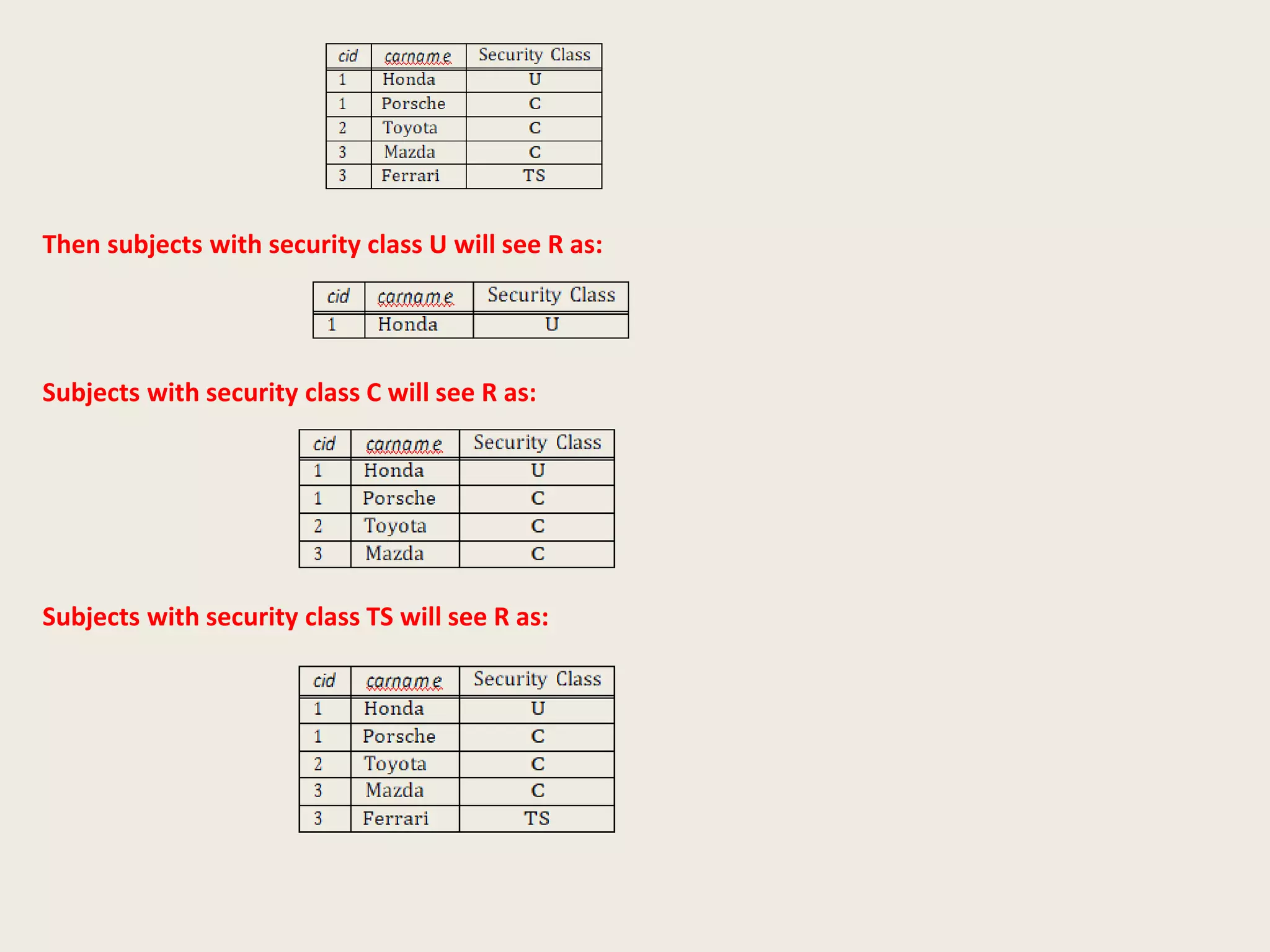
The document discusses concepts related to database security, focusing on the Bell-LaPadula model's rules for mandatory access control, the use of covert channels to bypass these controls, and the importance of discretionary access controls in specific scenarios. It highlights the roles of encryption, statistical database limitations, auditing, and public-key encryption's superiority over traditional methods like DES. Additionally, it covers secure online transactions and methods of user authentication and message verification.