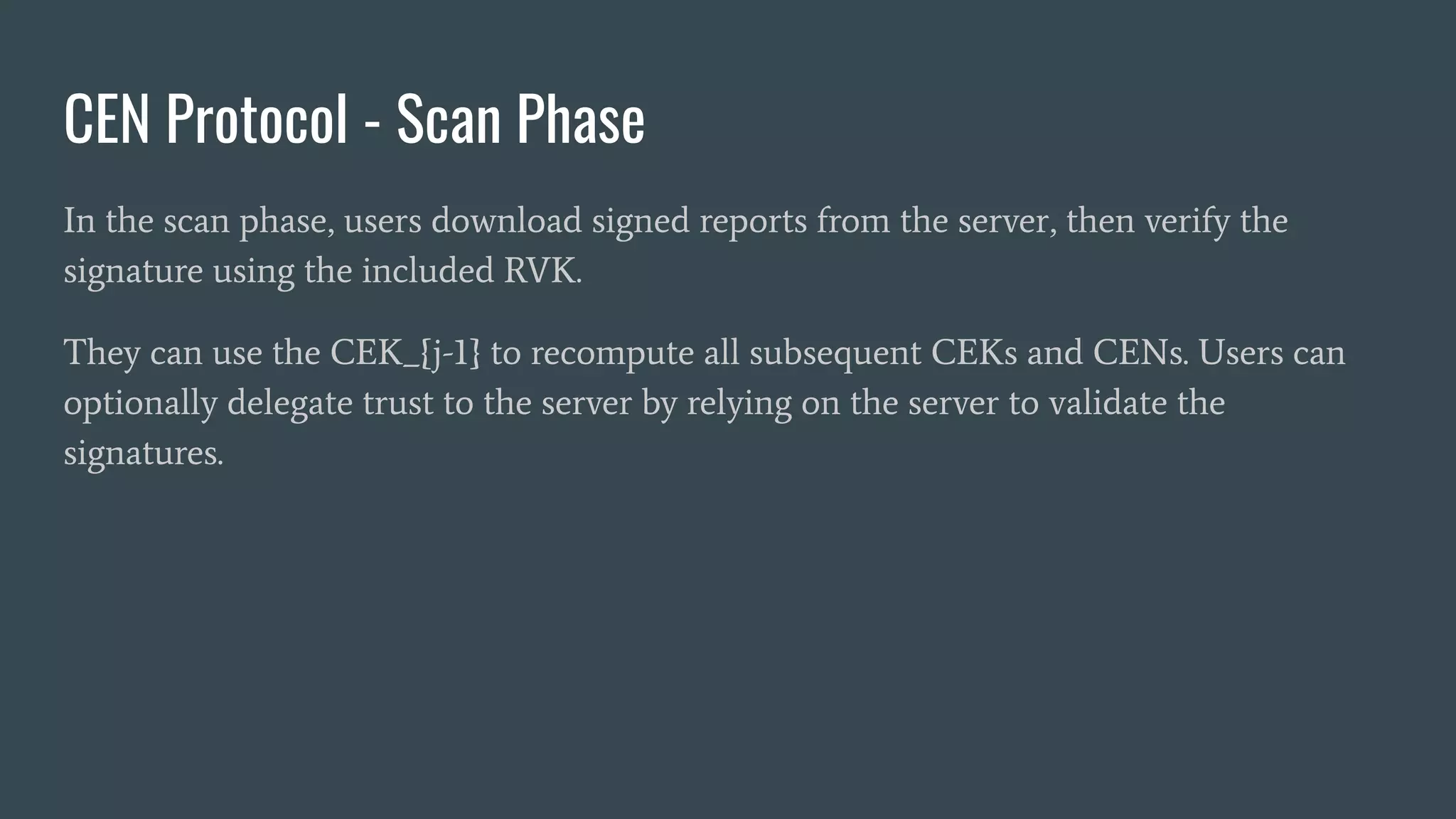
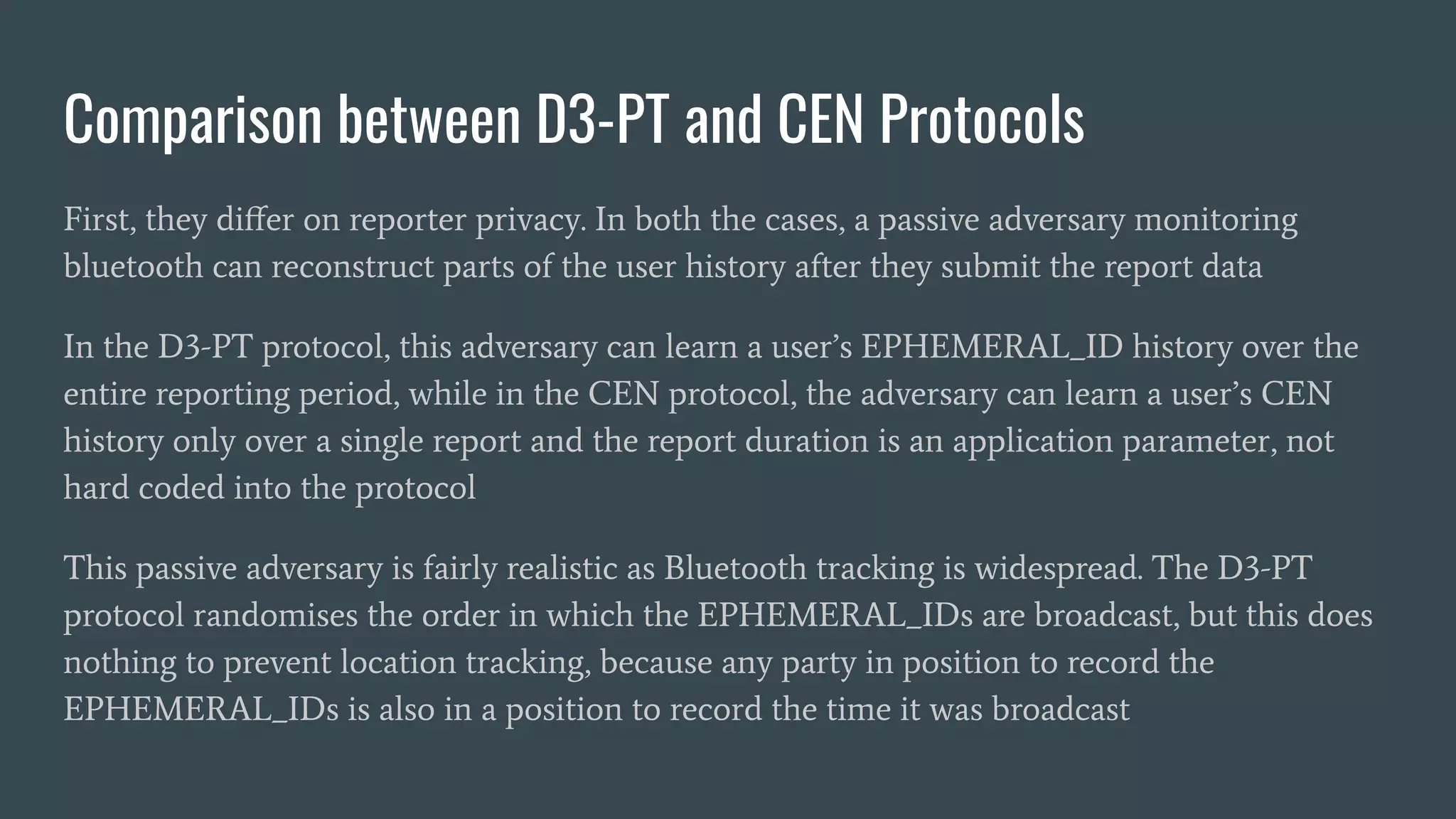
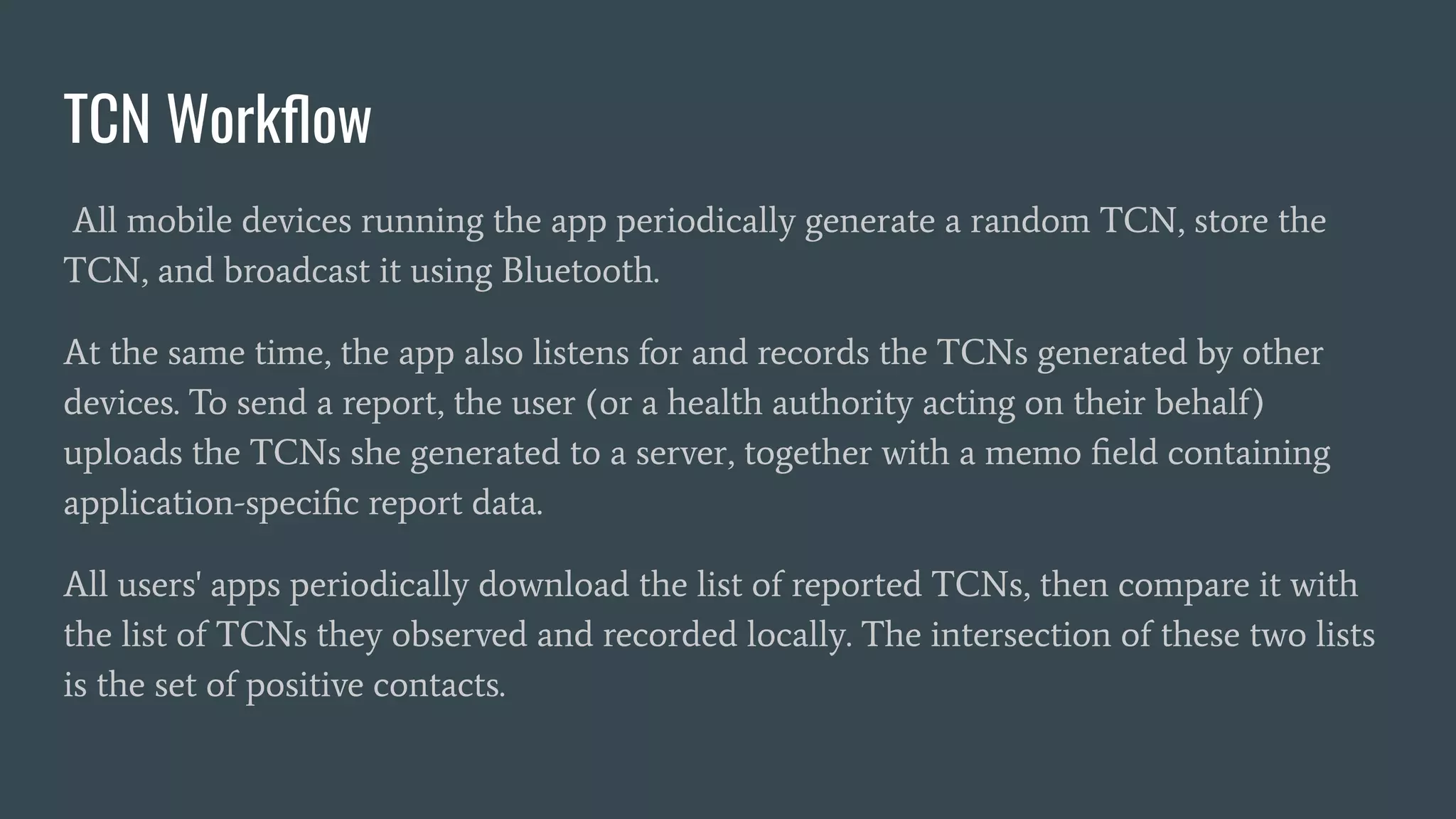
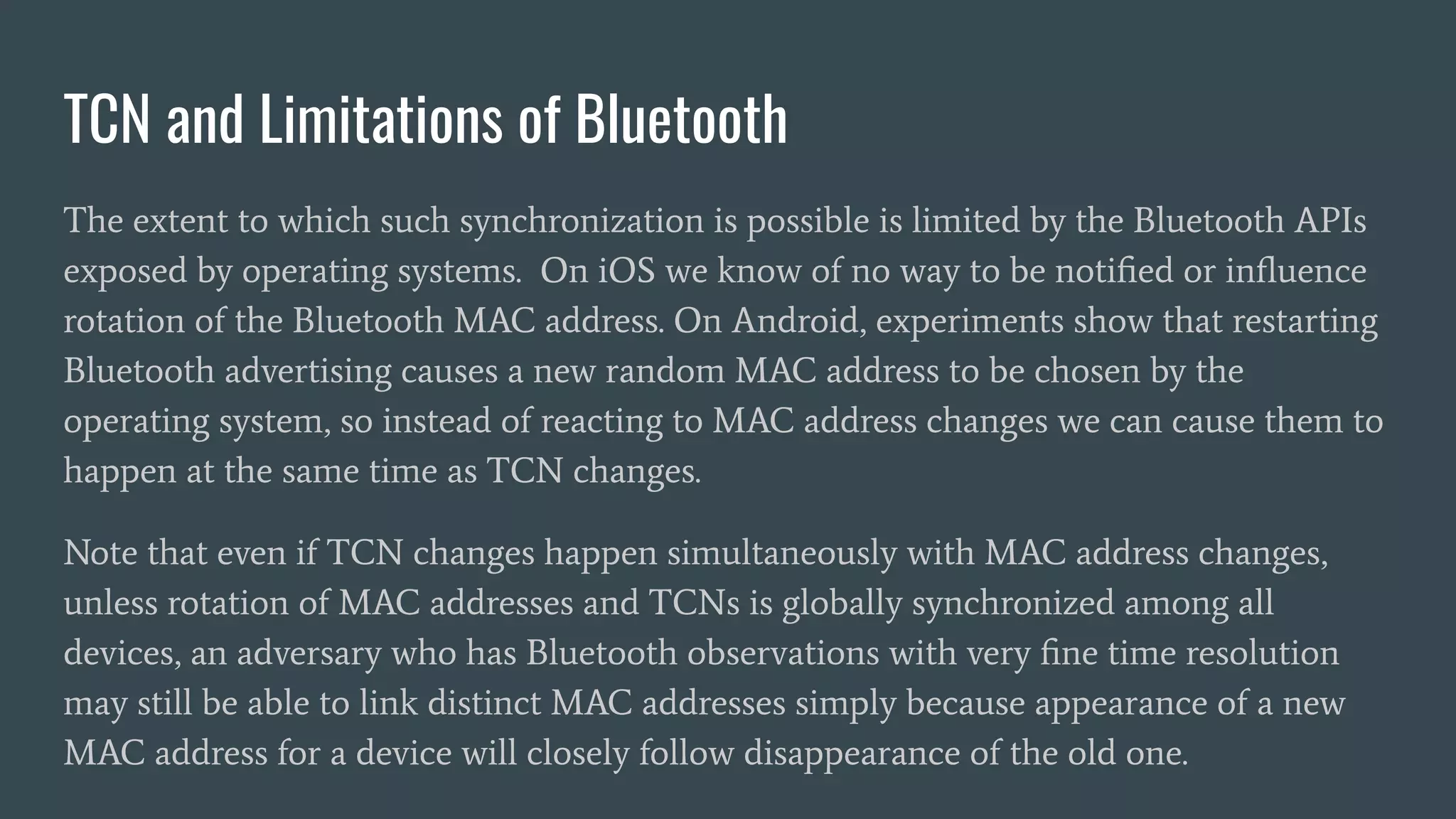
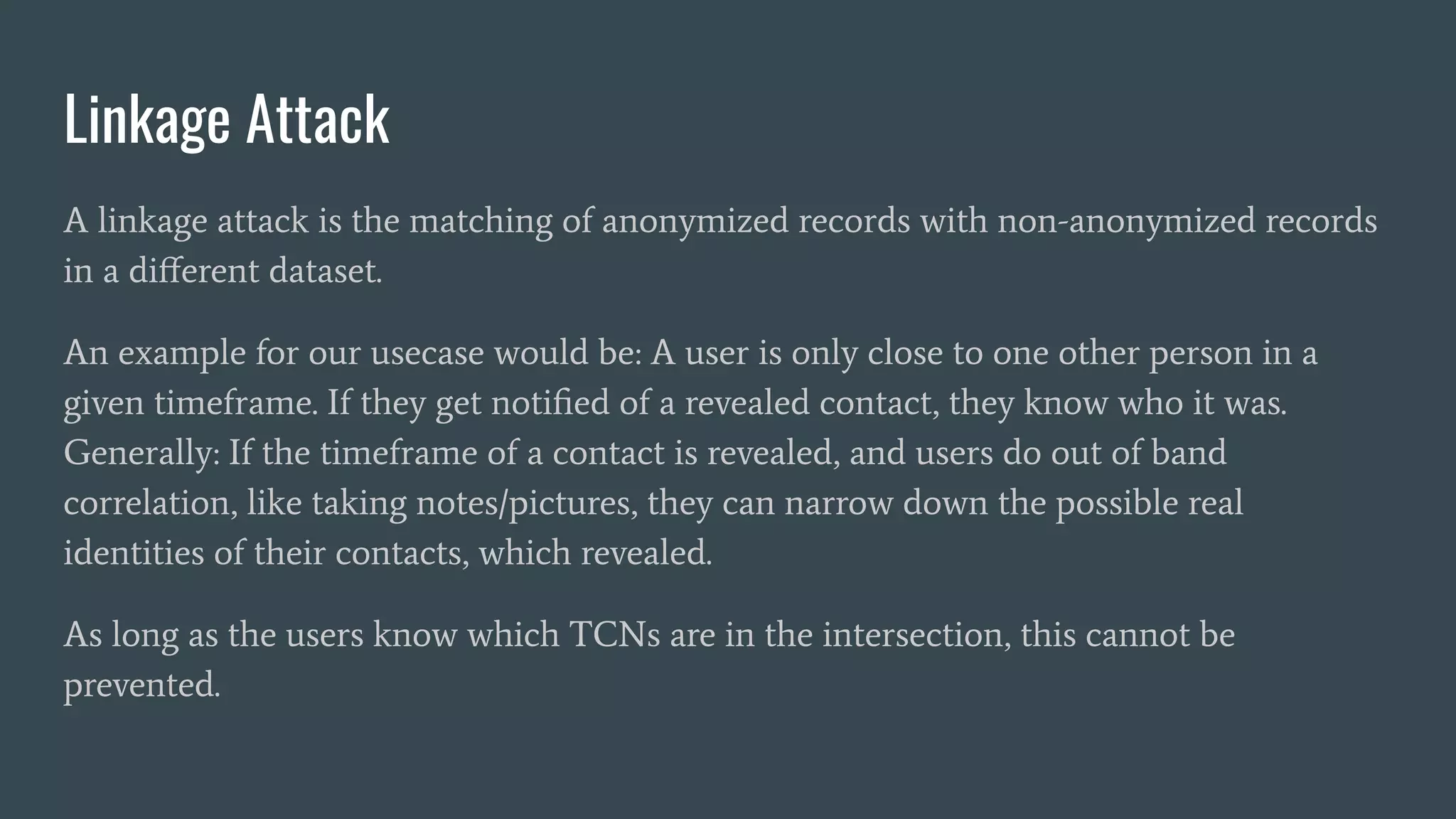
