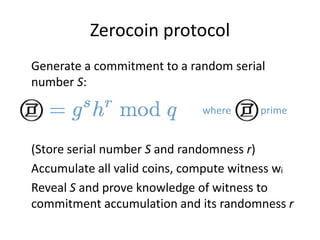
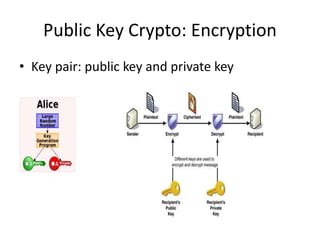
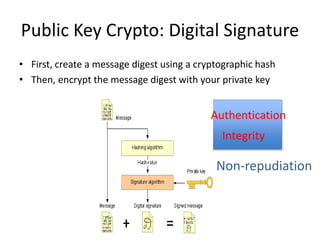
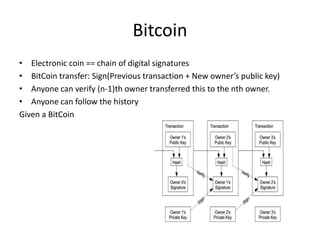
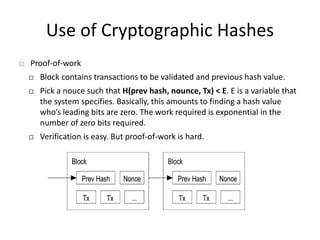
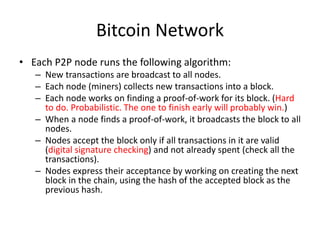
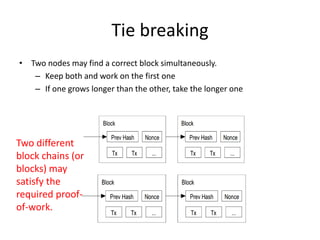
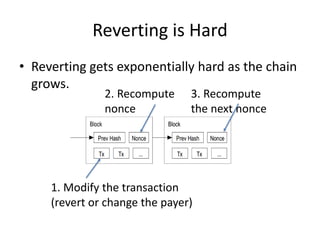
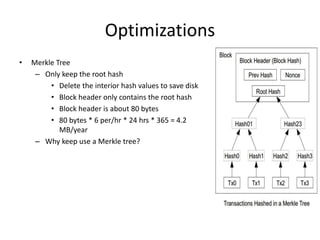
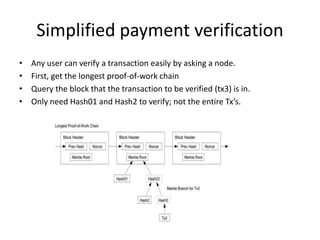
Bitcoin is a decentralized digital currency that uses cryptography to secure online transactions without relying on central authorities. It works by maintaining a distributed ledger called the blockchain that records all transactions. Transactions are authenticated through digital signatures and verified by the network through proof-of-work mining to prevent double spending. While providing pseudonymity, Bitcoin transactions are publicly visible on the blockchain, compromising user privacy. Zerocoin was proposed to add an anonymous currency layer on top of Bitcoin through cryptographic commitments and zero-knowledge proofs to allow untraceable transactions.


















![Zero-knowledge proofs
• Zero-knowledge [Goldwasser, Micali 1980s,
and beyond]
• Prove knowledge of a witness satisfying a
statement
• Specific variant: non-interactive proof of
knowledge
• Here we prove we know:
1.The serial number of a zerocoin
2.That the coin is in the block chain](https://image.slidesharecdn.com/15-bitcoin-220804124741-1cfc6952/85/Blockchain-and-Bitcoin-pptx-31-320.jpg)