Intercept product
•
0 likes•17 views
Intercept is a cybersecurity platform that automatically discovers all digital devices on a network to identify threats. It detects behavioral anomalies across endpoints, networks, and IoT devices to locate threats within 30 minutes, much faster than the industry average of 24 hours. Intercept provides full network coverage through active device discovery and resource-light agents. It seamlessly integrates with other tools for threat hunting, detection, response, and vulnerability management to protect organizations from attacks.
Report
Share
Report
Share
Download to read offline
Recommended
Intrusion detection and prevention system for network using Honey pots and Ho...

Intrusion detection and prevention system for network using Honey pots and Ho...Eng. Mohammed Ahmed Siddiqui
In this research work an Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) will be implemented to detect and prevent critical networks infrastructure from cyber-attacks. To strengthen network security and improve the network's active defense intrusion detection capabilities, this project will consist of intrusion detection system using honey token based encrypted pointers and intrusion prevention system which based on the mixed interactive honeypot. The Intrusion Detection System (IDS) is based on the novel approach of Honey Token based Encrypted Pointers. This honey token inside the frame will serve as a trap for the attacker. All nodes operating within the working domain of critical infrastructure network are divided into four different pools. This division is based per their computational power and level of vulnerability. These pools are provided with different levels of security measures within the network. IDS use different number of Honey Tokens (HT) per frame for every different pool e.g. Pool-A contains 4 HT/frame, Pool-B contains 3 HT/frame, Pool-C contains 2 HT/frame and Pool-D contain 1 HT/frame. Moreover, every pool uses different types of encryption schemes (AES-128,192,256). Our critical infrastructure network of 64 nodes is under the umbrella of unified security provided by this single Network Intrusion Detection System (NIDS). After the design phase of IDS, we analyze the performance of IDS in terms of True Positives (TP) and False Negatives (FN). Finally, we test these IDS through Network Penetration Testing (NPT) phase. The detection rate depends on the number of honey tokens per frame. Our proposed IDS are a scalable solution and it can be implemented for any number of nodes in critical infrastructure network. However, in case of Intrusion Prevention System (IPS) we use Virtual honeypot technology which is the best active prevention technology among all honeypot technologies. By using the original operating system and virtual technology, the honeypot lures attackers in a pre-arranged manner, analyzes and audits various attacking behavior, tracks the attack source, obtains evidence, and finds effective solutions.
call for papers, research paper publishing, where to publish research paper, ...

call for papers, research paper publishing, where to publish research paper, ...International Journal of Engineering Inventions www.ijeijournal.com
Intrusion detection system 

hey guys here comes my new implementation of my learning i.e the IDS a concept of network security go through it and add your valuable comments
A hybrid intrusion detection system for cloud computing environments

A hybrid intrusion detection system for cloud computing environments
Network security - Defense in Depth

Network security all around, from firewalls to host-level hardening
NGIPS(Next Generation Intrusion Prevention System) in Network security presen...

in this slide i've sgare all details about Next Generation Intrusion Prevention System also known as NGIPS in network security.
FORTIFICATION OF HYBRID INTRUSION DETECTION SYSTEM USING VARIANTS OF NEURAL ...

Intrusion Detection Systems (IDS) form a key part of system defence, where it identifies abnormal
activities happening in a computer system. In recent years different soft computing based techniques have
been proposed for the development of IDS. On the other hand, intrusion detection is not yet a perfect
technology. This has provided an opportunity for data mining to make quite a lot of important
contributions in the field of intrusion detection. In this paper we have proposed a new hybrid technique
by utilizing data mining techniques such as fuzzy C means clustering, Fuzzy neural network / Neurofuzzy and radial basis function(RBF) SVM for fortification of the intrusion detection system. The
proposed technique has five major steps in which, first step is to perform the relevance analysis, and then
input data is clustered using Fuzzy C-means clustering. After that, neuro-fuzzy is trained, such that each
of the data point is trained with the corresponding neuro-fuzzy classifier associated with the cluster.
Subsequently, a vector for SVM classification is formed and in the last step, classification using RBF-
SVM is performed to detect intrusion has happened or not. Data set used is the KDD cup 1999 dataset
and we have used precision, recall, F-measure and accuracy as the evaluation metrics parameters. Our
technique could achieve better accuracy for all types of intrusions. The results of proposed technique are
compared with the other existing techniques. These comparisons proved the effectiveness of our
technique.
Recommended
Intrusion detection and prevention system for network using Honey pots and Ho...

