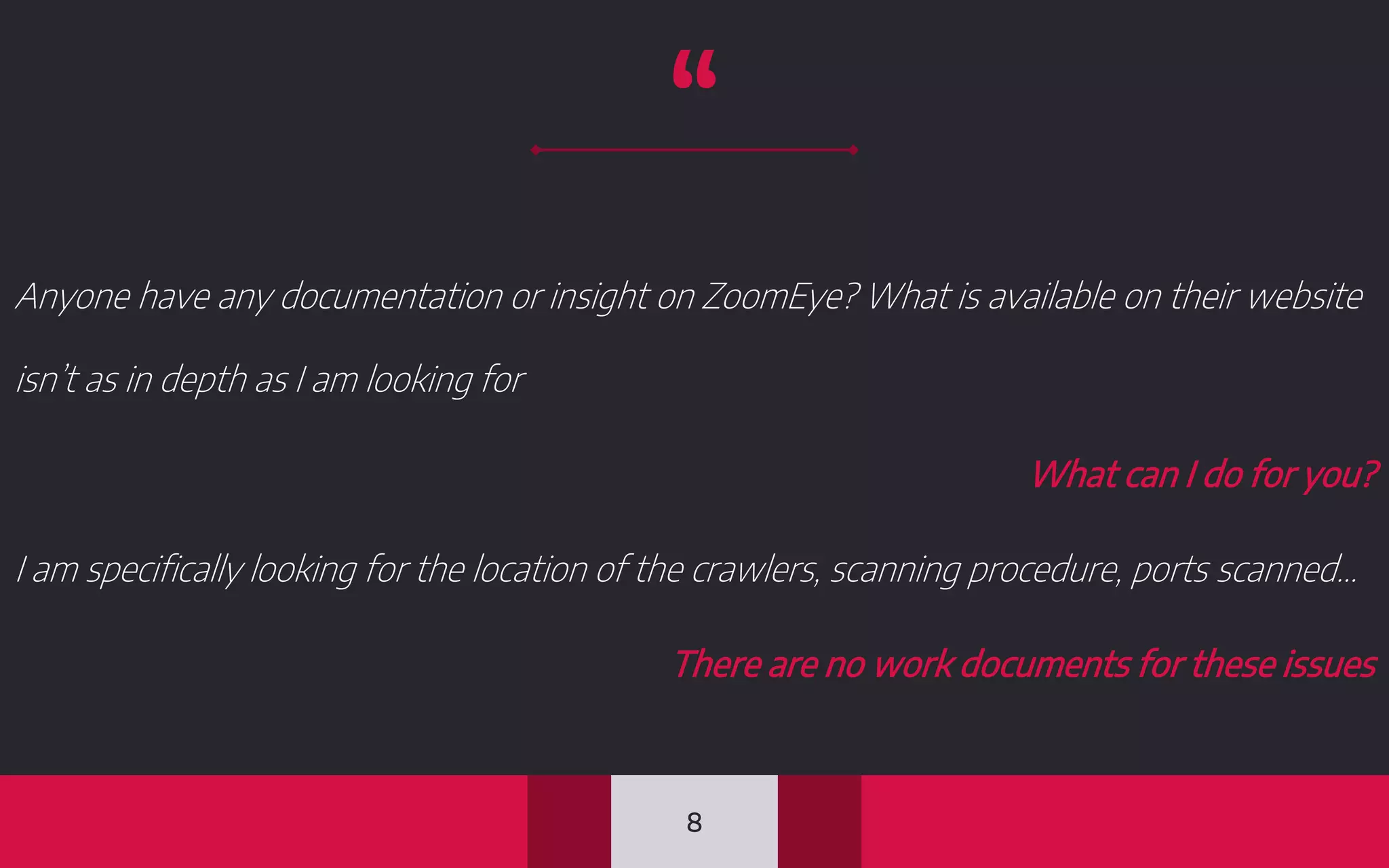
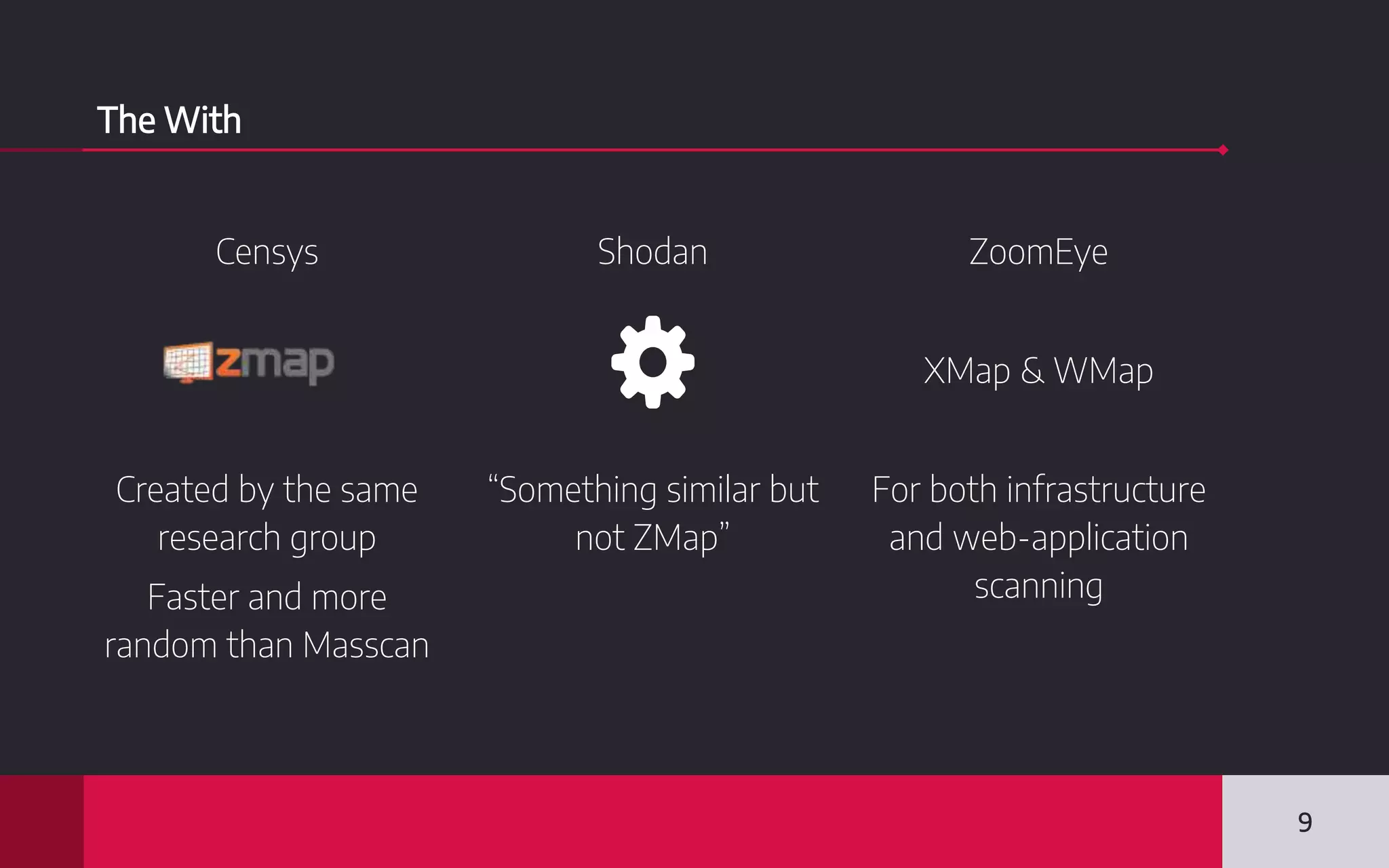
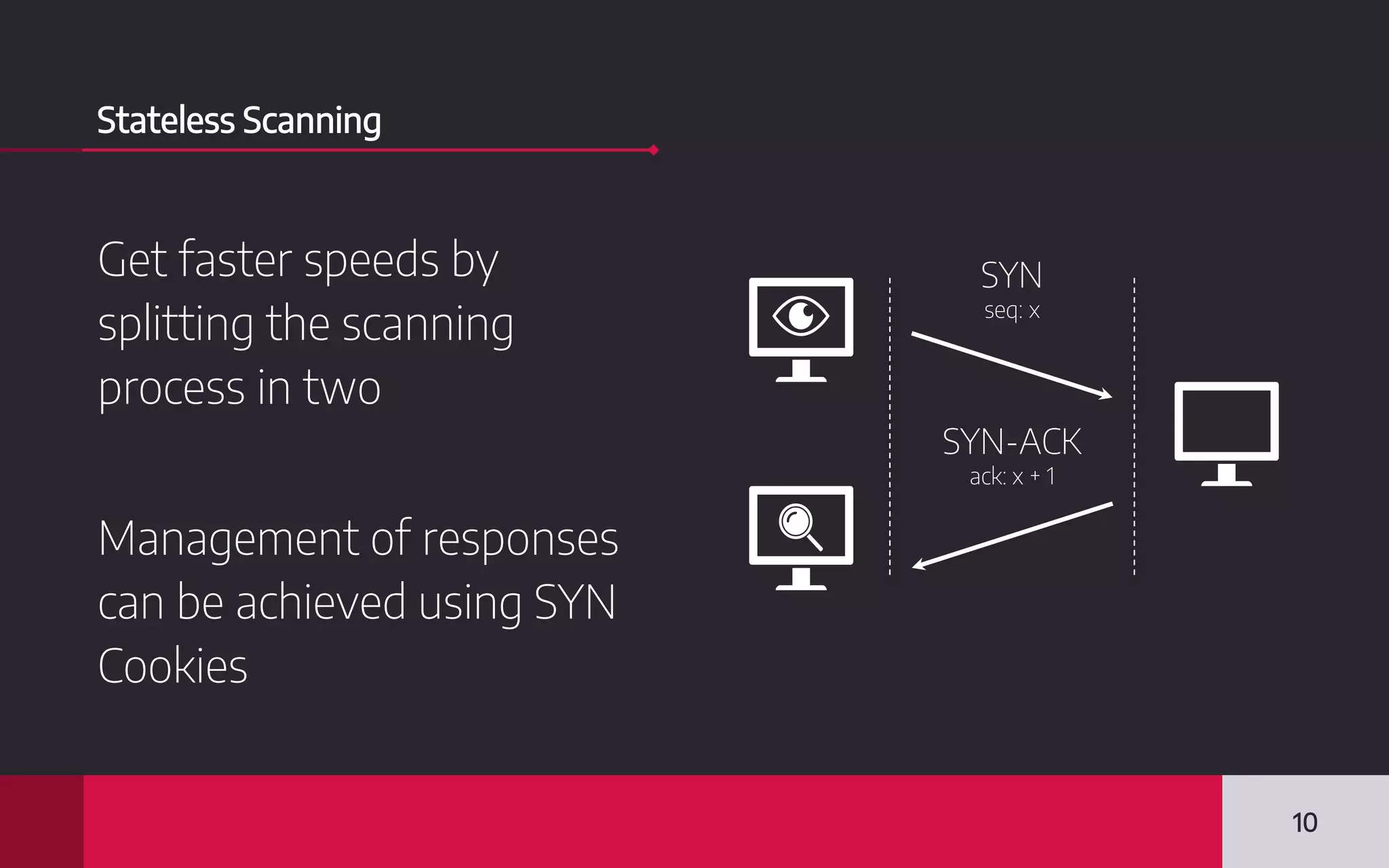
