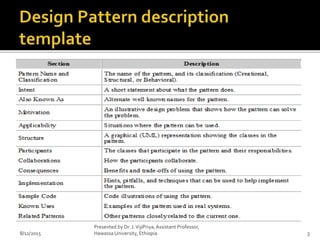
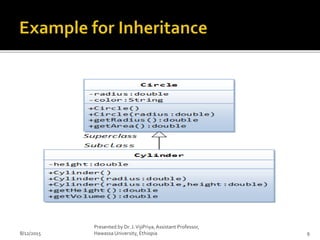
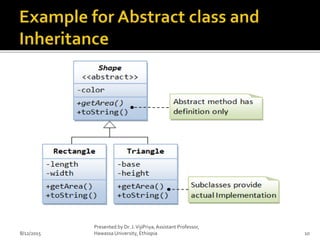
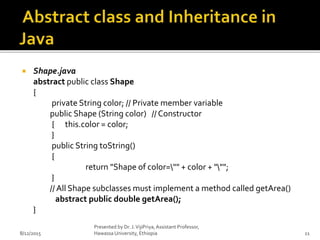
The document discusses key concepts in software design, including design patterns, inheritance, application programming interfaces (APIs), and version control. It defines design patterns as reusable solutions that aid in object-oriented programming and classifies them into creational, structural, and behavioral groups. Additionally, it highlights the importance of version control systems for collaborative project management, detailing their functions and types.