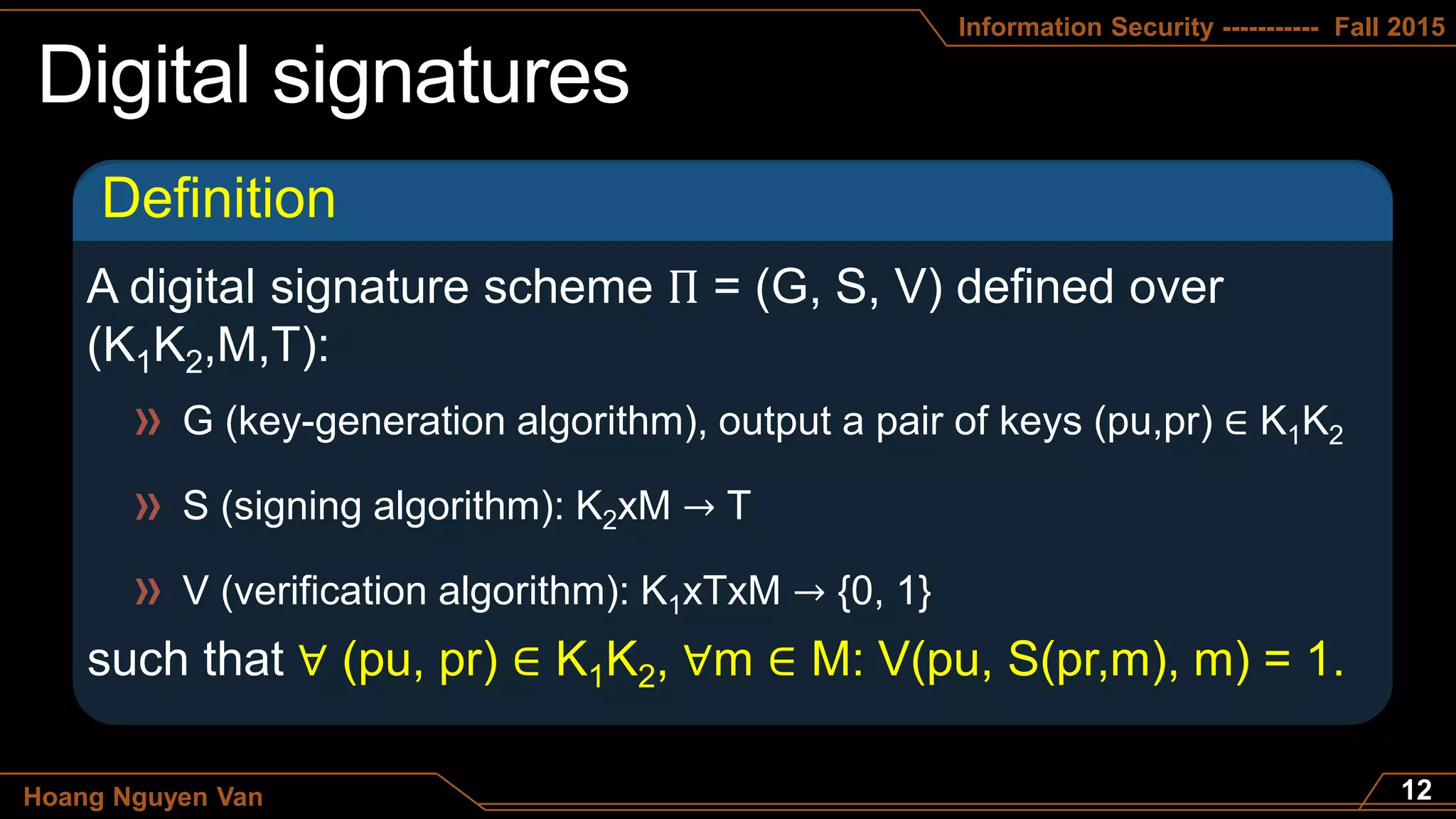
The document appears to be lecture slides on information security. It discusses several topics:
- Digital signature schemes and what it means for them to be secure
- Approaches for building secure digital signature schemes such as using hash functions and RSA
- Public key infrastructure and how certificate authorities can be used to securely distribute public keys
- Alternative models for establishing trust between parties such as web of trust without a centralized trusted authority
The document contains definitions, theorems, and examples related to these information security concepts.










