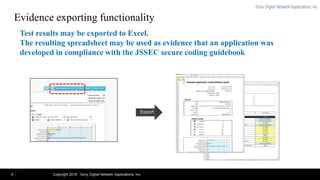
The document introduces Secure Coding Checker, a tool developed by Sony Digital Network Applications that identifies vulnerabilities in Android apps. It scans APK files to detect issues within minutes and provides guidance to help developers quickly fix problems. The tool analyzes apps and visually displays any vulnerabilities found. It suggests fixes and links to sample code. Secure Coding Checker helps development teams test apps and minimize pre-release bugs by allowing multiple scans. It is currently used by over 100 listed companies in Japan.