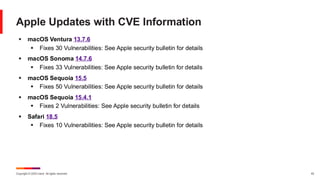
Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
























![Copyright © 2025 Ivanti. All rights reserved. 29
May Known Issues for Windows 10
▪ KB 5058392 - Win 10 Enterprise LTSC 2019, Win 10 IoT Enterprise LTSC 2019, Windows 10
IoT Core LTSC, Windows Server 2019
▪ [Citrix_SRA] Devices that have certain Citrix components installed might be unable to
complete installation of the January 2025 Windows security update. This has been noted
with the Citrix Session Recording Agent installed.
▪ Workaround: Citrix has provided several workaround options until they resolve the issue
with Microsoft. See KB for details.
▪ KB 5058379 – Windows 10 Enterprise LTSC 2021, Windows 10 IoT Enterprise LTSC 2021,
Windows 10, version 22H2, all editions
▪ [Citrix_SRA]](https://image.slidesharecdn.com/may2025patchtuesday-250514193317-06015c8c/85/May-Patch-Tuesday-29-320.jpg)