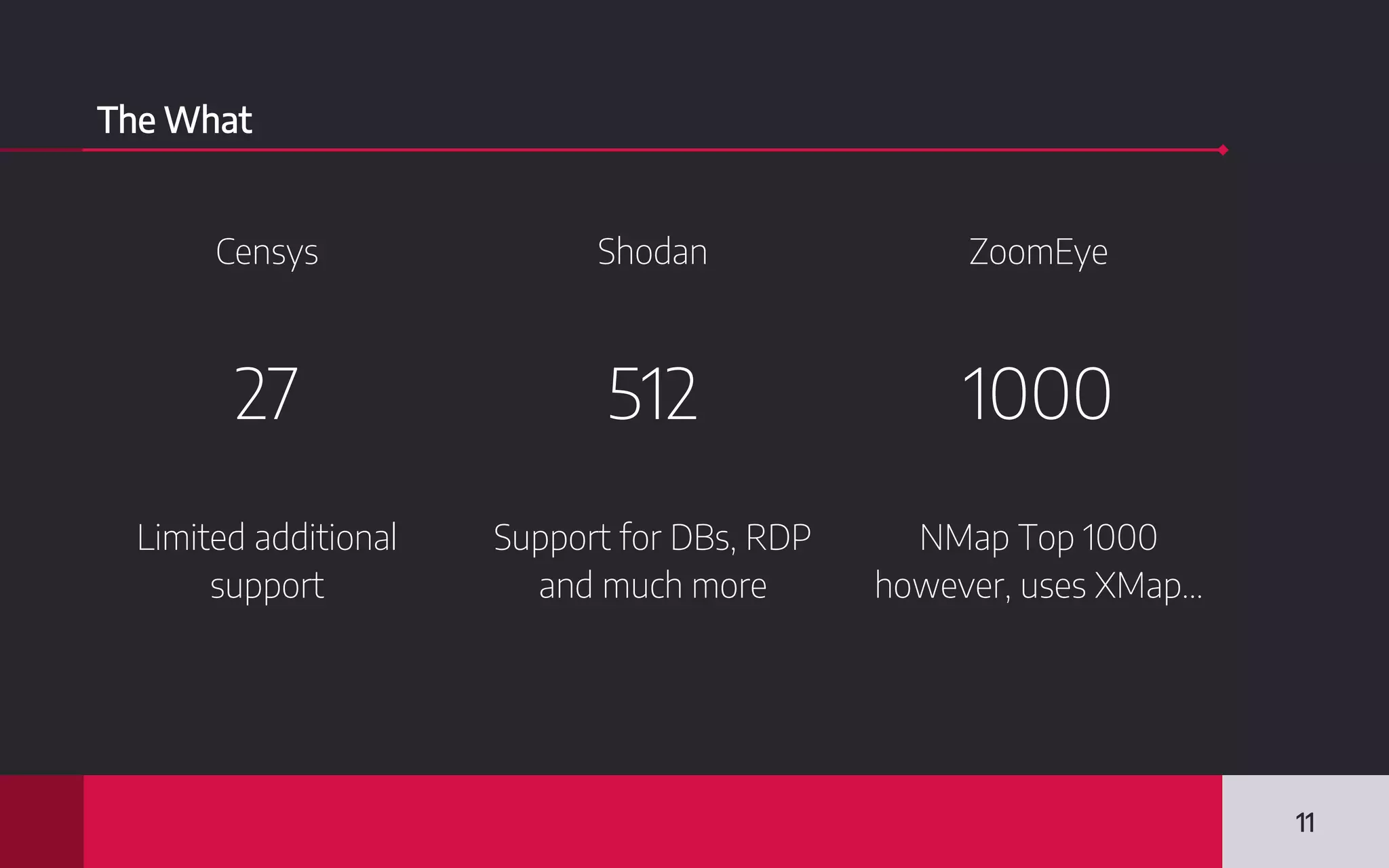
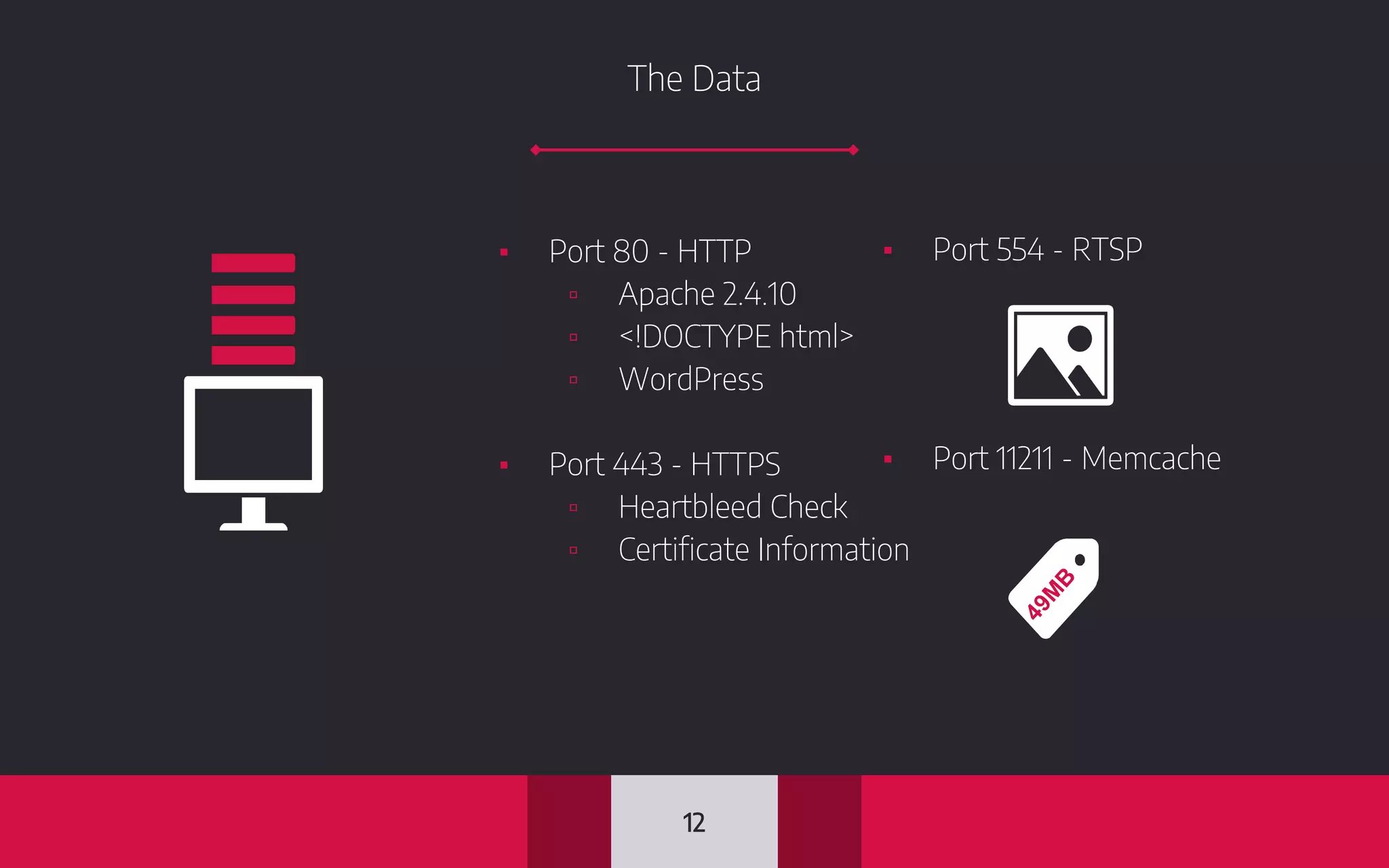
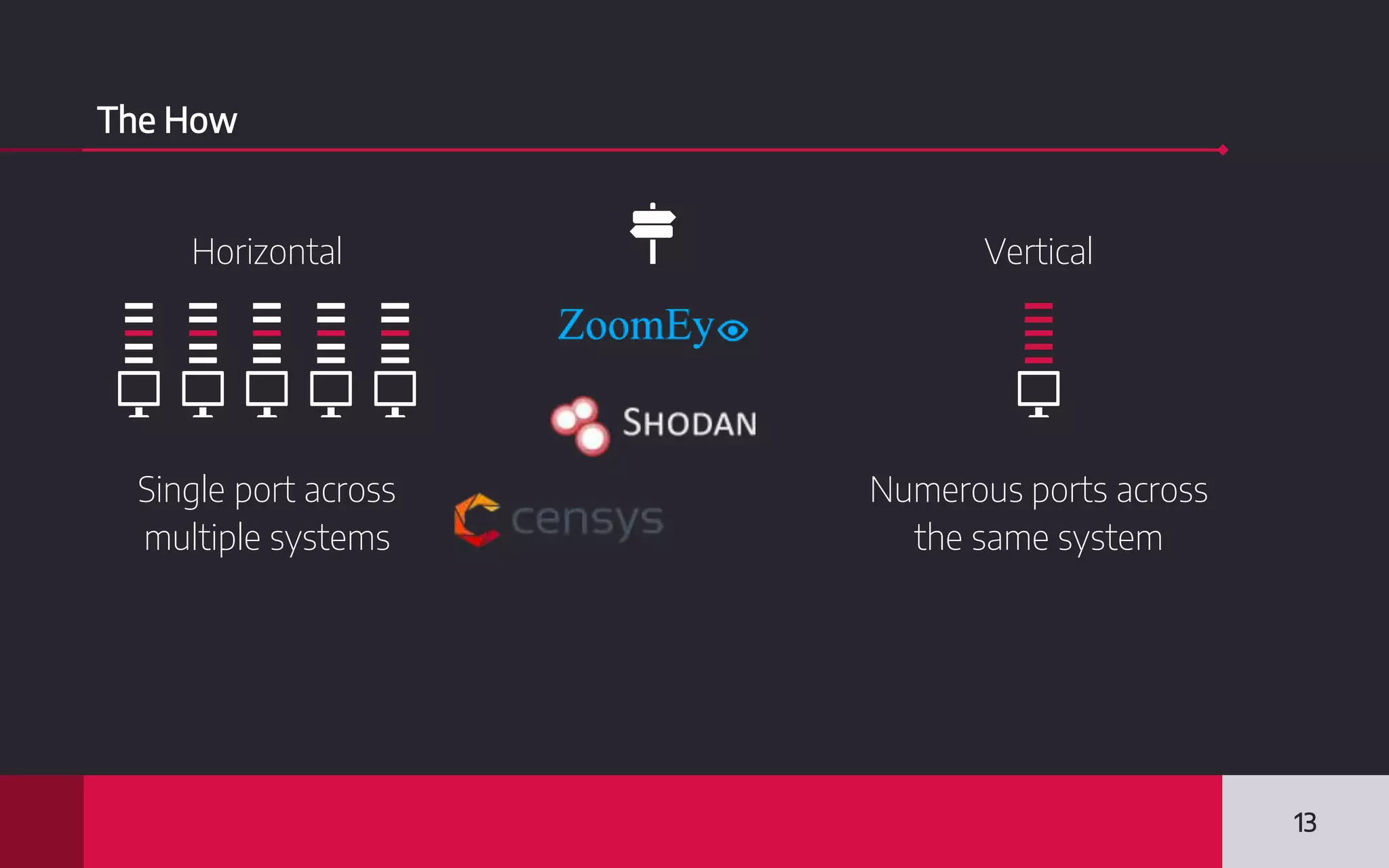
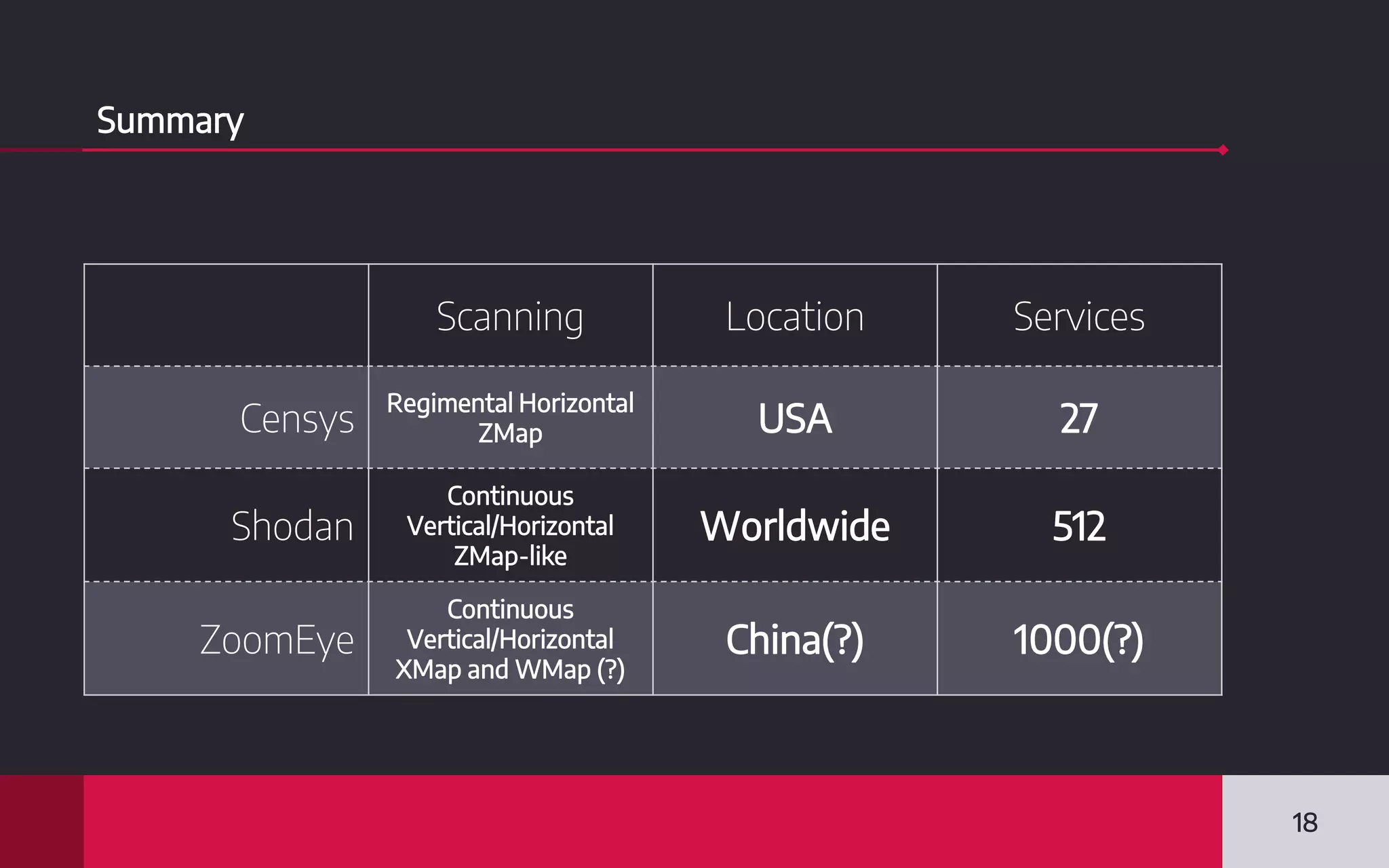
