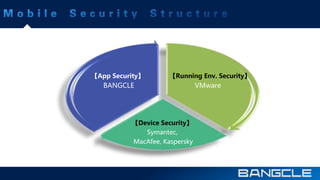
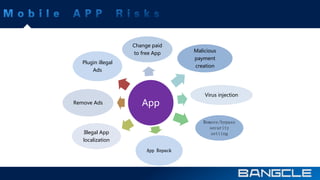
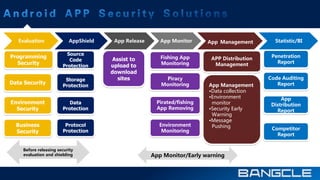
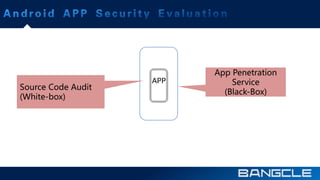
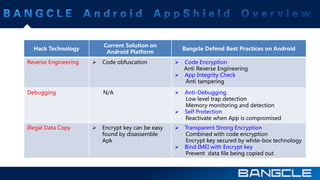
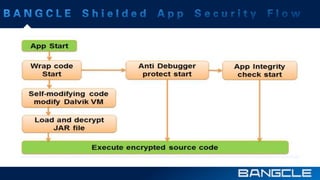
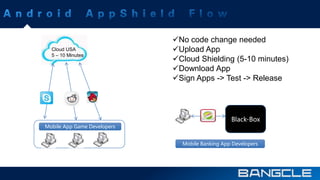
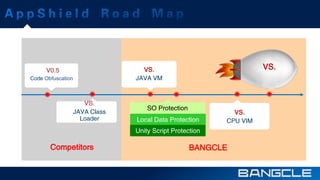
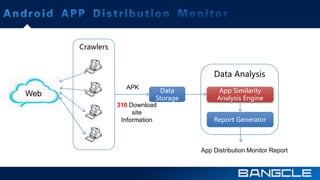
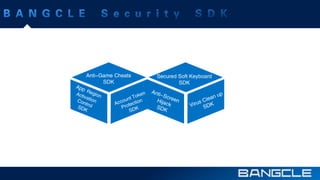
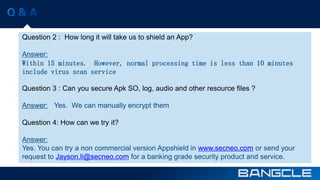
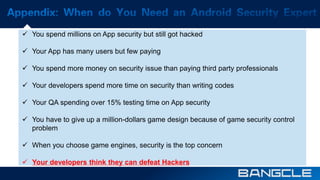
The document discusses mobile app security services provided by Bangcle and Secneo, detailing various solutions for app protection, including code obfuscation, encryption, and anti-reverse engineering techniques. It highlights performance impacts, implementation speed, and security challenges faced by developers, particularly in the gaming industry. Additional information about the company’s offerings and contact details for inquiries are also provided.