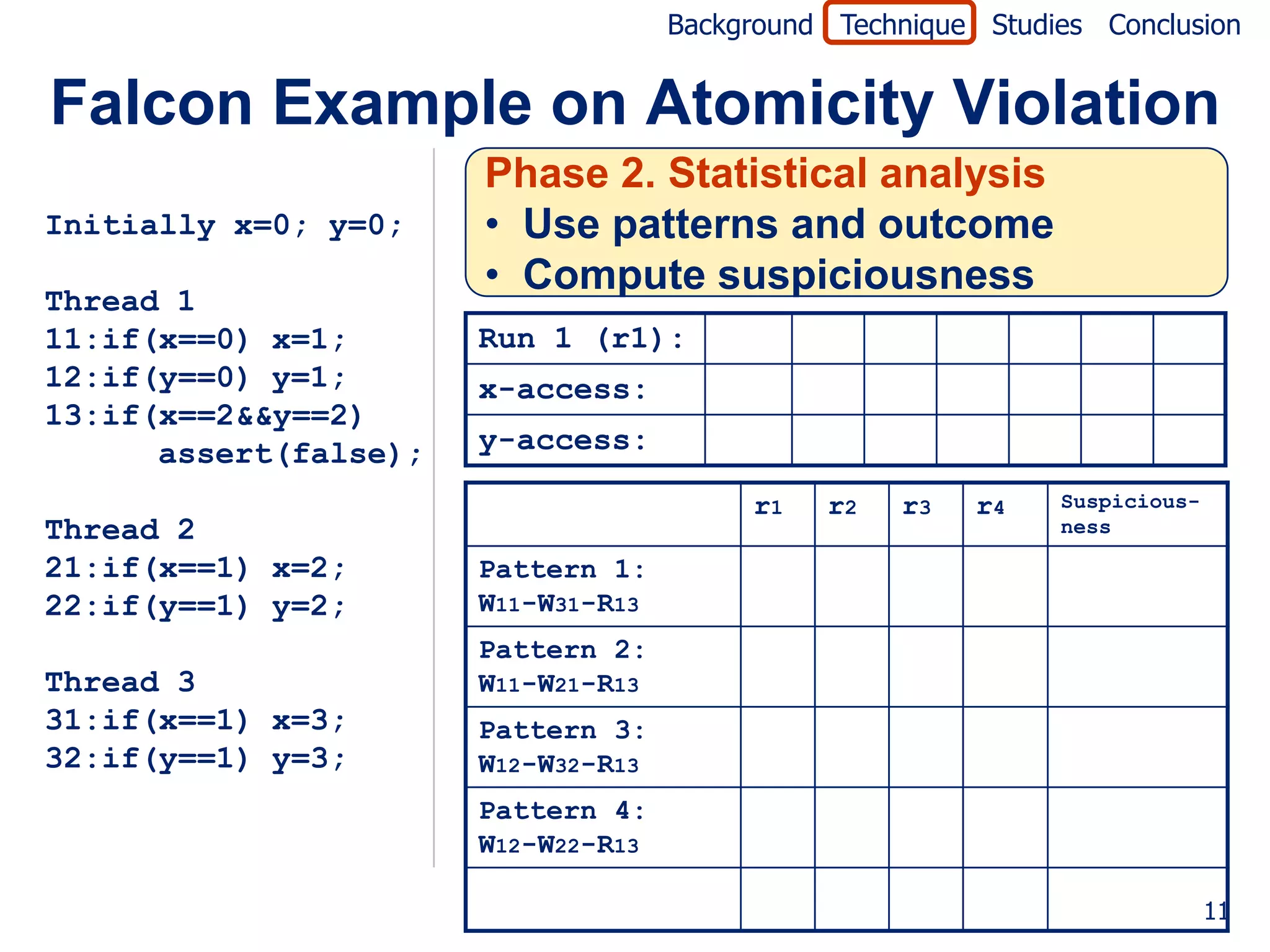
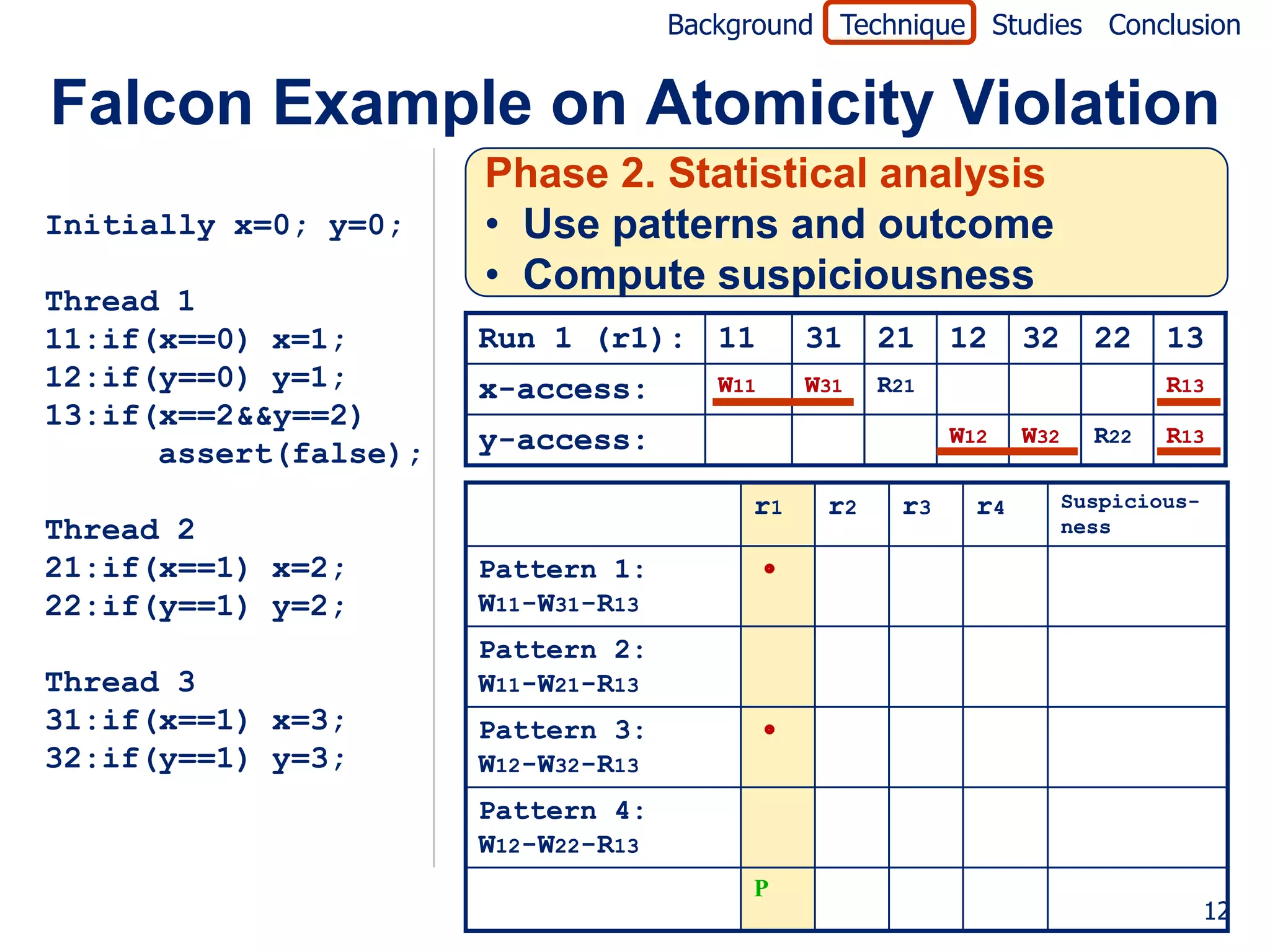
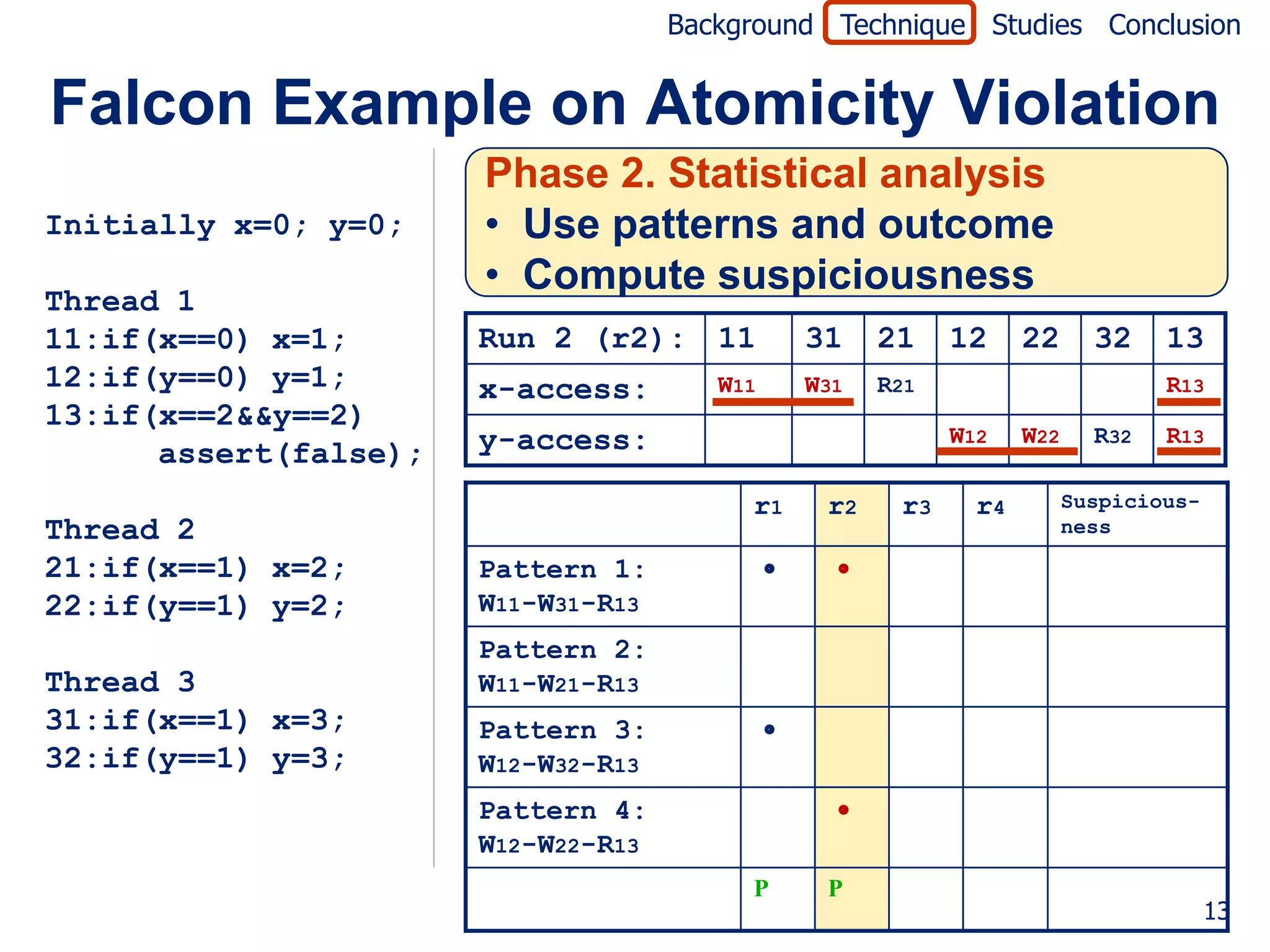
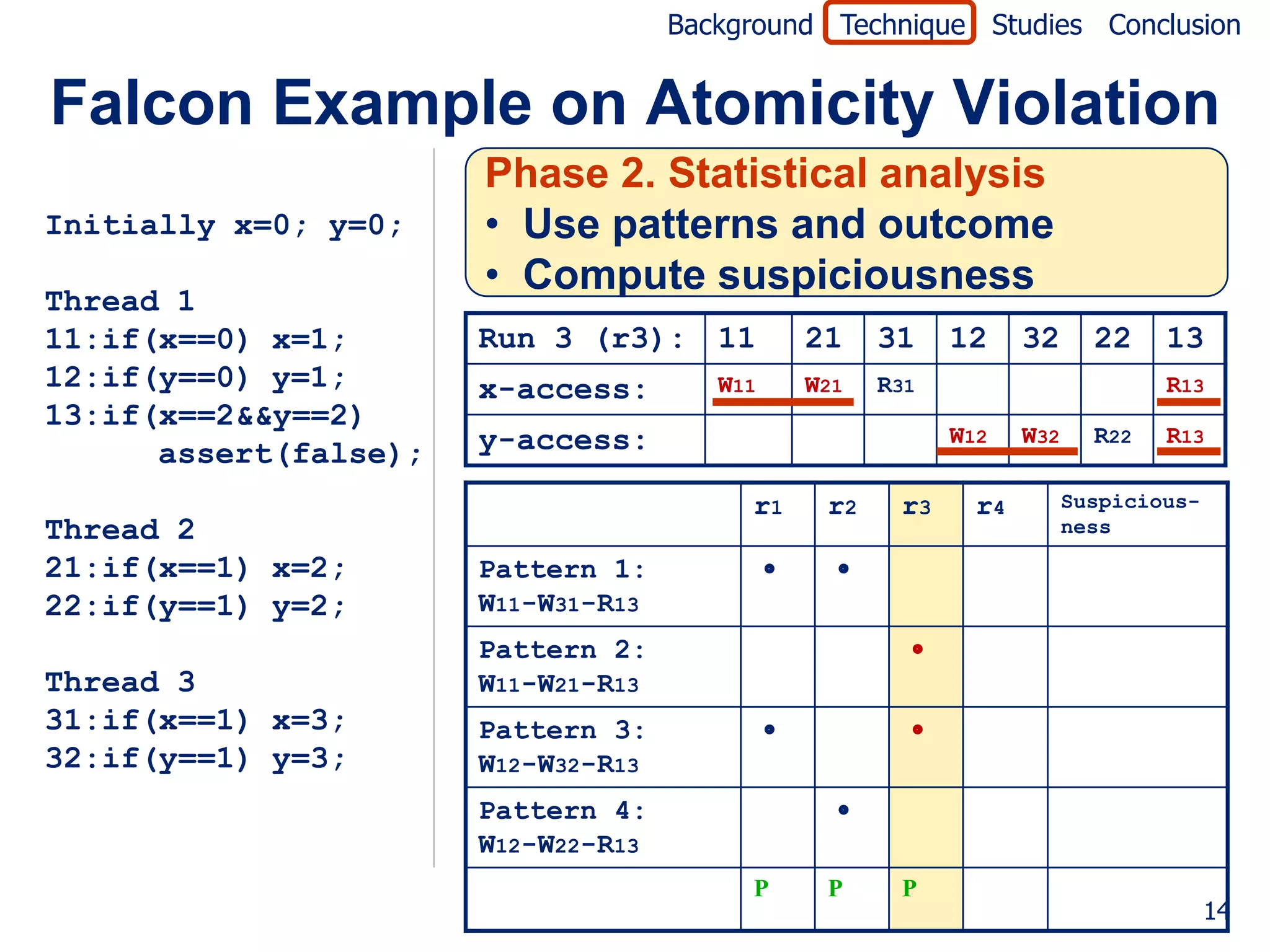
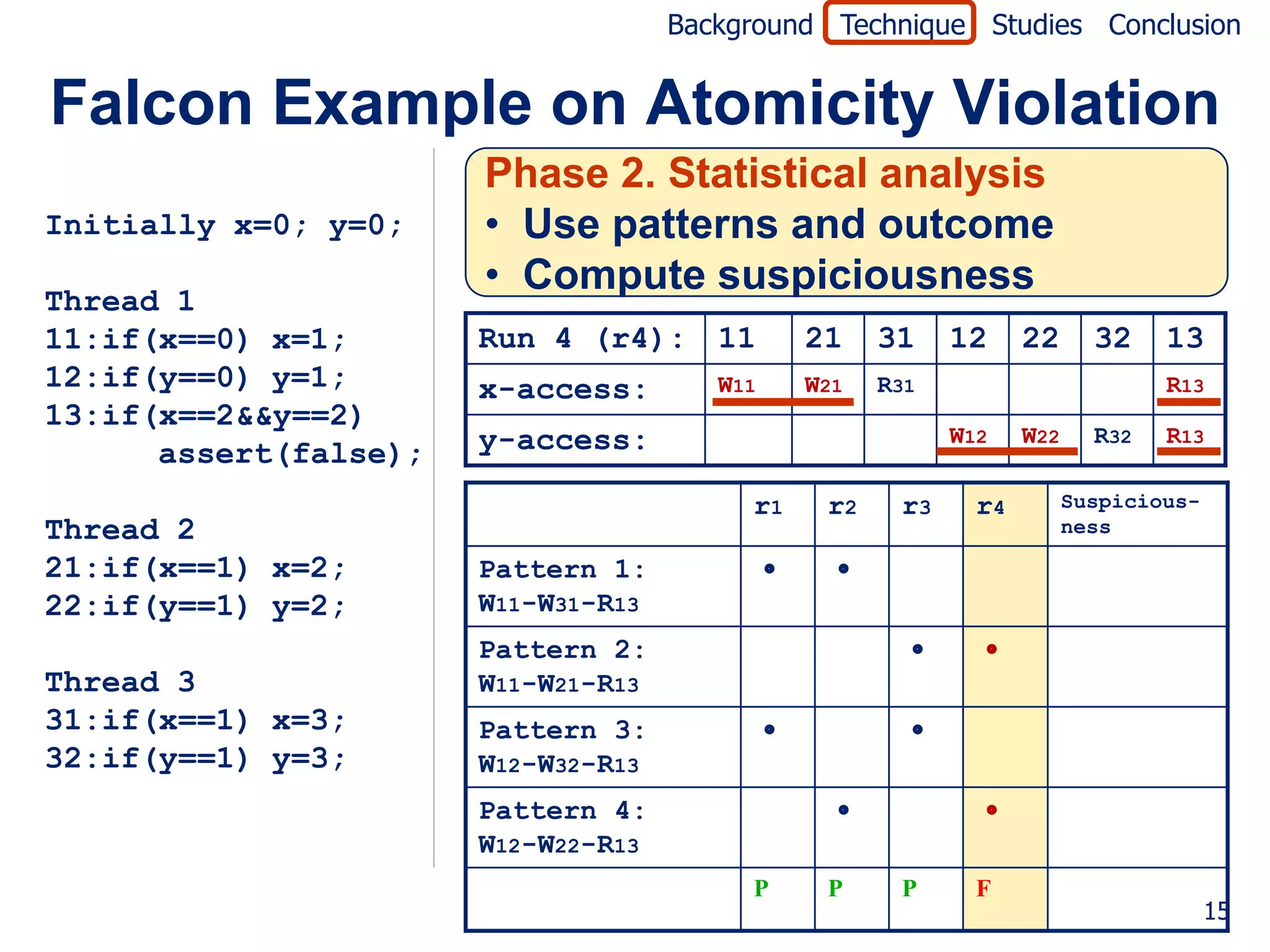
![Background Technique Studies Conclusion
Falcon Example on Atomicity Violation
Initially x=0; y=0; Jaccard formula [Abreu07]
failed (P)
