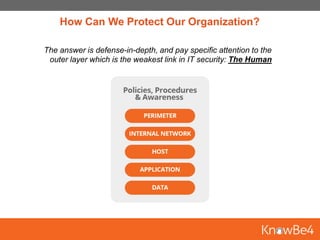
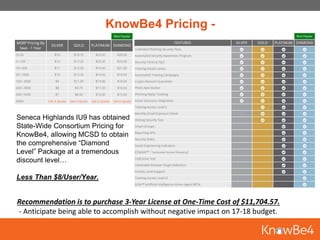
KnowBe4 is an integrated security awareness training and simulated phishing platform that can help organizations mitigate cybersecurity risks. The document discusses how CEO fraud and other scams cost organizations billions annually. It recommends that MCSD implement a security awareness training program using KnowBe4, which includes baseline phishing tests, training all employees, continuing phishing simulations, and analyzing phishing data. KnowBe4 pricing through an IU9 consortium would be significantly less than competitors like $7.80 per user per year for MCSD.