![Information Security ----------- Fall 2015
Hoang Nguyen Van
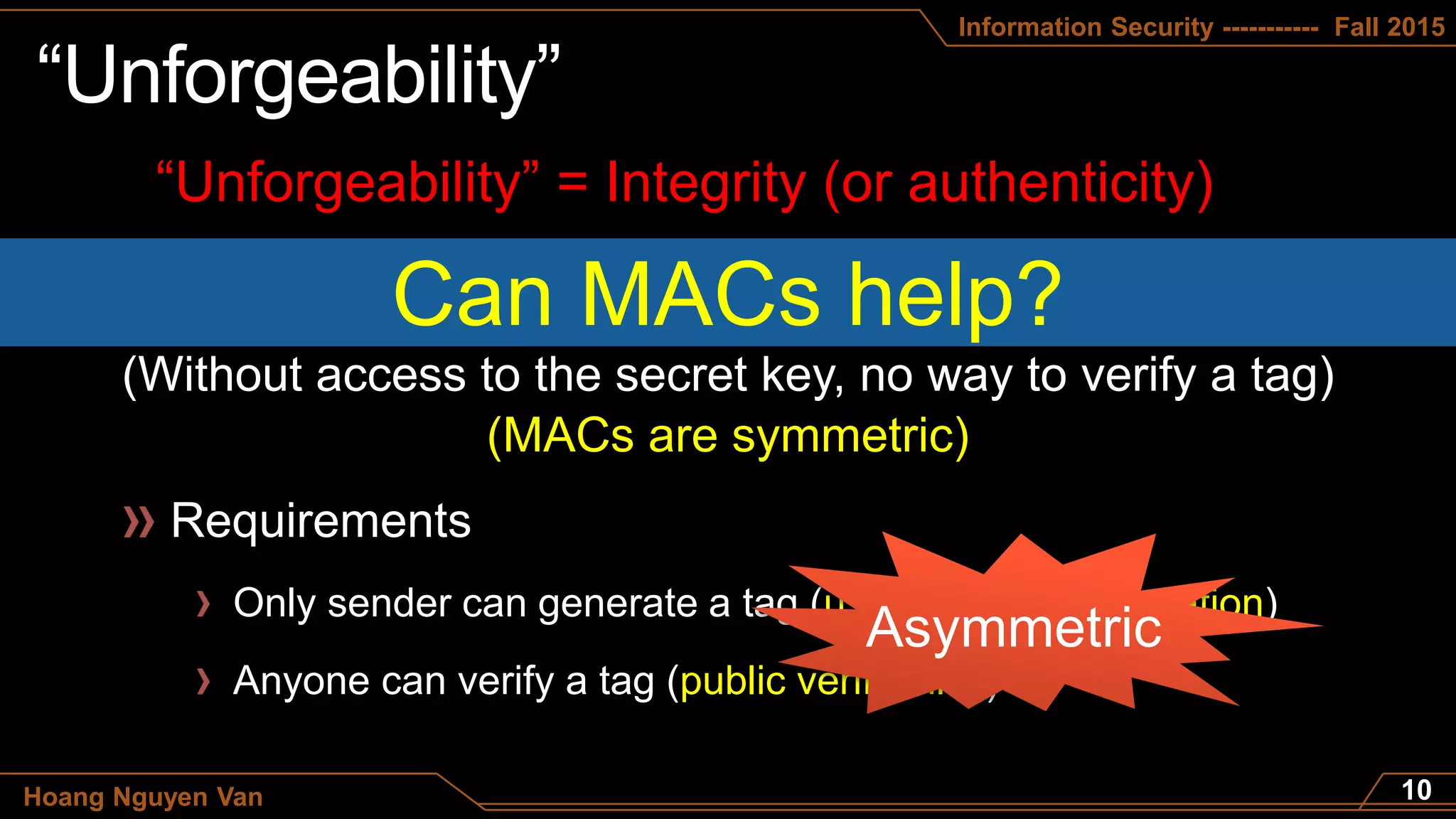
Chal. Adv.
