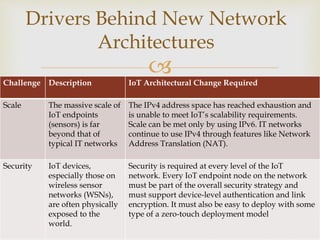
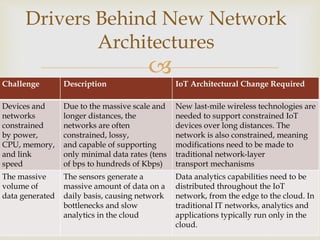
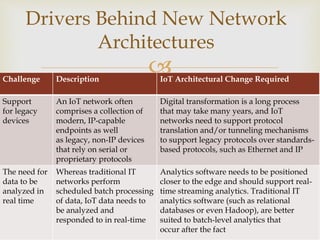
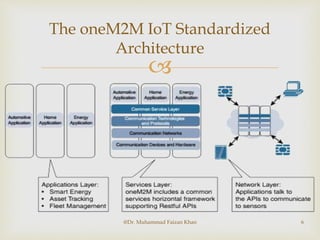
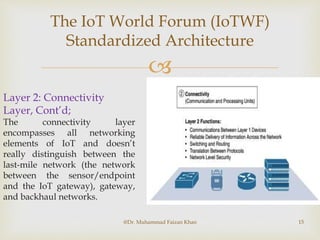
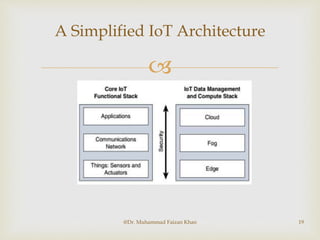
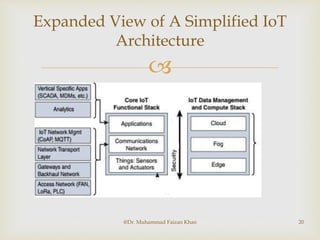
The document discusses two common IoT network architectures: oneM2M and the IoT World Forum (IoTWF) architecture. The oneM2M architecture divides functions into an application layer, services layer, and network layer. The IoTWF architecture is a seven-layer model with layers including physical devices, connectivity, edge computing, data storage and analytics, and applications. Both architectures aim to provide standardized frameworks to address challenges of designing large-scale IoT networks.