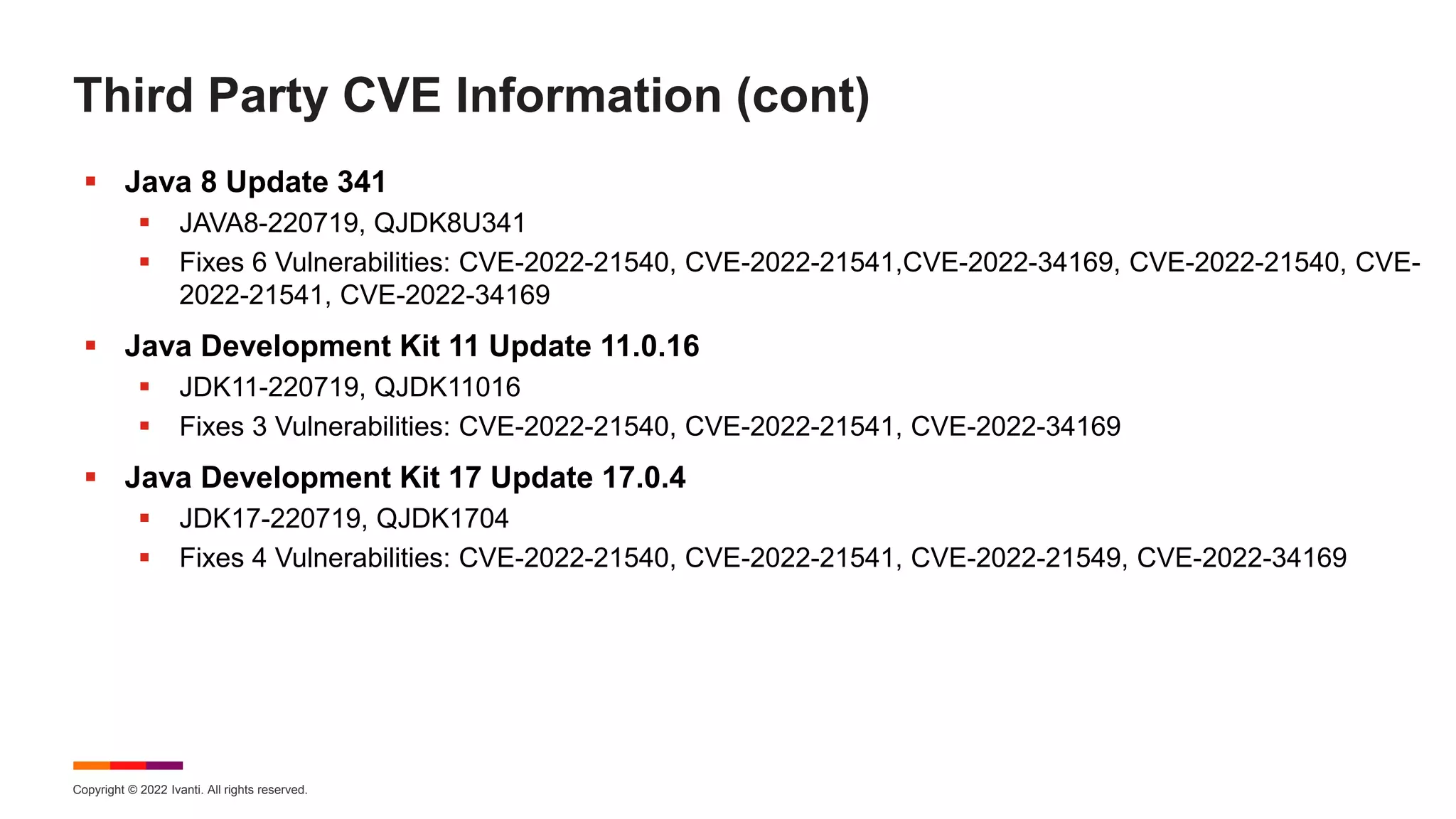
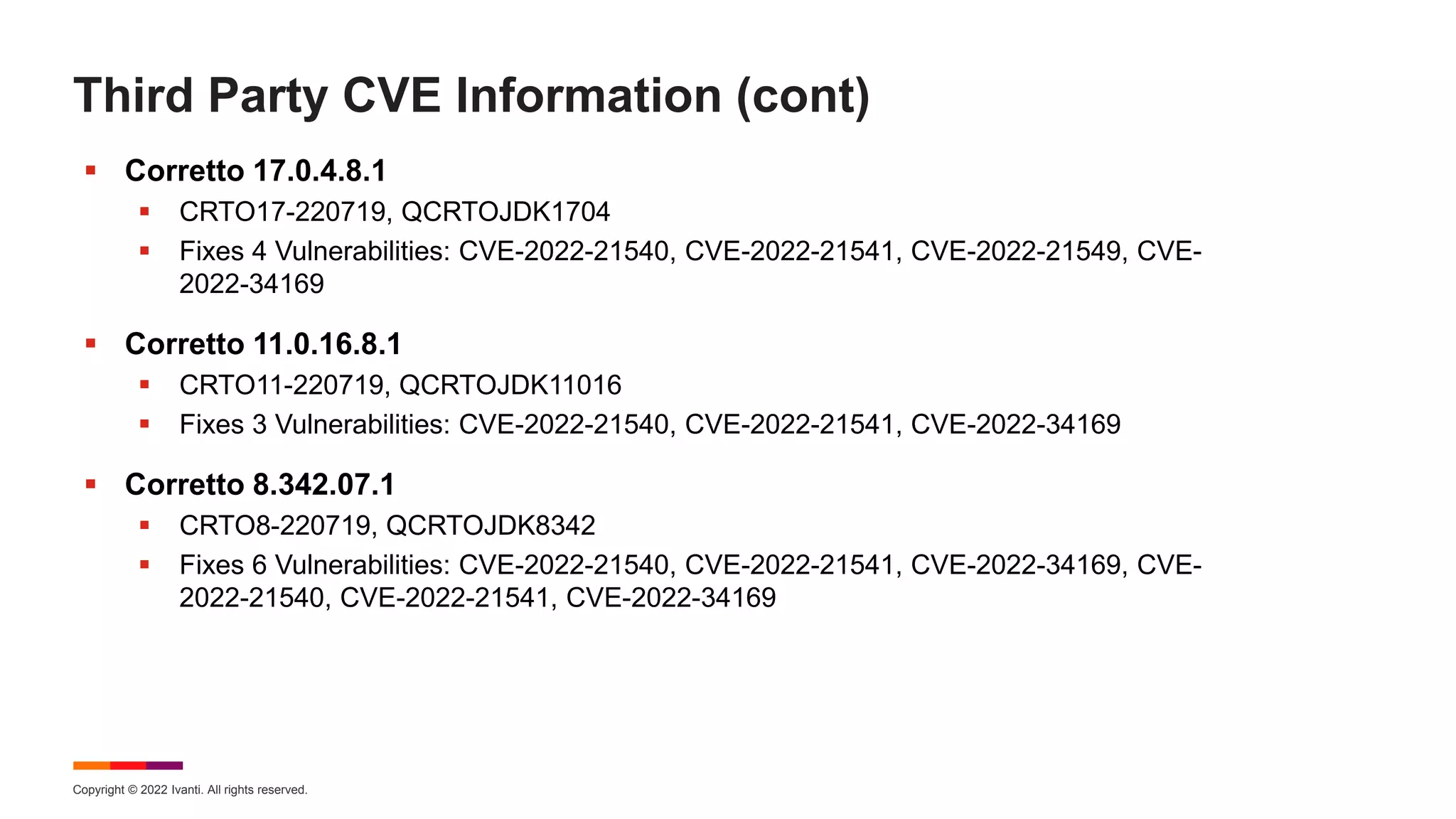
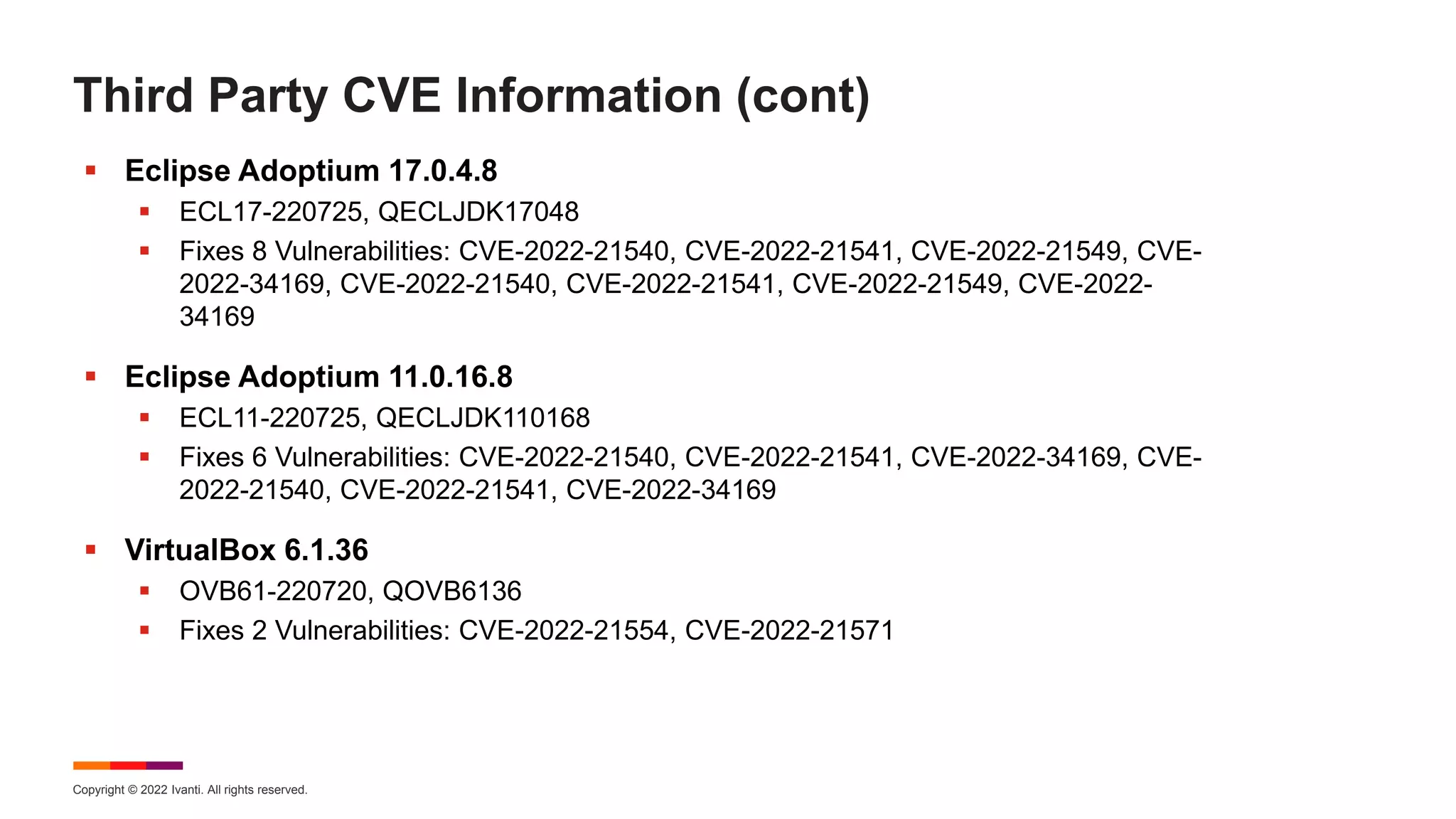
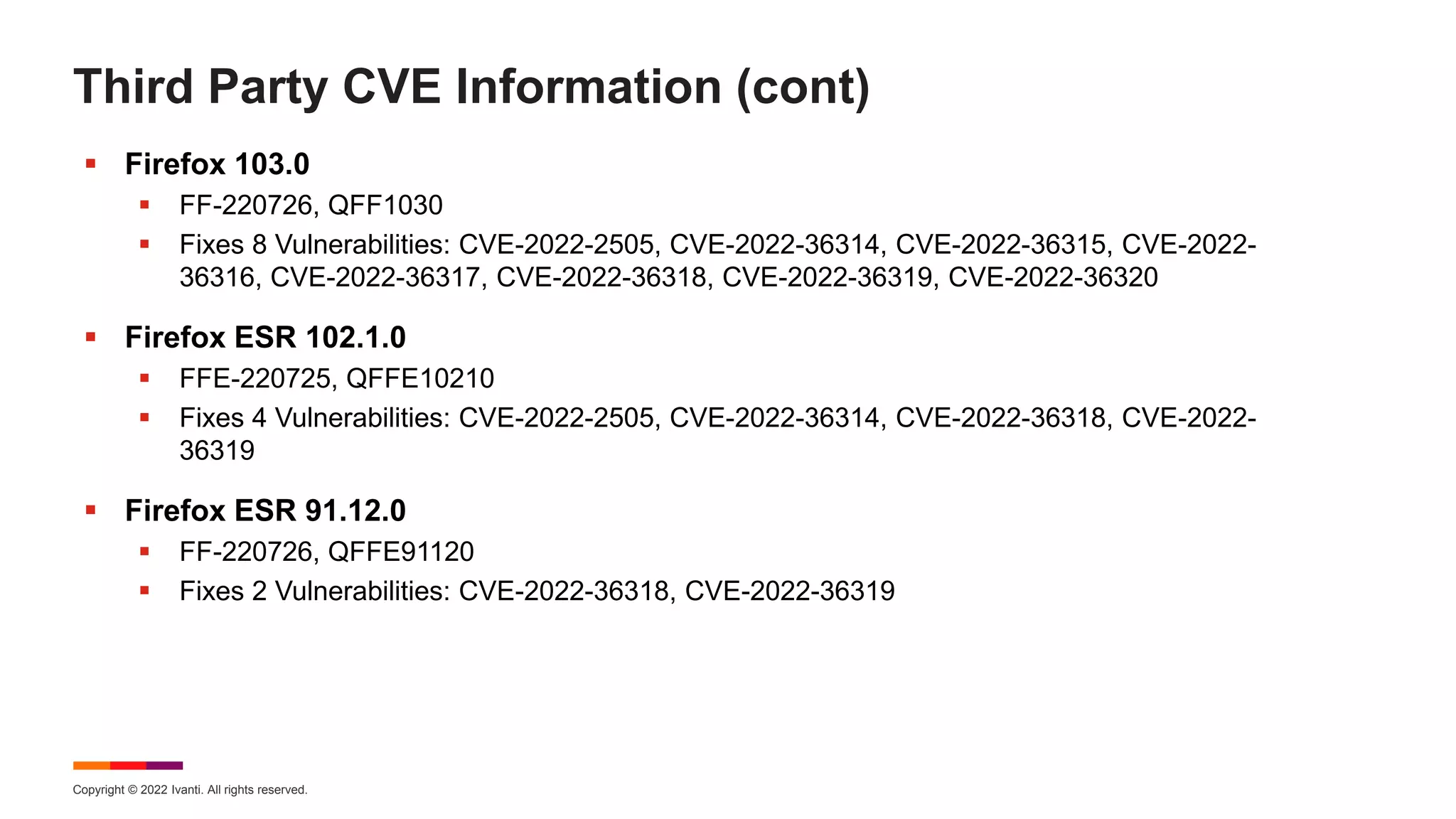
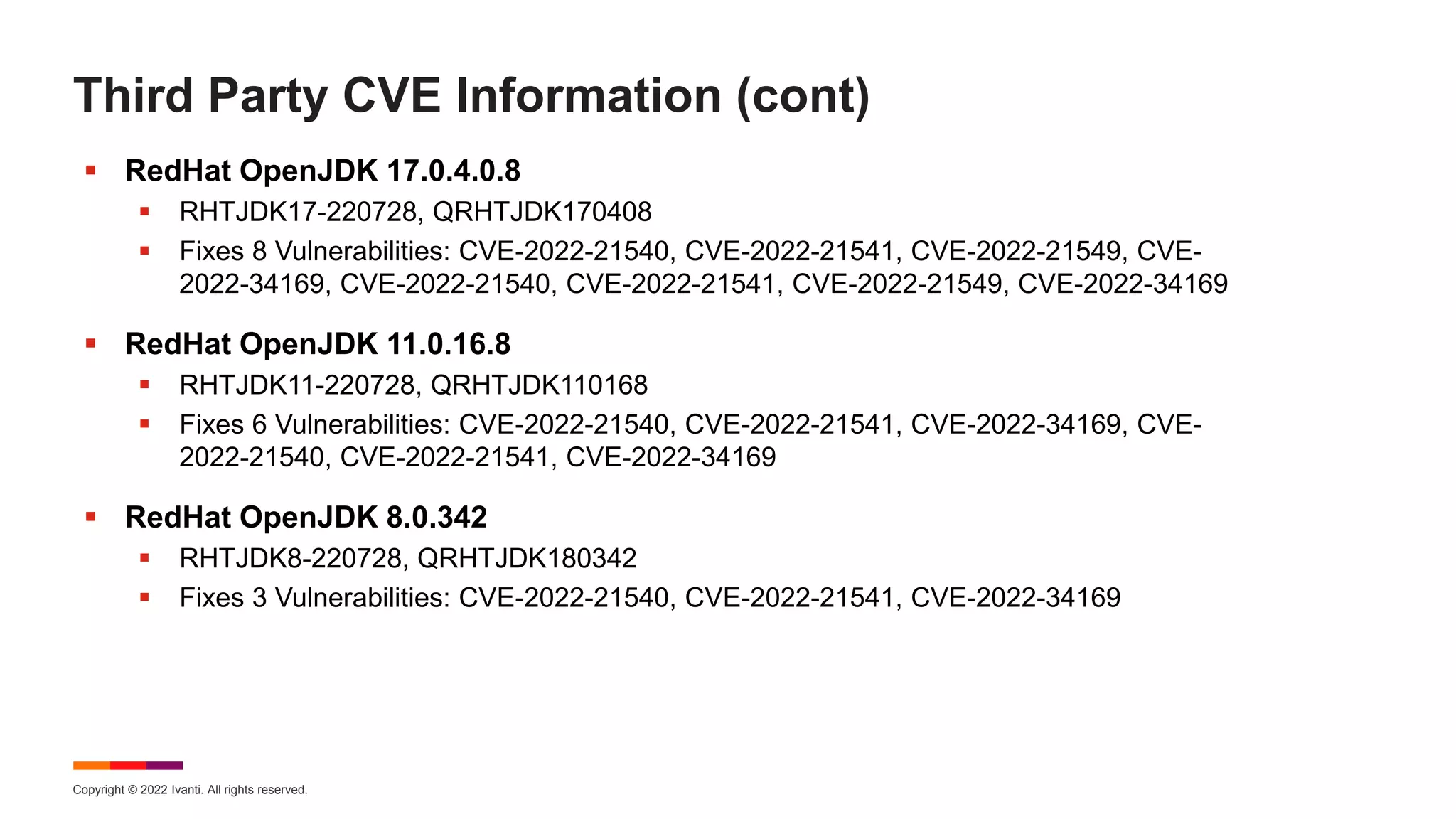
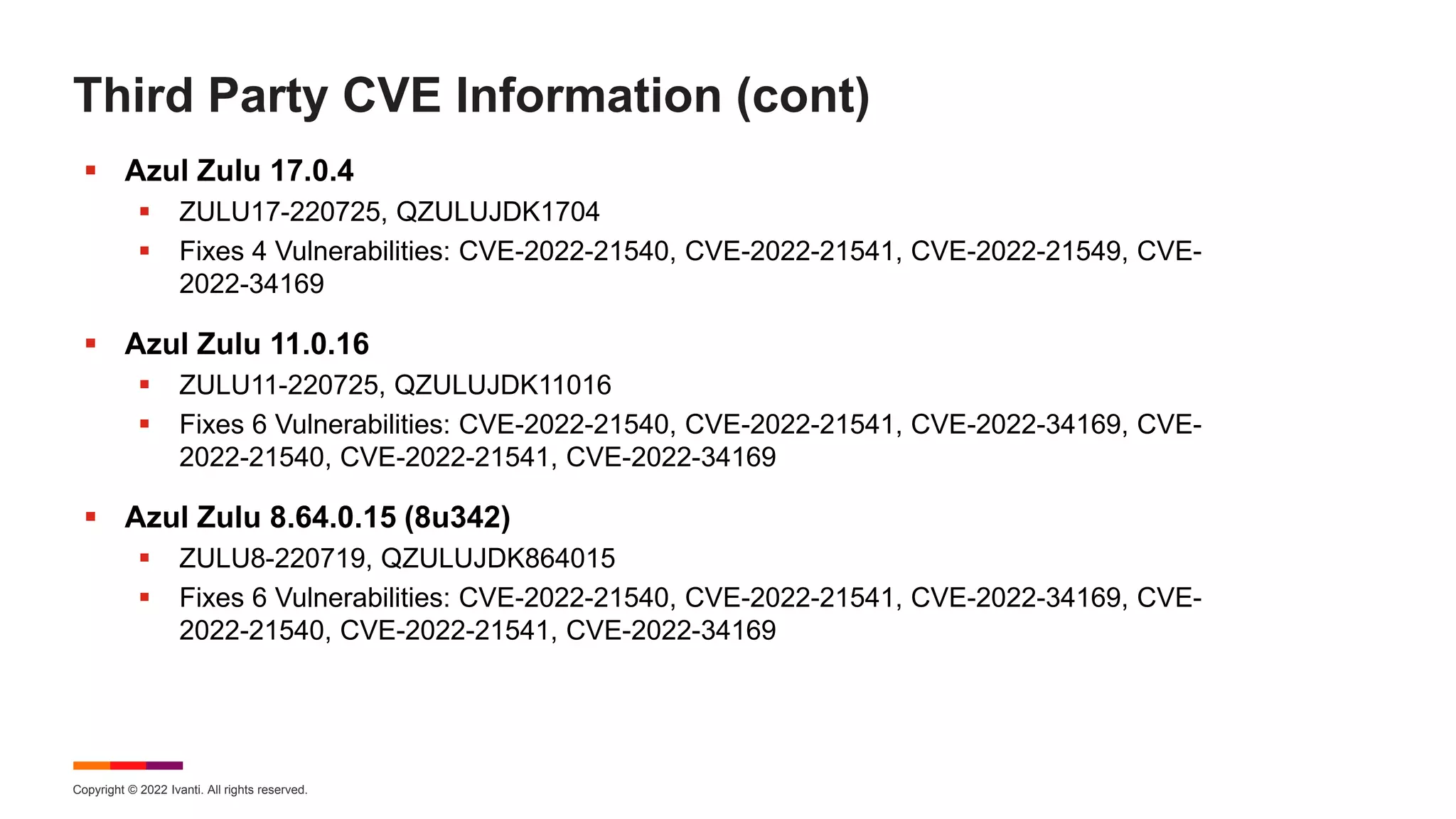
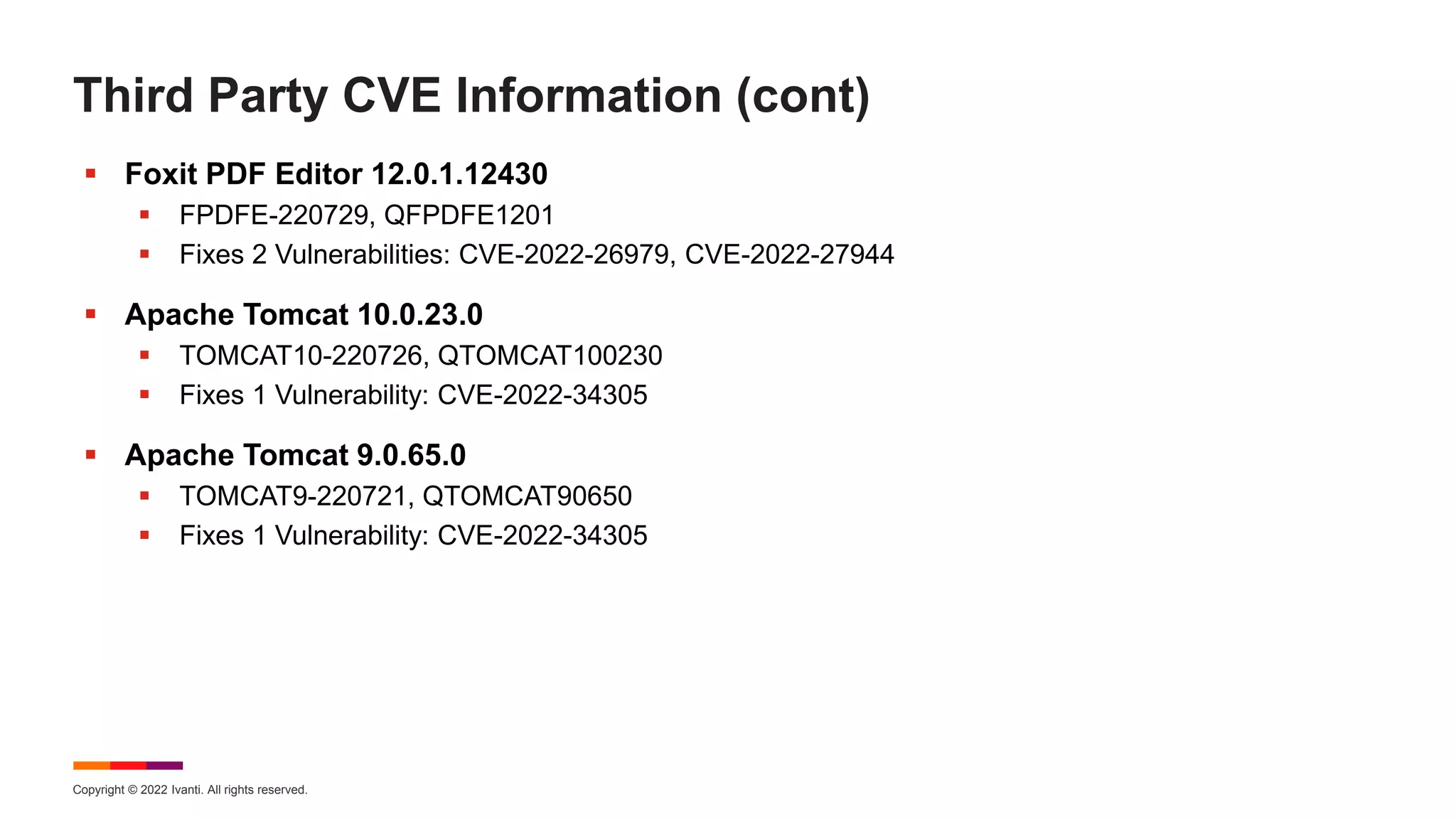
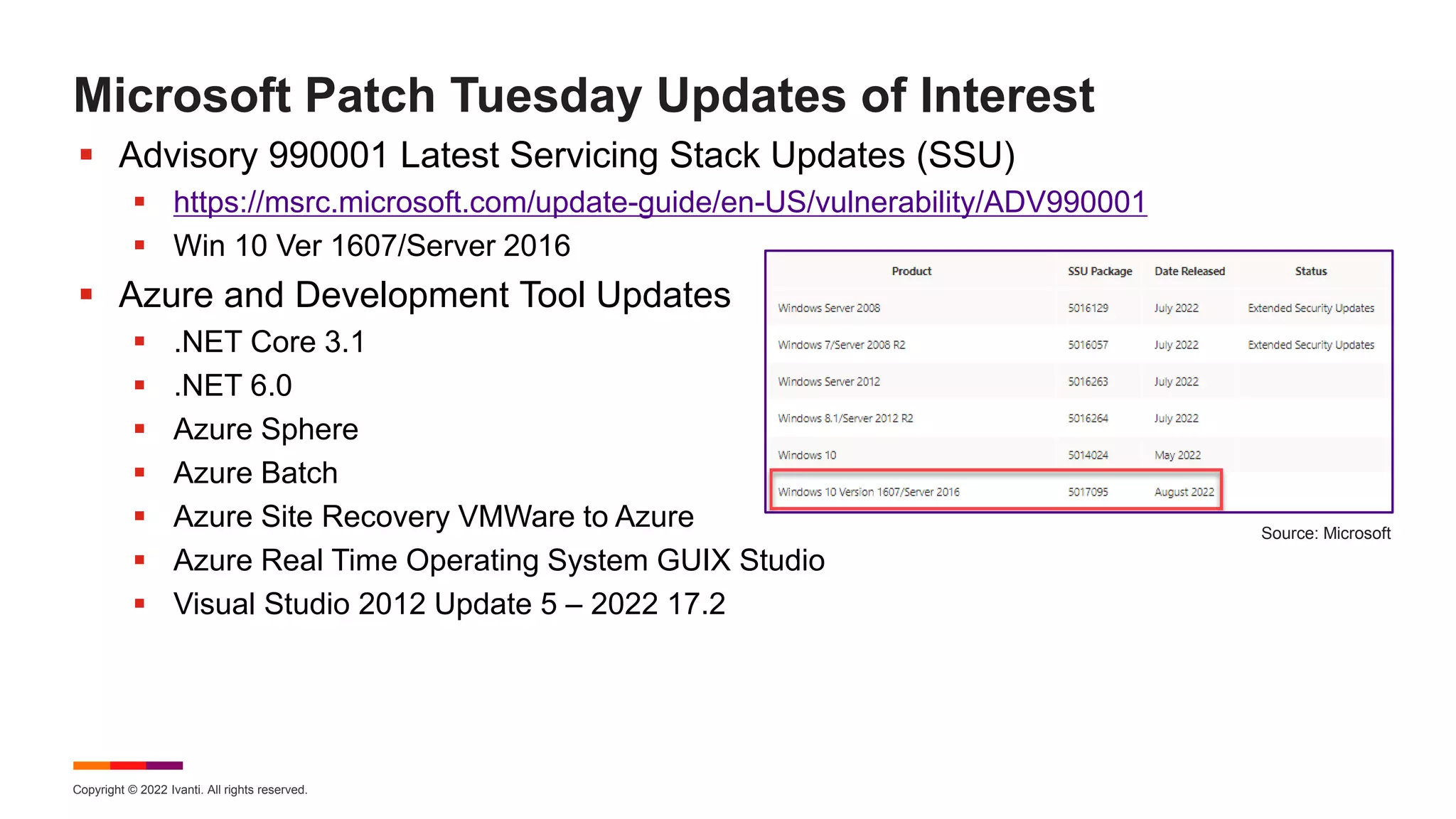
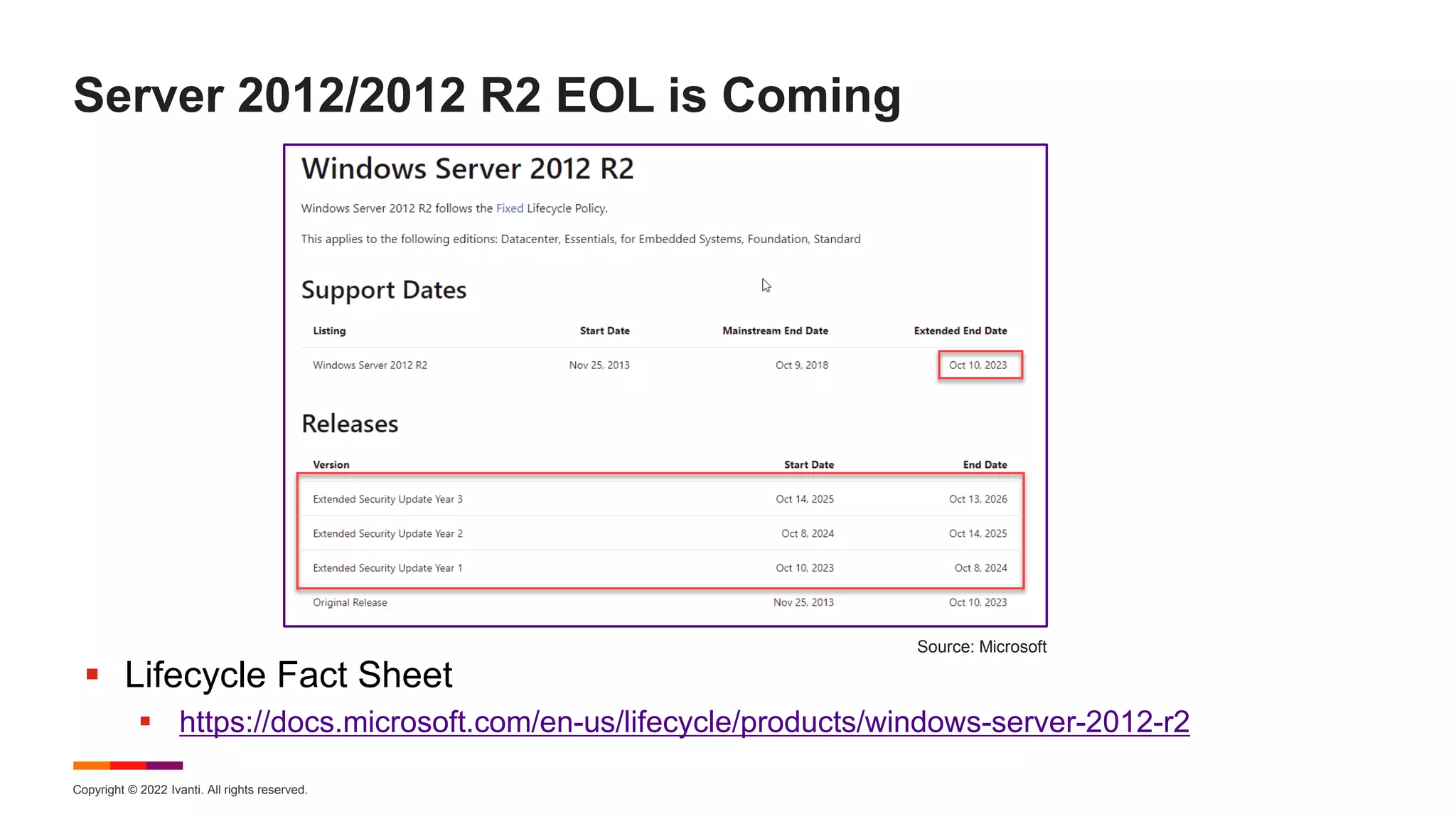
The August 2022 Patch Tuesday webinar presented by Chris Goettl and