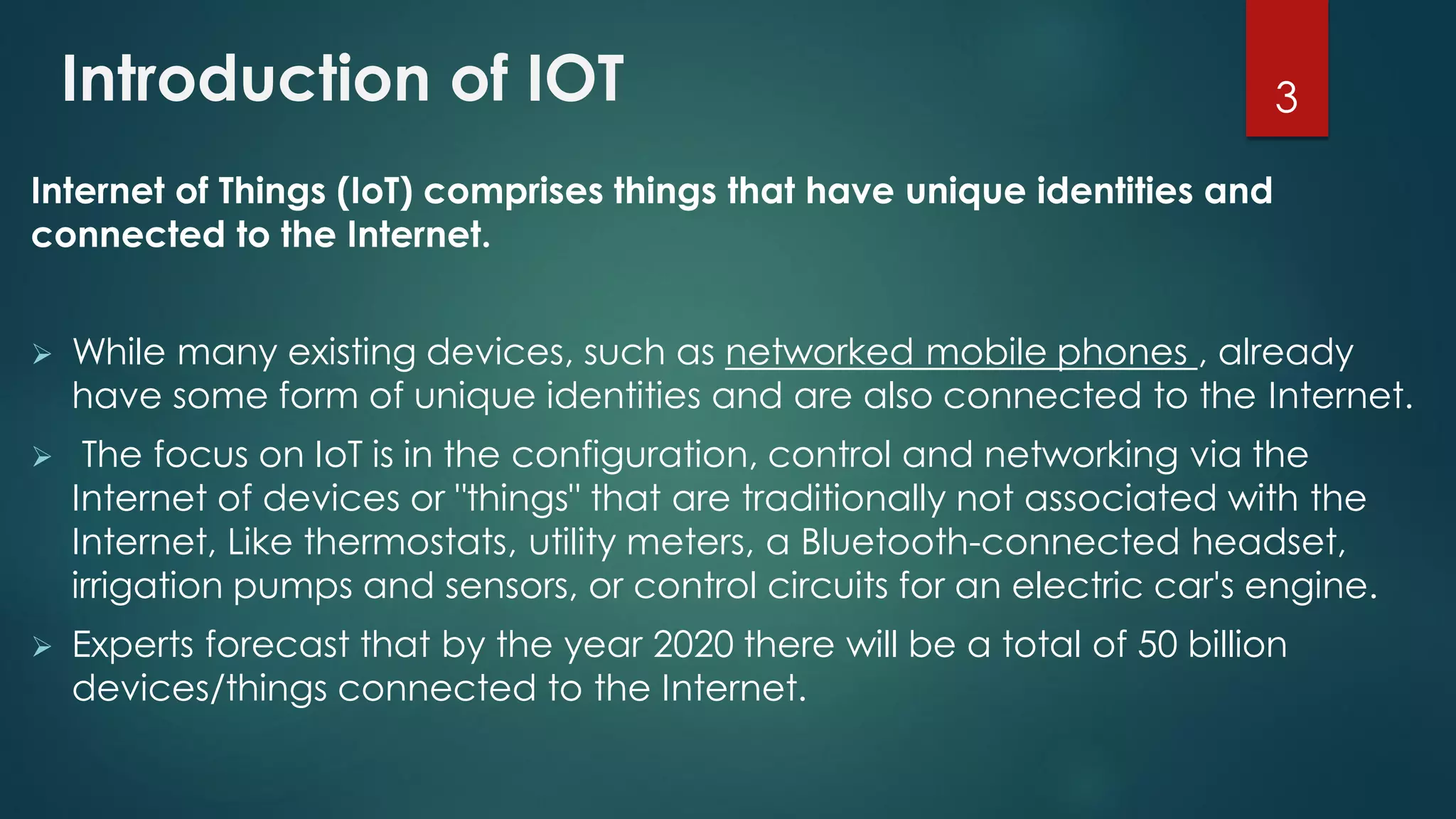
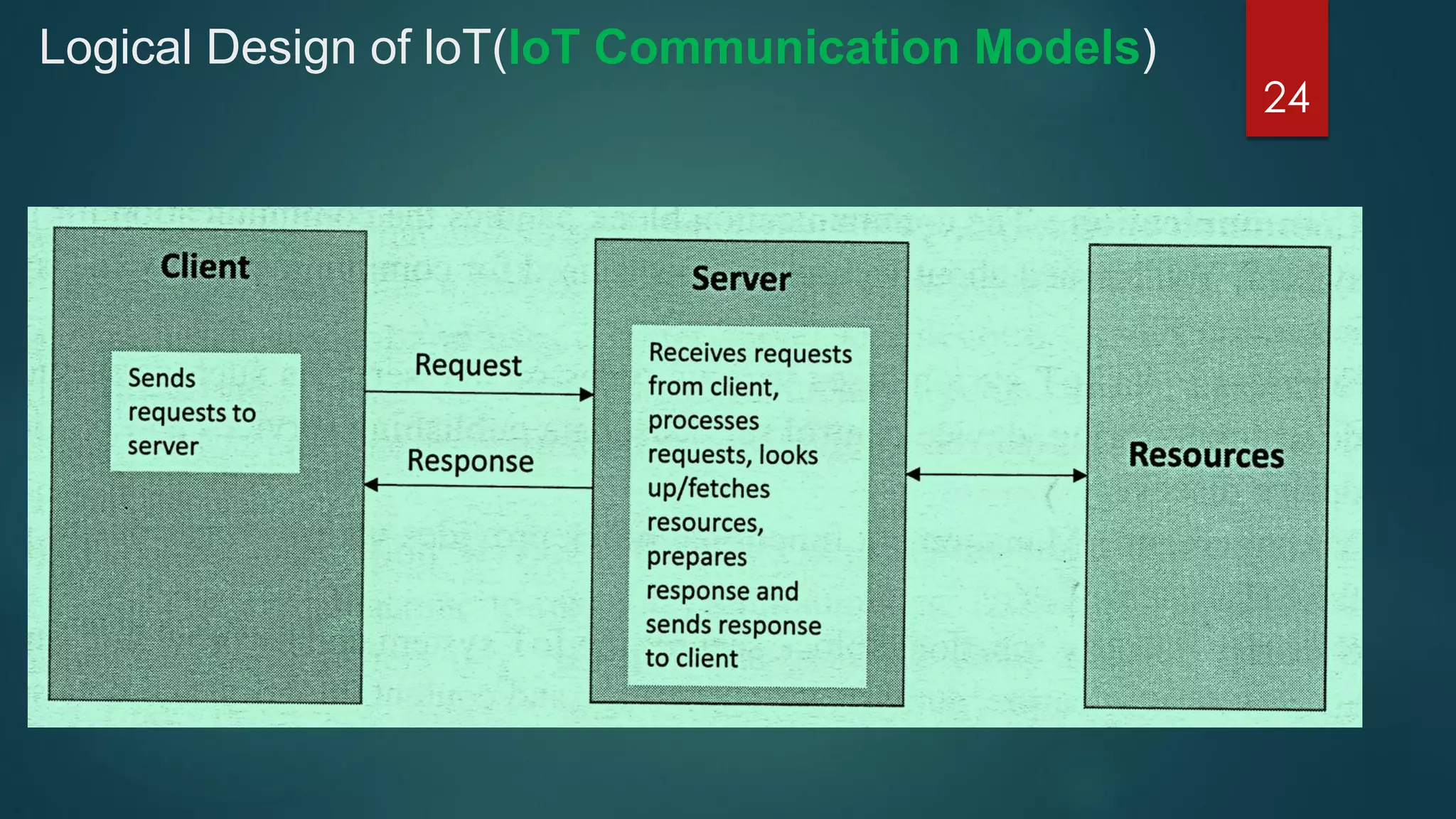
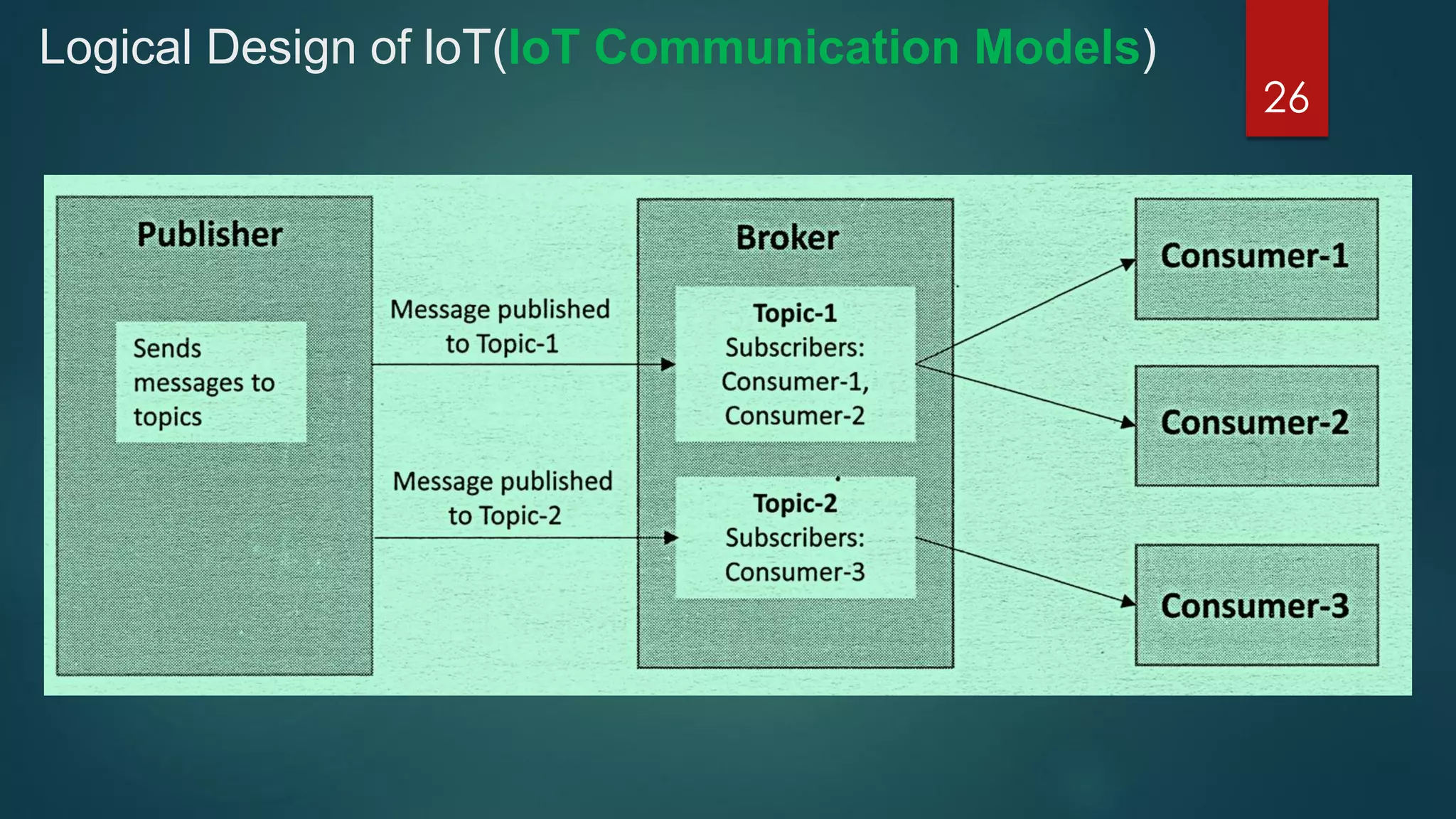
