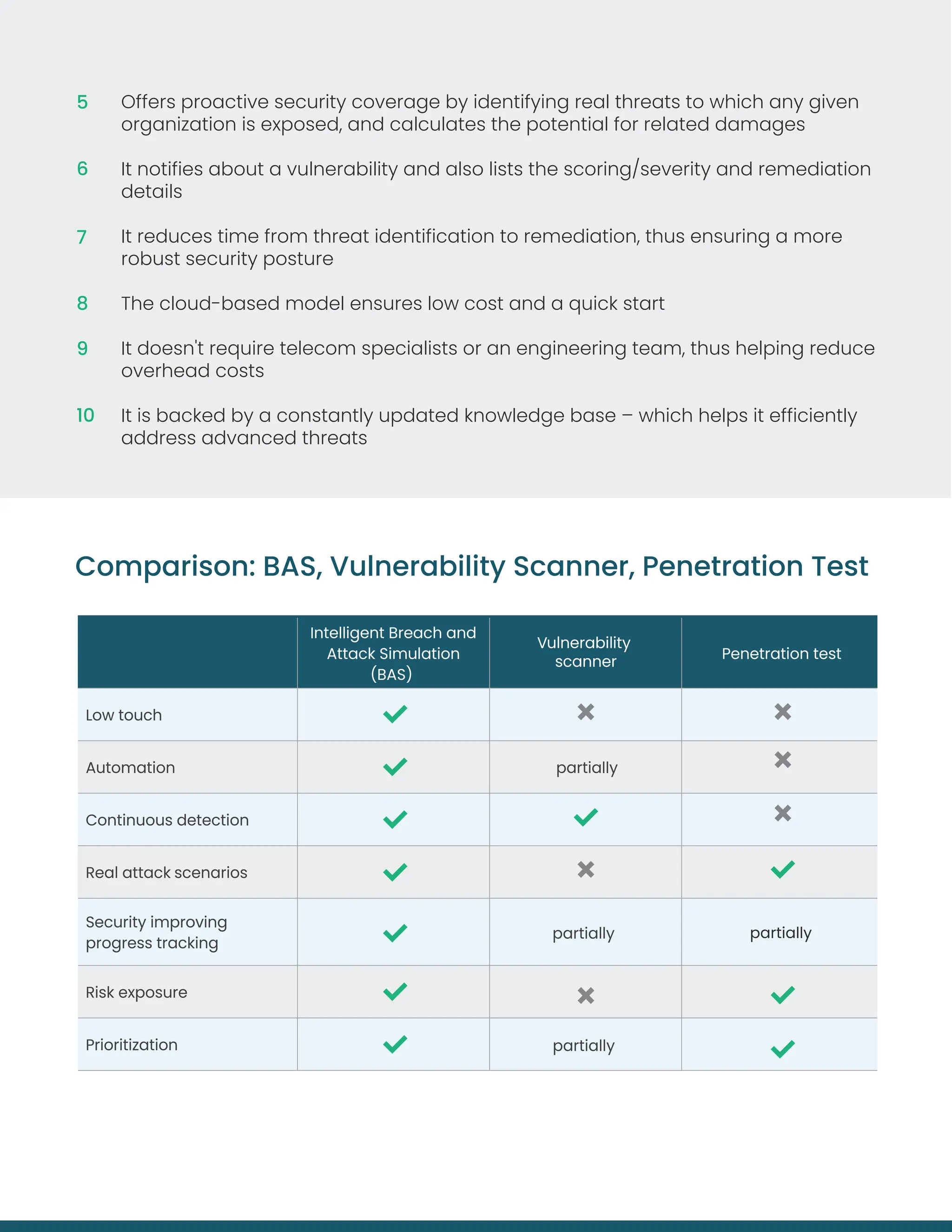
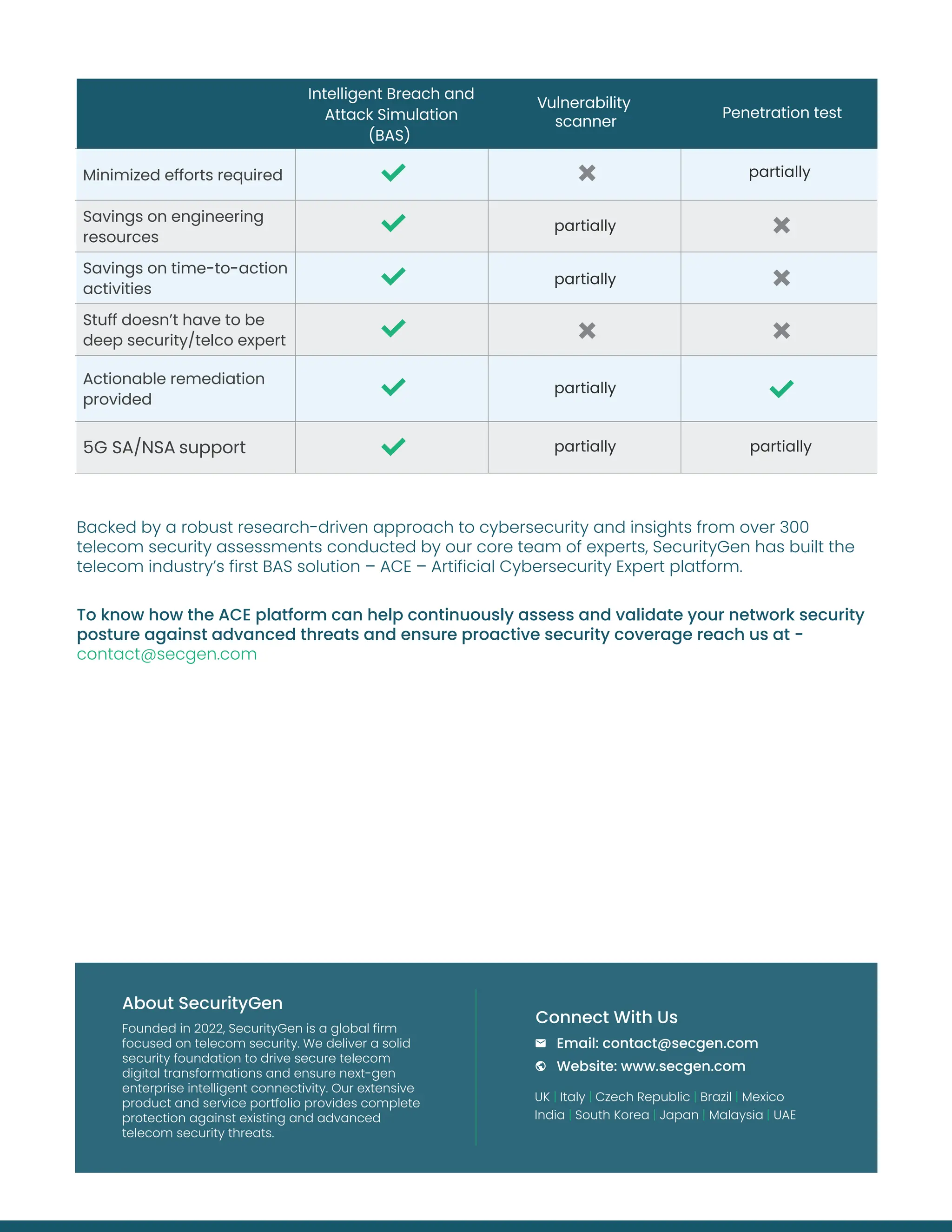
Cyberattacks present significant threats to the telecom industry, making it essential to assess security systems effectively. Traditional methods like penetration testing and vulnerability scans have limitations, such as infrequent assessments and failure to address unknown vulnerabilities. The breach and attack simulation (BAS) approach offers a solution by simulating real attack scenarios, providing continuous monitoring, and improving overall security posture with actionable insights.