Todd Schell detailed Microsoft's release of updates addressing 121 CVEs, including critical vulnerabilities in Windows and Exchange server that require specific resolution steps. Additionally, Adobe released updates for Acrobat and Reader, addressing various vulnerabilities, while the document highlighted important housekeeping items regarding the end of support for older server versions. The webinar also discussed known exploited vulnerabilities, security features, and updates for various Microsoft products.








![Copyright © 2022 Ivanti. All rights reserved.
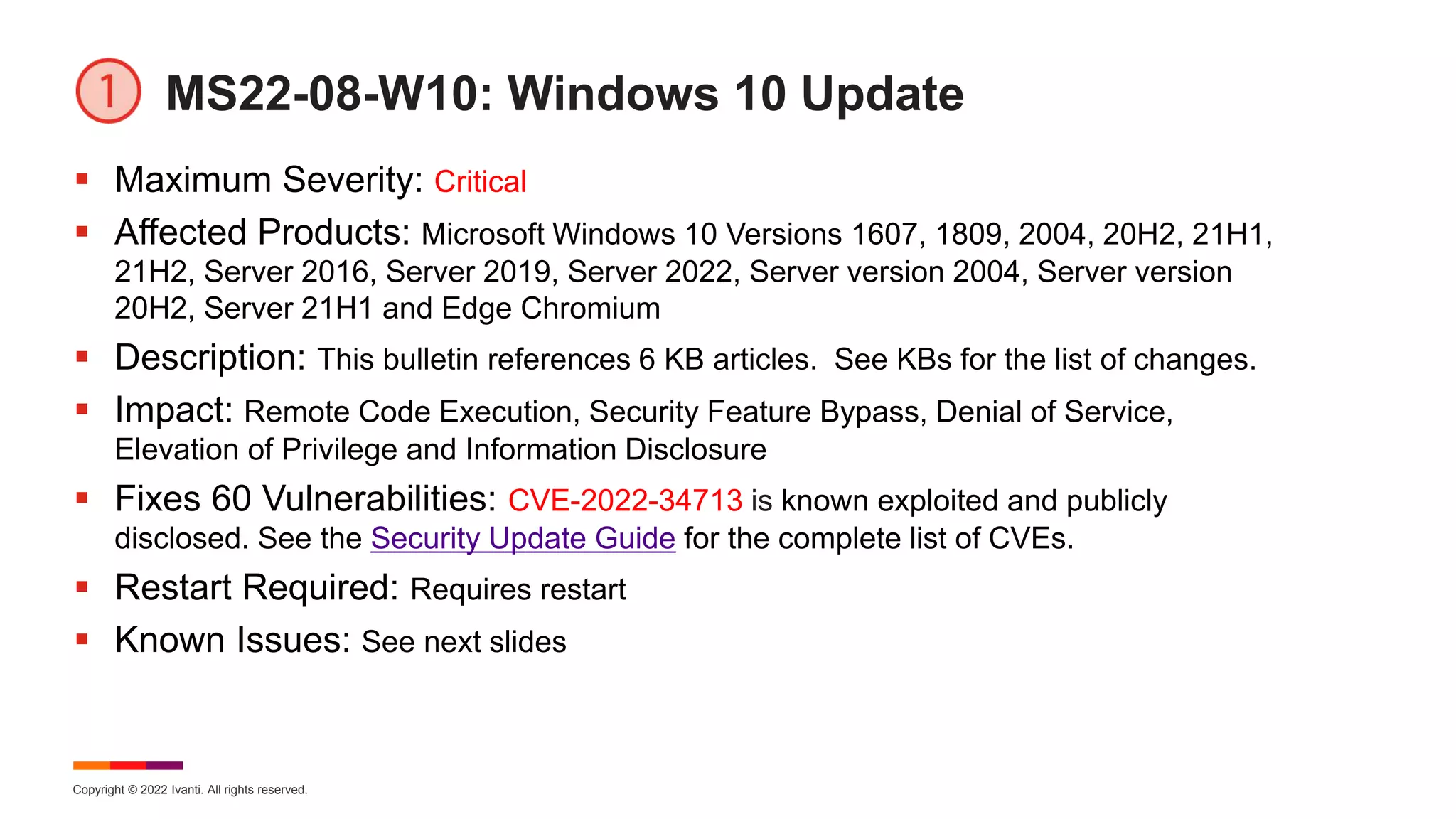
August Known Issues for Windows 11
KB 5016629 – Windows 11
[IE Mode] After installing this update, IE mode tabs in Microsoft Edge might stop
responding when a site displays a modal dialog box. A modal dialog box is a form or
dialog box that requires the user to respond before continuing or interacting with other
portions of the webpage or app. Workaround: This issue is resolved using Known
Issue Rollback (KIR). See KB for link to Windows 11 (original release) KB 5014019
220624_22553 Known Issue Rollback. For enterprise-managed devices that have
installed an affected update and encountered this issue, they can resolve it by
installing and configuring the special Group Policy also provided in KB.
