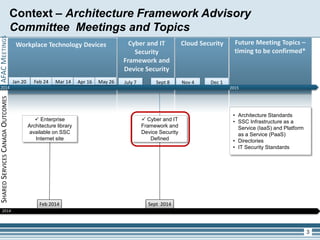
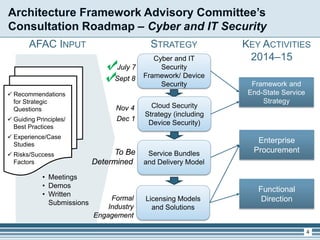
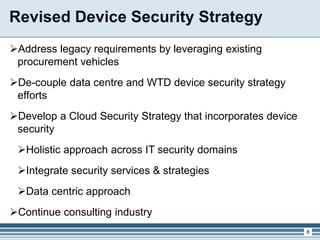
The presentation outlines the updates from the Architecture Framework Advisory Committee (AFAC) regarding cyber and IT security, focusing on device security and shared services within Canada's government. Key objectives include enhancing security services, supporting integration with cloud technologies, and establishing a framework for device security strategies. Upcoming steps involve further exploration of cloud security and soliciting feedback from AFAC members to inform future initiatives.