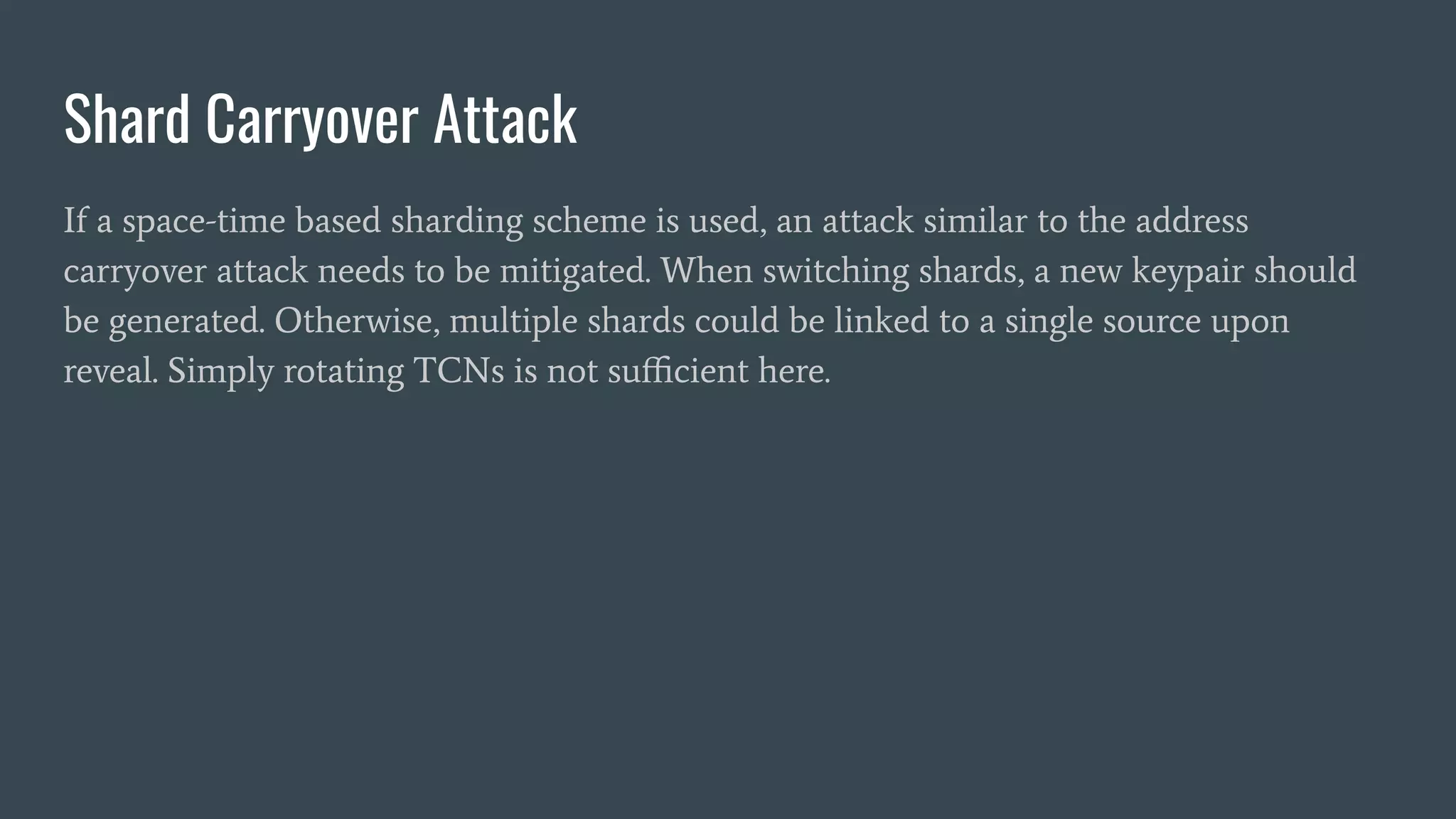
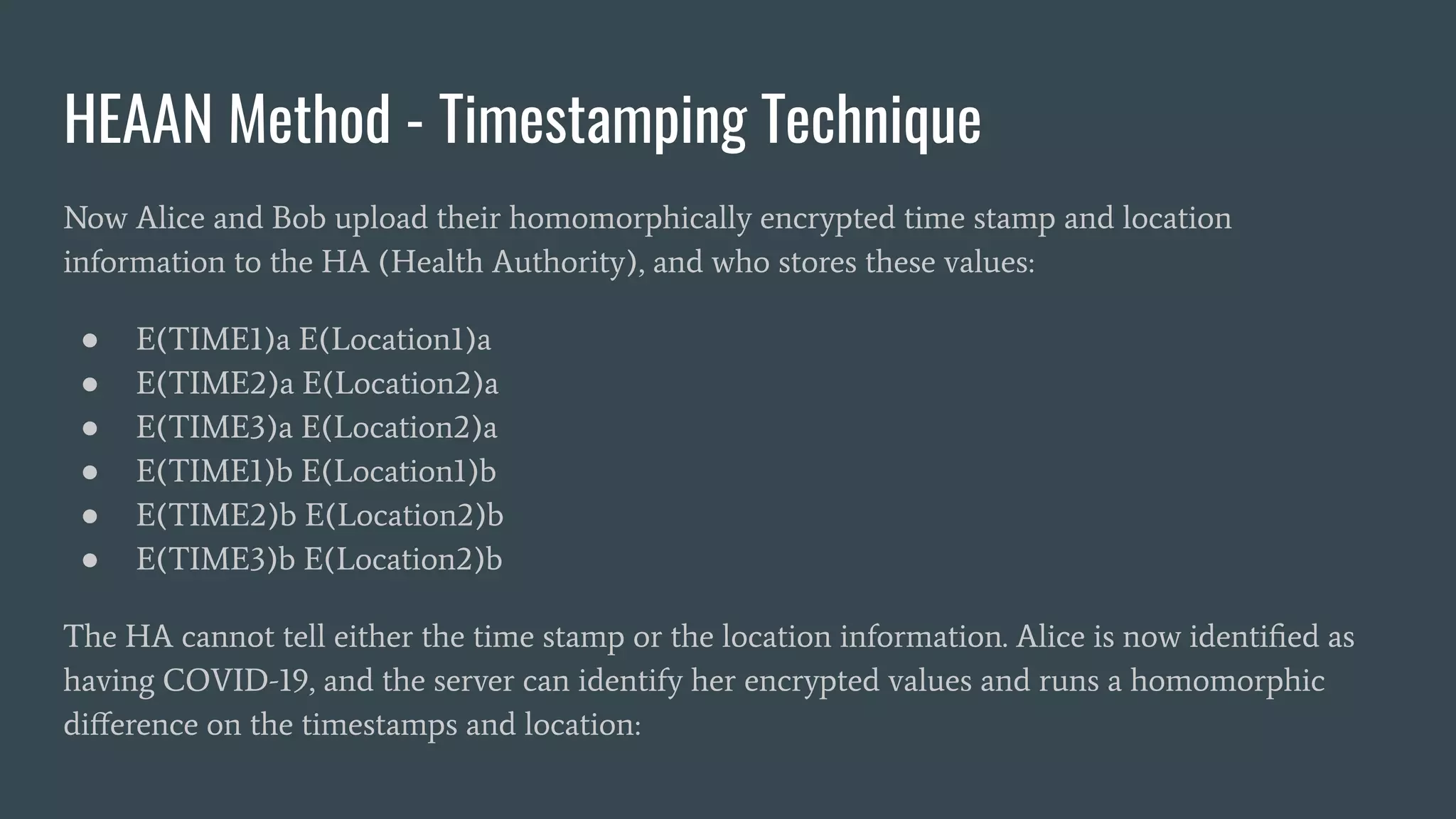
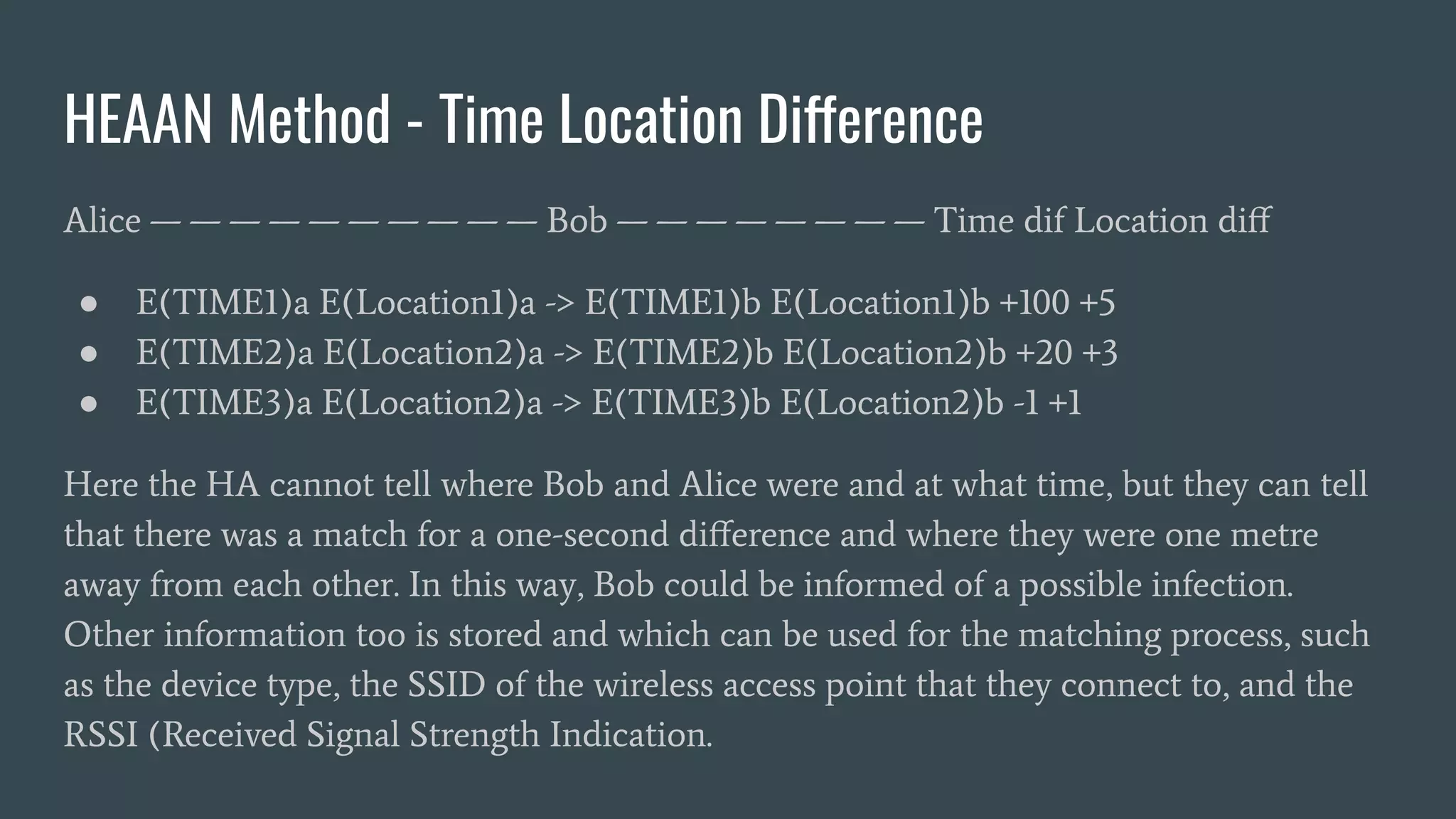
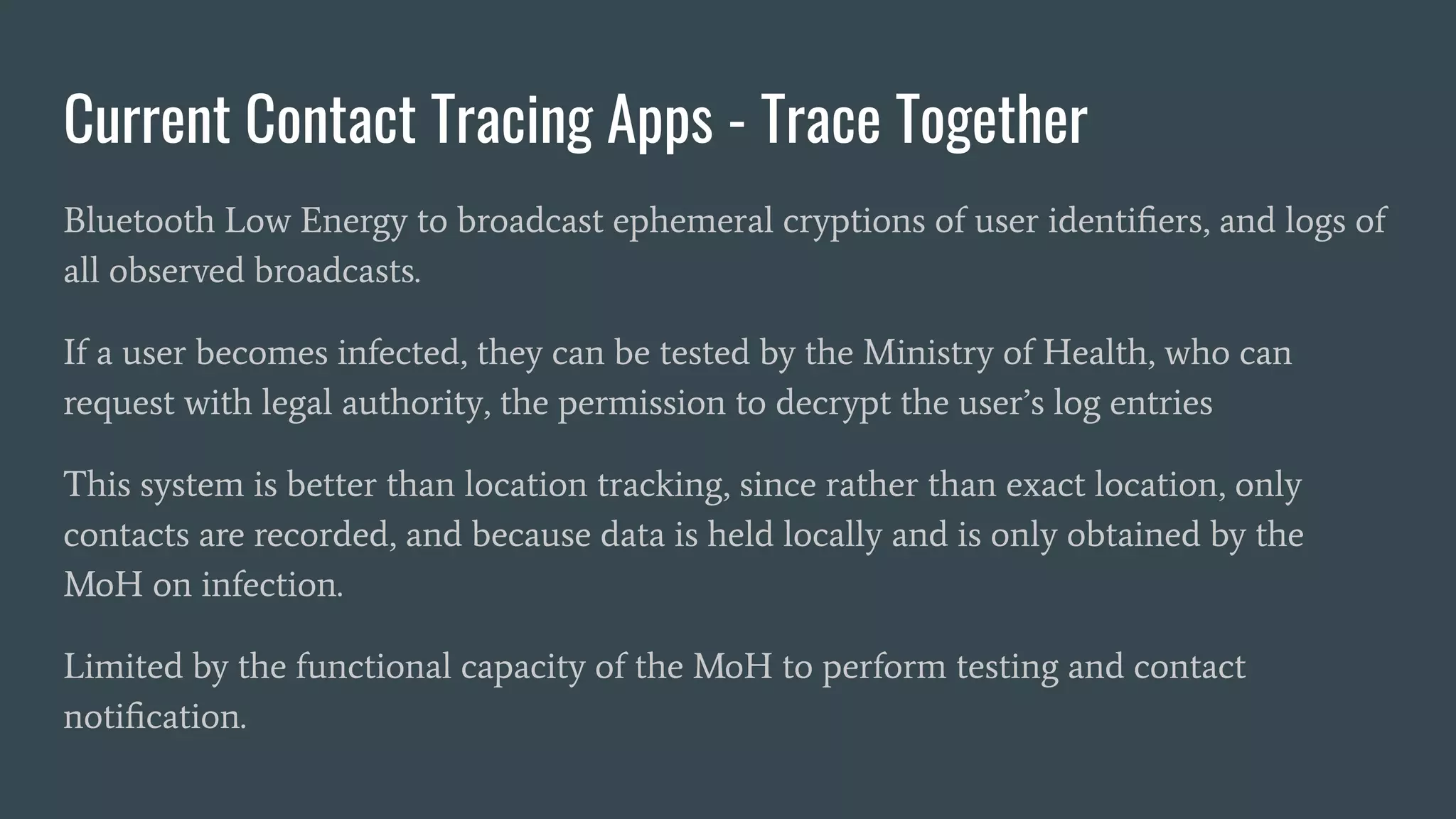
