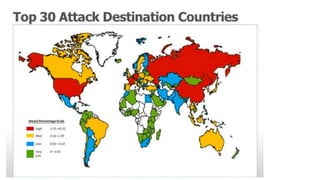
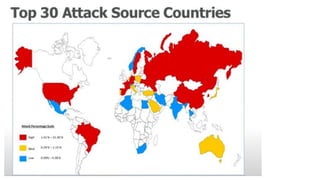
The document discusses the rising threats of cybercrime in Africa, detailing its economic impact and the global cybersecurity market projected to reach $152 billion by 2025. It highlights the severe costs of cybercrime, with estimates of $500 billion in global losses, and the urgent need for skilled professionals and cohesive international cooperation to counter these threats. Additionally, the document emphasizes the role of frameworks such as the Budapest Convention in promoting cybersecurity regulation and cooperation among nations.