Thread 1 suspiciousness(P) =
11:if(x==0) x=1; totalfailed + passed(P)
12:if(y==0) y=1;
13:if(x==2&&y==2) r1 r2 r3 r4 Suspicious-
ness
assert(false);
Pattern 1: 0.0
W11-W31-R13
Thread 2
Pattern 2: 0.5
21:if(x==1) x=2;
W11-W21-R13
22:if(y==1) y=2;
Pattern 3: 0.0
Thread 3 W12-W32-R13
31:if(x==1) x=3; Pattern 4: 0.5
32:if(y==1) y=3; W12-W22-R13
P P P F
16](https://image.slidesharecdn.com/icse2010-v4-120406144228-phpapp01/75/Falcon-Fault-Localization-in-Concurrent-Programs-16-2048.jpg)
![Background Technique Studies Conclusion
Empirical Studies
• Studies
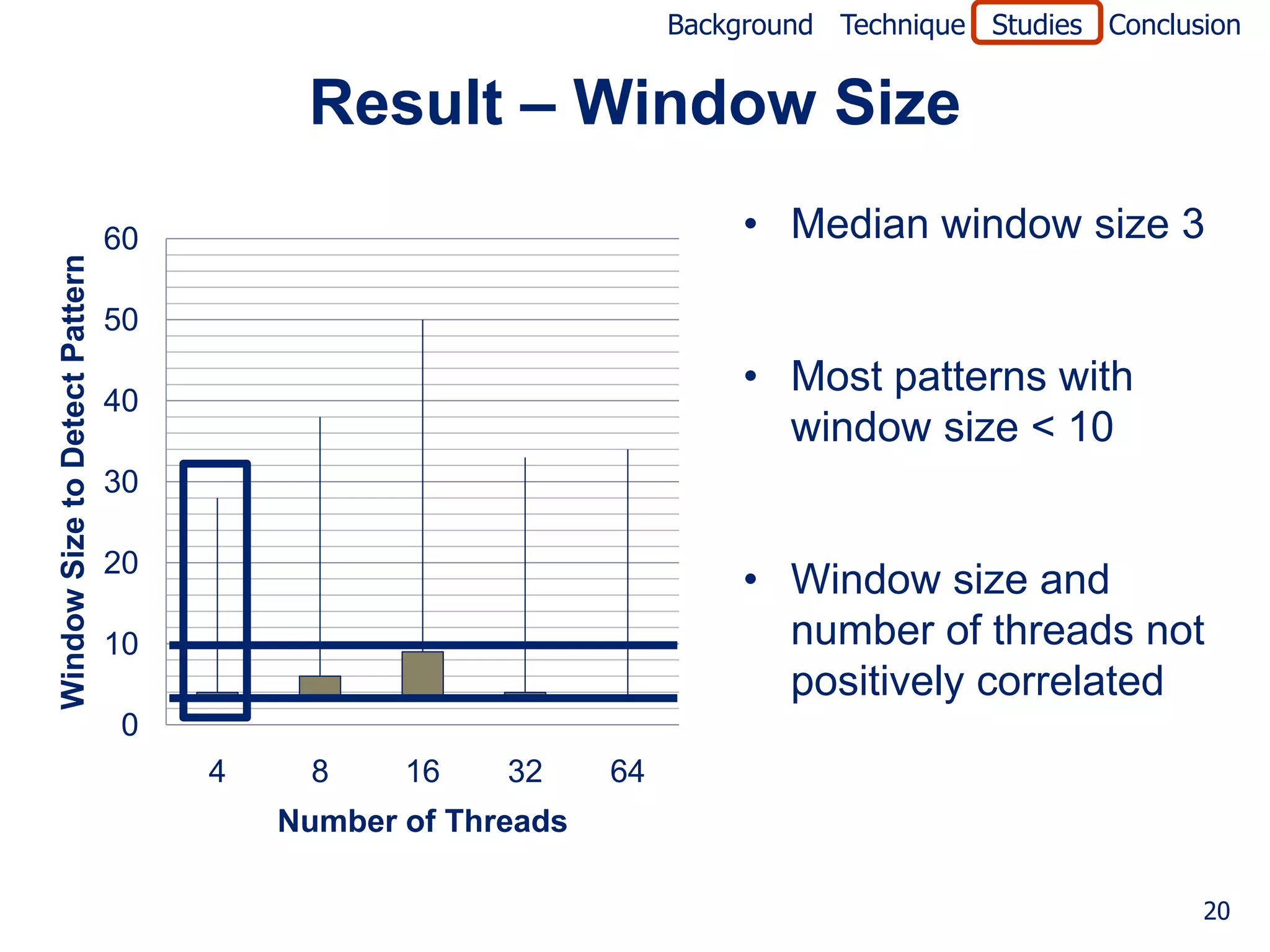
1. Determine window size needed and
its relationship to number of threads
2. Evaluate technique’s effectiveness