AkK
(m,t)
m1 M
t1 S(pr,m1)
b=1 if V(pu,m,t) = 1 and (m,t) { (m1,t1) , … , (mq,tq) }
b=0 otherwise
b
m2 , …, mq
t2 , …, tq
Secure DSS
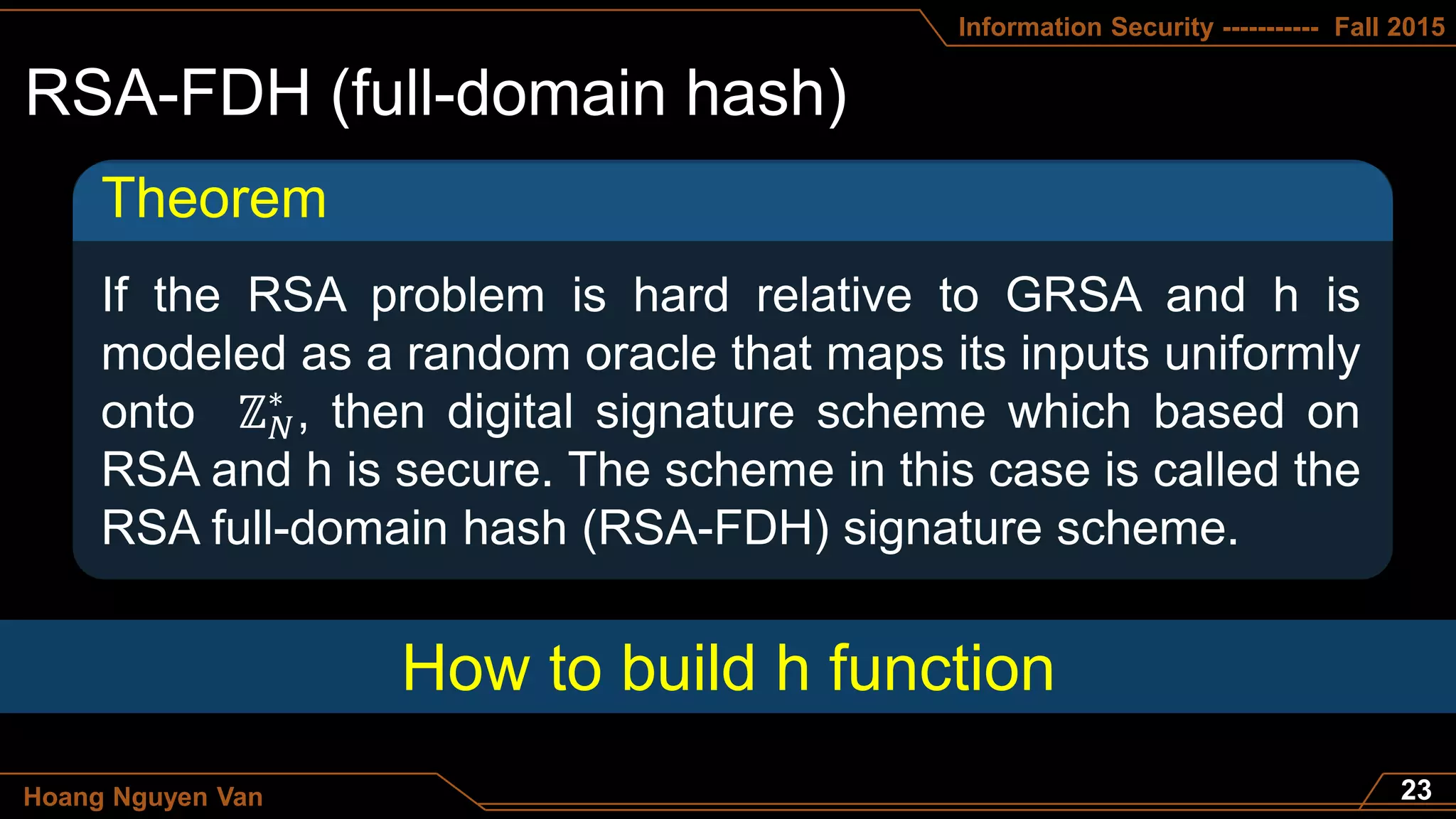
Def: Π =(G,S,V) is a secure DSS if for all “efficient” A:
AdvDSS[A, Π] = Pr[Chal. outputs 1] is “negligible”.](https://image.slidesharecdn.com/lec10trust-pdf-150924092501-lva1-app6892/75/Trust-Digital-Signature-16-2048.jpg)


![Information Security ----------- Fall 2015
Hoang Nguyen Van
RSA assumption: Given pu=<N,e>, hard to compute
the eth root of a uniform m ∈ ℤ 𝑁
∗
. ⟹ easy to compute eth
root of some specific message.