[XPS Viewer] After installing this update, XPS Viewer might be unable to open XML
Paper Specification (XPS) documents in some non-English languages, including some
Japanese and Chinese character encodings. This issue affects both XML Paper
Specification (XPS) and Open XML Paper Specification (OXPS) files. See KB for
more details. Workaround: None. Microsoft is working on a resolution.](https://image.slidesharecdn.com/august2022patchtuesday-220810164258-a97659f0/75/2022-August-Patch-Tuesday-18-2048.jpg)
![Copyright © 2022 Ivanti. All rights reserved.
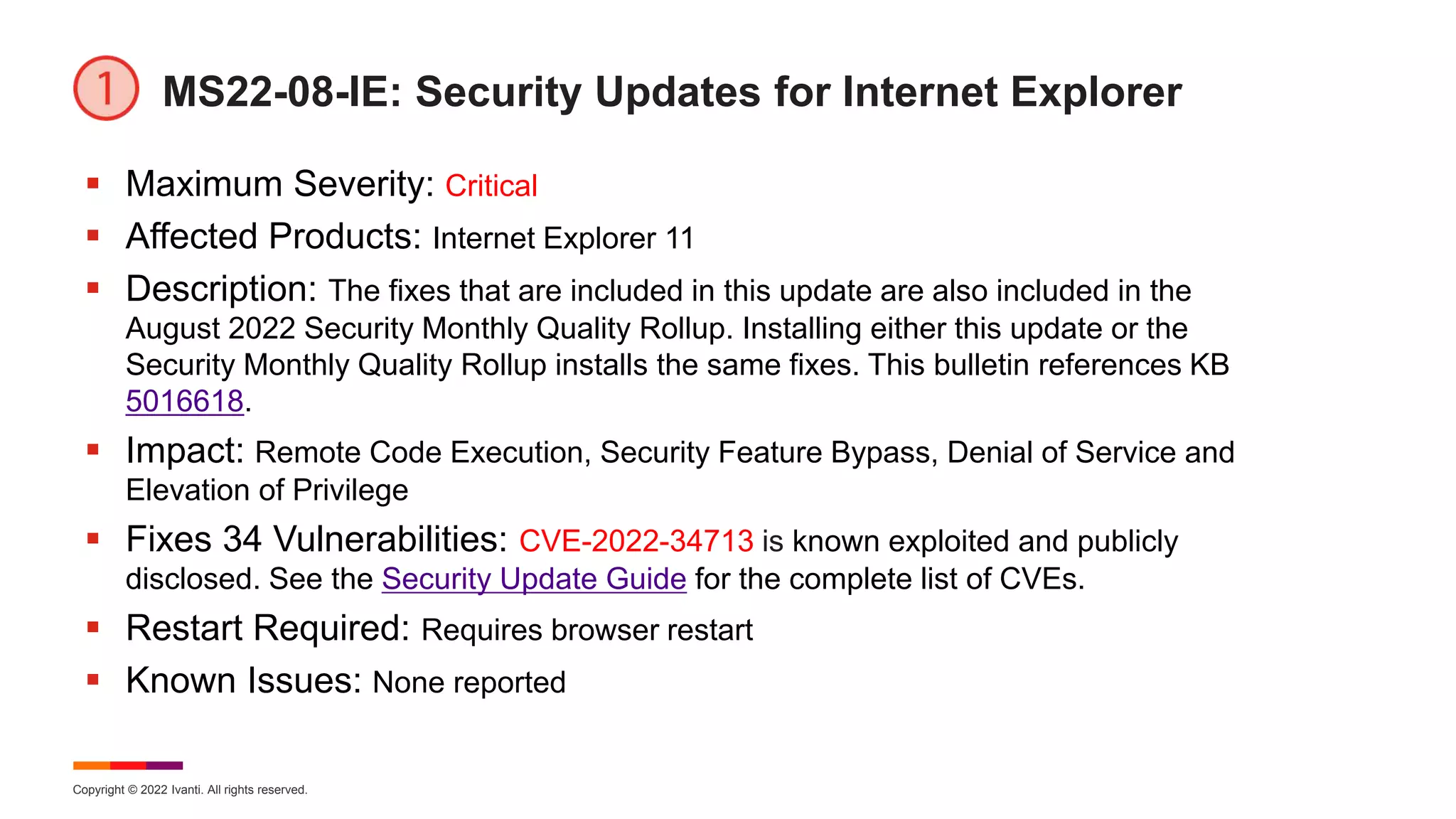
August Known Issues for Windows 10
KB 5016623 – Windows 10 Enterprise 2019 LTSC, Windows 10 IoT
Enterprise 2019 LTSC, Windows 10 IoT Core 2019 LTSC, Windows
Server 2019
[Asian Packs] After installing KB 4493509, devices with some Asian language
packs installed may receive the error, "0x800f0982 -
PSFX_E_MATCHING_COMPONENT_NOT_FOUND.“ Workaround: Uninstall
and reinstall any recently added language packs or select Check for Updates and
install the April 2019 Cumulative Update. See KB for more recovery details.
Microsoft is working on a resolution.
[Cluster Update] After installing KB 5001342 or later, the Cluster Service might fail
to start because a Cluster Network Driver is not found. Workaround: This issue
occurs because of an update to the PnP class drivers used by this service. After
about 20 minutes, you should be able to restart your device and not encounter this
issue. For more information about the specific errors, cause, and workaround for
this issue, please see KB 5003571.](https://image.slidesharecdn.com/august2022patchtuesday-220810164258-a97659f0/75/2022-August-Patch-Tuesday-20-2048.jpg)
![Copyright © 2022 Ivanti. All rights reserved.
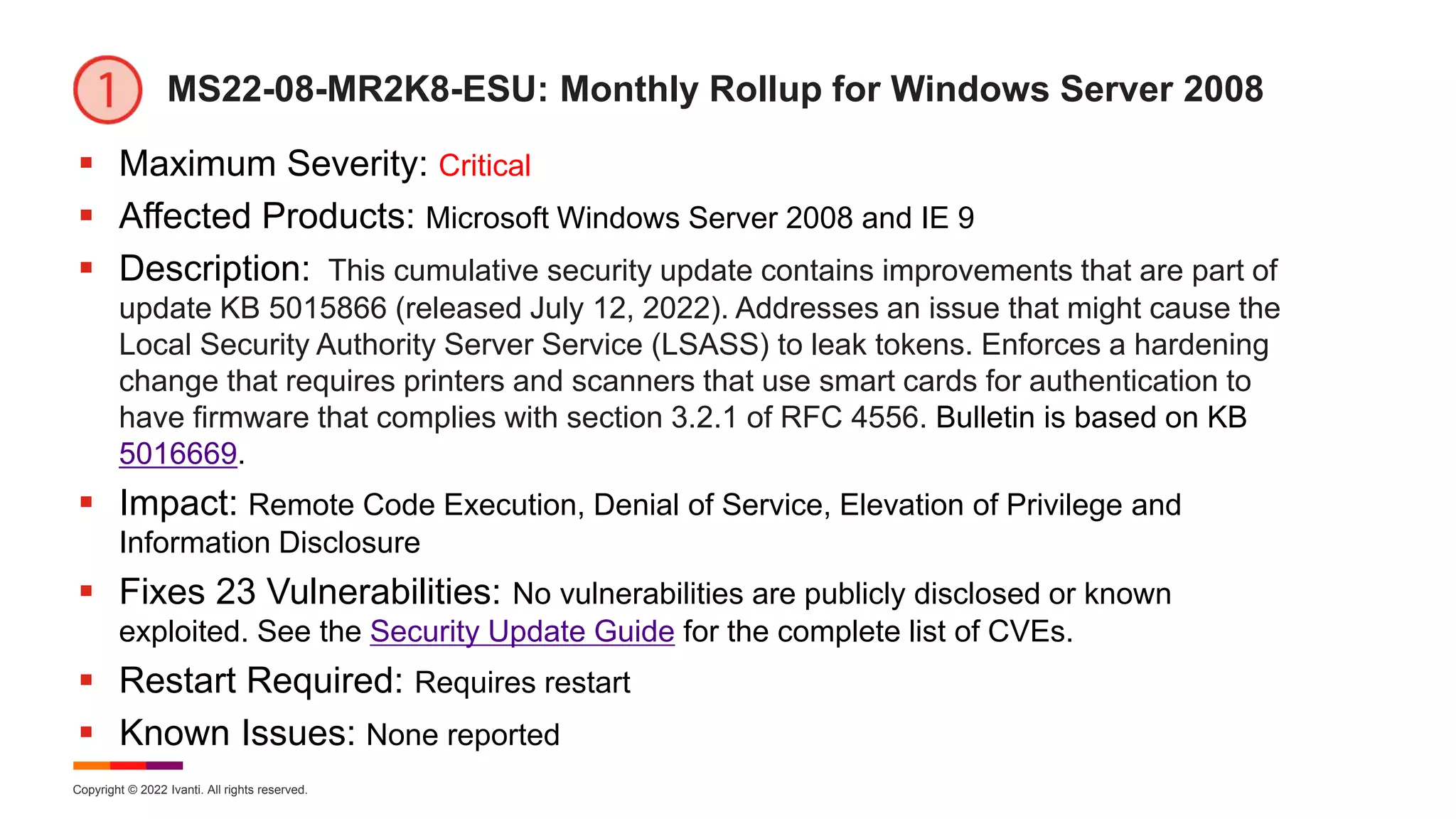
August Known Issues for Windows 10 (cont)
KB 5016616 –Windows 10 version 20H2, Windows Server version 20H2,
Windows 10 version 21H1
[Edge Removed] Devices with Windows installations created from custom offline
media or custom ISO image might have Microsoft Edge Legacy removed by this
update, but not automatically replaced by the new Microsoft Edge. Devices that
connect directly to Windows Update to receive updates are not affected.