3. Compare technique with Cooperative Crug
Isolation (CCI) [Thakur et al.,WODA09]
4. Evaluate technique’s efficiency (see paper)
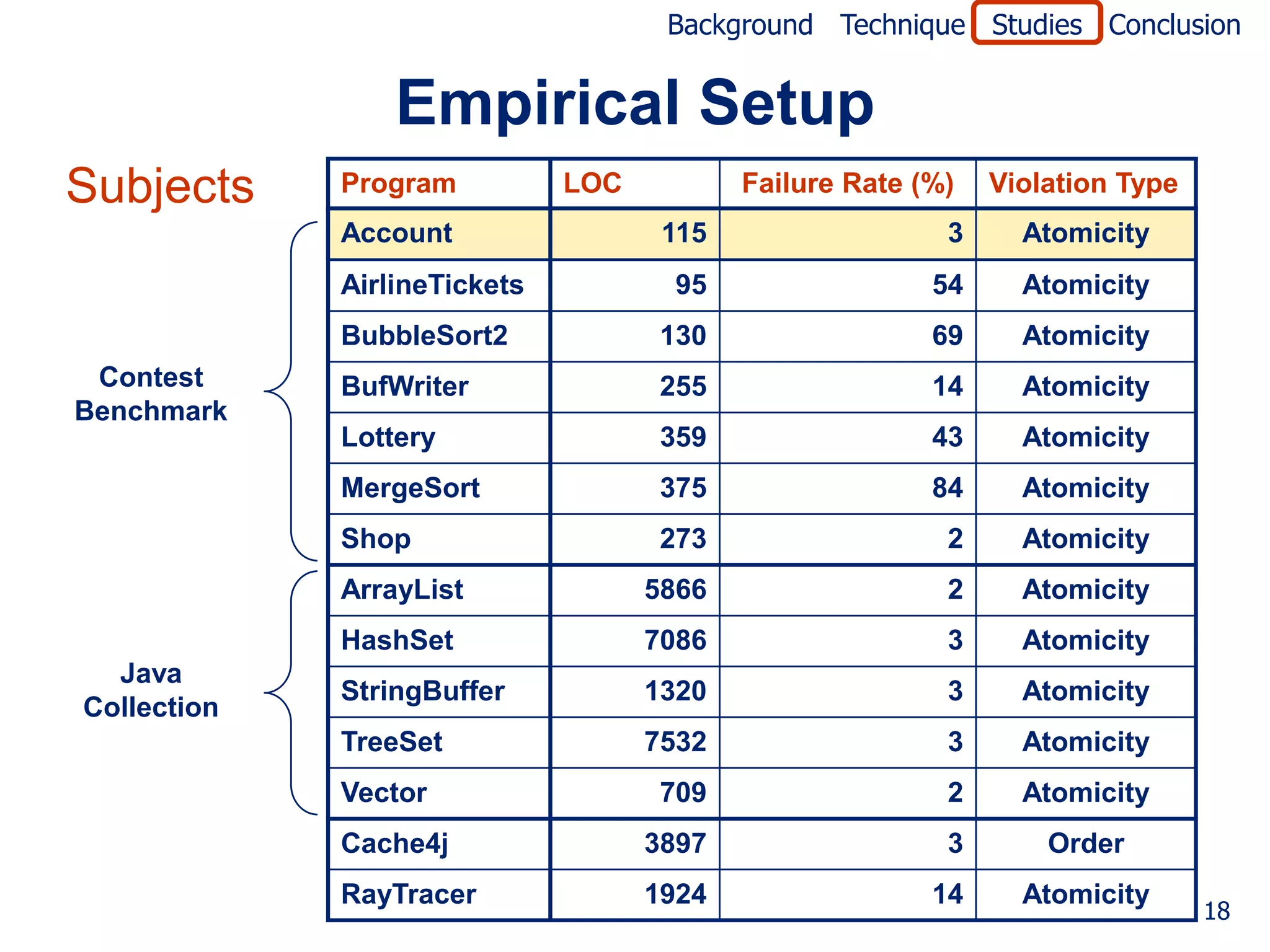
• Empirical setup
• Implemented in Java
• Evaluated on a set of subjects
17](https://image.slidesharecdn.com/icse2010-v4-120406144228-phpapp01/75/Falcon-Fault-Localization-in-Concurrent-Programs-17-2048.jpg)

