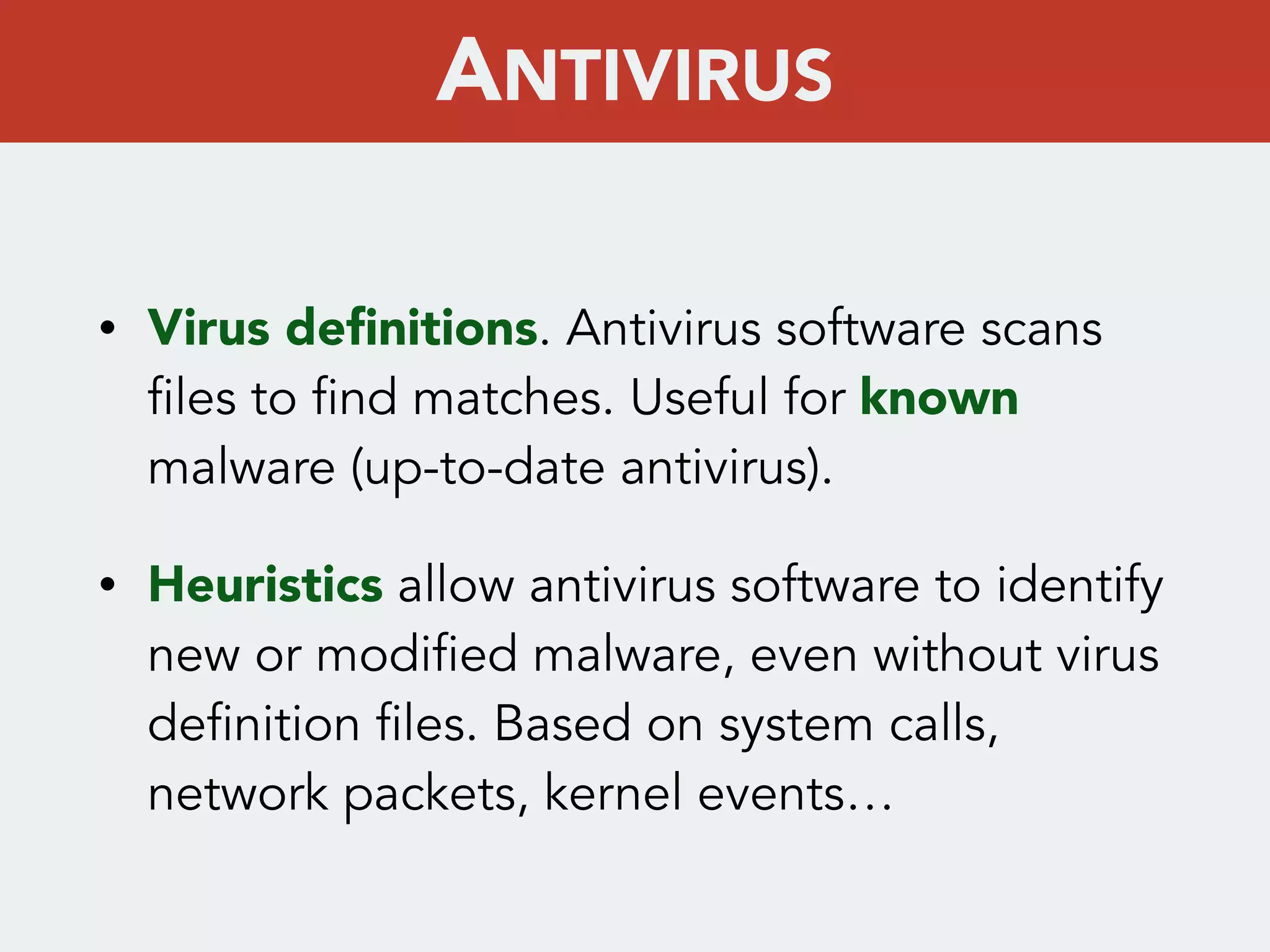
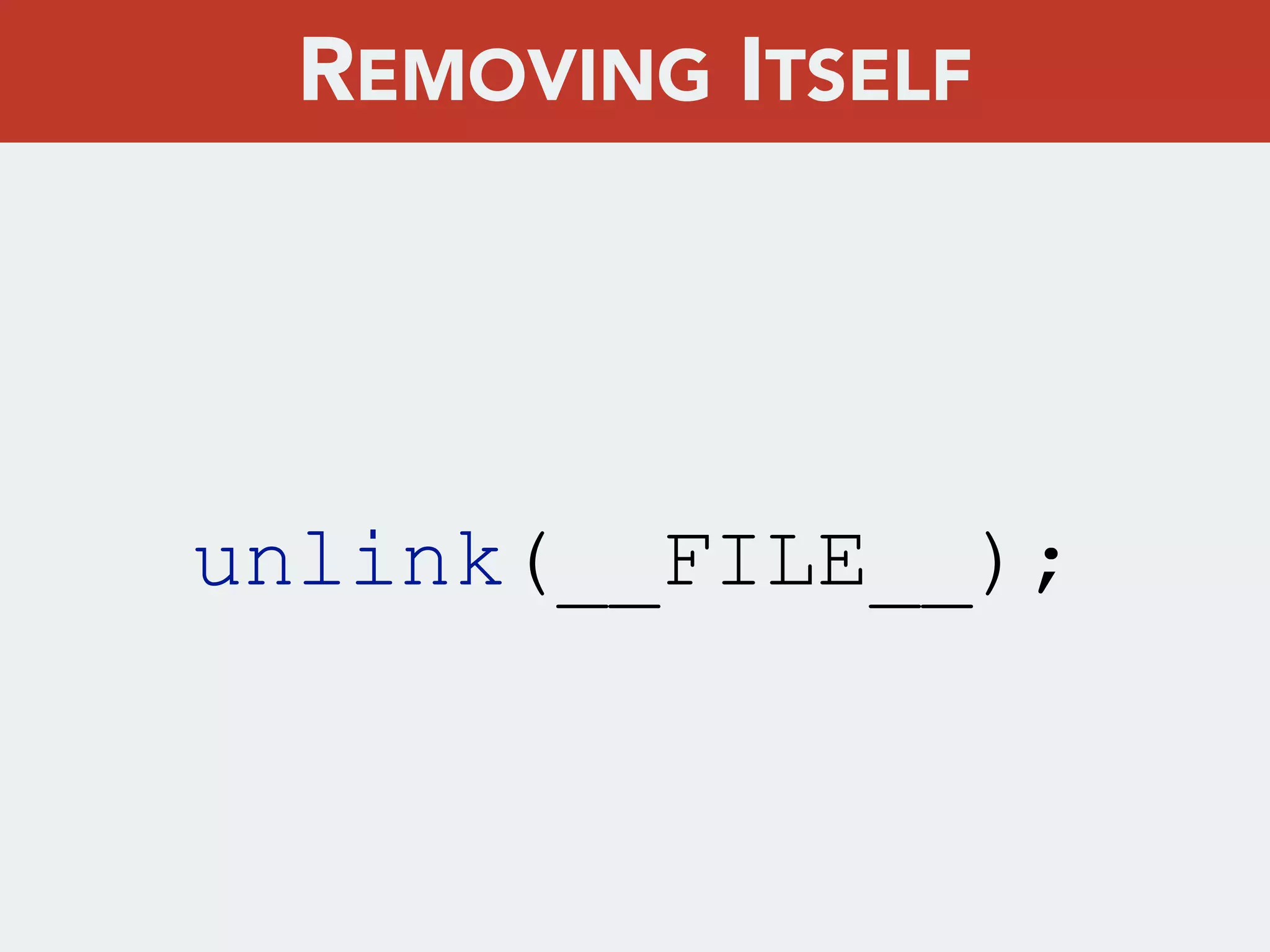
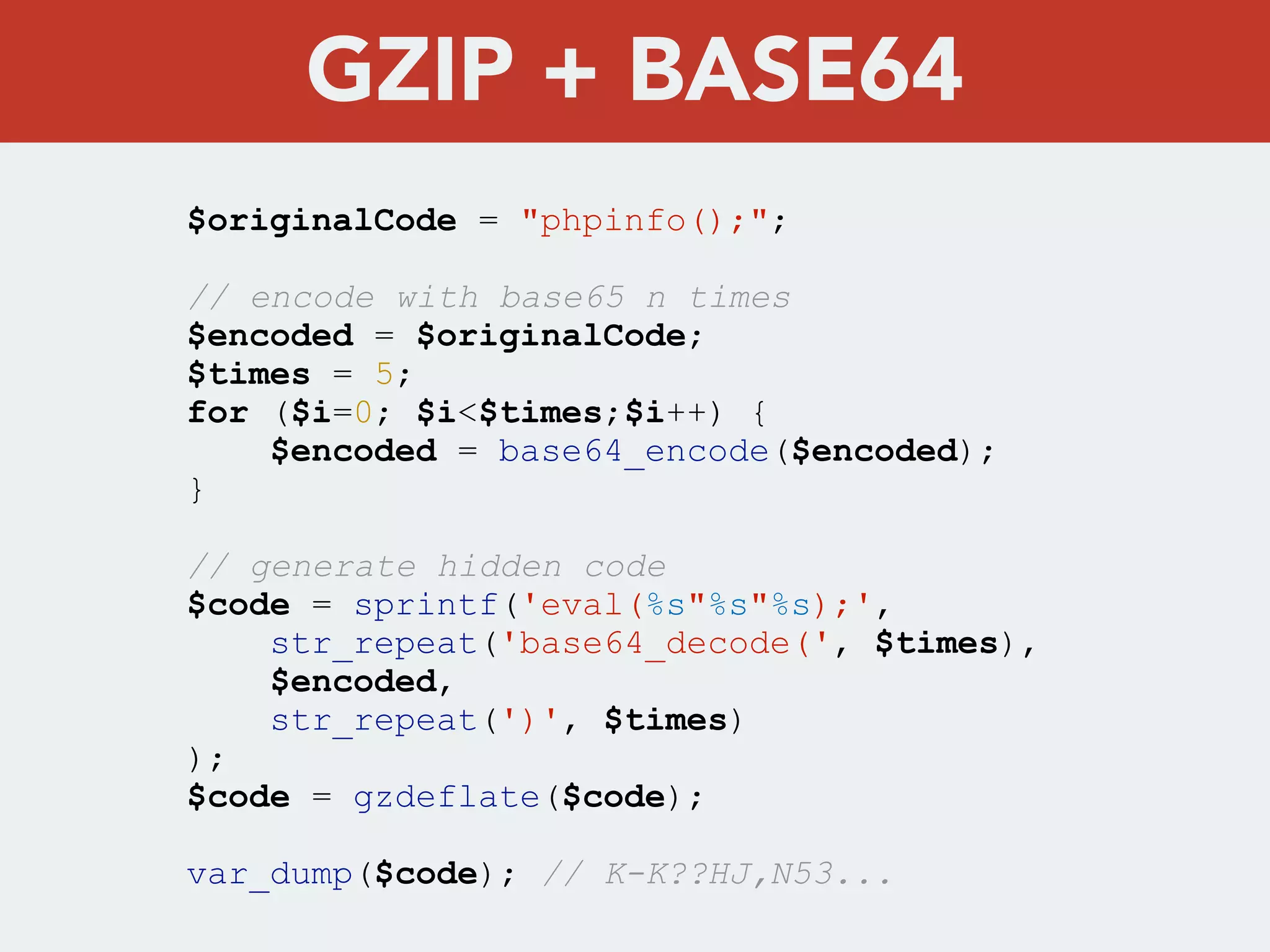
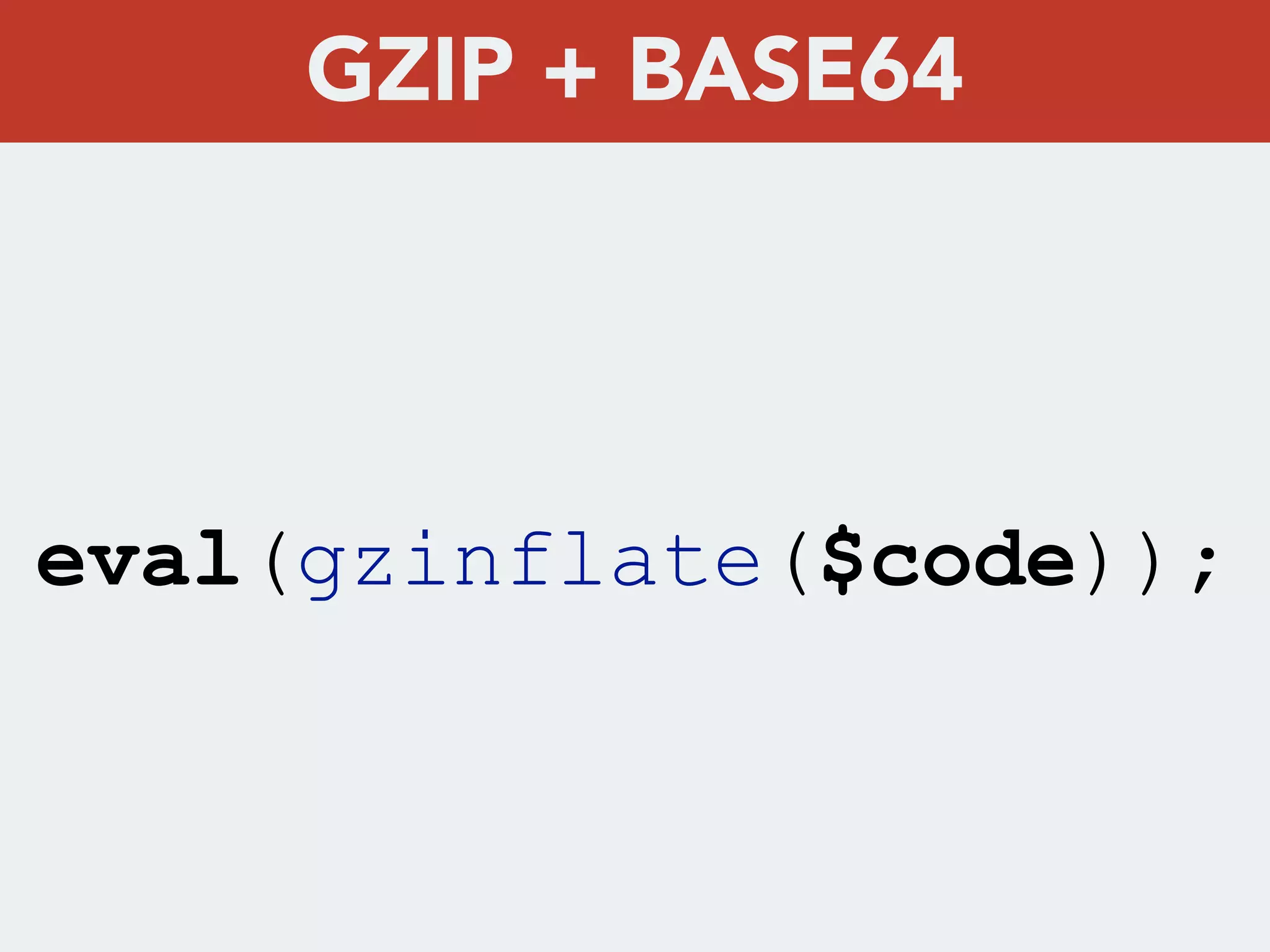
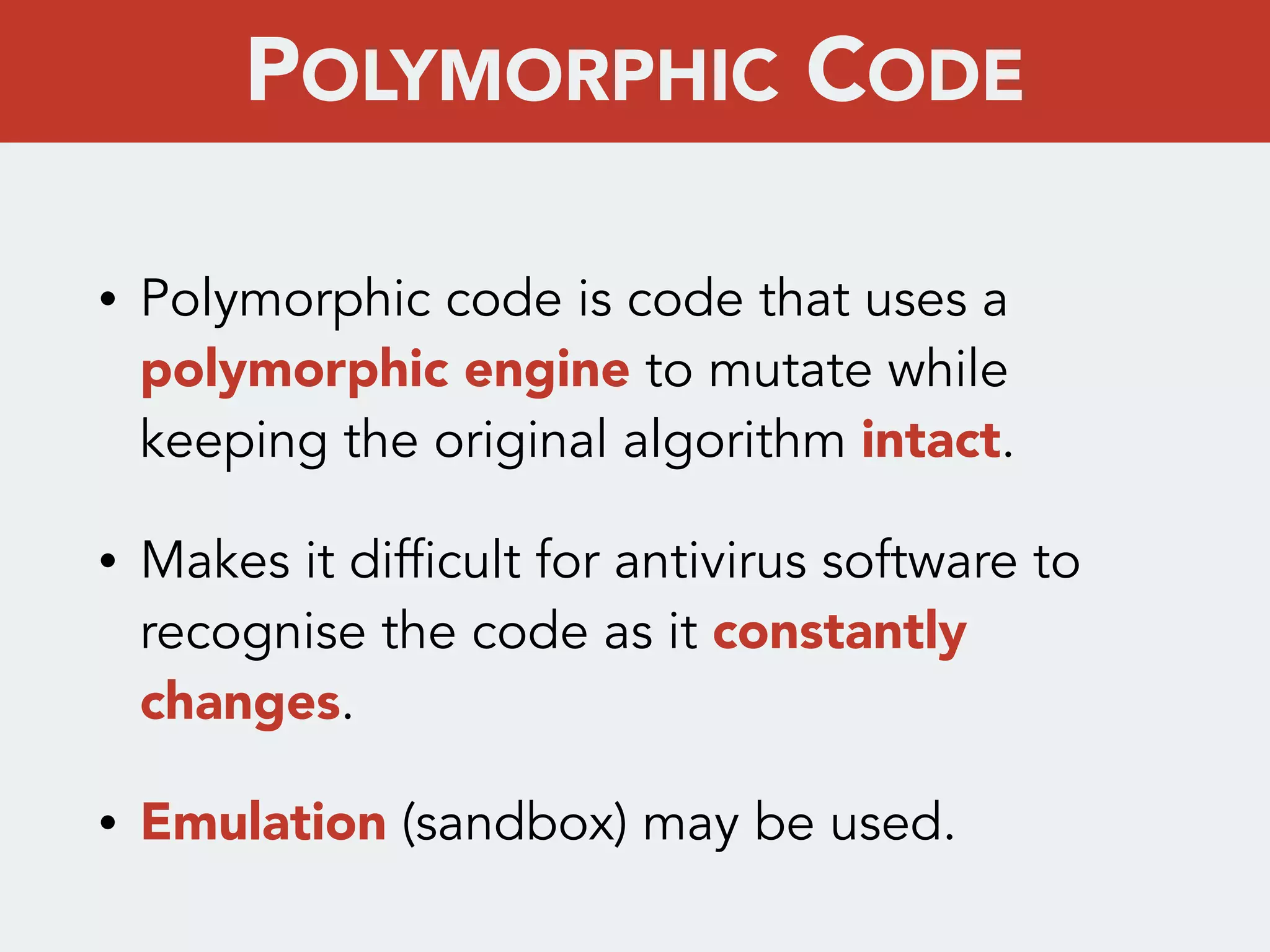
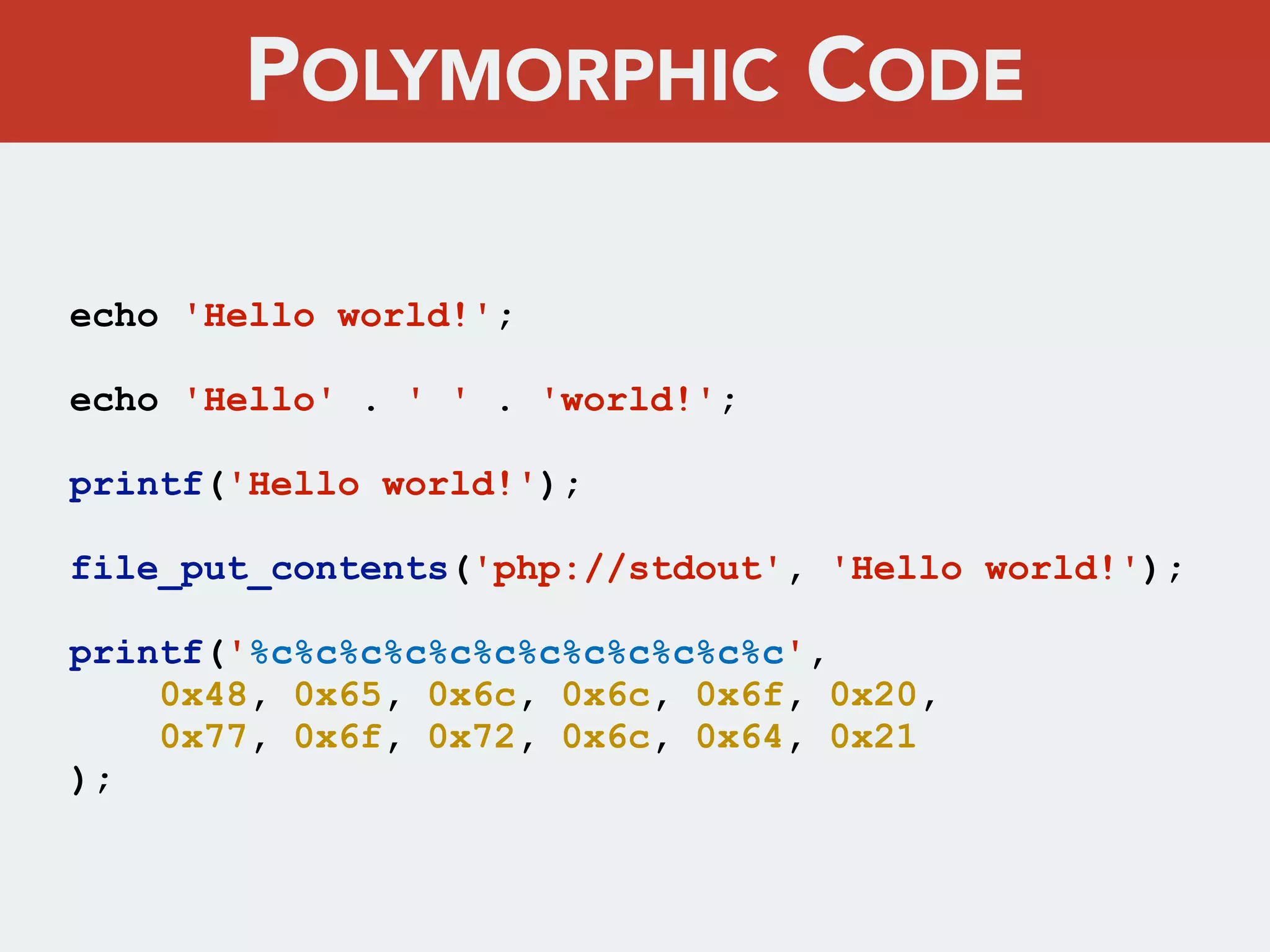
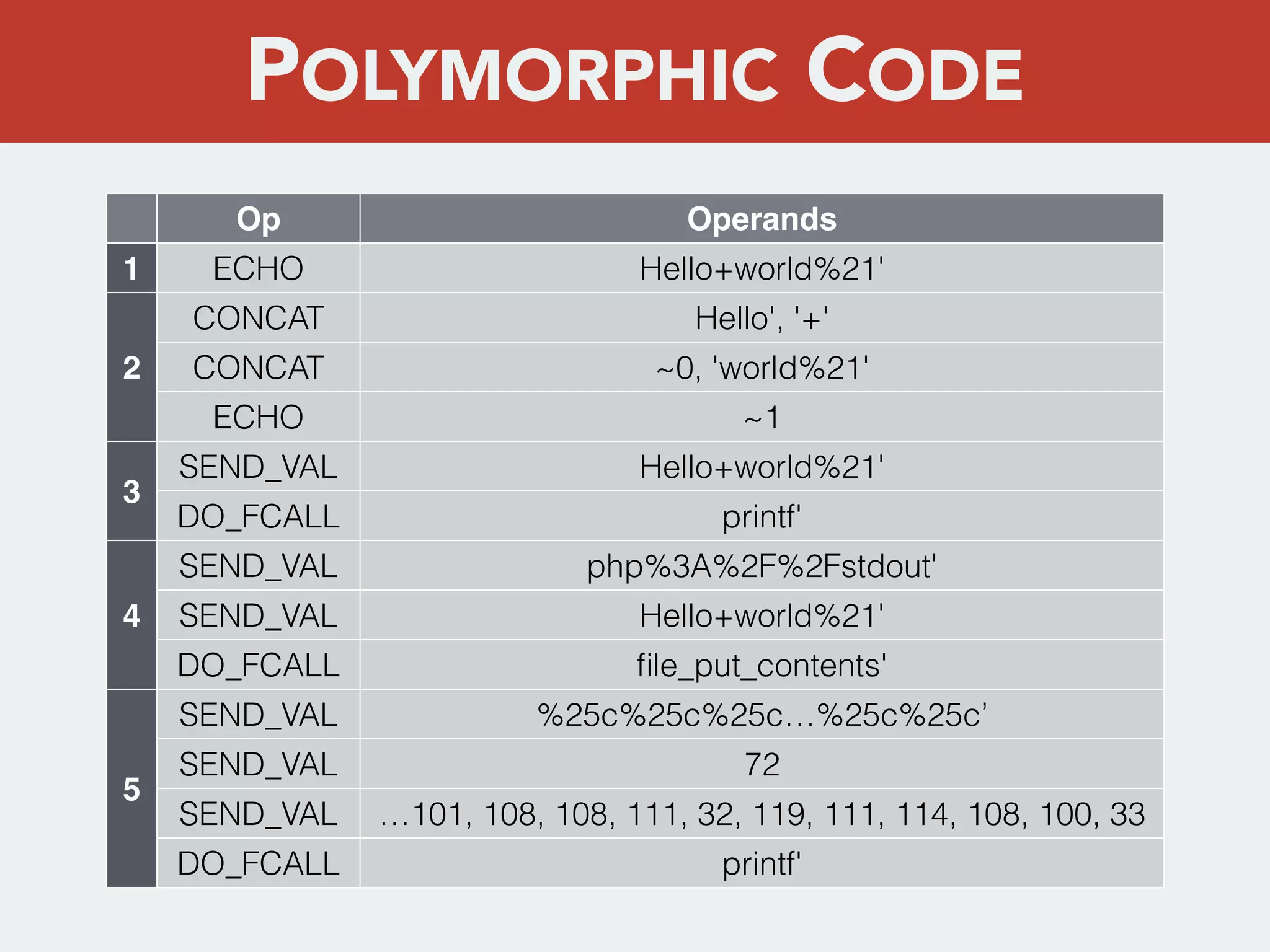
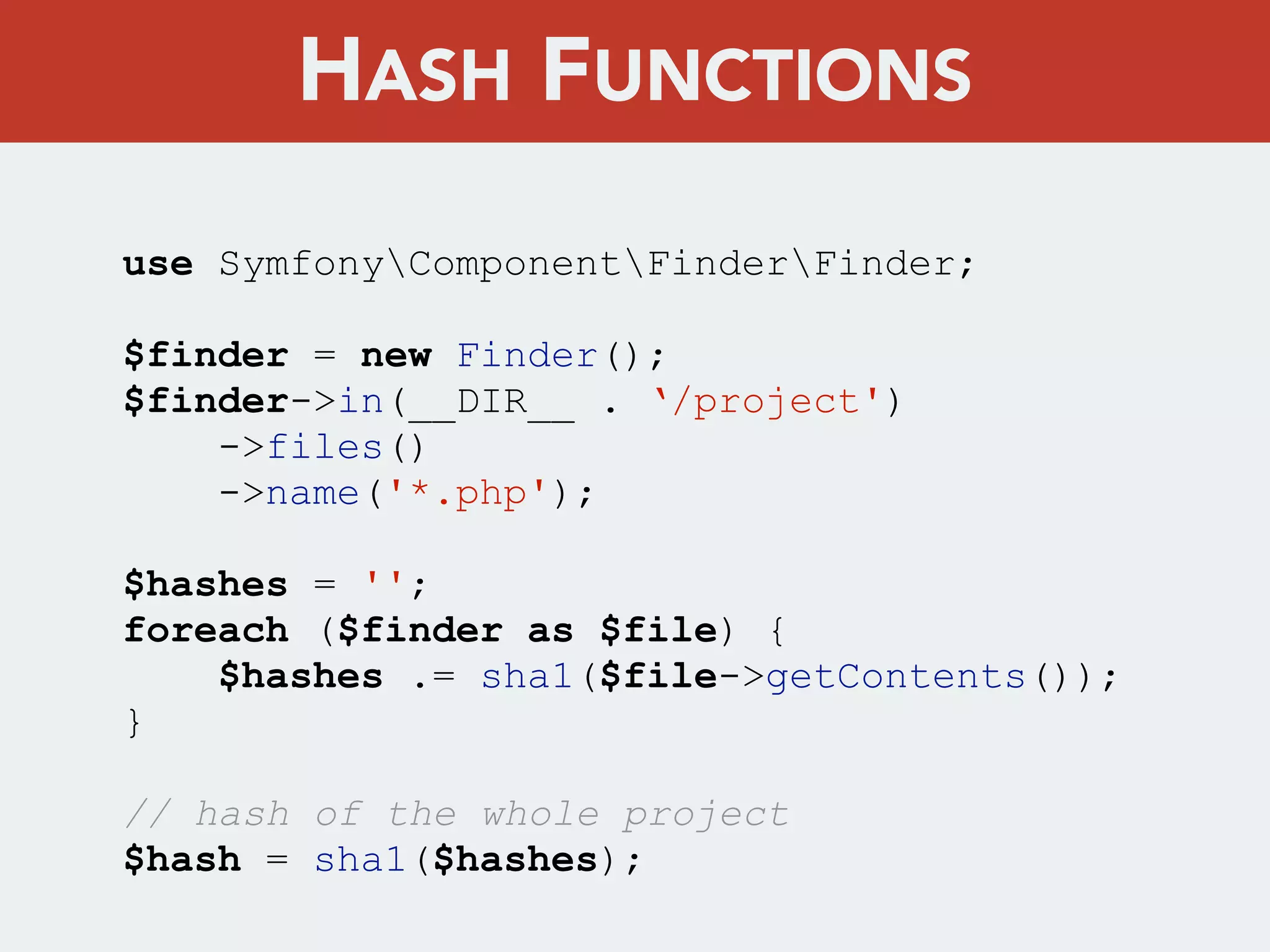
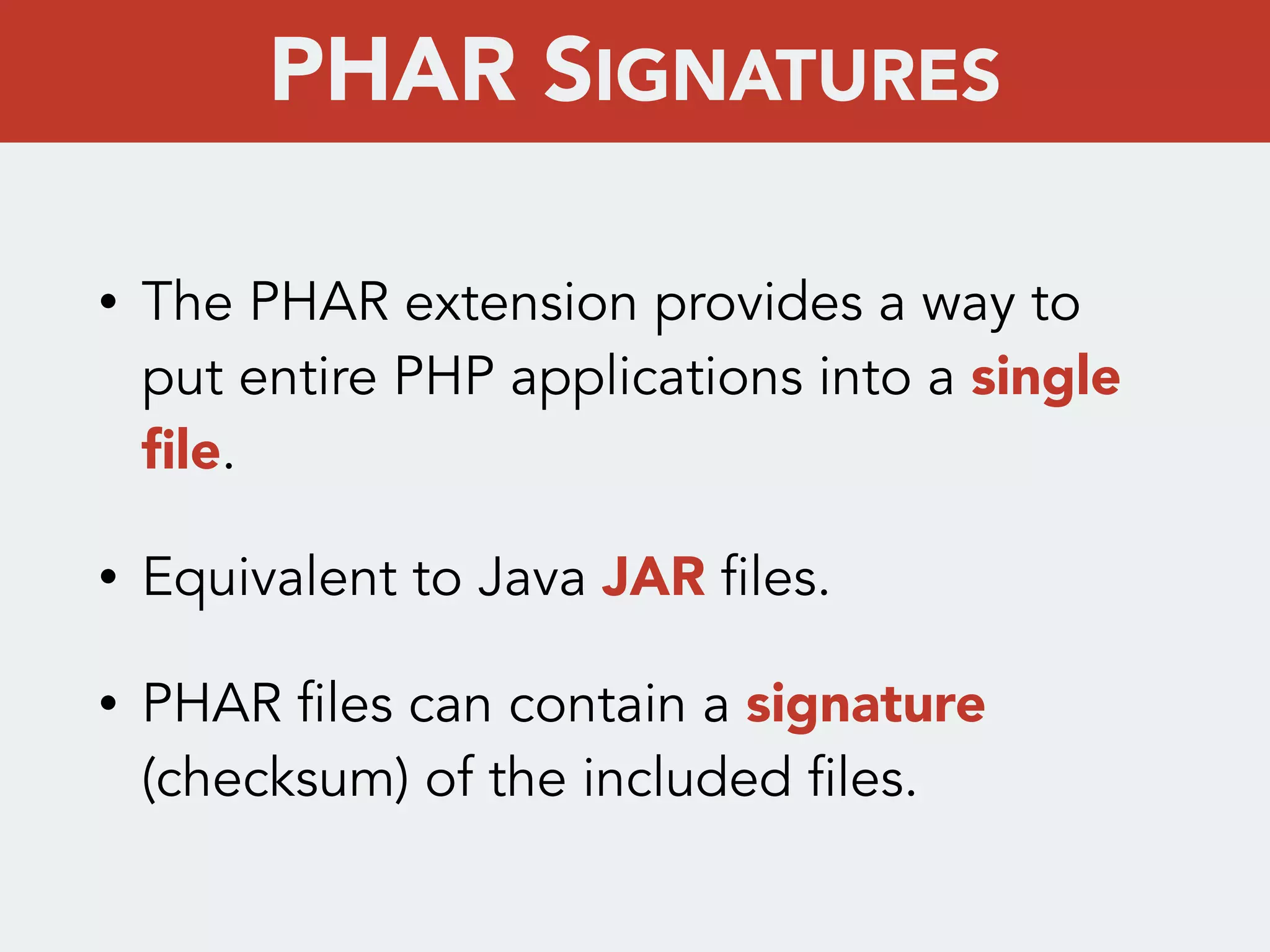
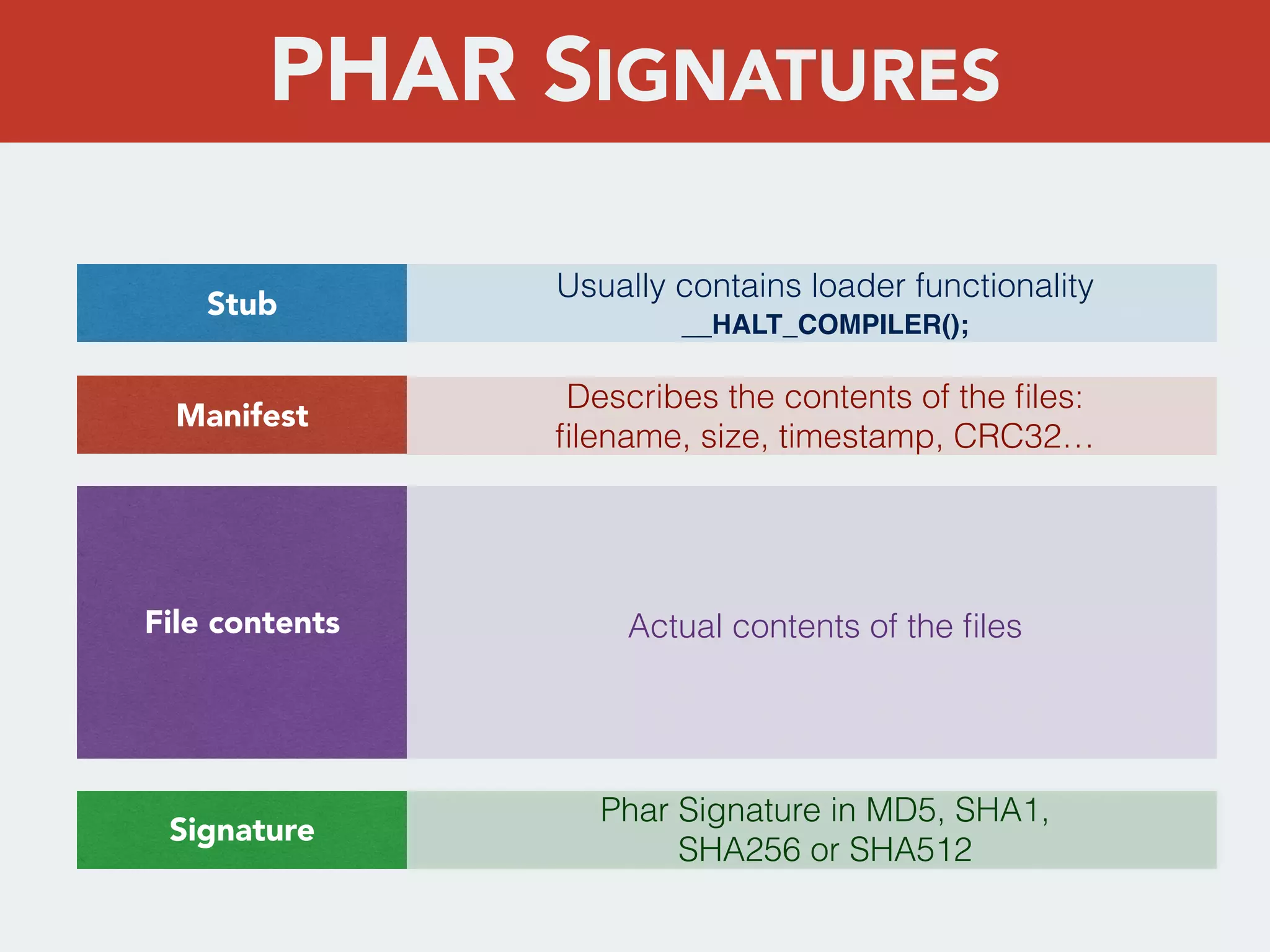