Intrusion detection and prevention system for network using Honey pots and Ho...Eng. Mohammed Ahmed Siddiqui
In this research work an Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) will be implemented to detect and prevent critical networks infrastructure from cyber-attacks. To strengthen network security and improve the network's active defense intrusion detection capabilities, this project will consist of intrusion detection system using honey token based encrypted pointers and intrusion prevention system which based on the mixed interactive honeypot. The Intrusion Detection System (IDS) is based on the novel approach of Honey Token based Encrypted Pointers. This honey token inside the frame will serve as a trap for the attacker. All nodes operating within the working domain of critical infrastructure network are divided into four different pools. This division is based per their computational power and level of vulnerability. These pools are provided with different levels of security measures within the network. IDS use different number of Honey Tokens (HT) per frame for every different pool e.g. Pool-A contains 4 HT/frame, Pool-B contains 3 HT/frame, Pool-C contains 2 HT/frame and Pool-D contain 1 HT/frame. Moreover, every pool uses different types of encryption schemes (AES-128,192,256). Our critical infrastructure network of 64 nodes is under the umbrella of unified security provided by this single Network Intrusion Detection System (NIDS). After the design phase of IDS, we analyze the performance of IDS in terms of True Positives (TP) and False Negatives (FN). Finally, we test these IDS through Network Penetration Testing (NPT) phase. The detection rate depends on the number of honey tokens per frame. Our proposed IDS are a scalable solution and it can be implemented for any number of nodes in critical infrastructure network. However, in case of Intrusion Prevention System (IPS) we use Virtual honeypot technology which is the best active prevention technology among all honeypot technologies. By using the original operating system and virtual technology, the honeypot lures attackers in a pre-arranged manner, analyzes and audits various attacking behavior, tracks the attack source, obtains evidence, and finds effective solutions.
call for papers, research paper publishing, where to publish research paper, ...

call for papers, research paper publishing, where to publish research paper, ...International Journal of Engineering Inventions www.ijeijournal.com
Intrusion detection system 

hey guys here comes my new implementation of my learning i.e the IDS a concept of network security go through it and add your valuable comments
A hybrid intrusion detection system for cloud computing environments

A hybrid intrusion detection system for cloud computing environments
Network security - Defense in Depth

Network security all around, from firewalls to host-level hardening
NGIPS(Next Generation Intrusion Prevention System) in Network security presen...

in this slide i've sgare all details about Next Generation Intrusion Prevention System also known as NGIPS in network security.
FORTIFICATION OF HYBRID INTRUSION DETECTION SYSTEM USING VARIANTS OF NEURAL ...

Intrusion Detection Systems (IDS) form a key part of system defence, where it identifies abnormal
activities happening in a computer system. In recent years different soft computing based techniques have
been proposed for the development of IDS. On the other hand, intrusion detection is not yet a perfect
technology. This has provided an opportunity for data mining to make quite a lot of important
contributions in the field of intrusion detection. In this paper we have proposed a new hybrid technique
by utilizing data mining techniques such as fuzzy C means clustering, Fuzzy neural network / Neurofuzzy and radial basis function(RBF) SVM for fortification of the intrusion detection system. The
proposed technique has five major steps in which, first step is to perform the relevance analysis, and then
input data is clustered using Fuzzy C-means clustering. After that, neuro-fuzzy is trained, such that each
of the data point is trained with the corresponding neuro-fuzzy classifier associated with the cluster.
Subsequently, a vector for SVM classification is formed and in the last step, classification using RBF-
SVM is performed to detect intrusion has happened or not. Data set used is the KDD cup 1999 dataset
and we have used precision, recall, F-measure and accuracy as the evaluation metrics parameters. Our
technique could achieve better accuracy for all types of intrusions. The results of proposed technique are
compared with the other existing techniques. These comparisons proved the effectiveness of our
technique.
RSA Anatomy of an Attack

Presentation slides from the Anatomy of an Attack Briefing by RSA and Integrity Solutions focusing on the security breach experienced by RSA in 2011.
Cloudslam09:Building a Cloud Computing Analysis System for Intrusion Detection

In order to resolve huge amount of anomaly
information generated by Intrusion Detection System (IDS), this paper presents and evaluates a log analysis system for IDS based on Cloud Computing technique,
named IDS Cloud Analysis System (ICAS). To achieve this, there are two basic components have to be designed. First is the regular parser, which normalizes
the raw log files. The other is the Analysis Procedure, which contains Data Mapper and Data Reducer. The Data Mapper is designed to anatomize alert messages and the Data Reducer is used to aggregates and merges. As a result, this paper will show that the
performance of ICAS is suitable for analyzing and reducing large alerts.
Intrusion Detection System Project Report

The following project " Intrusion Detection System " Modules Are :-
1. Firewall
2. Honeypot
3. Dos / Ddos Attack Detection Programs
4. Log Management
Sourcefire Webinar - NEW GENERATION IPS

Preview delle ultime novità di prodotto Sourcefire IPS Entriamo in dettaglio delle novità di prodotto annunciate da Sourcefire nell\’ultimo mese, incluso:
New 3D8000 Series Sensors with FirePOWER
New Defense Center Models
New IPSx Solution
Intrusion detection system

It's power-point presentation on software application that monitors a network or systems for malicious activity or policy violations.
Intrusion detection and prevention system