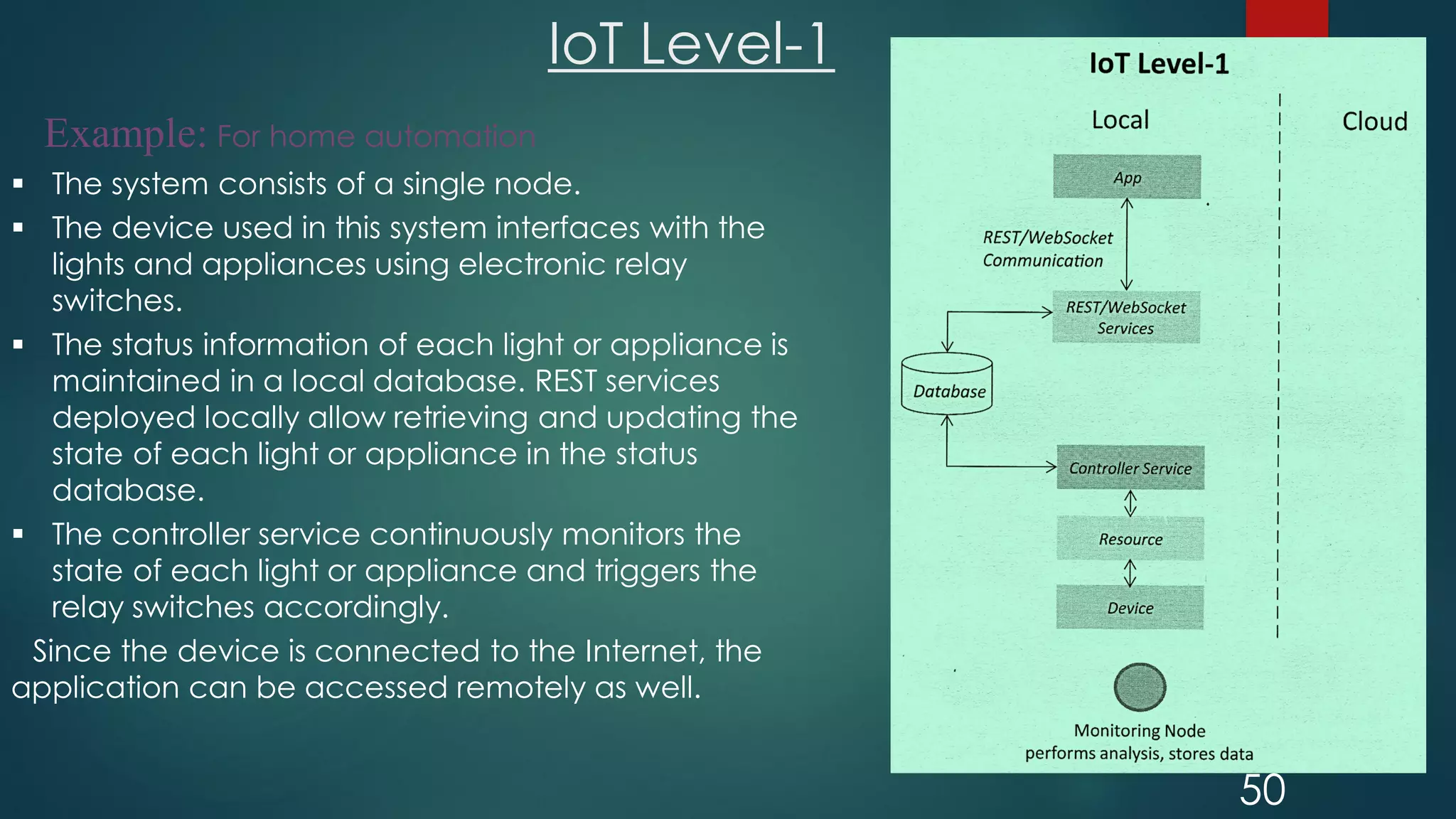
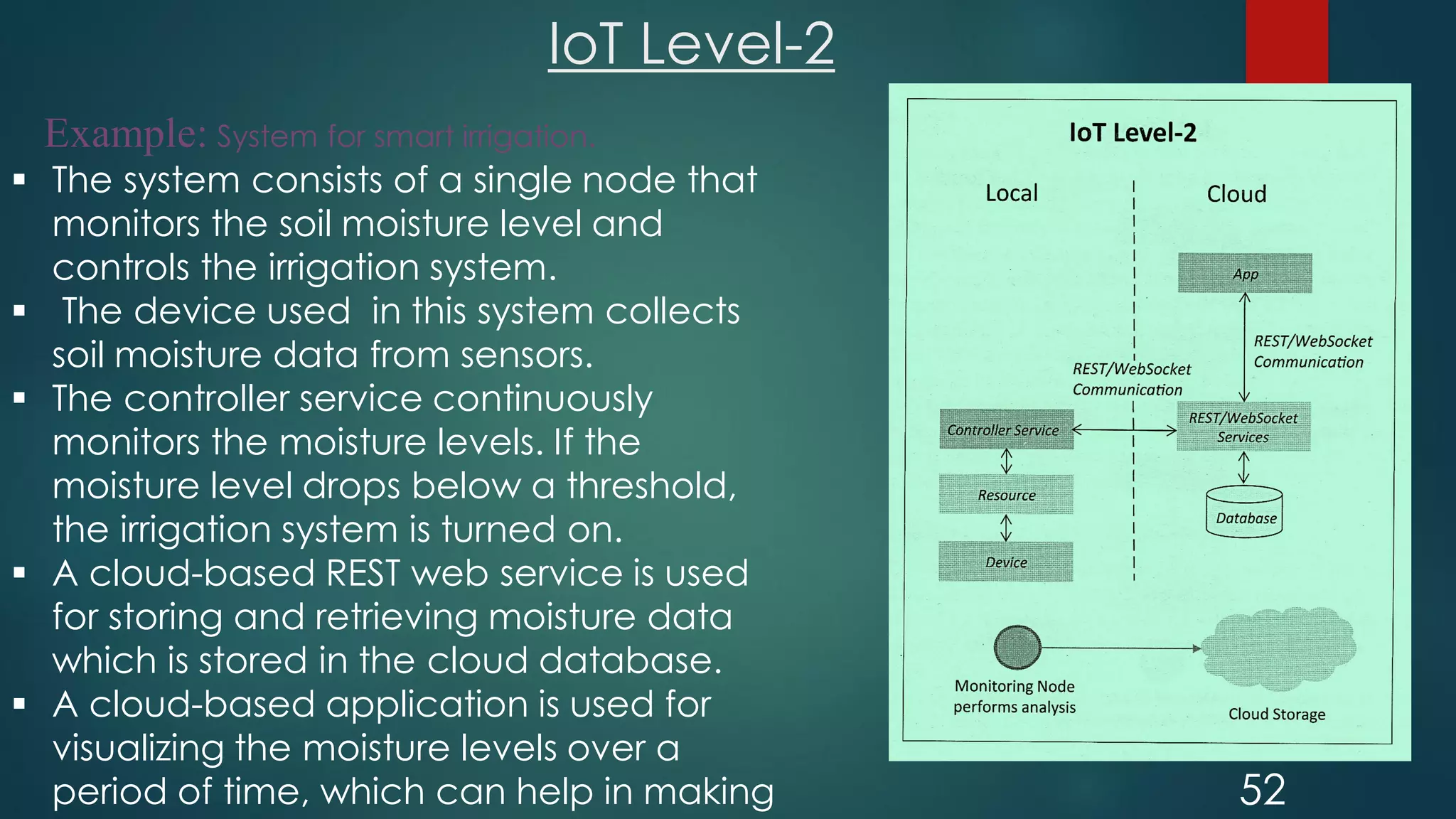
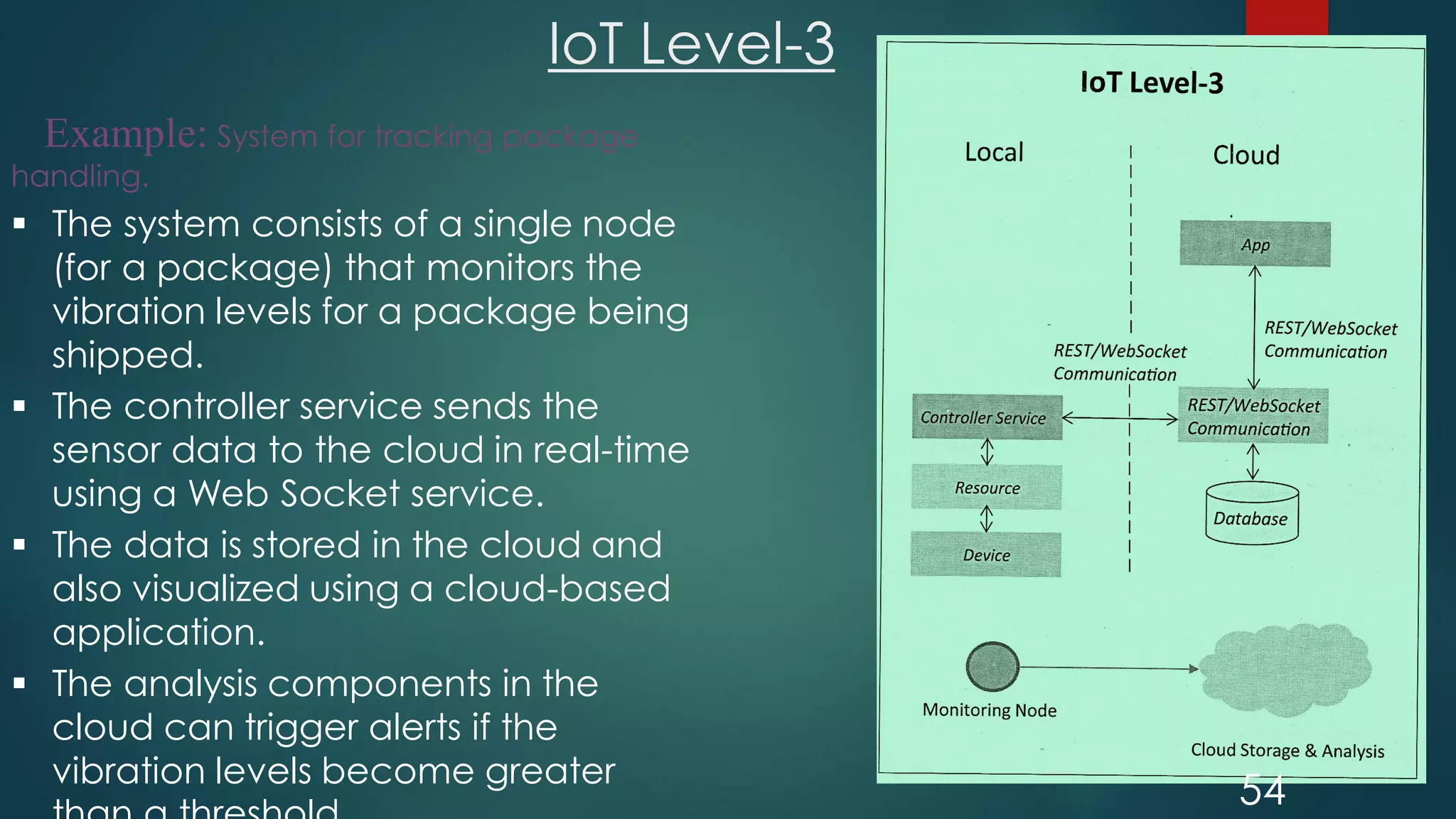
