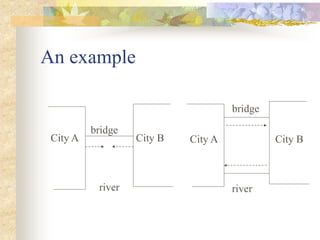
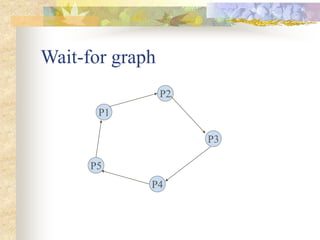
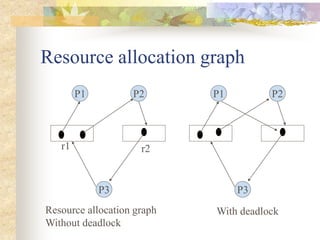
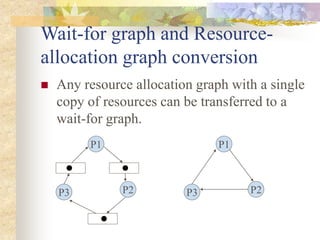
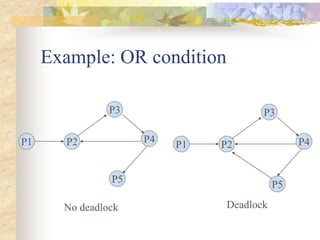
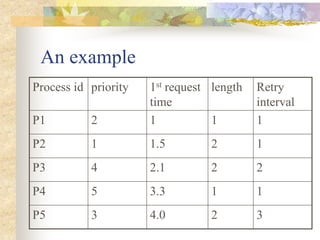
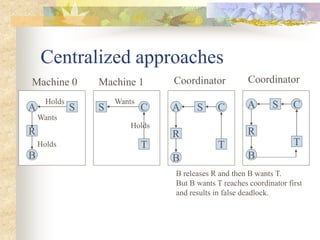
Deadlocks occur when processes are blocked waiting for resources held by other processes, forming a cyclic dependency. There are four conditions for deadlock: mutual exclusion, hold and wait, no preemption, and circular wait. Strategies to handle deadlocks include prevention, avoidance, and detection/recovery. Prevention breaks deadlock conditions through methods like simultaneous or priority-based resource acquisition. Avoidance dynamically allocates resources if the resulting state is safe. Detection finds existing deadlocks in the wait-for graph and recovery breaks them.