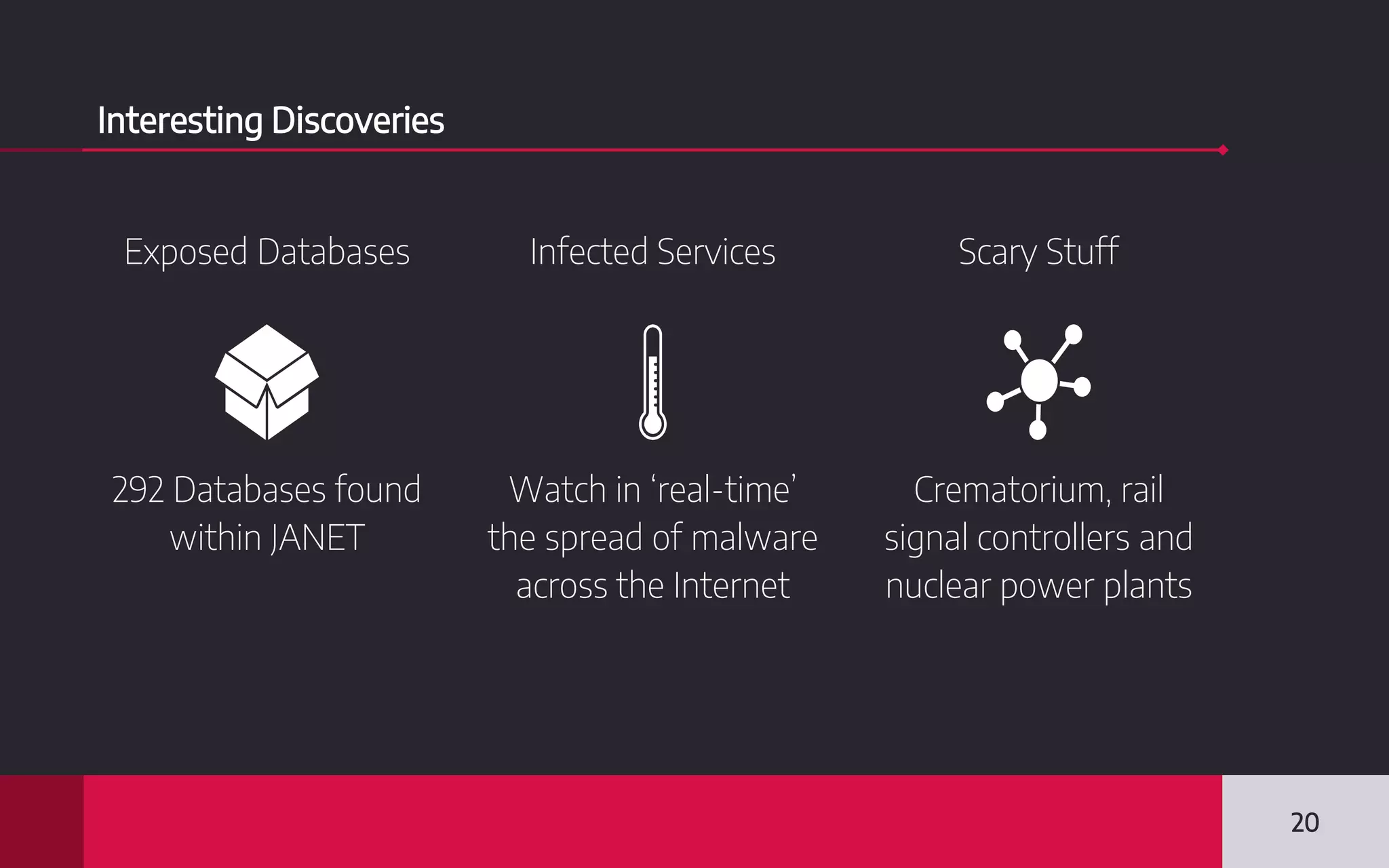
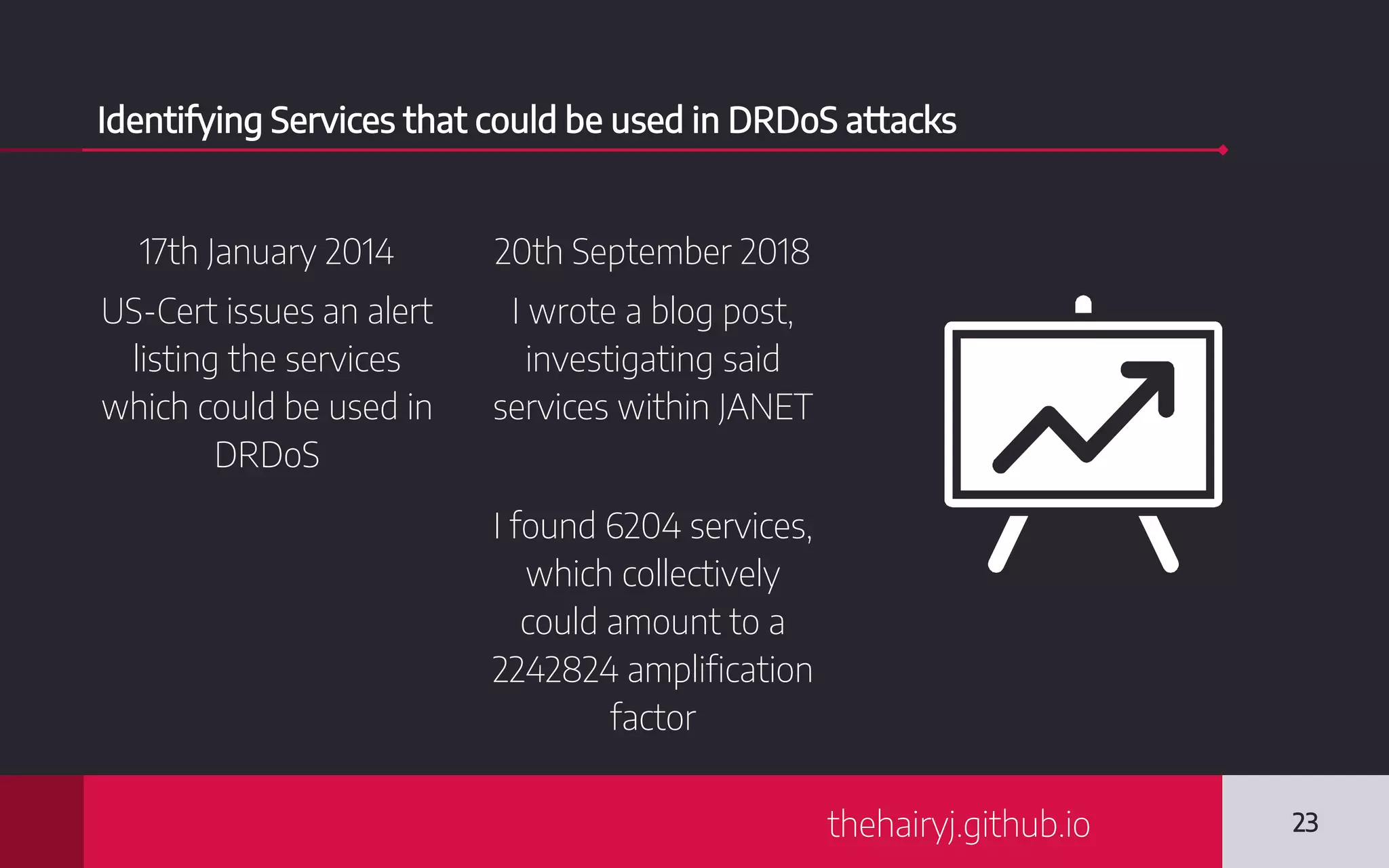
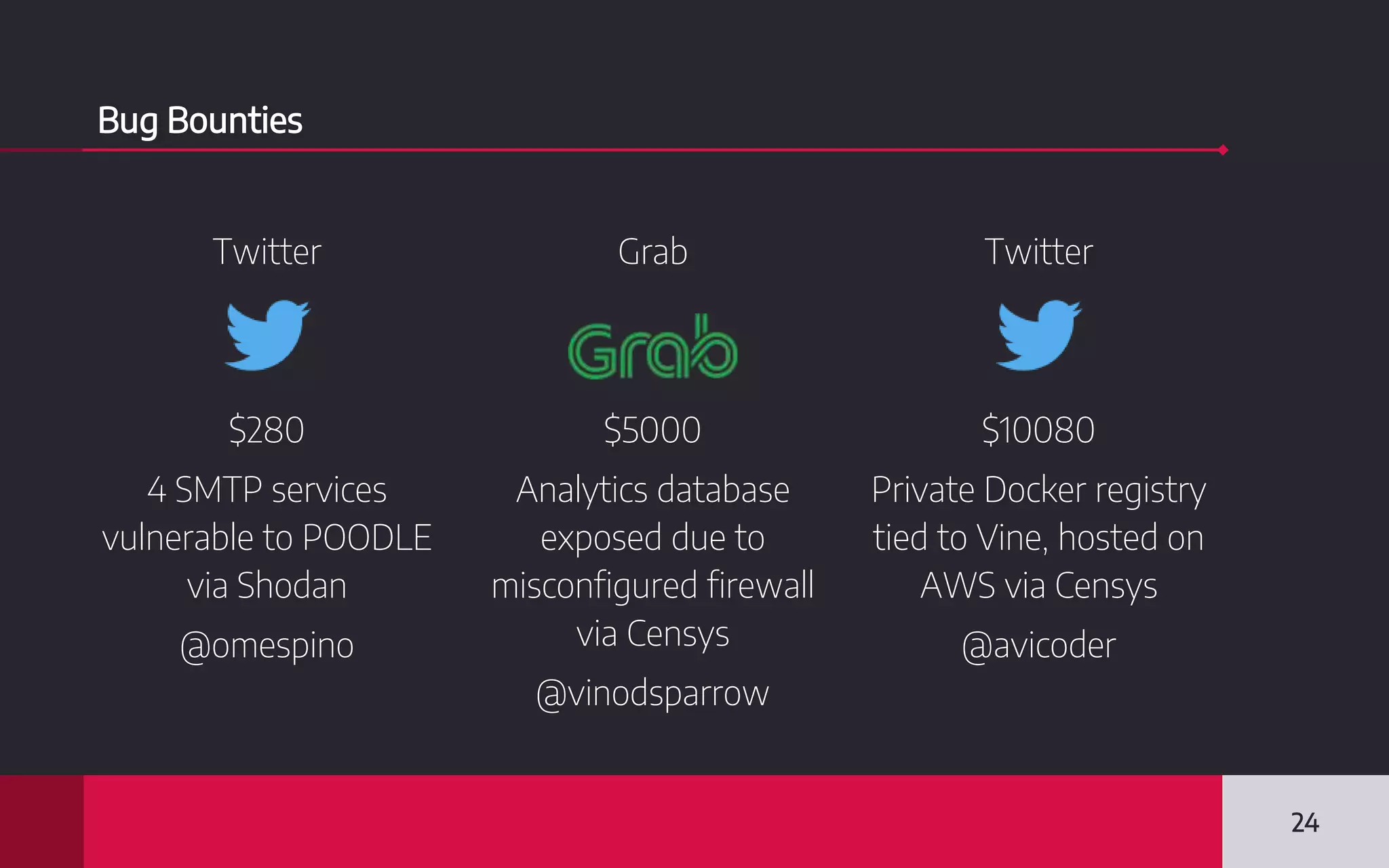