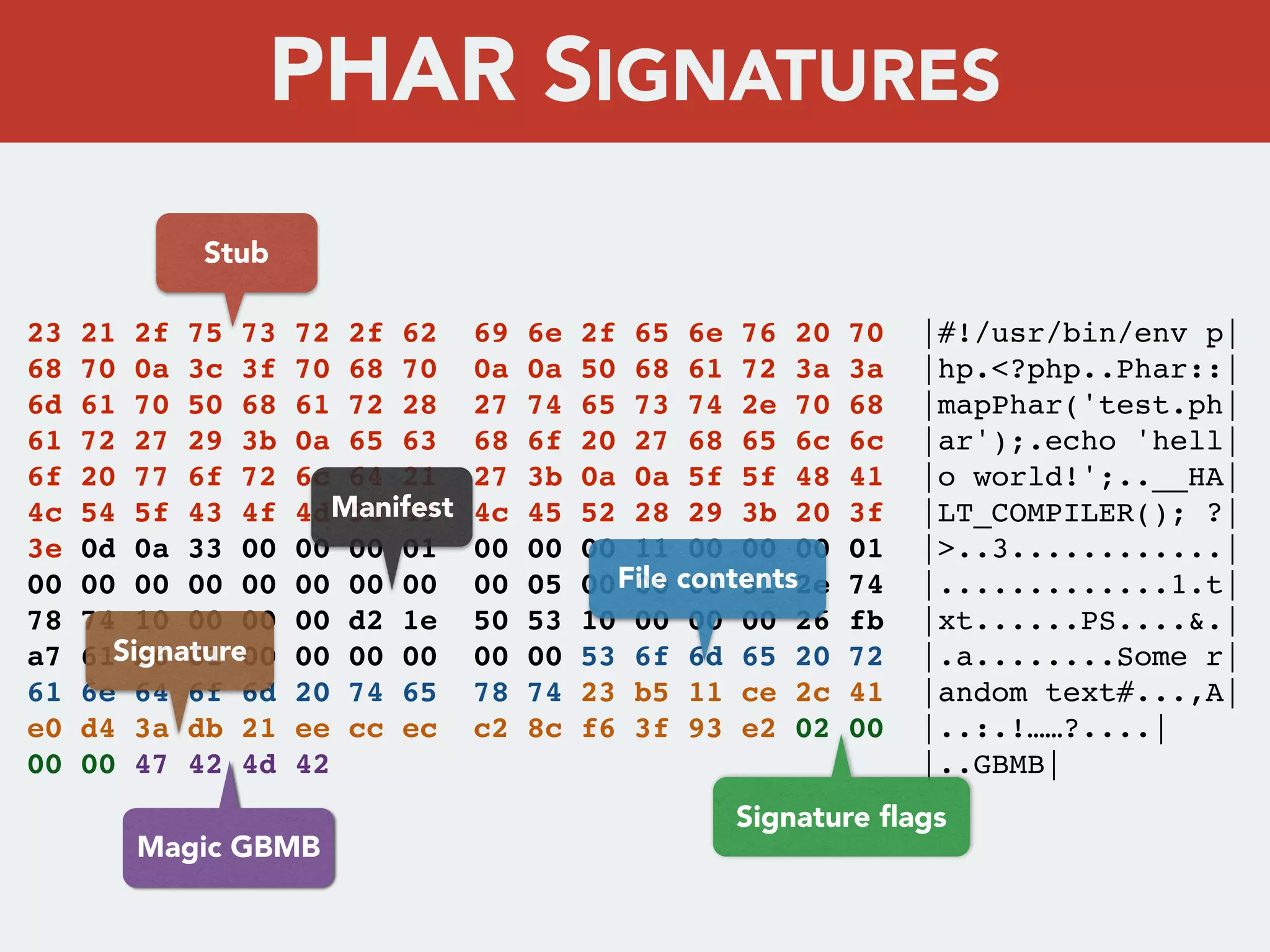
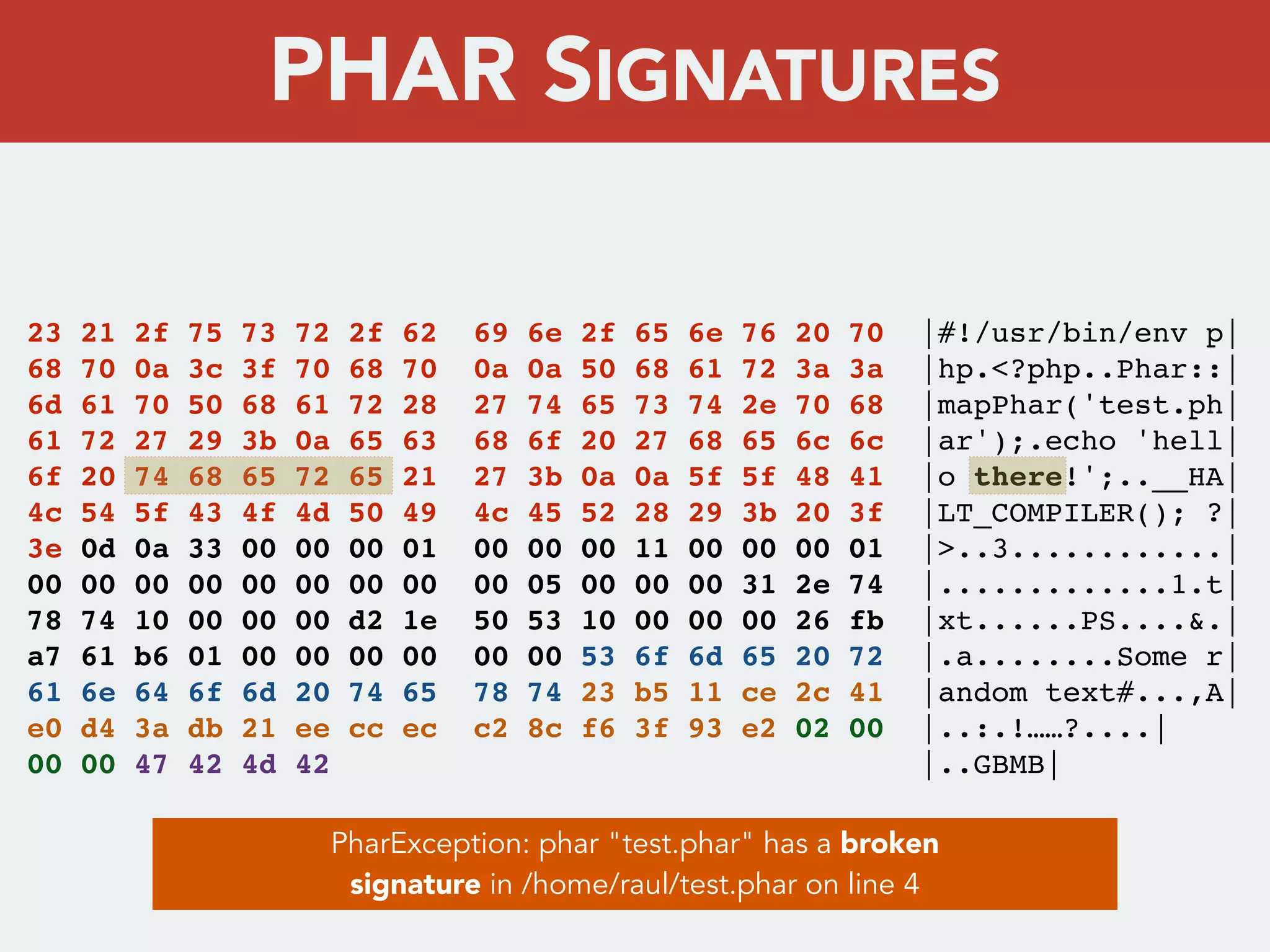
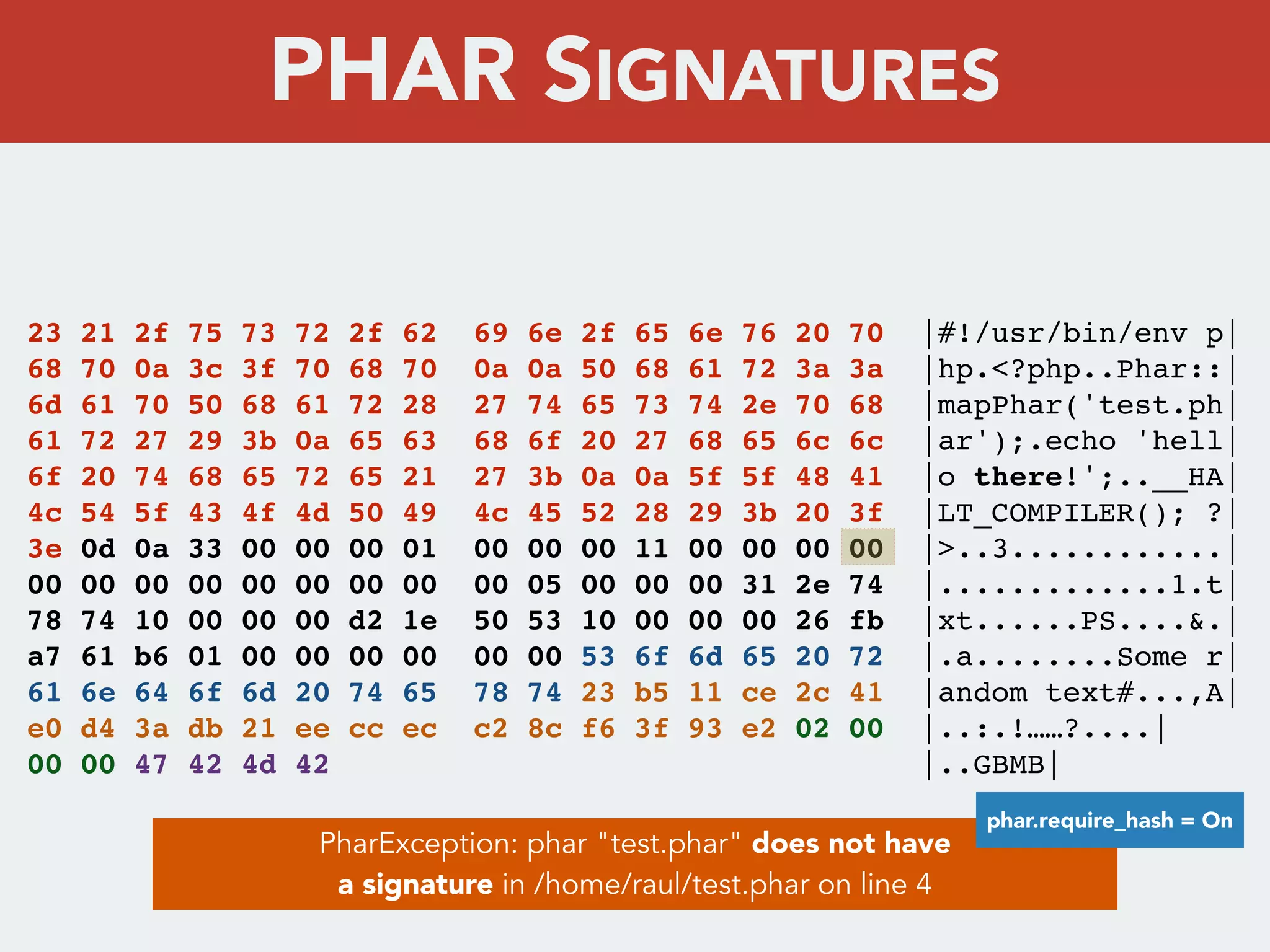
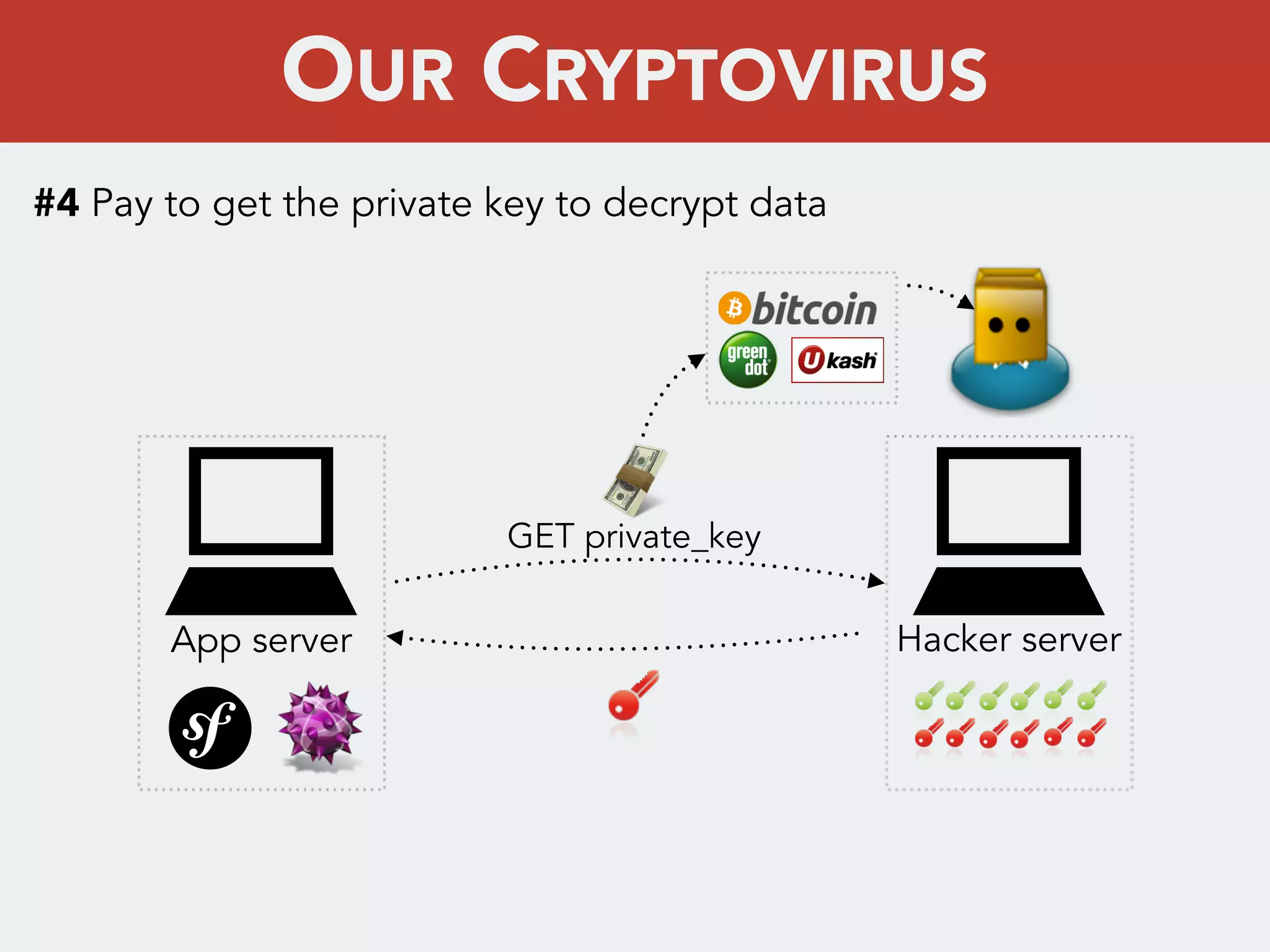
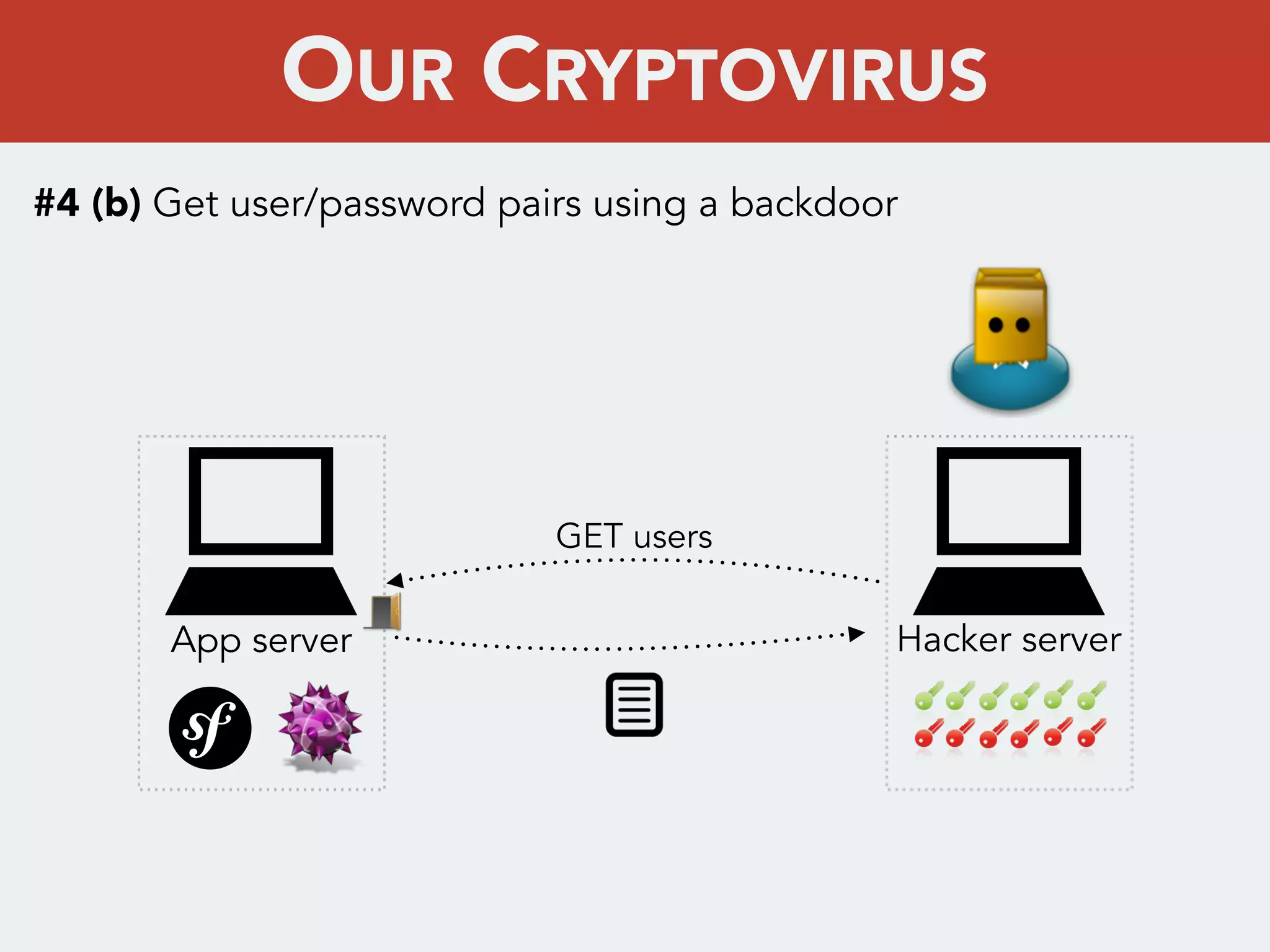
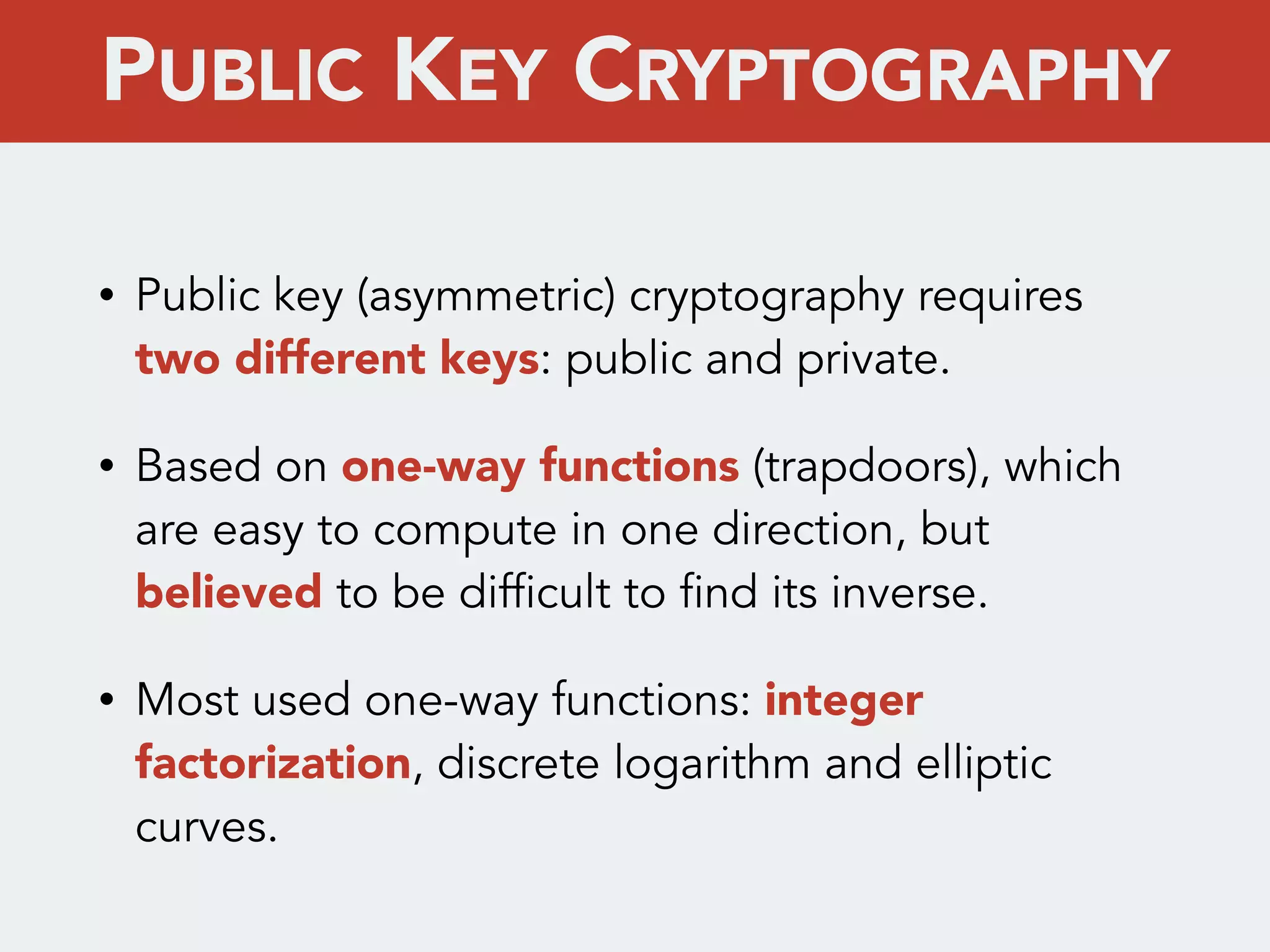
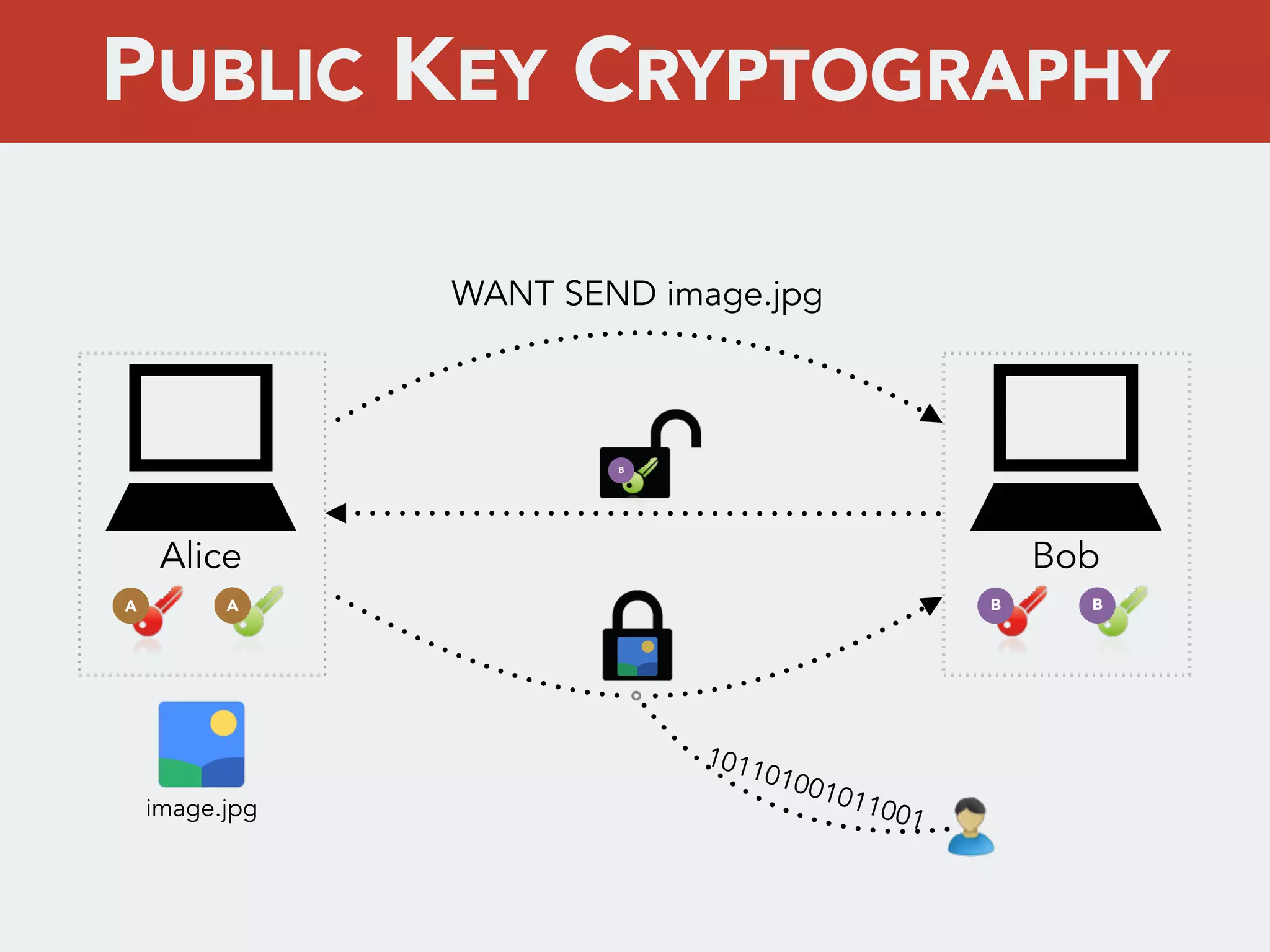
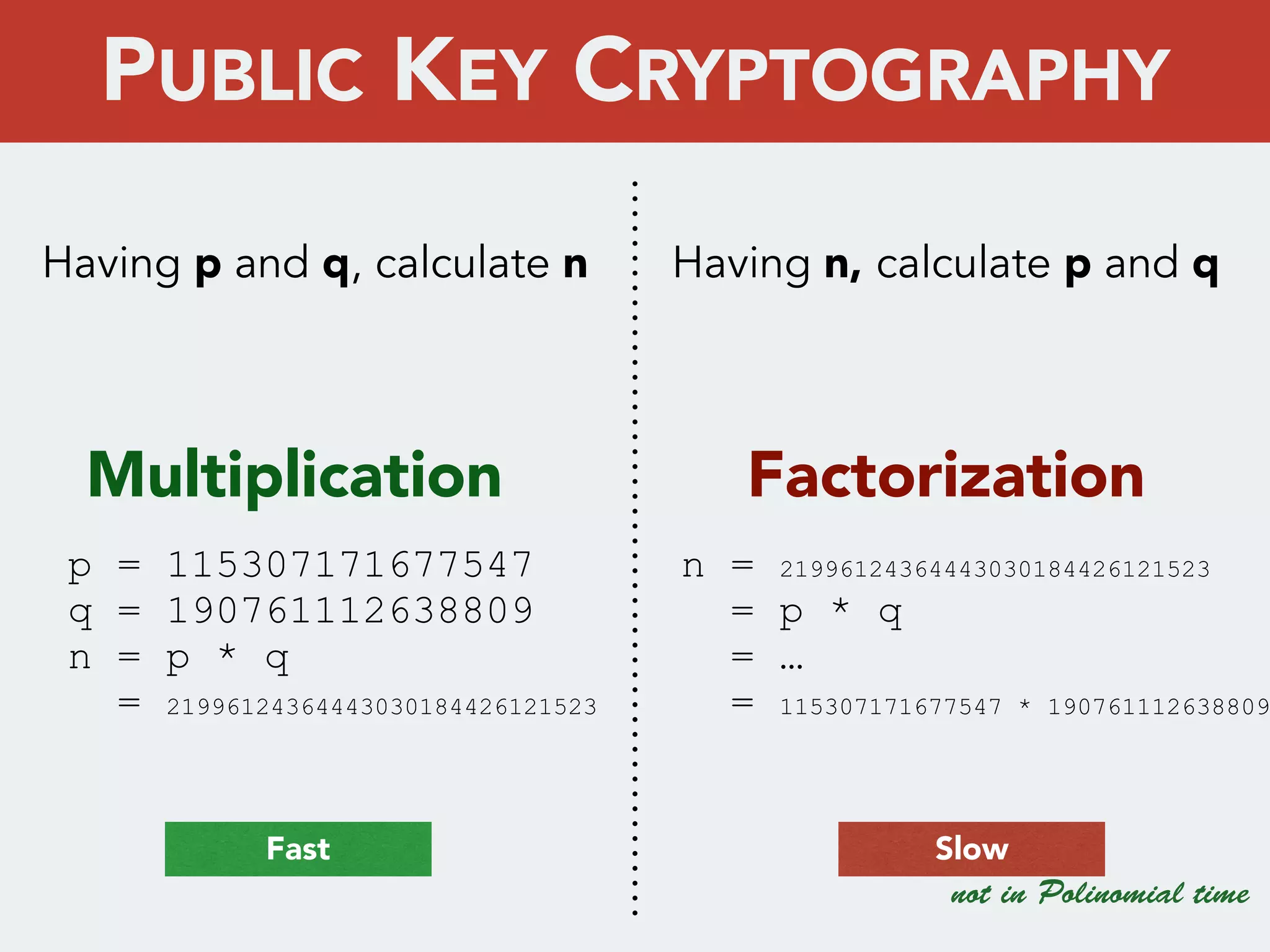
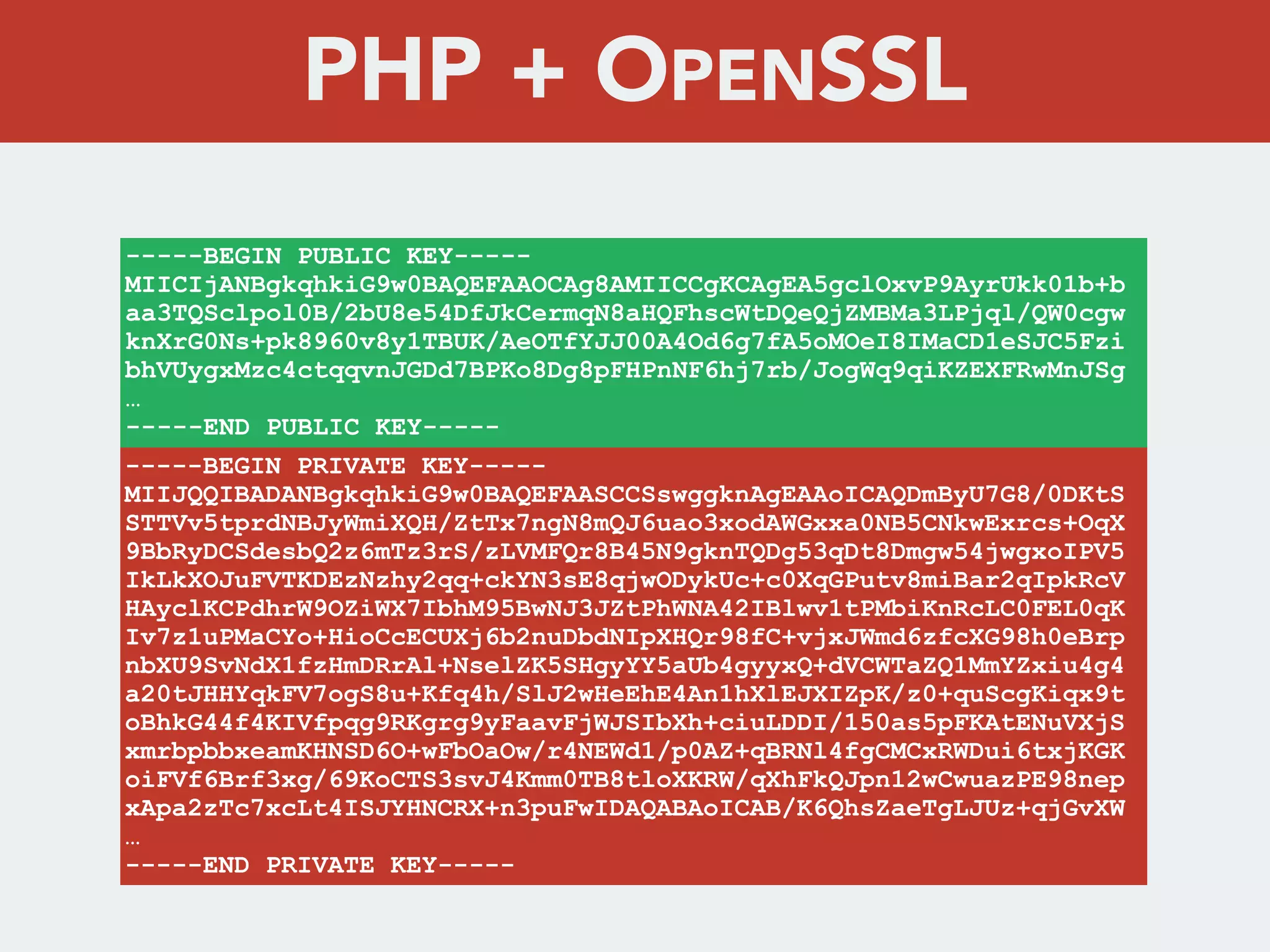
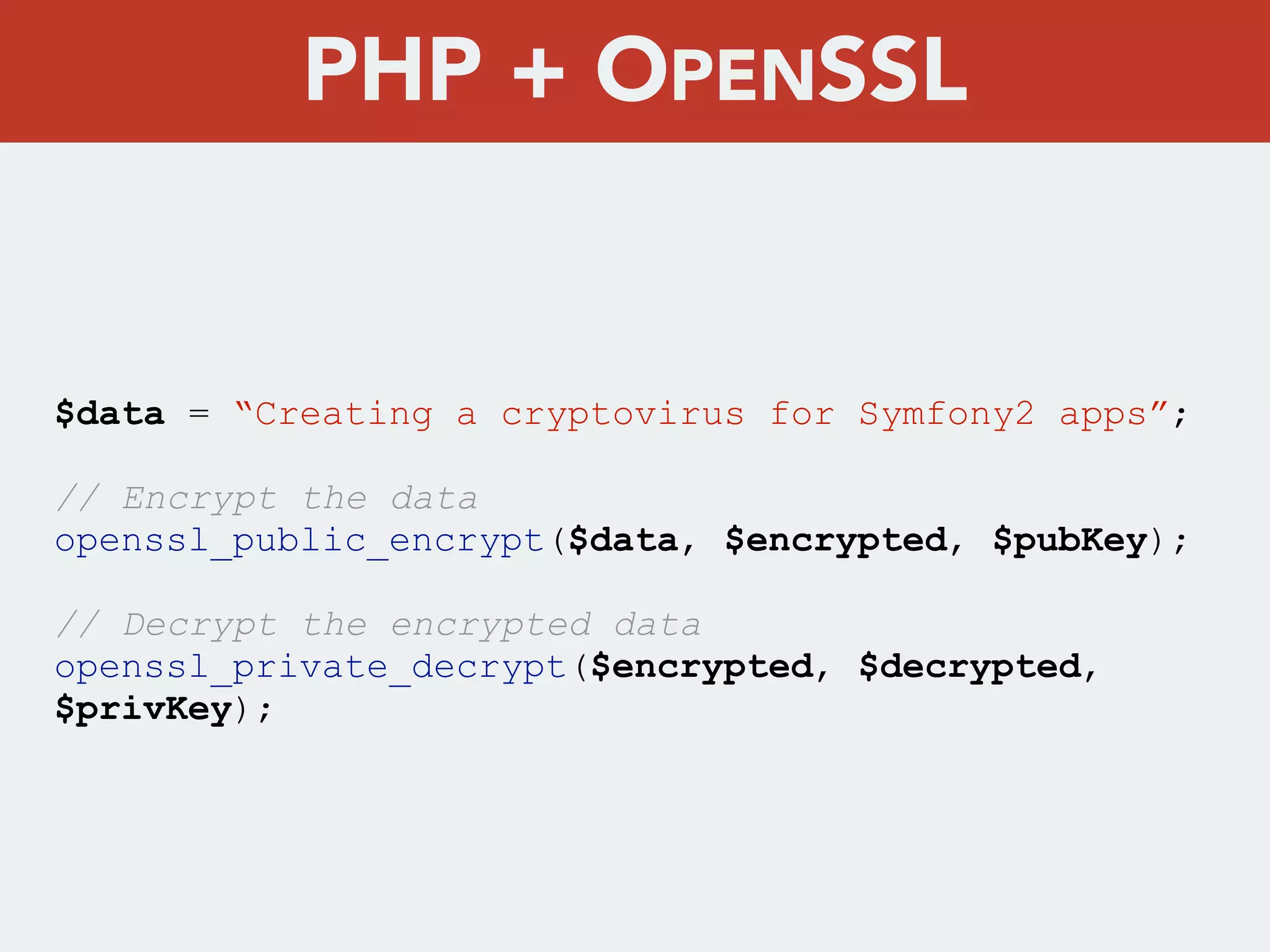