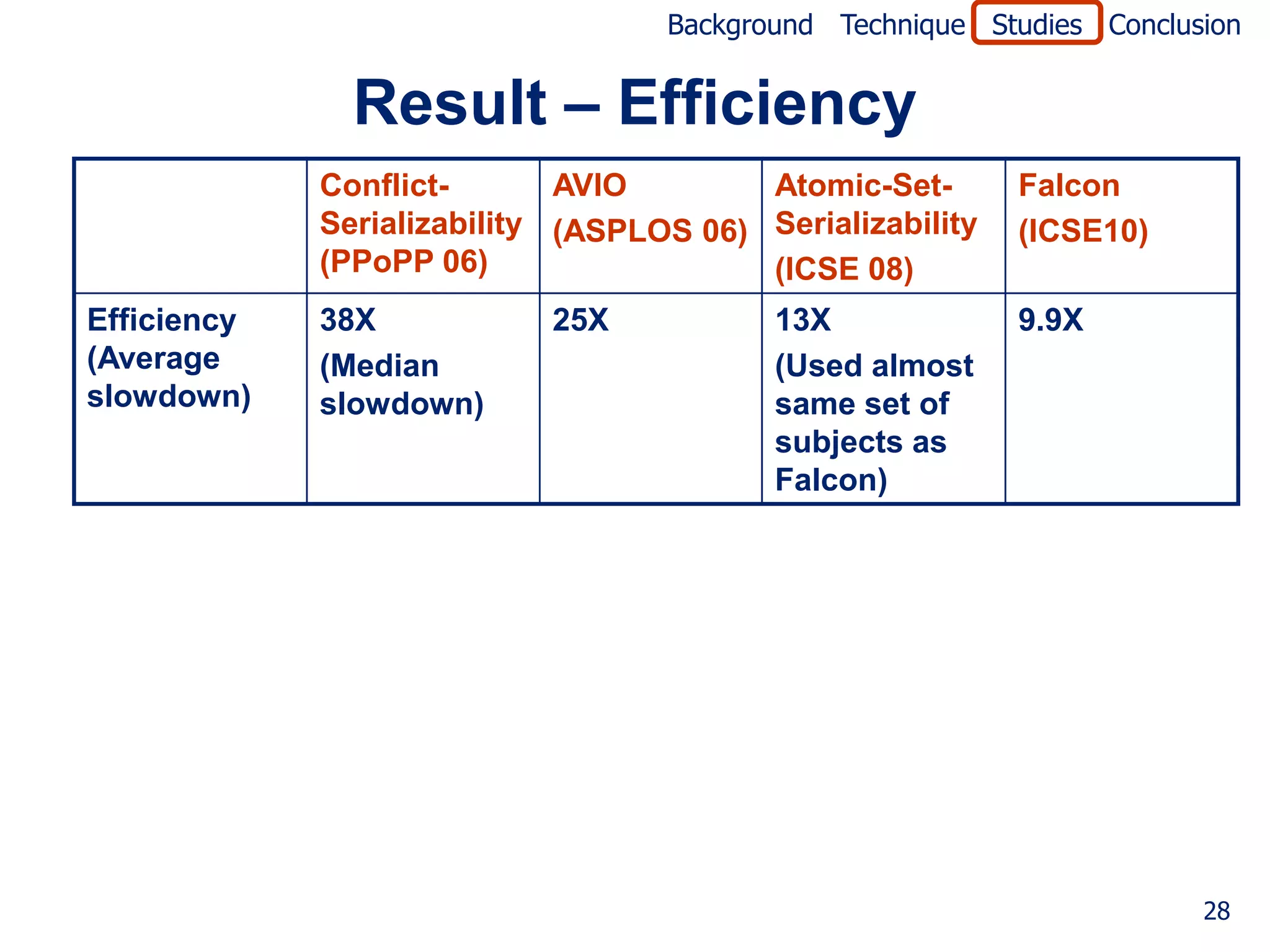
![Background Technique Studies Conclusion
Empirical Study 2 – Effectiveness
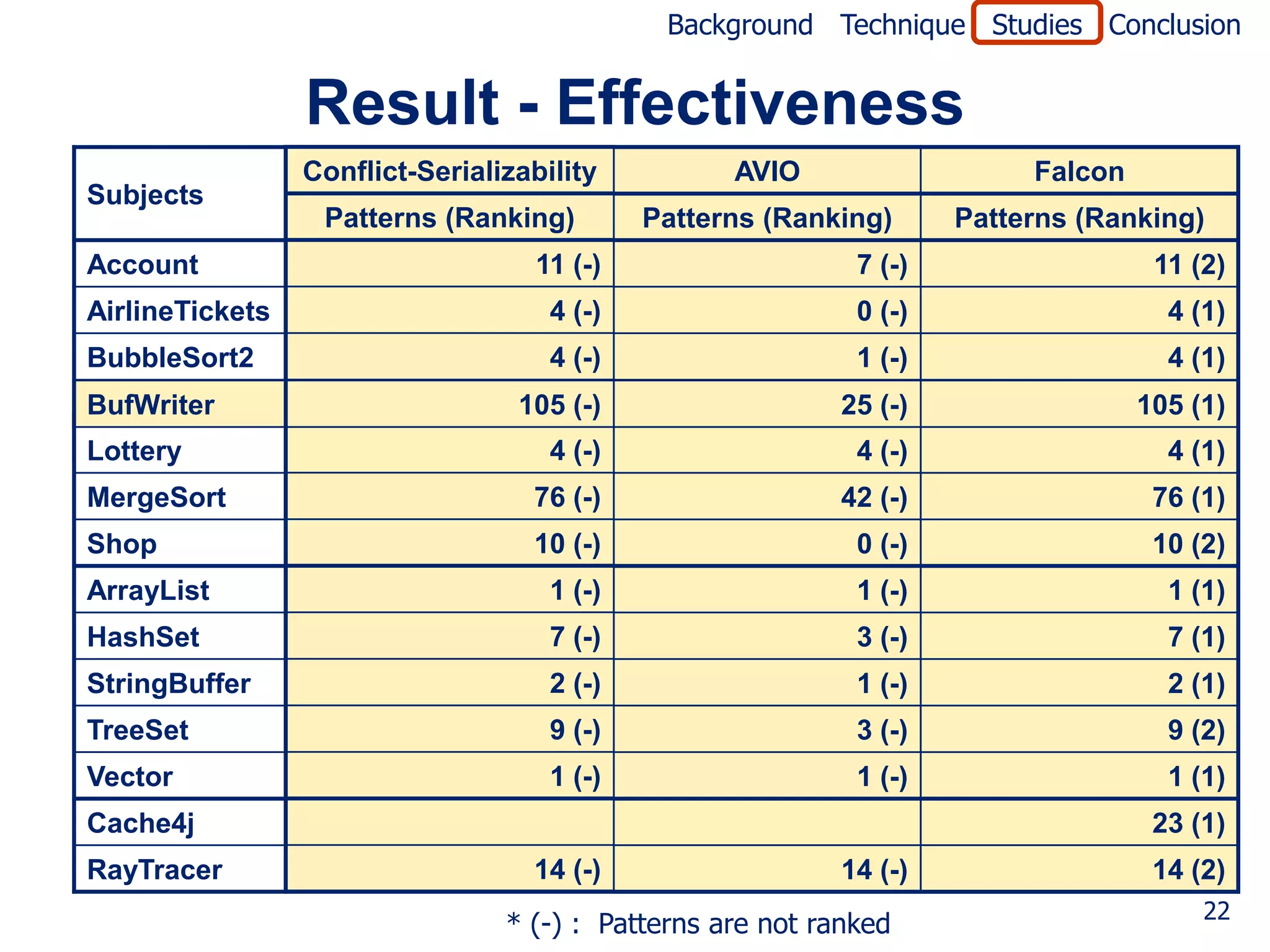
Goal
• To measure effectiveness of suspiciousness ranking
Techniques compared
• Conflict Serializability (e..g, [Wang and Stoller, PPoPP06])
