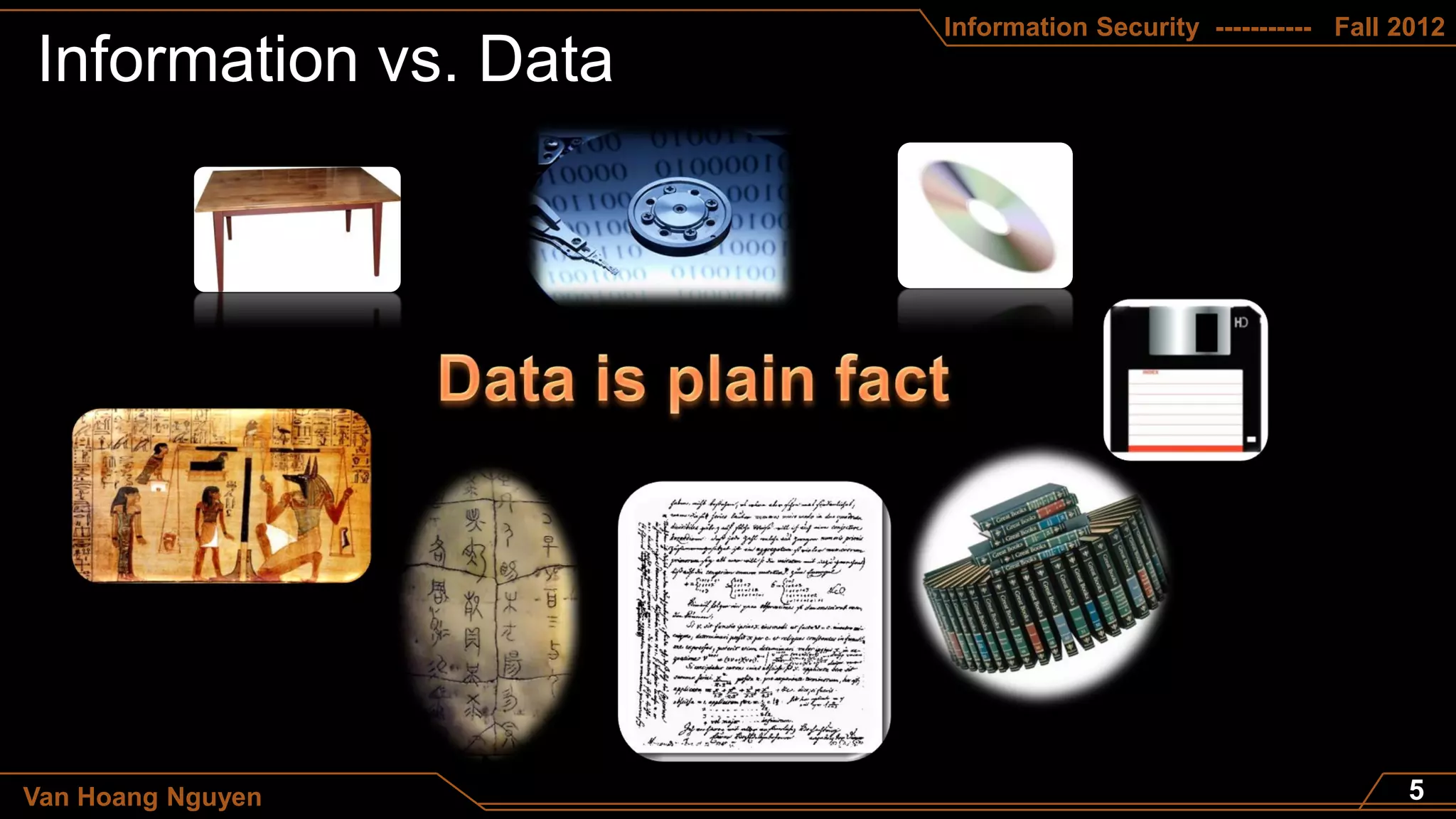
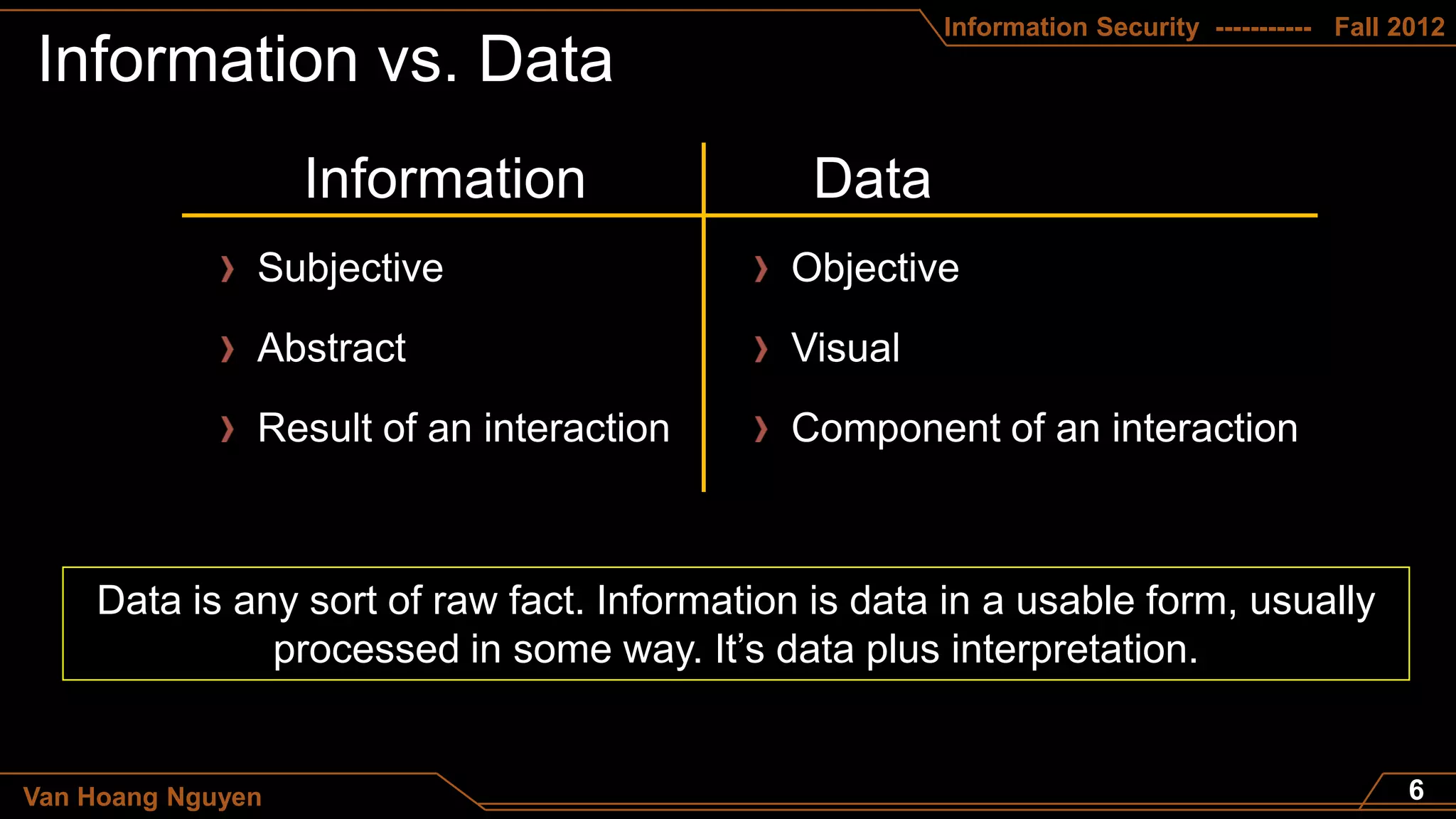
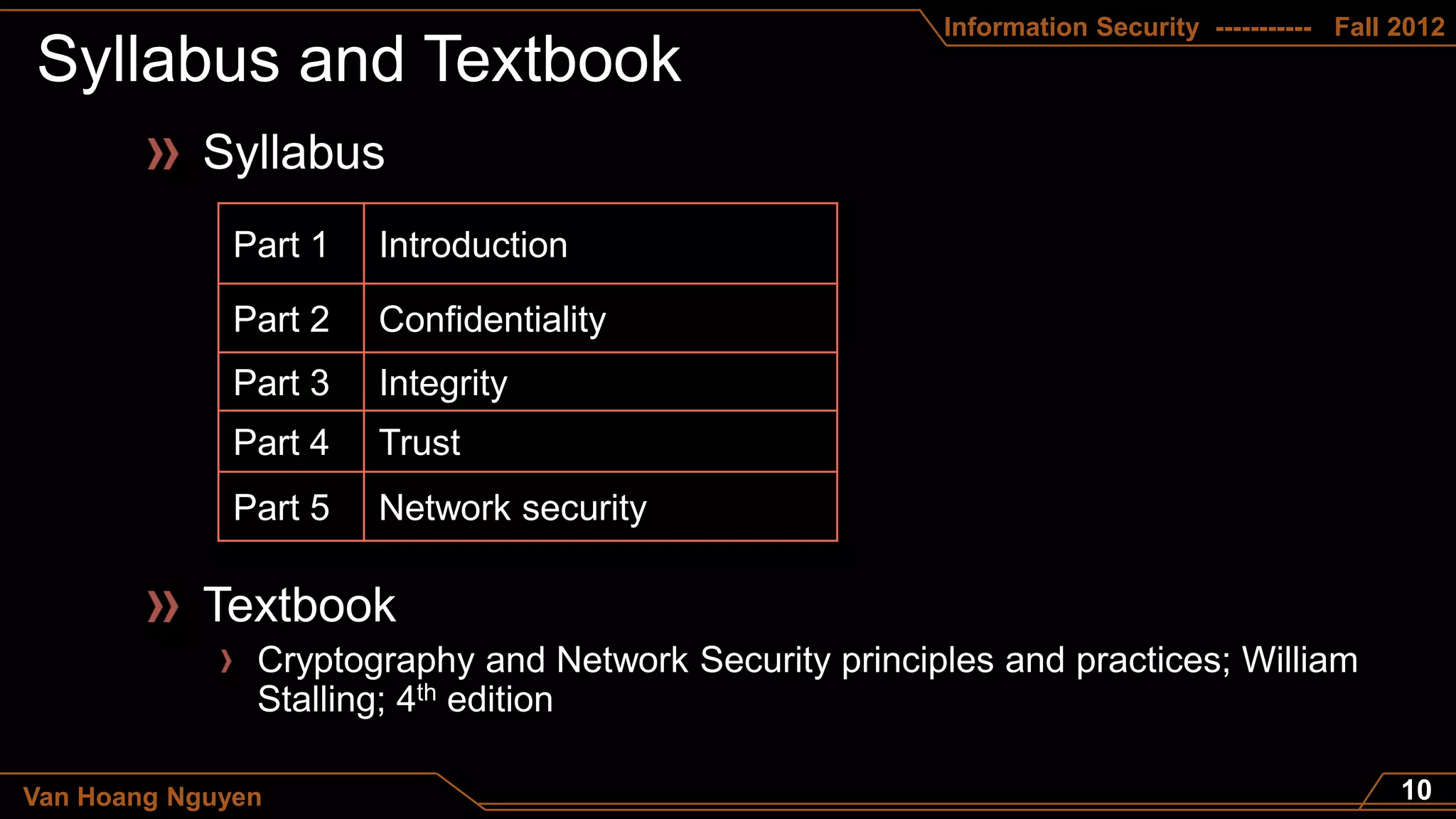
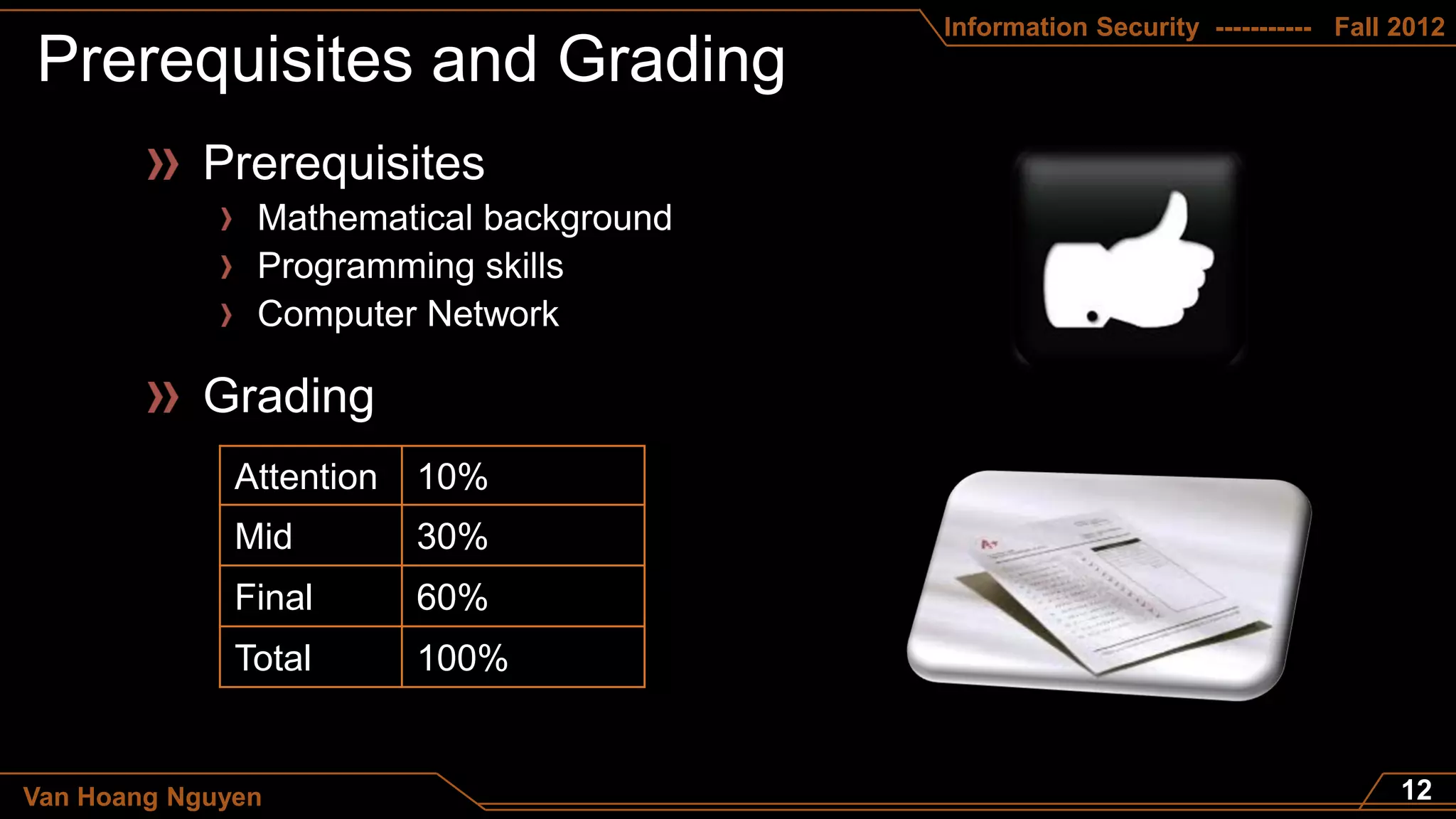
This document appears to be a course syllabus for an Information Security course taught by Van Hoang Nguyen at the Department of Computer Science - FITA - HUA in the fall of 2012. The syllabus outlines that the course will cover topics such as the differences between data and information, definitions of information security, principles of confidentiality, integrity, and trust, and network security. It also lists the grading breakdown as 10% for attention, 30% for a midterm, and 60% for a final exam.