The eth root of m modulo N is [md mod N]
(md)e = mde = m[ed mod 𝜙(N)] = m mod N
Example
easy to compute the eth root of m = 1.](https://image.slidesharecdn.com/lec10trust-pdf-150924092501-lva1-app6892/75/Trust-Digital-Signature-19-2048.jpg)


![Information Security ----------- Fall 2015
Hoang Nguyen Van
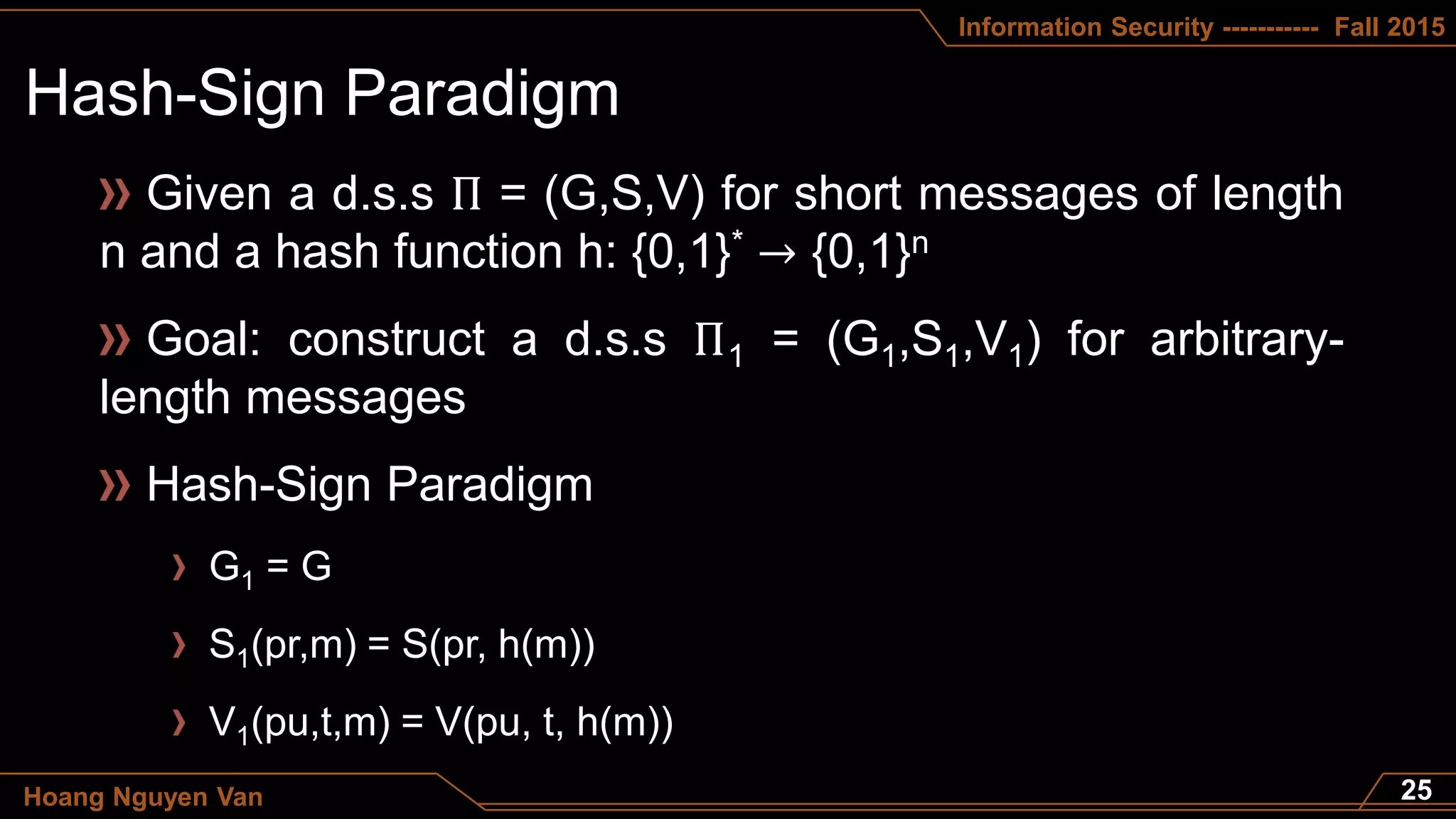
Transformation function h: M ⟶ ℤ 𝑁
∗
Π = (G, S, V)
G = GRSA which outputs pu = <N,e> and pr = <N,d>
S(pr, m) = ERSA(pr, h(m)) = [h(m)]d mod N
V(pu, t, m) = 1 if h(m) = DRSA(pu, t) = te mod N and = 0 otherwise
What cryptographic property h should have](https://image.slidesharecdn.com/lec10trust-pdf-150924092501-lva1-app6892/75/Trust-Digital-Signature-22-2048.jpg)