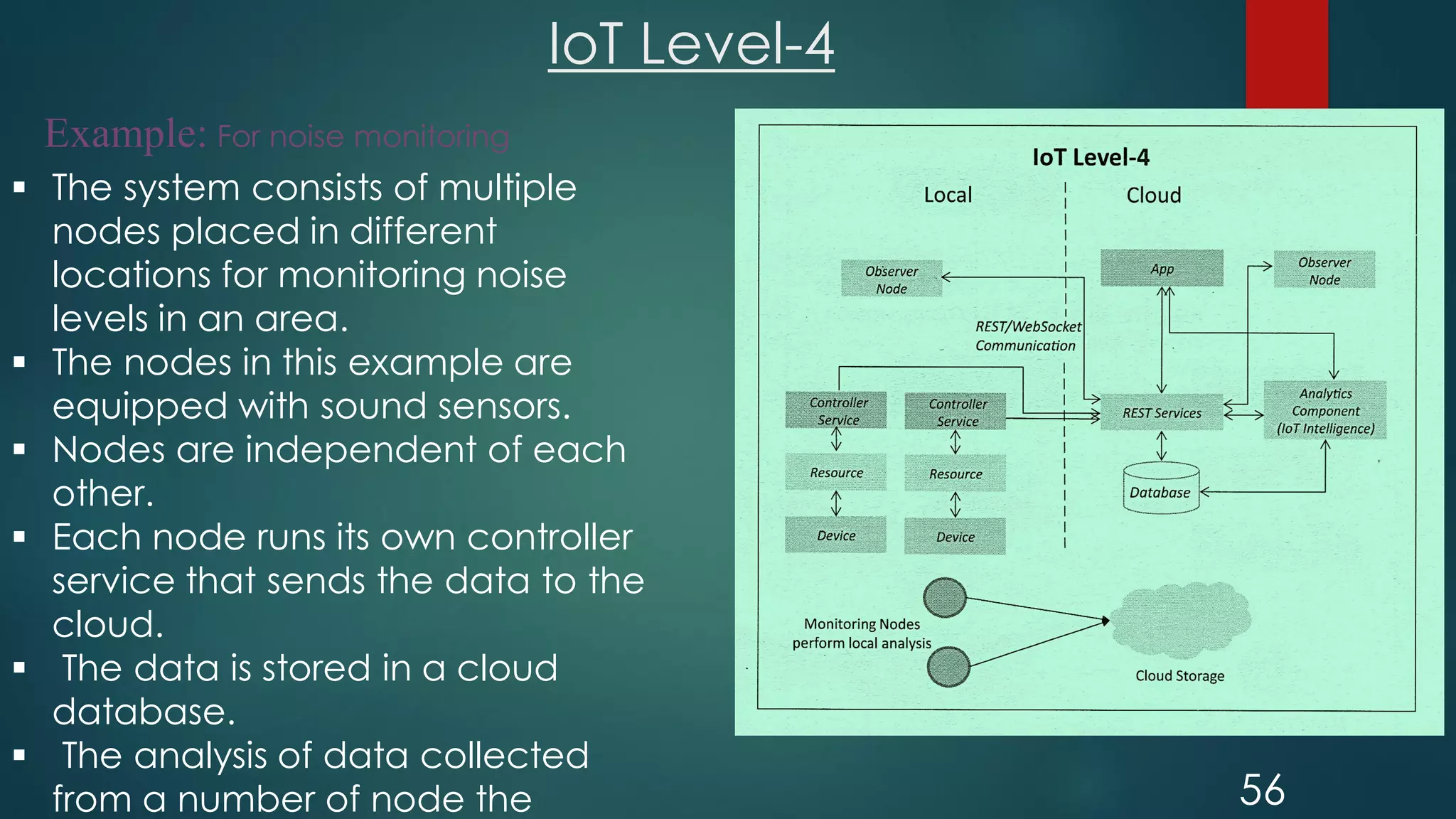
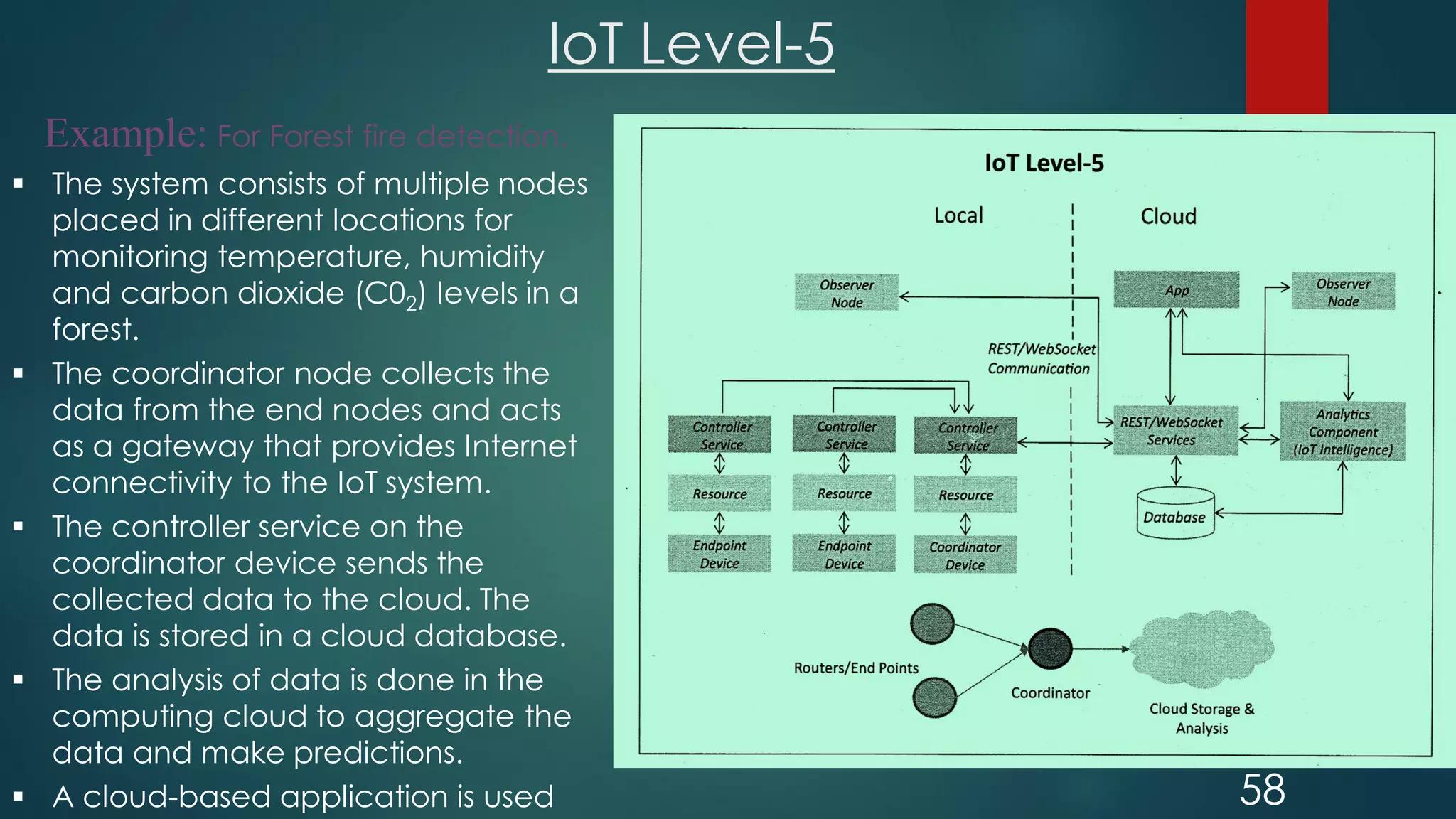
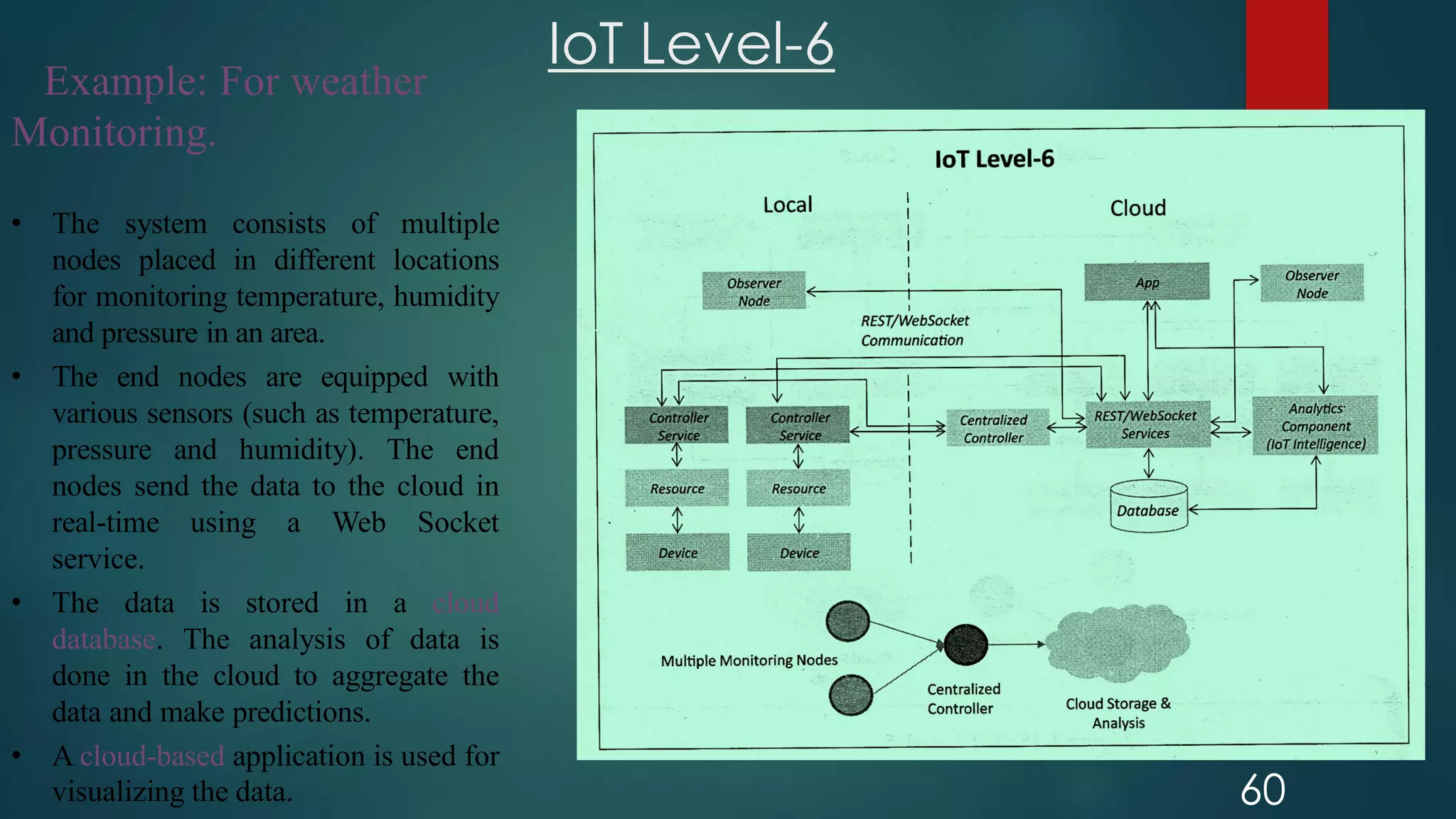
The document provides an introduction to Internet of Things (IoT). It defines IoT as comprising things that have unique identities and are connected to the Internet. It notes that while many existing devices like mobile phones are already connected, the focus of IoT is on traditionally unconnected devices like thermostats and sensors being networked. Experts forecast that by 2020 there will be 50 billion devices connected to the Internet. The document then discusses various aspects of IoT including the physical and logical design, enabling technologies, communication models, and deployment templates.