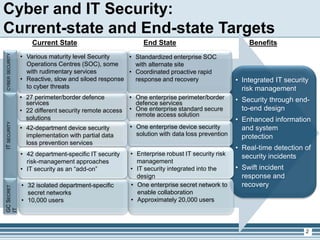
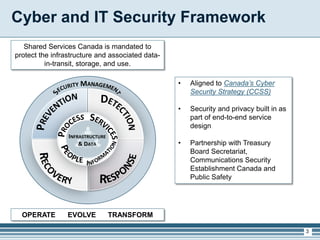
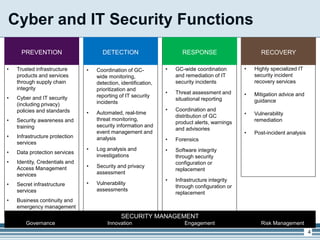
The presentation outlines Shared Services Canada's cyber and IT security framework, highlighting the importance of integrated risk management and enhanced protection measures for infrastructure and data. It details the current state of security solutions versus the targeted end state, emphasizing the need for unified systems and improved incident response capabilities. The discussion concludes with a focus on security principles, a gradual shift towards advanced security models, and next steps for implementation and governance.