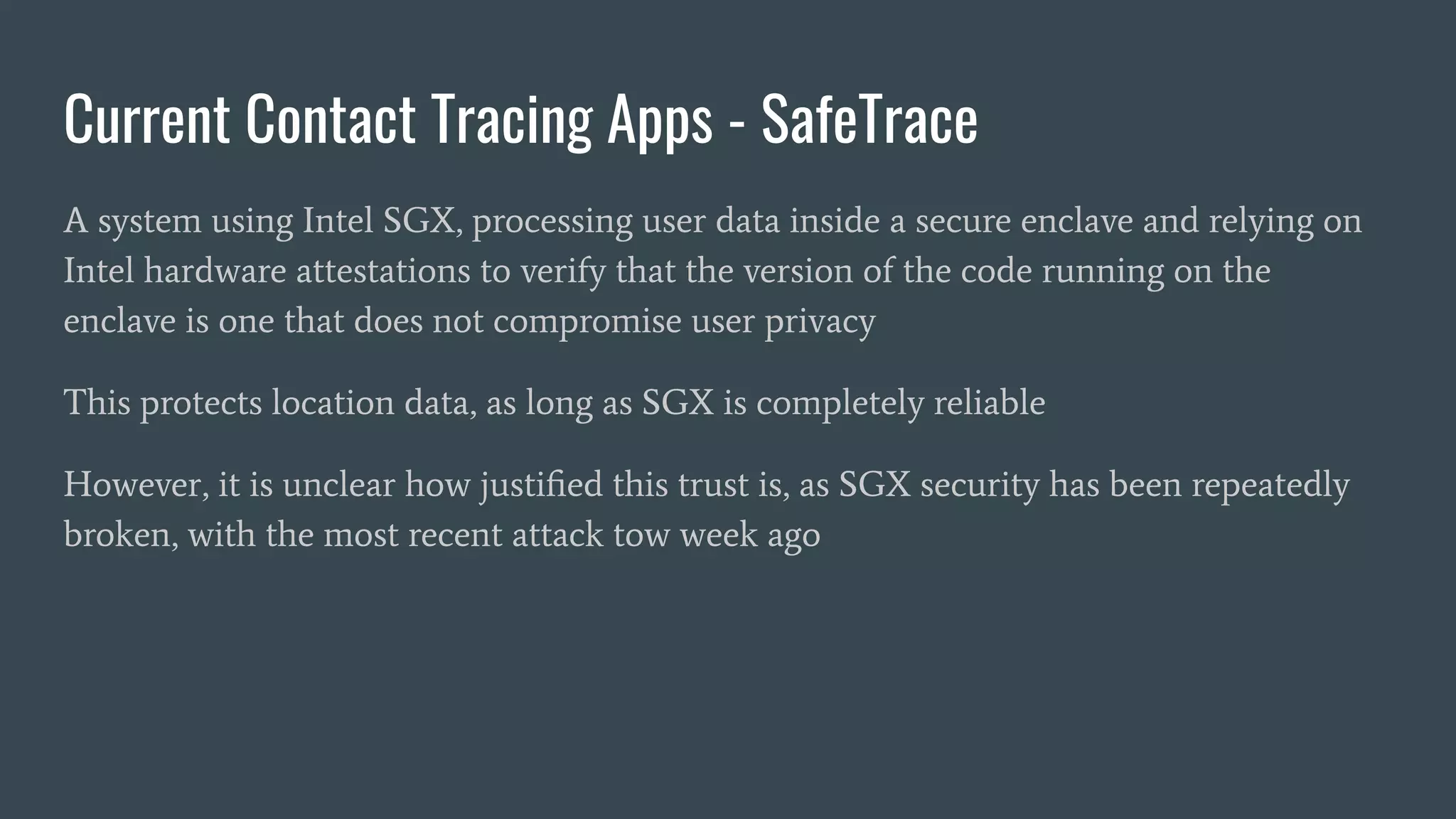
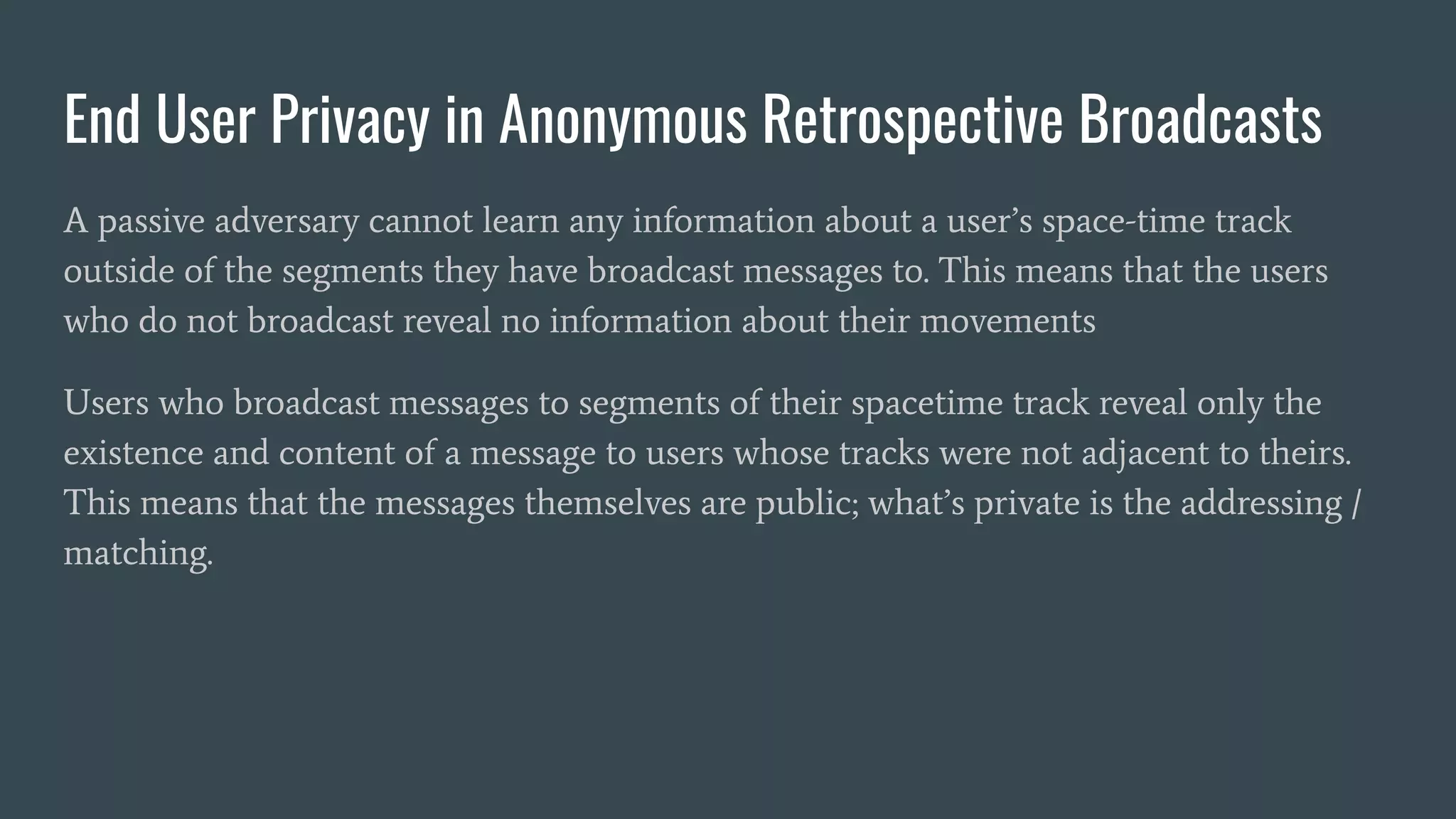
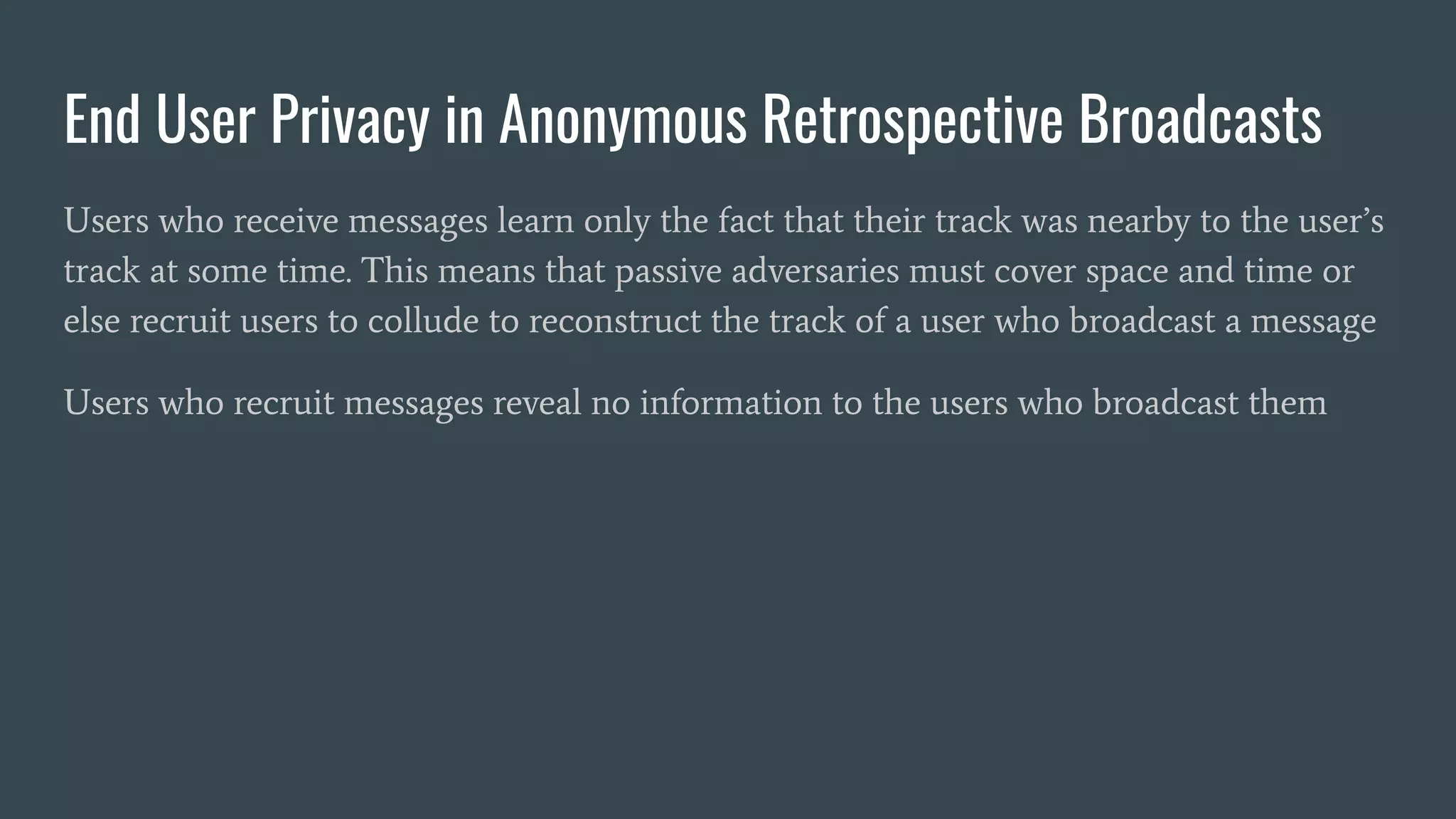
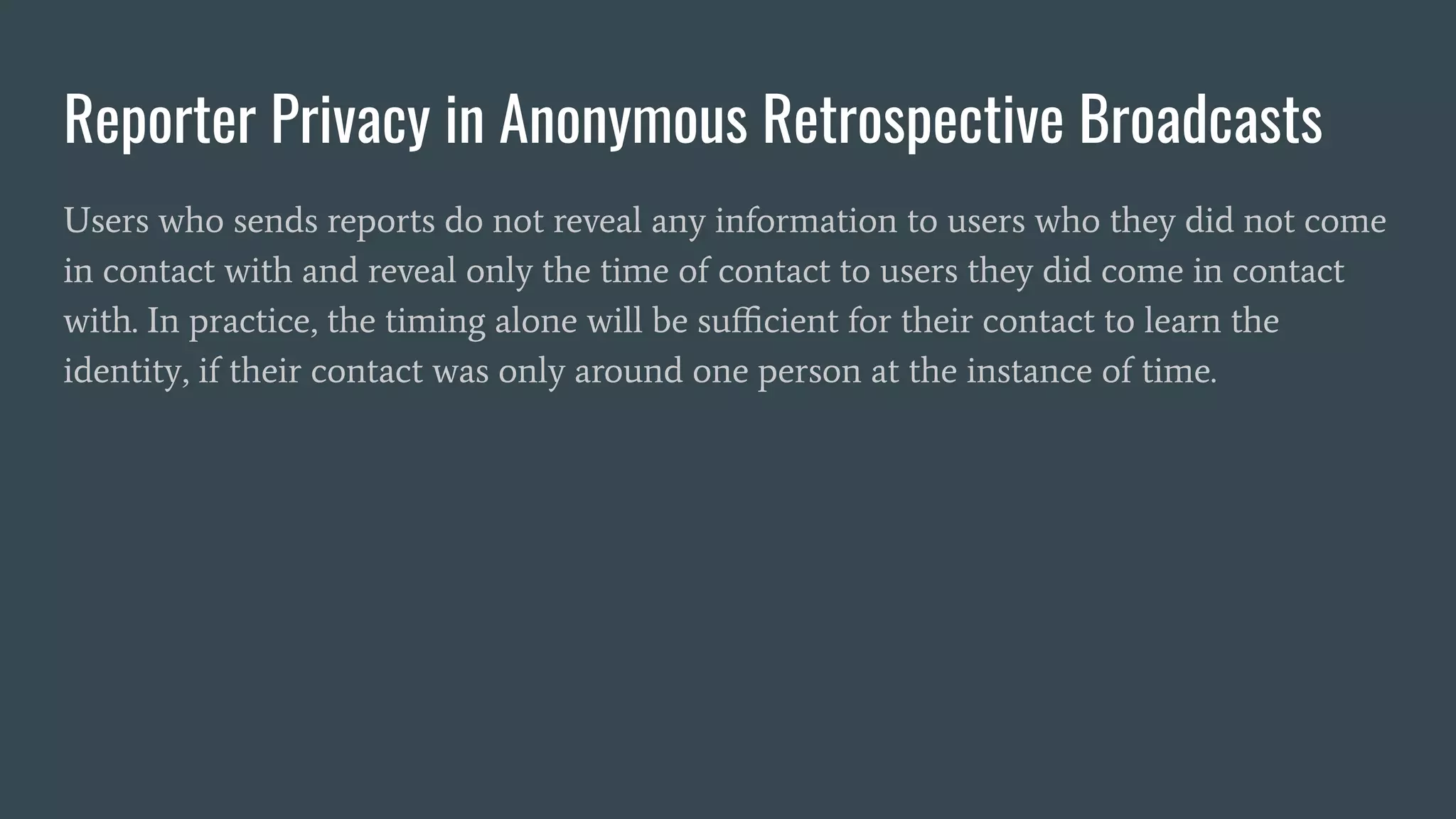
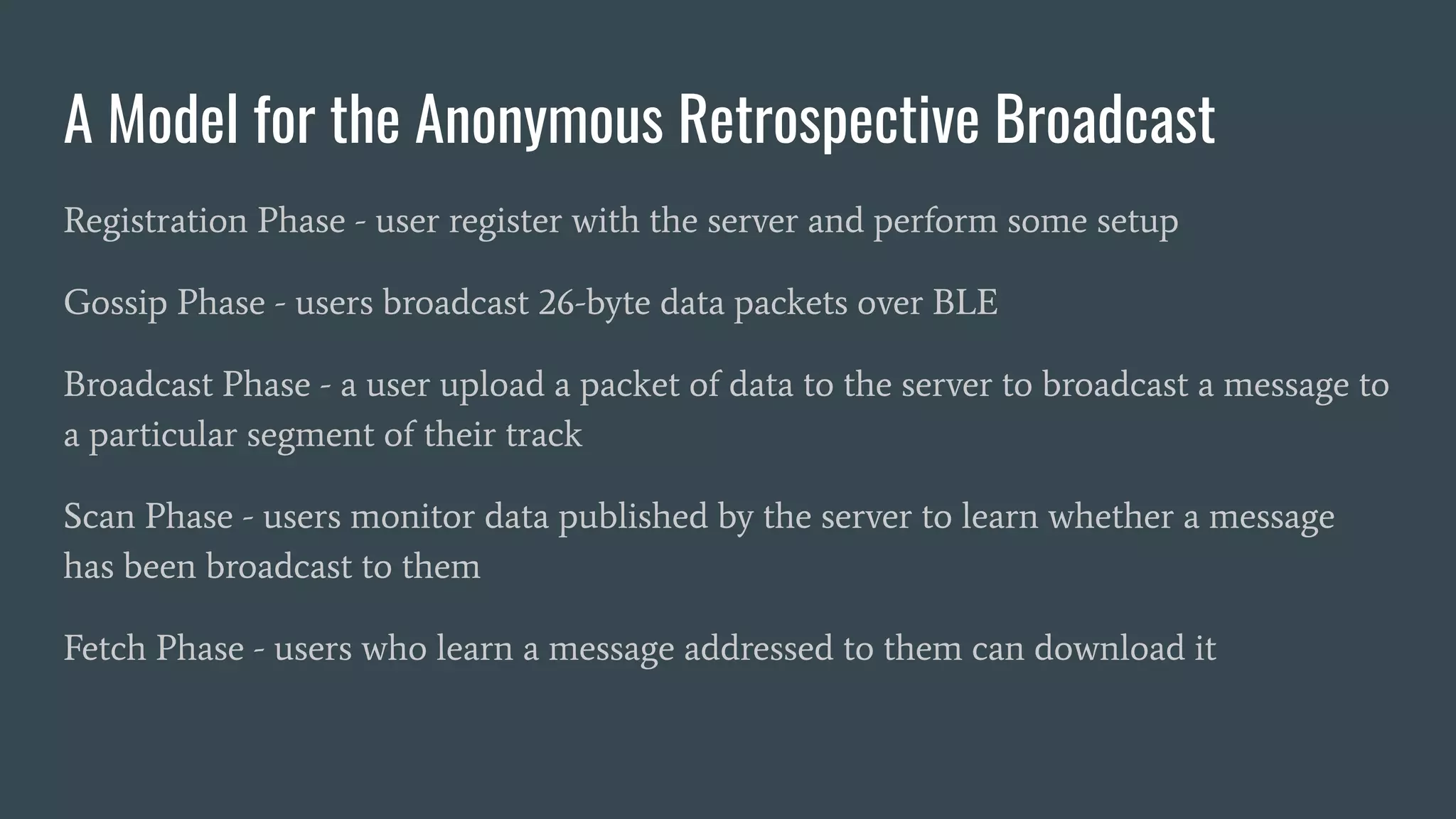
The document discusses various privacy-preserving proximity protocols for contact tracing, highlighting frameworks that utilize cryptography to manage trust in the access and use of sensitive location data. It compares current contact tracing apps and protocols such as DP-3T, CEN, and TCN, focusing on their mechanisms for protecting user privacy while enabling effective contact tracing. Additionally, it addresses potential security attacks and limitations in Bluetooth technology that could compromise user anonymity and data integrity.











