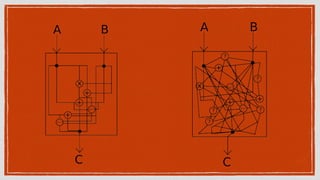
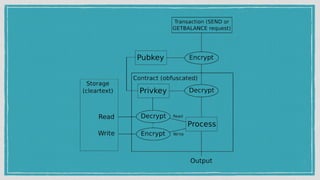
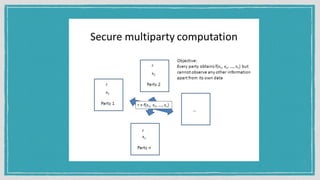
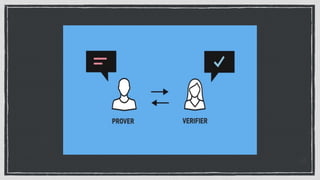
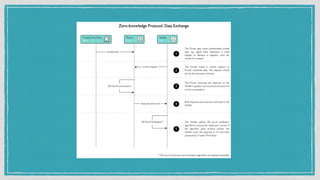
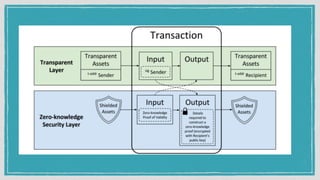
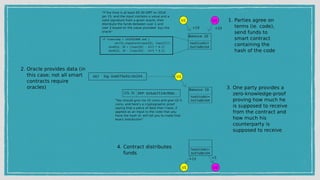
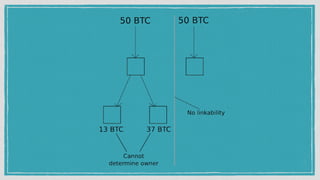
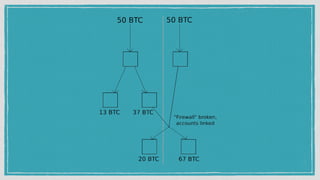
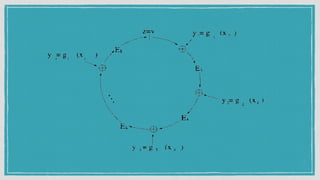
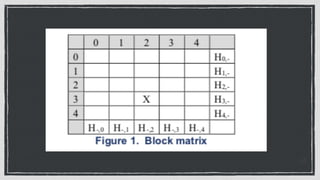
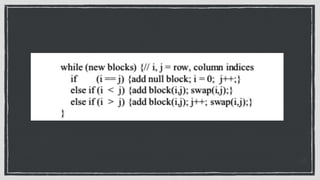
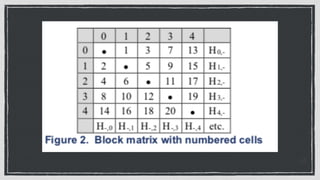
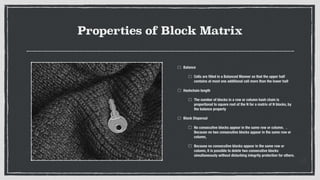
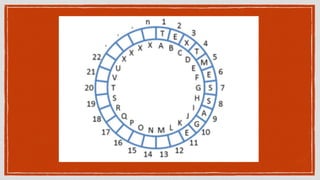
The document discusses various privacy-preserving techniques in blockchain, including ring signatures, zero-knowledge proofs, and secure multi-party computation (SMPC). It highlights the complexities and challenges associated with these techniques, particularly in maintaining trust among participants and ensuring data integrity while complying with regulations such as GDPR. Additionally, it introduces innovative data structures like block matrices to support secure deletion of data while preserving integrity and presents future challenges in achieving computational practicality without compromising privacy.