• AVIO [Lu et al., ASPLOS06]
Method
• For test case with 100 runs and window size 5
• Computed suspiciousness of each pattern
• Computed fault-localization expense (number of
patterns that must be examined to find fault)
21](https://image.slidesharecdn.com/icse2010-v4-120406144228-phpapp01/75/Falcon-Fault-Localization-in-Concurrent-Programs-21-2048.jpg)
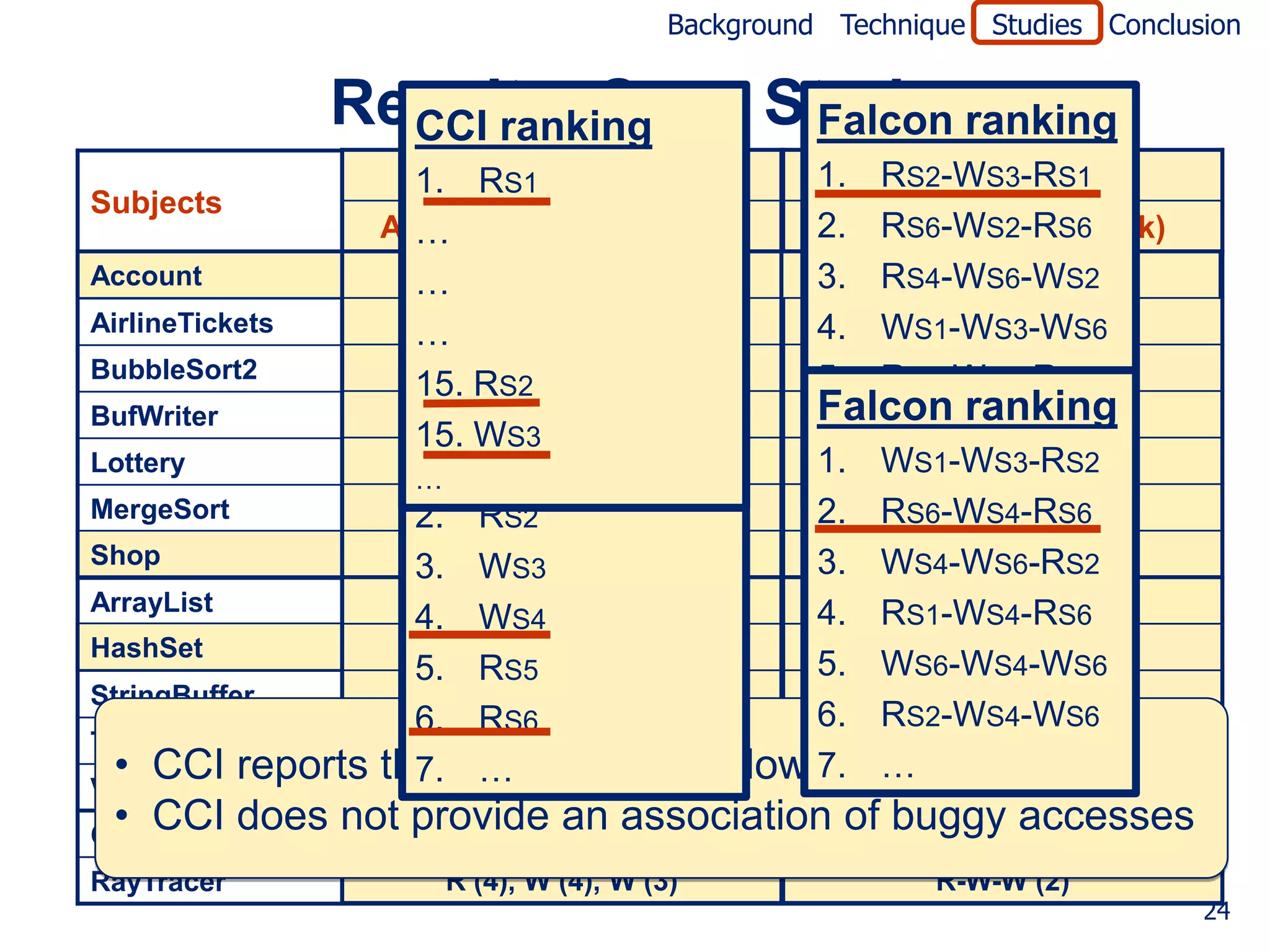
![Background Technique Studies Conclusion
Empirical Study 3 – Case Study
Goal
• To compare effectiveness of Falcon to CCI*
• CCI observes memory accesses, outcome (pass/fail)
• CCI reports suspiciousness of each memory access predicate
(i.e., memory access and previous access type pair)
Method
• Implemented the CCI technique in the Falcon toolset
• For test case with 100 runs and subjects
• Executed the tool
• Found the access and rank of actual bug
* Cooperative Crug Isolation [Thakur, Sen, Liblit, Lu, WODA09]
23](https://image.slidesharecdn.com/icse2010-v4-120406144228-phpapp01/75/Falcon-Fault-Localization-in-Concurrent-Programs-23-2048.jpg)