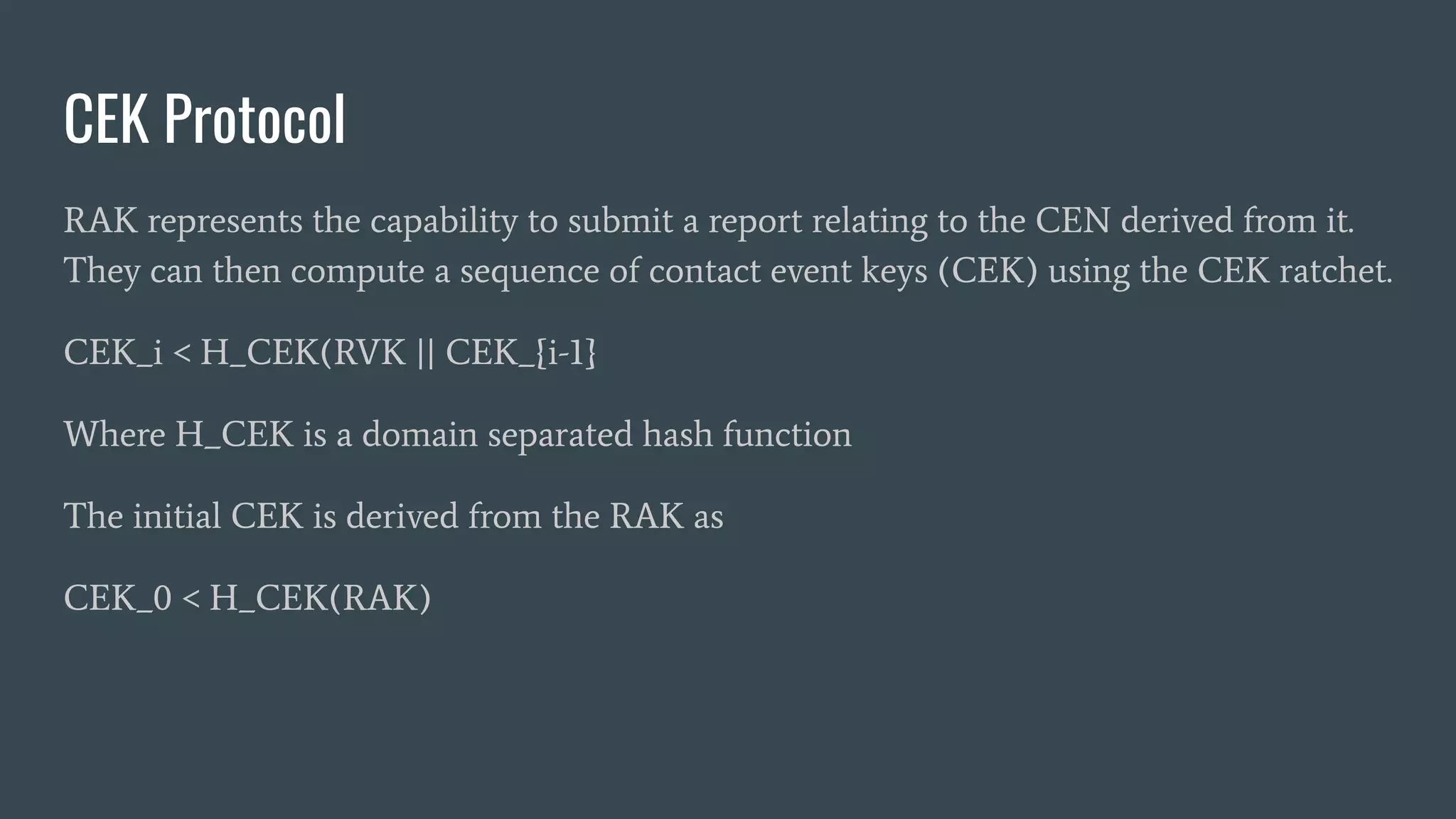
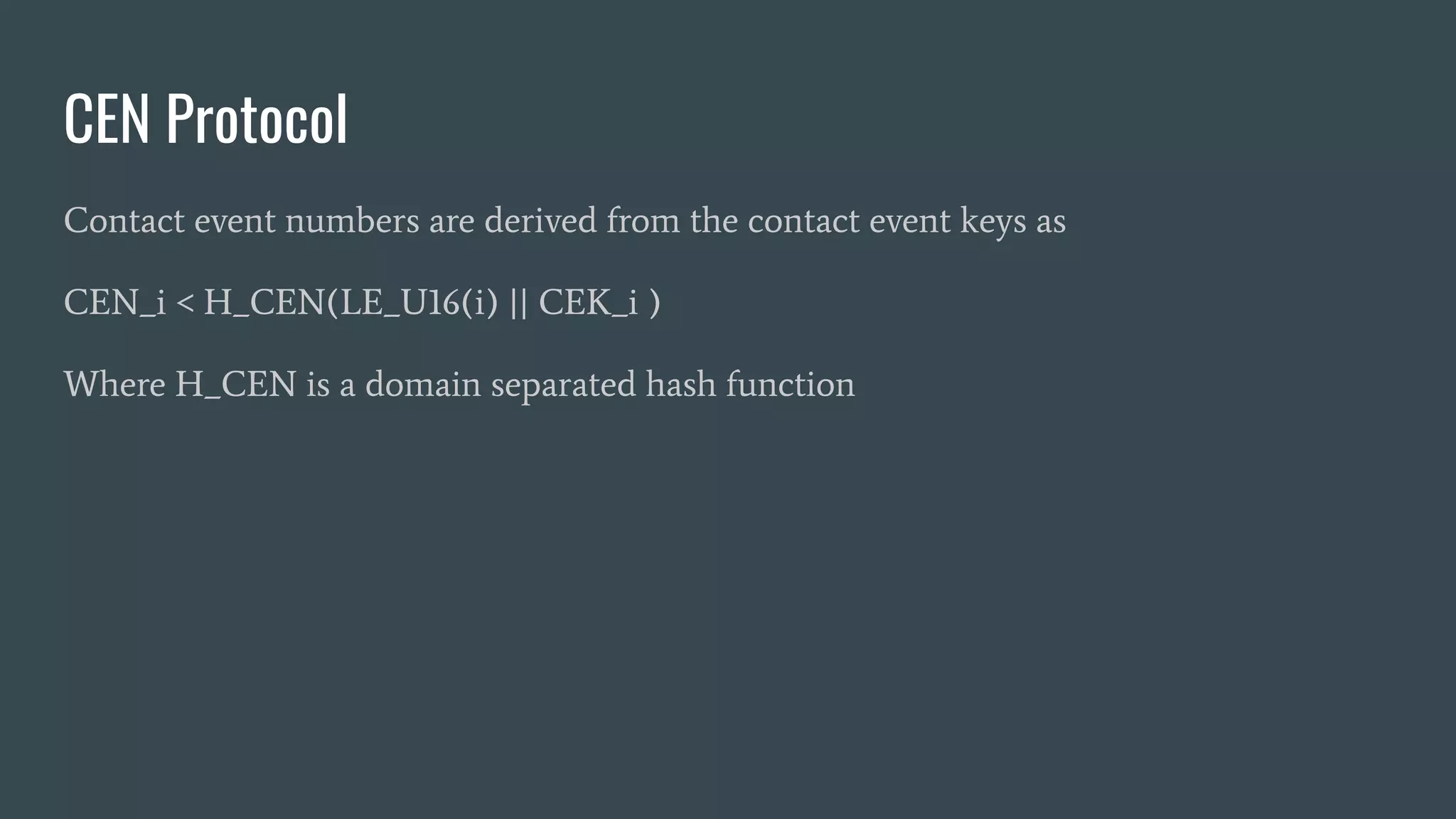

![CEN Protocol - Reporting Phase
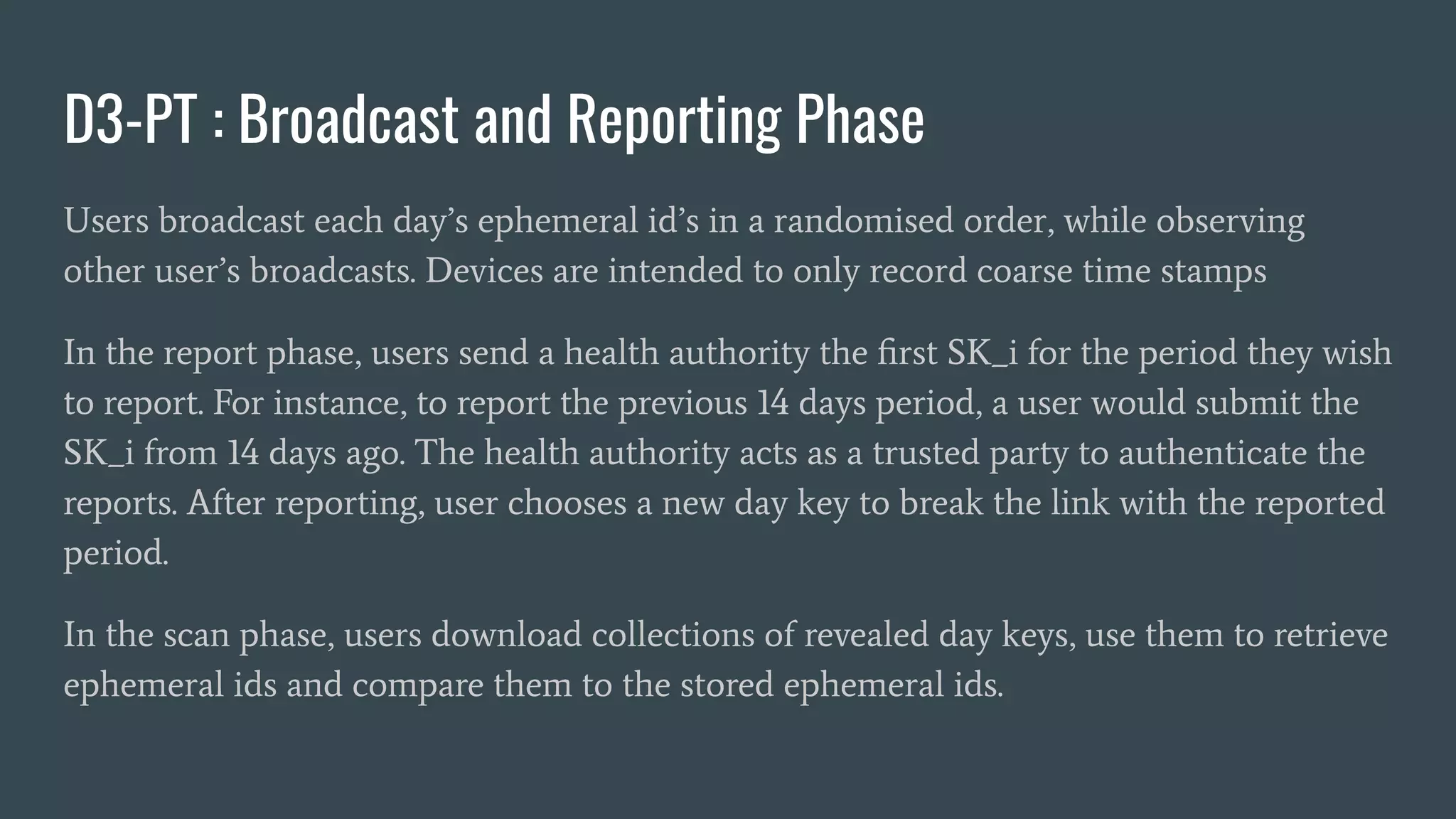
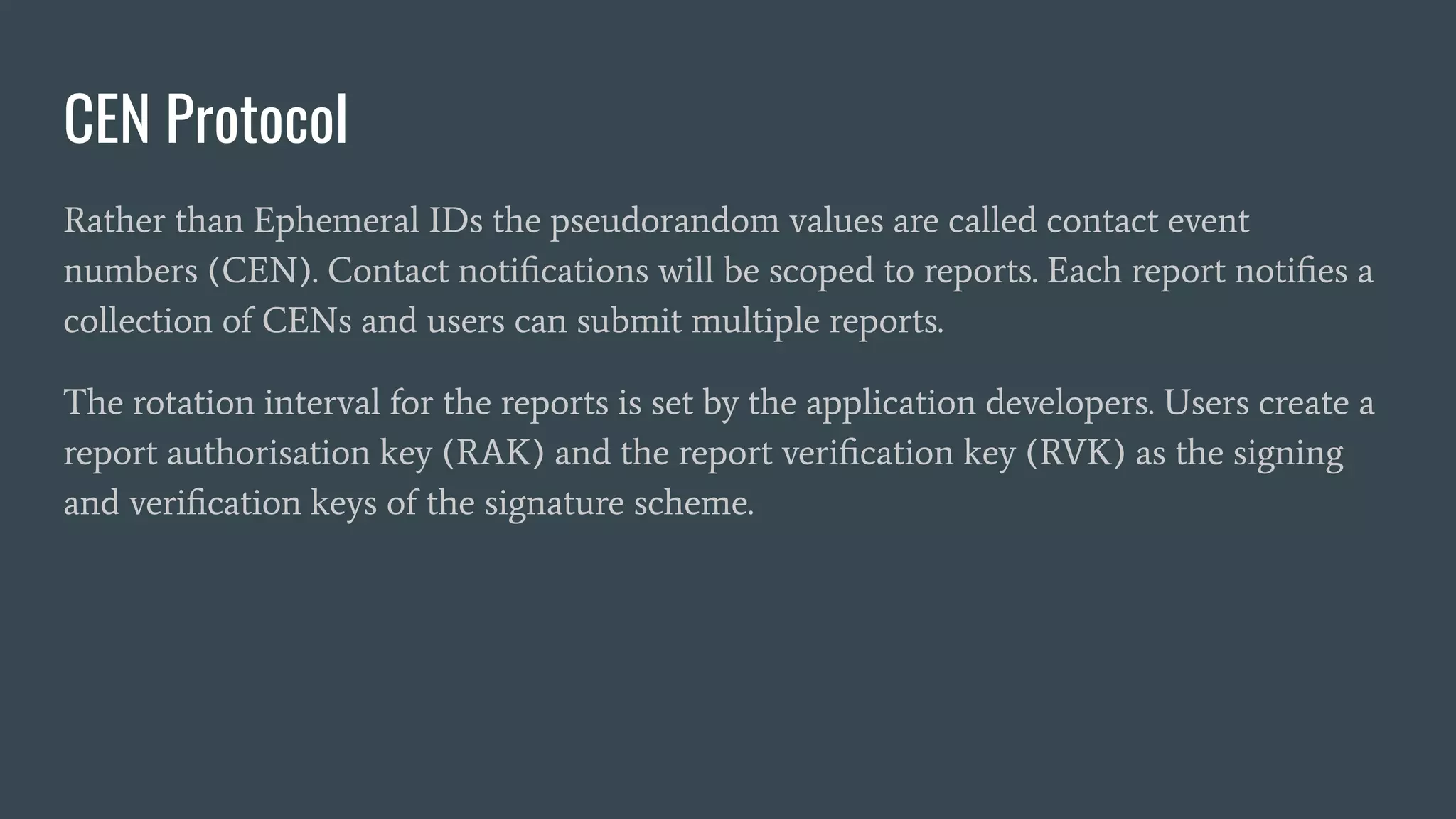
In the reporting phase, users wishing to notify contact they encountered over the
period with CEN indices ji and j2 to prepare the report as :
Report < RVK || CEK [j1 - 1] || LE_U16(j1) || LE_U16(j2) || memo
Then use RAK to produce SIG, a signature over the report, and upload the signed
report REPORT || SIG. The memo field provides a compact space for freedom
messages.](https://image.slidesharecdn.com/tnsfprivacypreservingproximityprotocols2020-200705174916/75/Covid19-ContactTracing-Privacy-Preserving-Proximity-Protocols-23-2048.jpg)