Workaround: Slipstream the SSU released March 29, 2021 or later into the custom
offline media or ISO image before slipstreaming the LCU. See KB for details.
[Printer Copy] Reports of duplicate copies of printers installed on a device
(commonly with a similar name and the suffix "Copy1"), and applications which refer
to the printer by a specific name cannot print. Normal printer usage might be
interrupted, resulting in failure of printing operations. Workaround: Review printer
settings and adjust as needed – remove, rename, re-install, etc. See KB for details.
[IE Mode]
[XPS Viewer]](https://image.slidesharecdn.com/august2022patchtuesday-220810164258-a97659f0/75/2022-August-Patch-Tuesday-21-2048.jpg)
![Copyright © 2022 Ivanti. All rights reserved.
August Known Issues for Windows 10 (cont)
KB 5016627 – Windows Server 2022
[IE Mode]](https://image.slidesharecdn.com/august2022patchtuesday-220810164258-a97659f0/75/2022-August-Patch-Tuesday-22-2048.jpg)
![Copyright © 2022 Ivanti. All rights reserved.
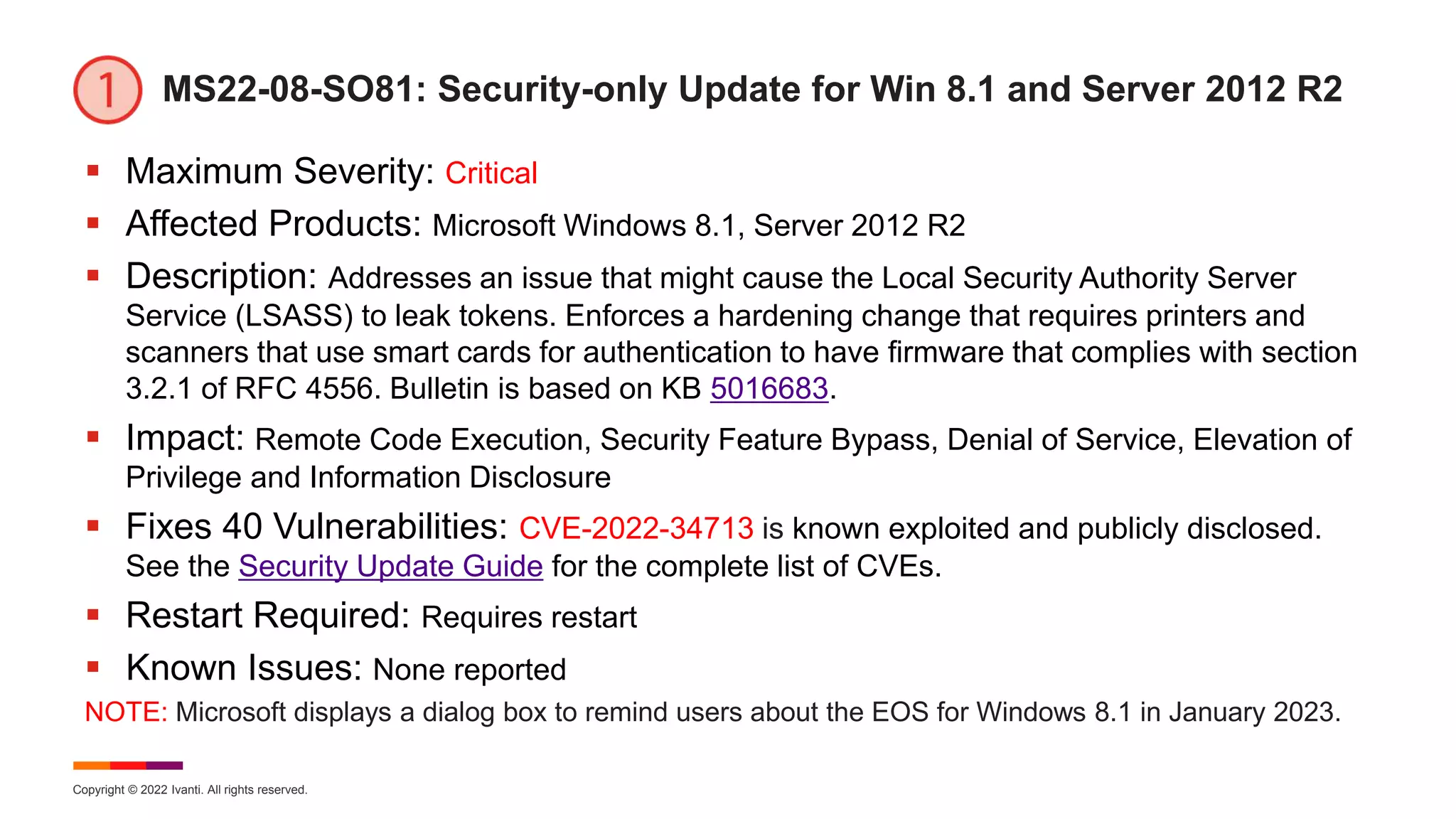
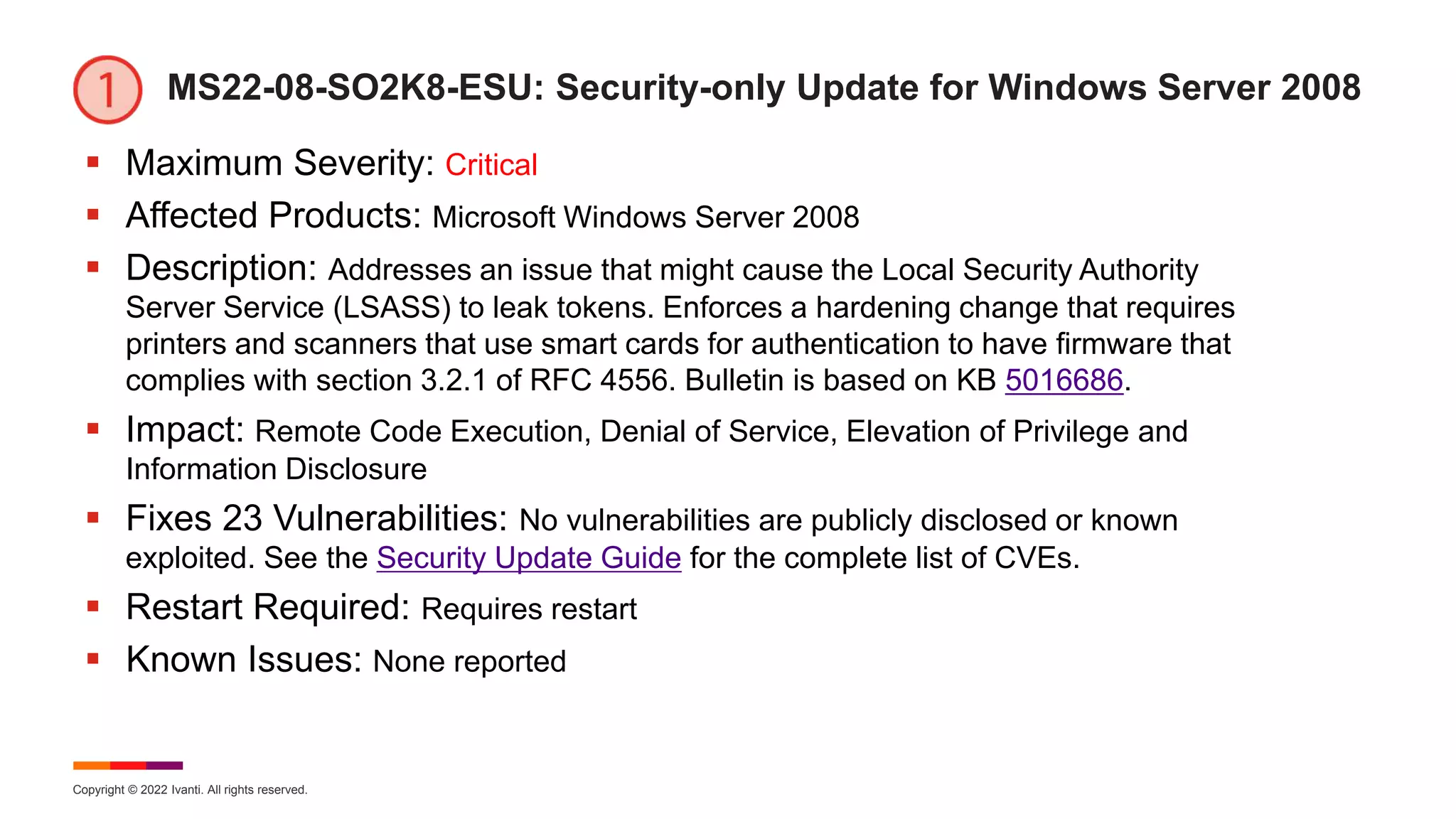
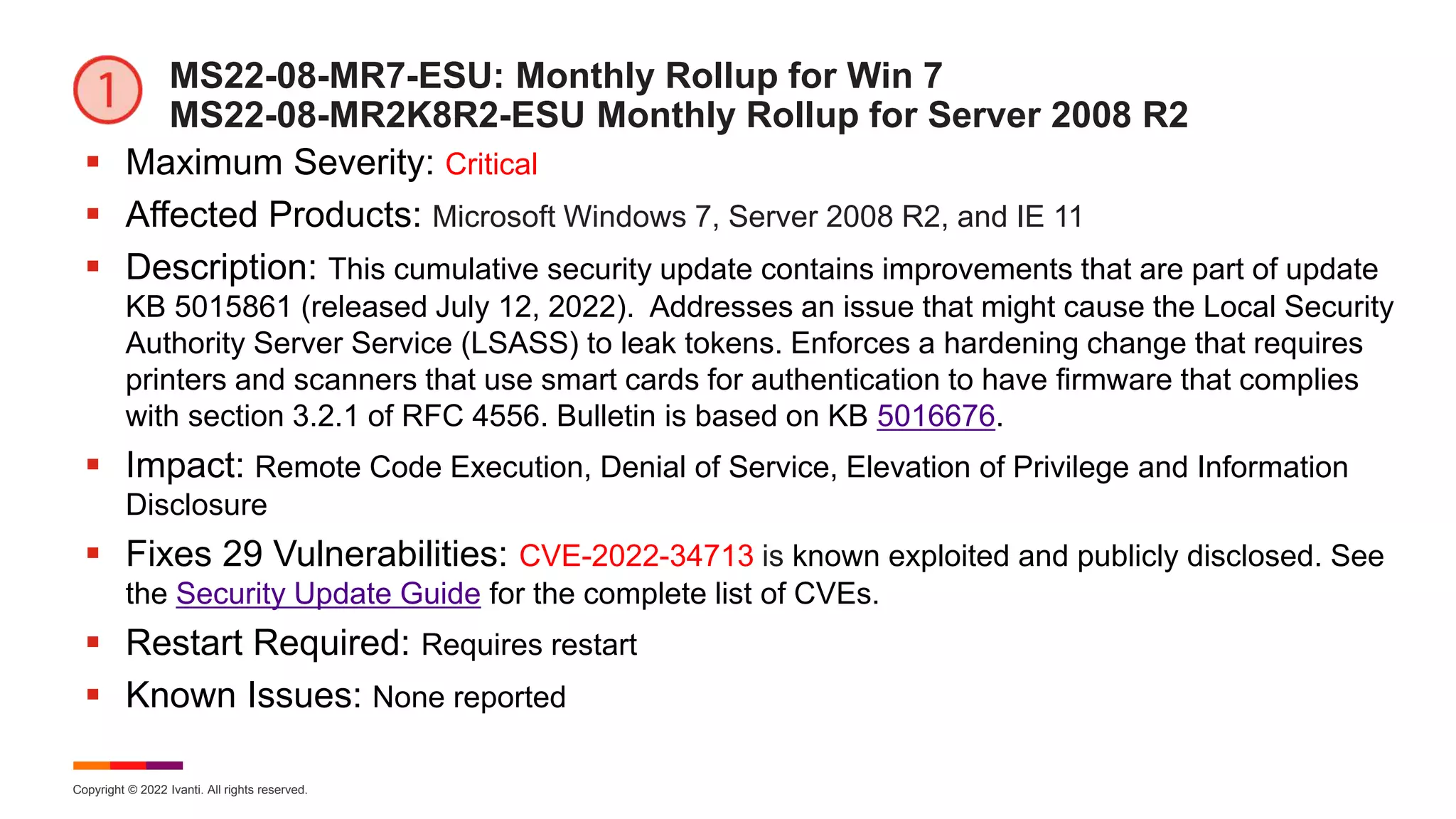
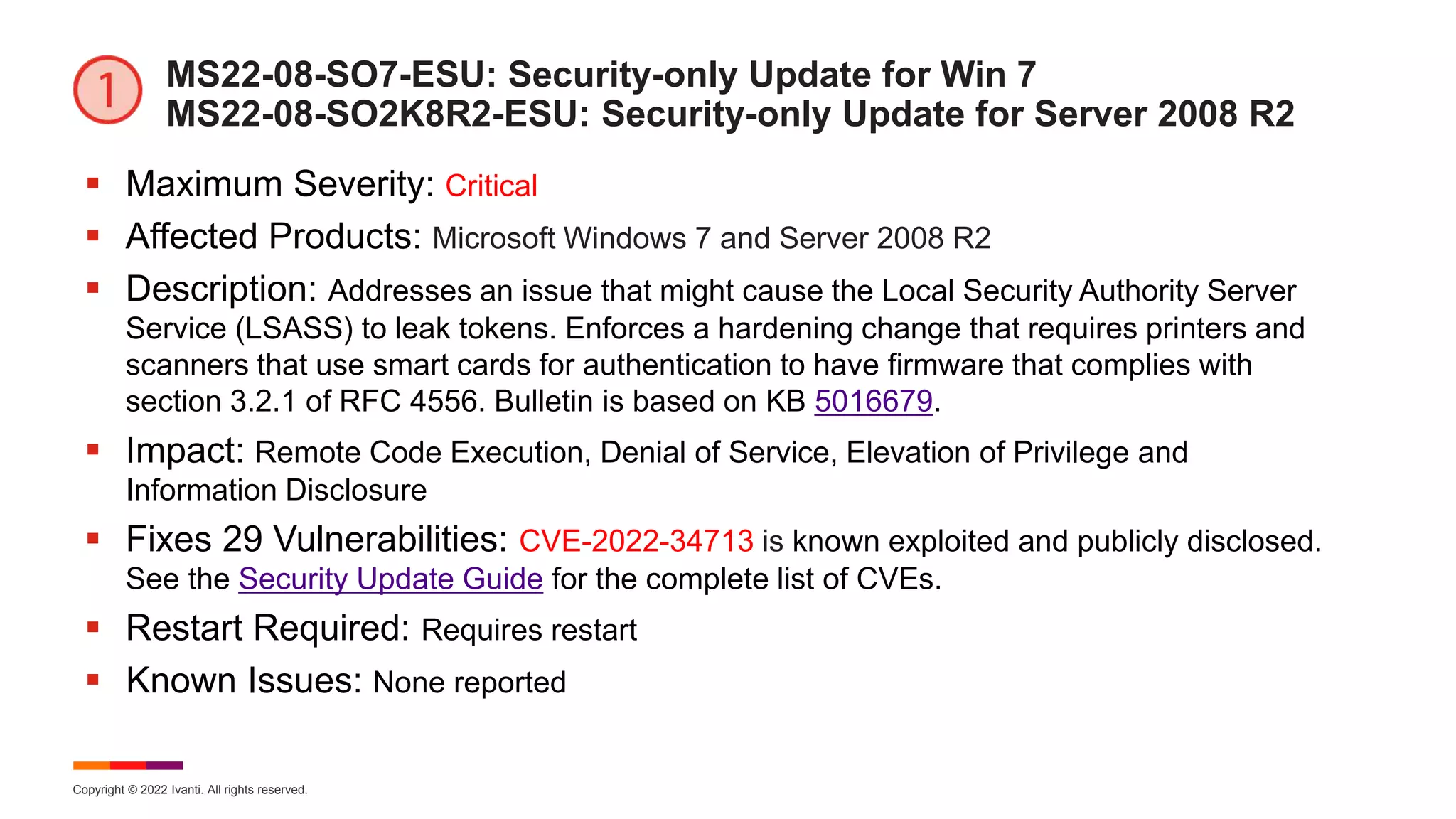
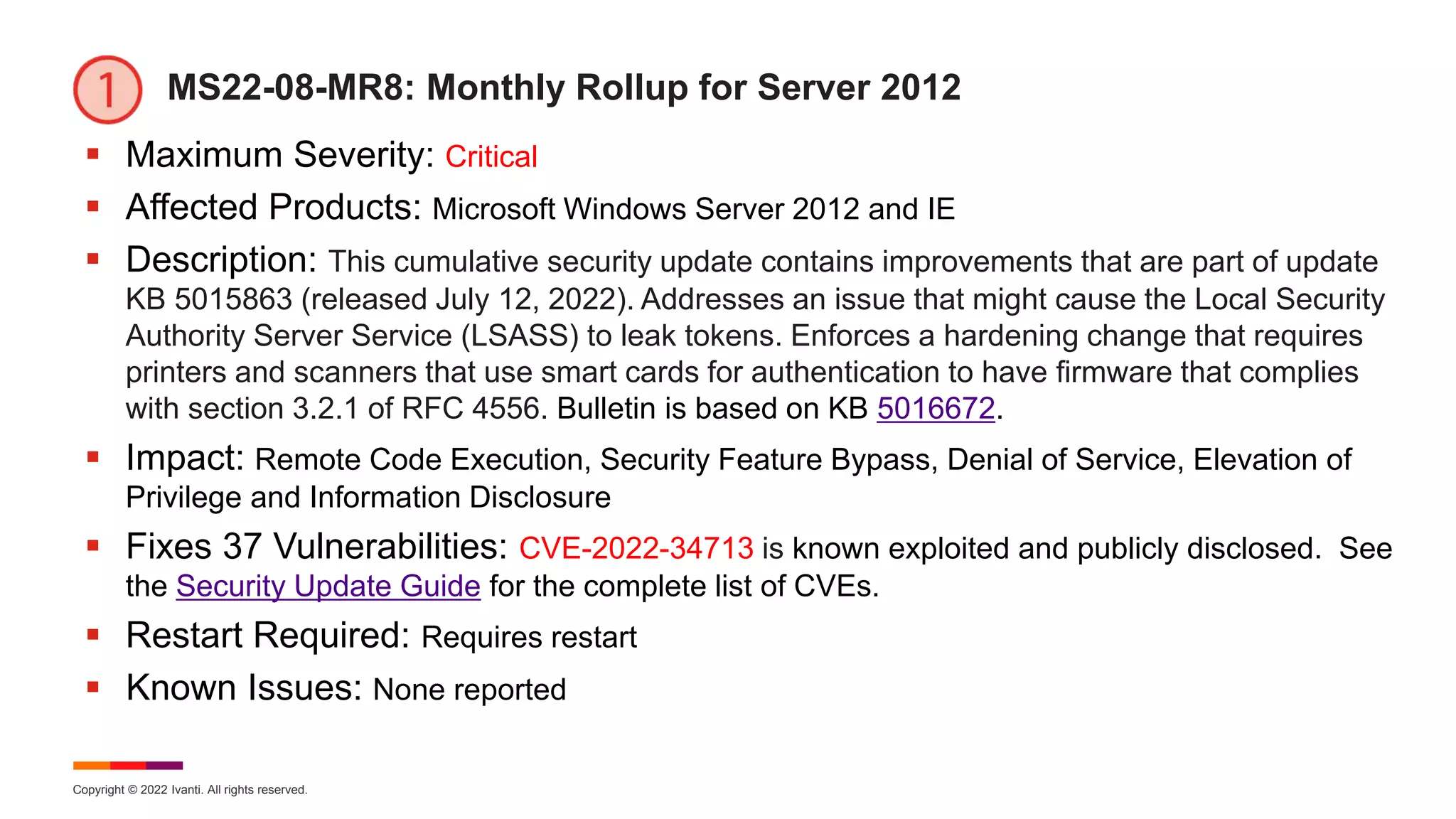
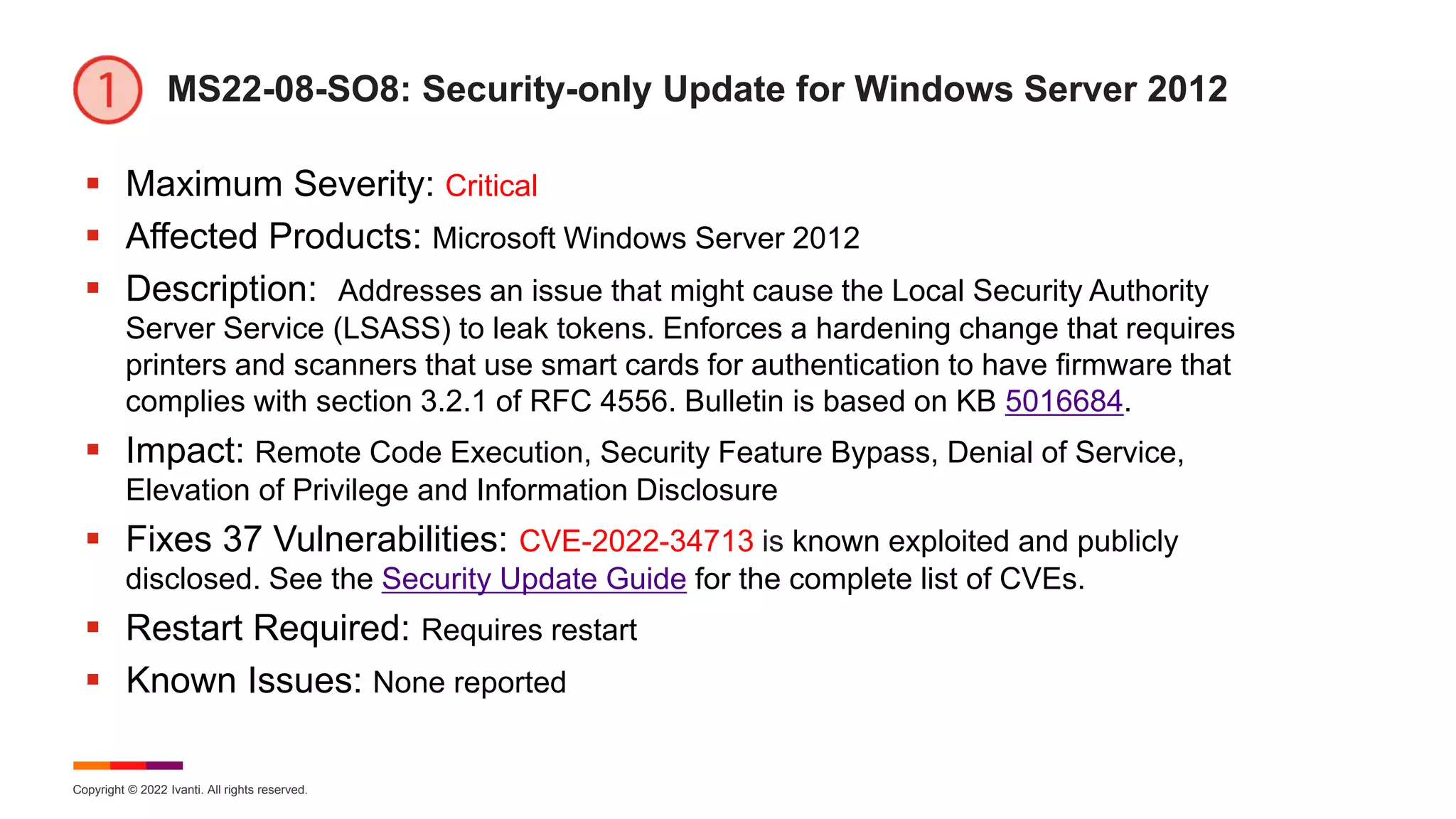
MS22-08-MR81: Monthly Rollup for Win 8.1 and Server 2012 R2
Maximum Severity: Critical
Affected Products: Microsoft Windows 8.1, Server 2012 R2, and IE
Description: This cumulative security update includes improvements that are part of update
KB 5015874 (released July 12, 2022). Addresses an issue that might cause the Local Security