This document discusses creating a cryptovirus for Symfony applications as a proof of concept. It explains how a cryptovirus could work by getting a public key from a hacker server to encrypt data in the infected app, then paying to get the private key to decrypt the data. It covers relevant cryptography concepts like public key cryptography and OpenSSL. It also discusses techniques for hiding the virus from antivirus software like polymorphic code, gzip/base64 encoding, and checking file integrity with hash functions.




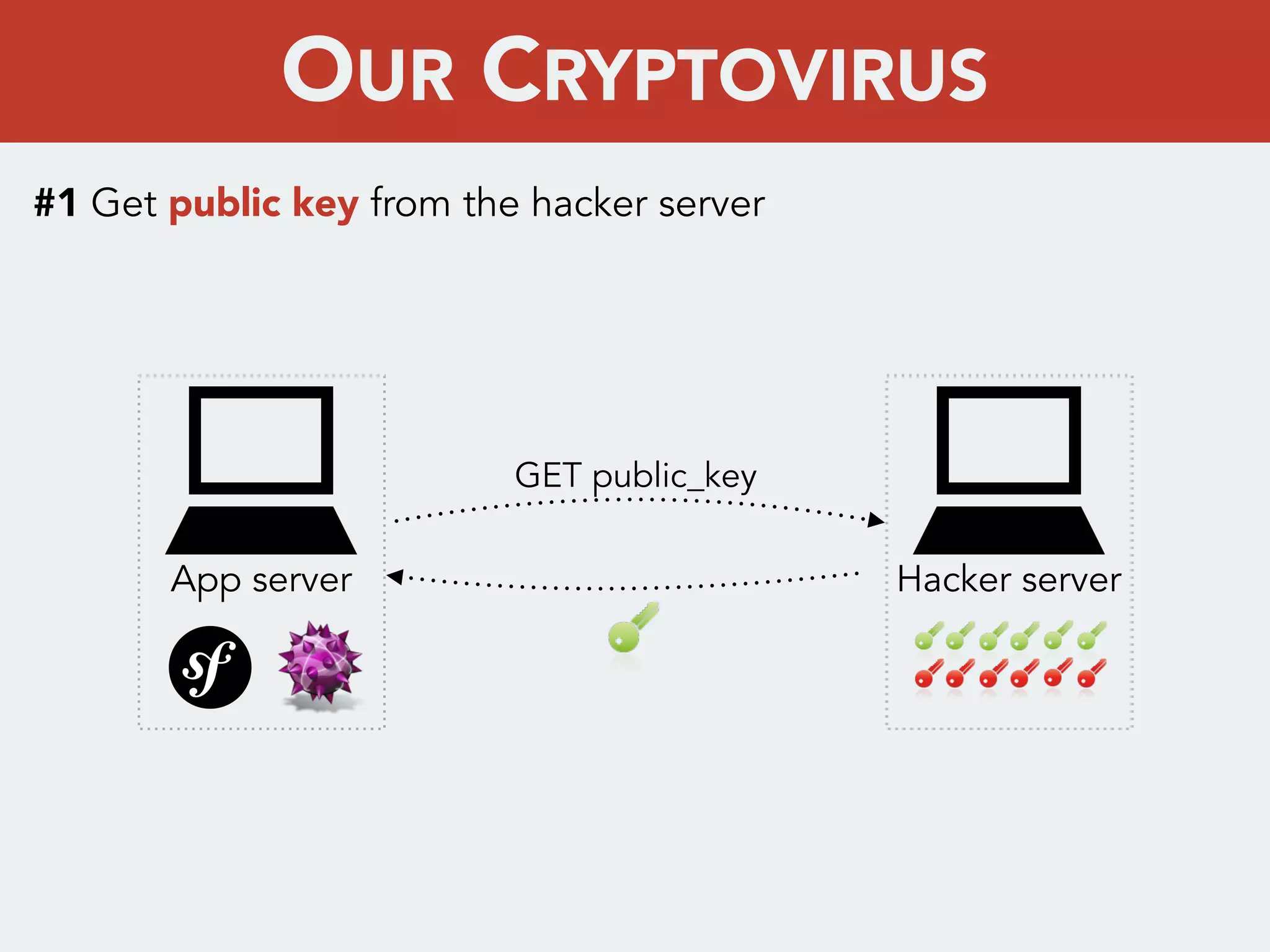
![#2 Infect the Symfony 2.x app
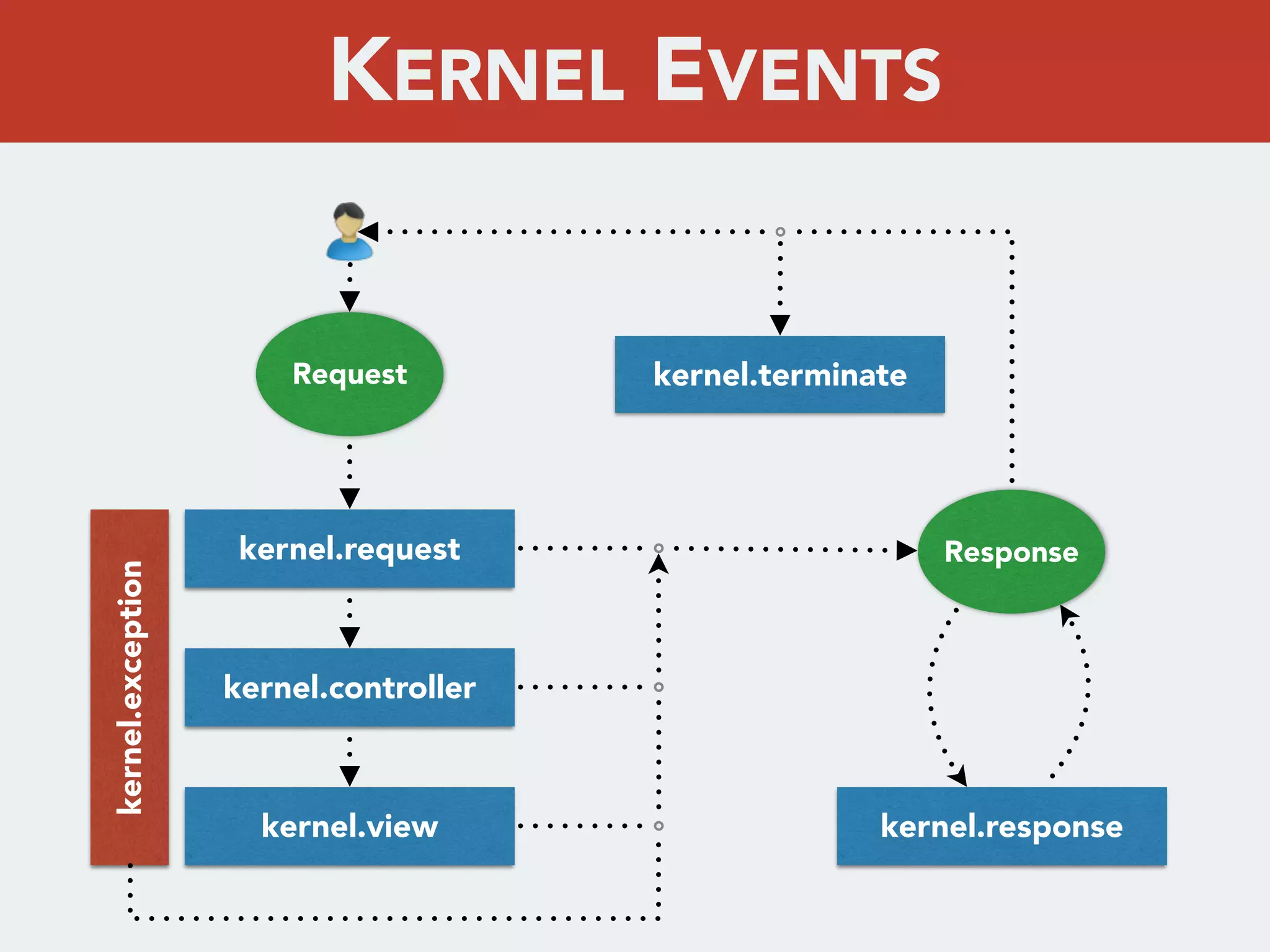
app[_dev].php
bootstrap.php.cache
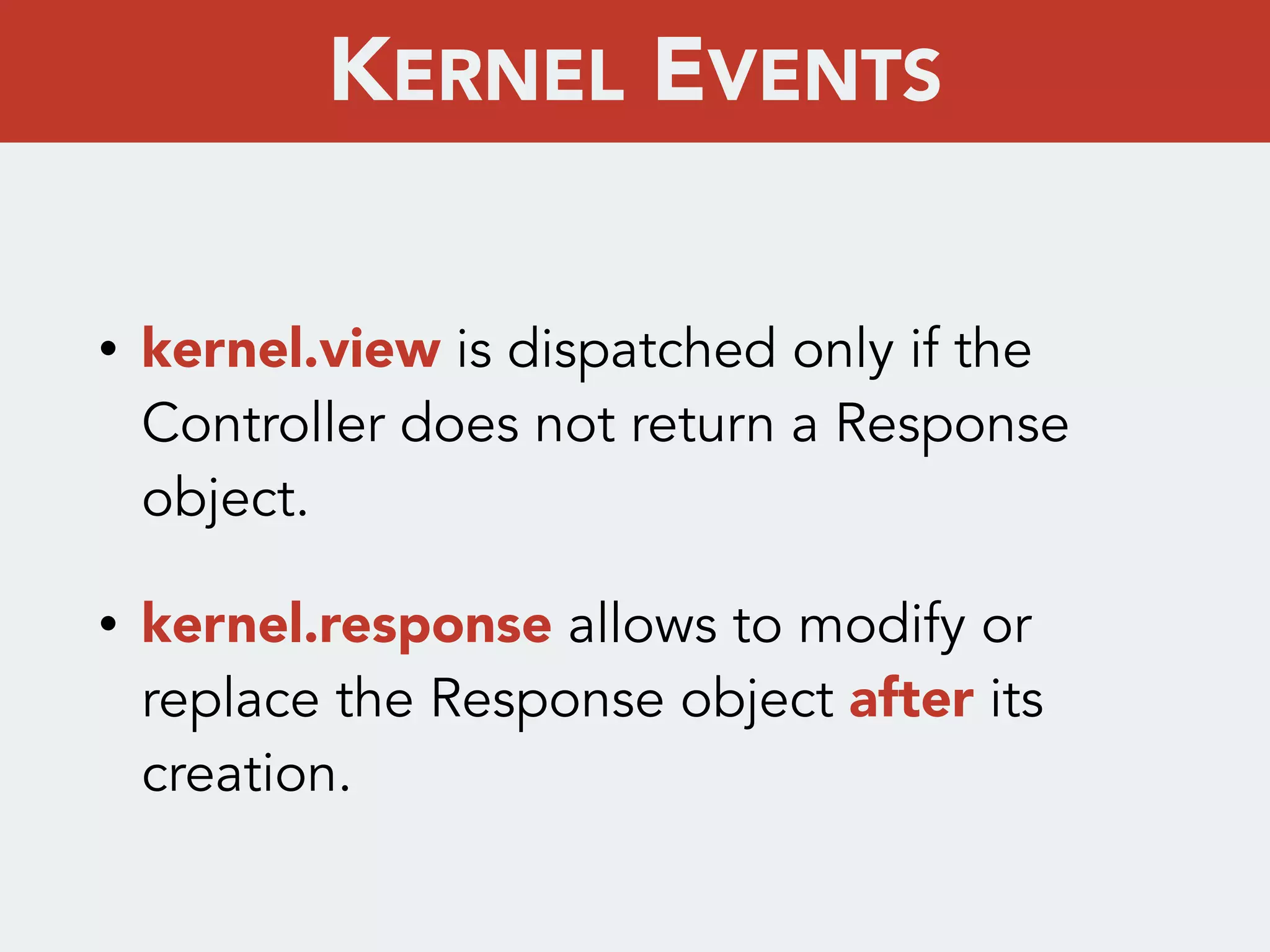
Kernel events
OUR CRYPTOVIRUS](https://image.slidesharecdn.com/symfonycryptopdf-140517003956-phpapp01