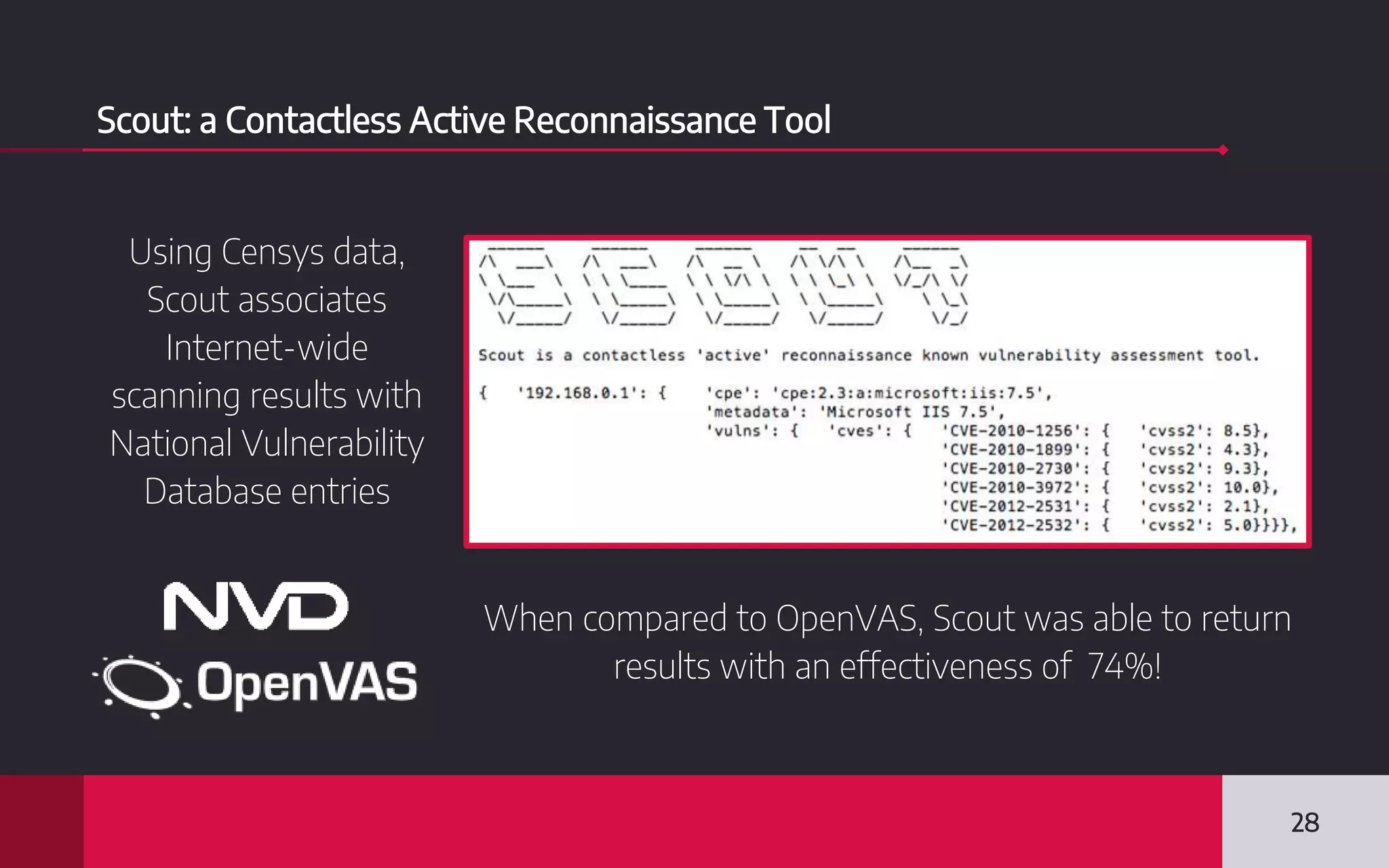
This document discusses internet-wide scanning tools like Censys, Shodan, and ZoomEye that scan publicly accessible systems and services on the internet. It provides details on the scanning procedures, ports scanned, locations of crawlers, and data collected by each tool. It also outlines several use cases for these tools, including identifying exposed databases, vulnerable services, and systems that could be used in distributed denial of service attacks. Researchers have used these scanning tools to identify vulnerabilities, conduct reconnaissance, and even earn bug bounties. The document advocates using these tools responsibly and keeping your own digital footprint secure.