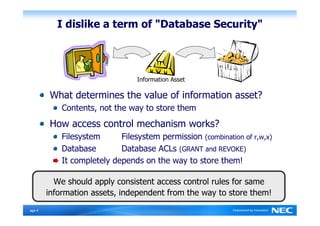
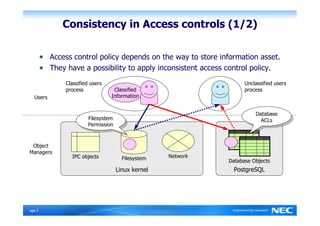
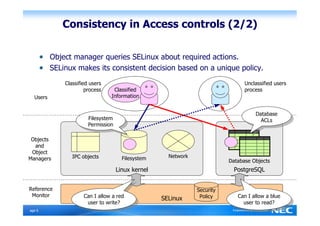
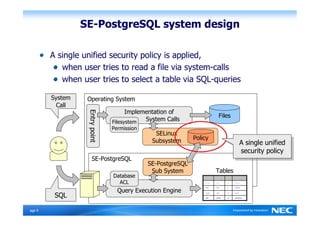
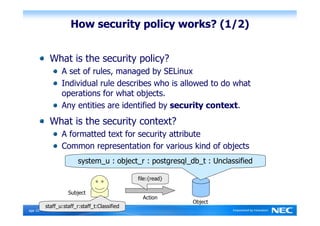
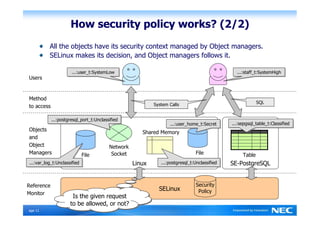
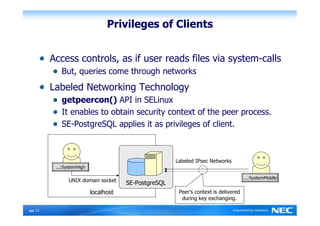
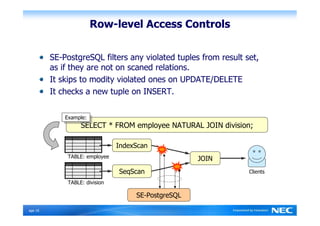
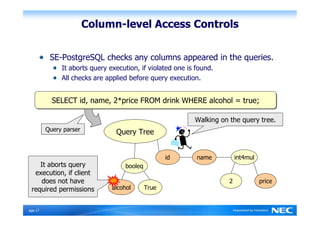
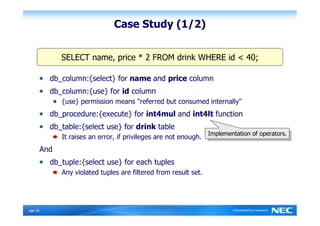
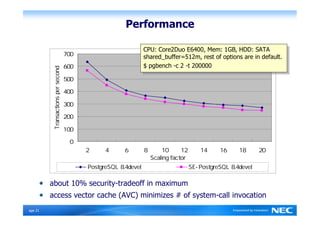
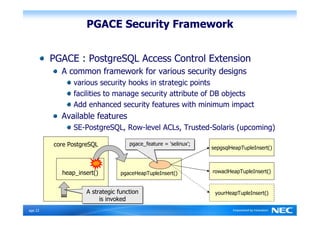
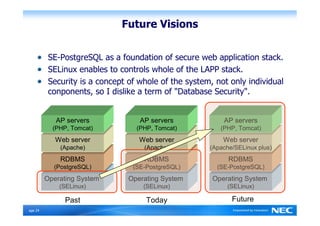
The Security-Enhanced PostgreSQL (SE-PostgreSQL) provides system-wide consistency in access controls between the operating system and database management system through a single unified security policy. It implements fine-grained mandatory access controls, including column- and row-level access controls. The goal of SE-PostgreSQL is to allow the database to be part of data flow control schemes and prevent information leakage or manipulation by malicious actors.