/75/kernel-infect-Creating-a-cryptovirus-for-Symfony2-apps-8-2048.jpg)
![#3 Use the public key to encrypt data
app[_dev].php
bootstrap.php.cache
Kernel events
Database
User uploads
Logs
…
OUR CRYPTOVIRUS](https://image.slidesharecdn.com/symfonycryptopdf-140517003956-phpapp01/75/kernel-infect-Creating-a-cryptovirus-for-Symfony2-apps-9-2048.jpg)
![#3 (b) Intercept user/passwords and save them encrypted
app[_dev].php
bootstrap.php.cache
Kernel events
raul
Submit
User
*****Password
OUR CRYPTOVIRUS](https://image.slidesharecdn.com/symfonycryptopdf-140517003956-phpapp01/75/kernel-infect-Creating-a-cryptovirus-for-Symfony2-apps-11-2048.jpg)


![$config = array(
"digest_alg" => "sha512",
"private_key_bits" => 4096,
"private_key_type" => OPENSSL_KEYTYPE_RSA,
);
// Create the private and public key
$resource = openssl_pkey_new($config);
// Extract the private key
openssl_pkey_export($resource, $privKey);
// Extract the public key
$pubKey = openssl_pkey_get_details($res);
$pubKey = $pubKey[“key"];
PHP + OPENSSL](https://image.slidesharecdn.com/symfonycryptopdf-140517003956-phpapp01/75/kernel-infect-Creating-a-cryptovirus-for-Symfony2-apps-18-2048.jpg)



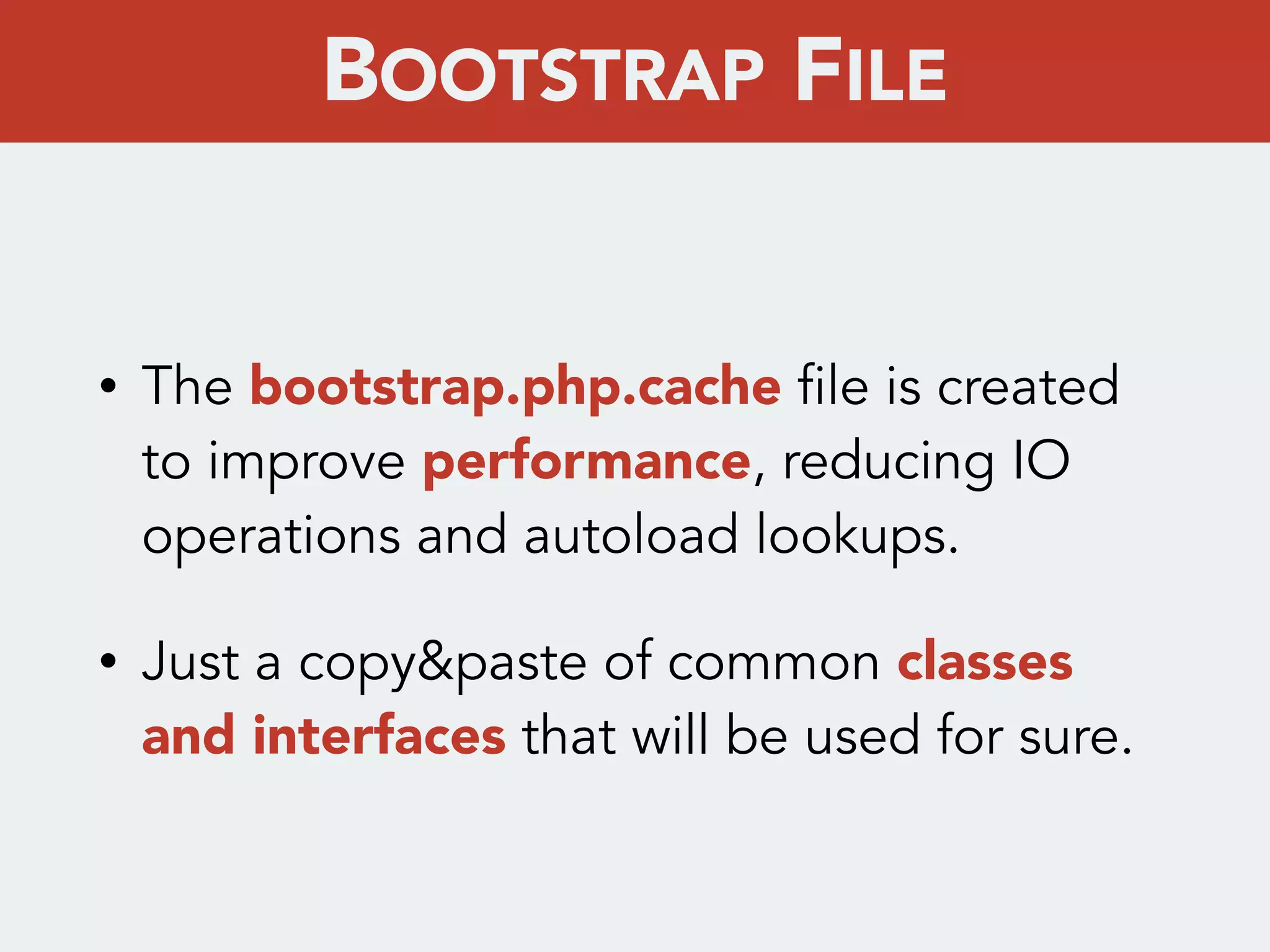
![{
"name": "symfony/framework-standard-edition",
"scripts": {
"post-install-cmd": [
...,
“SensioBundleDistributionBundleComposer
ScriptHandler::buildBootstrap",
...
],
"post-update-cmd": [
...,
“SensioBundleDistributionBundleComposer
ScriptHandler::buildBootstrap",
...
]
}
}
BOOTSTRAP FILE](https://image.slidesharecdn.com/symfonycryptopdf-140517003956-phpapp01/75/kernel-infect-Creating-a-cryptovirus-for-Symfony2-apps-27-2048.jpg)