Authority Server Service (LSASS) to leak tokens. Enforces a hardening change that requires
printers and scanners that use smart cards for authentication to have firmware that complies
with section 3.2.1 of RFC 4556. Bulletin is based on KB 5016681.
Impact: Remote Code Execution, Security Feature Bypass, Denial of Service, Elevation of
Privilege and Information Disclosure
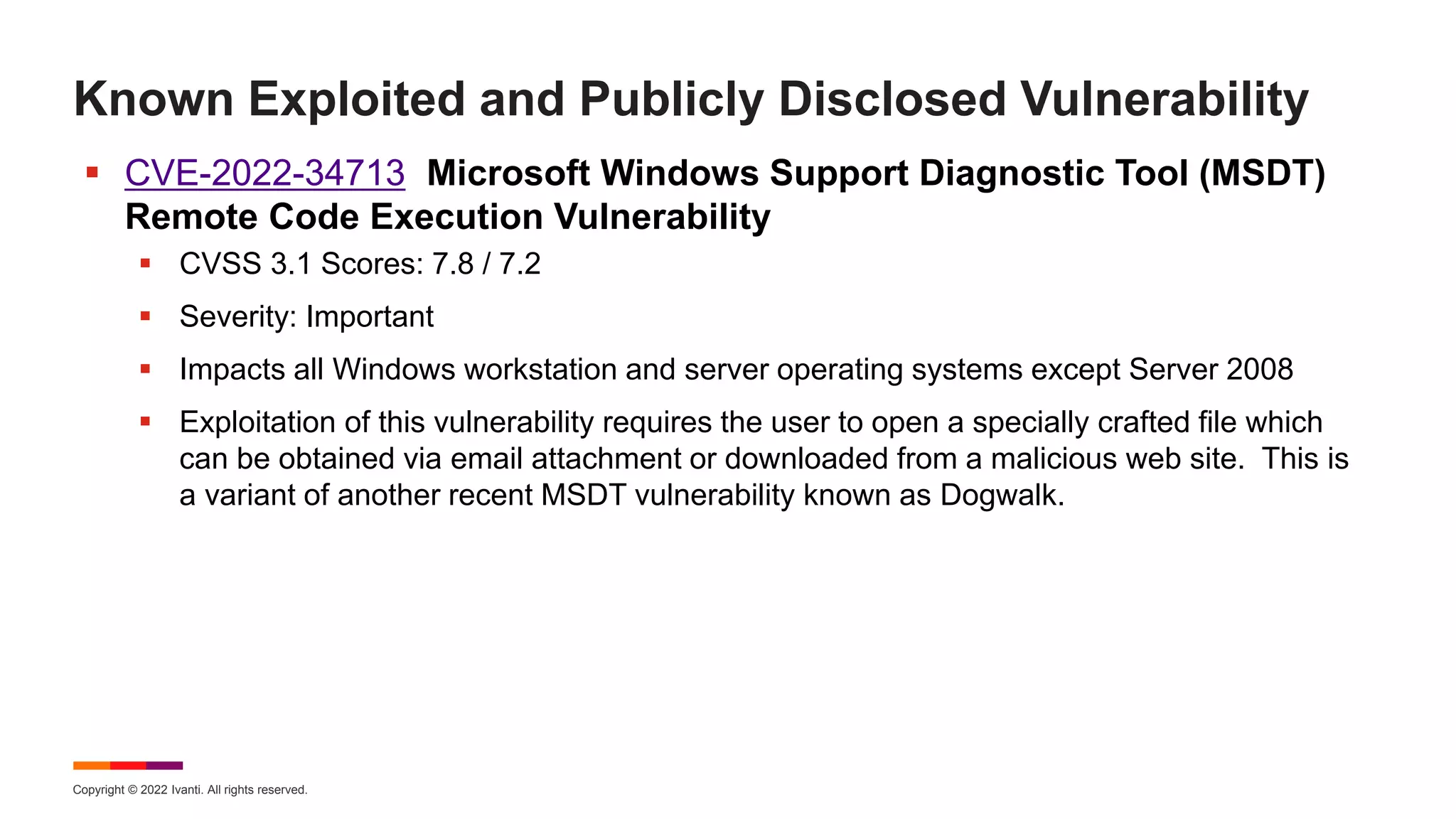
Fixes 40 Vulnerabilities: CVE-2022-34713 is known exploited and publicly disclosed. See
the Security Update Guide for the complete list of CVEs.
Restart Required: Requires restart
Known Issues: [File Rename]
NOTE: Microsoft displays a dialog box to remind users about the EOS for Windows 8.1 in January 2023.](https://image.slidesharecdn.com/august2022patchtuesday-220810164258-a97659f0/75/2022-August-Patch-Tuesday-30-2048.jpg)