This presentation describes how to implement Network based Intrusion Detection System (SNORT) in the network. Detecting and analyzing alerts generated and blocking the Attacker using Access Control List.
Using Genetic algorithm for Network Intrusion Detection

Using Genetic algorithm for Network Intrusion Detection : Genetic Algorithm IDS involves detecting the intrusion based on the log history, possible intrusions that are likely to occur. In Genetic Algorithm, each connection will be considered as a chromosome” which consists of many “genes” ( properties of the connection like : sourceIP, targetIP, port no., protocol …), One has to find the fitness value of each such chromosomes to detect intrusion.
INTRUSION DETECTION TECHNIQUES

Computer Application- INTRUSION DETECTION TECHNIQUES
Statistical anomaly detection
Threshold detection
Rule-based detection
Anomaly detection
Penetration identification
Time-Stamp
Resource-Usage
Exception-Condition
apl5iy2ftxiwofbhsmxj-signature-584e2459f99b5370bda435f09b42cc84cc8c063b8cd454...

apl5iy2ftxiwofbhsmxj-signature-584e2459f99b5370bda435f09b42cc84cc8c063b8cd454...Chrysostomos Christofi
IPS (intrusion prevention system)

IPS (Intrusion Prevention System) is definitely the next level of security technology with its capability to
provide security at all system levels from the operating system kernel to network data packets. It
provides policies and rules for network traffic along with an IDS for alerting system or network
administrators to suspicious traffic, but allows the administrator to provide the action upon being
alerted. Where IDS informs of a potential attack, an IPS makes attempts to stop it. Another huge leap
over IDS, is that IPS has the capability of being able to prevent known intrusion signatures, but also
some unknown attacks due to its database of generic attack behaviours. Thought of as a combination of
IDS and an application layer firewall for protection, IPS is generally considered to be the "next
generation" of IDS.
DTS Solution - Wireless Security Protocols / PenTesting 

DTS Solution presents wireless security protocols and attack vectors to break into the wireless security protocols.
Hunting: Defense Against The Dark Arts

This presentation was delivered at BSides Augusta in September 2016. The A/V portion is available here: https://www.youtube.com/watch?v=i6p71t9PFWM
Abstract:
"We can all agree that threat ("Evil") detection is an essential component of a functioning security monitoring program. Let's start thinking about how to take our tradecraft to the next level and hunt for insecure conditions ("Ways for Evil to do Evil things") that might allow threat actors to succeed in their mission.
This talk will run through some of the observations gathered during hunting expeditions inside the networks of multiple Fortune-ranked organizations and challenge you to expand your security operations thinking beyond signature-based detection.
- What is Hunting?
- How have we done it?
- What have we found, and what should be done about those findings?
- How might you achieve similar outcomes in your own environment?"
Speakers:
- Jacqueline Stokes (@find_evil) is an infosec enthusiast who picked up hacking as a preteen and cut her teeth over multiple years in Iraq. Her ongoing mission is to assess and advise clients on the most actionable and forward-thinking methods to improve detection, response, and containment of advanced threats. Jackie likes long walks on the beach, 90's nostalgia, and is the president and founding member of the Kevin Mandia Fan Club.
- Danny Akacki (@dakacki) was a Lead Analyst with GE Capitals' Applied Intelligence team prior to his employment with Mandiant, and now works for Bank of America's hunt team. He is a pragmatic optimist and believes we are probably screwed, but hopes we aren't. Danny enjoys finding evil on the weekends.
- Stephen Hinck (@stephenhinck) is a Senior Security Analyst at Oracle, Inc. Stephen stumbled into the information security world years ago and has since only managed to dig his way deeper to the rabbit hole. With a background in security operations, incident response and threat hunting, Stephen's experience is multi-faceted. Although he enjoys many things, he absolutely hates writing silly bios like this one.
Proactive Security That Works

Presentation on the first proactive and collaborative anti-cyber warfare technology.
More Related Content
What's hot
RSA Anatomy of an Attack

Presentation slides from the Anatomy of an Attack Briefing by RSA and Integrity Solutions focusing on the security breach experienced by RSA in 2011.
Cloudslam09:Building a Cloud Computing Analysis System for Intrusion Detection

In order to resolve huge amount of anomaly
information generated by Intrusion Detection System (IDS), this paper presents and evaluates a log analysis system for IDS based on Cloud Computing technique,
named IDS Cloud Analysis System (ICAS). To achieve this, there are two basic components have to be designed. First is the regular parser, which normalizes
the raw log files. The other is the Analysis Procedure, which contains Data Mapper and Data Reducer. The Data Mapper is designed to anatomize alert messages and the Data Reducer is used to aggregates and merges. As a result, this paper will show that the
performance of ICAS is suitable for analyzing and reducing large alerts.
Intrusion Detection System Project Report

The following project " Intrusion Detection System " Modules Are :-
1. Firewall
2. Honeypot
3. Dos / Ddos Attack Detection Programs
4. Log Management
Sourcefire Webinar - NEW GENERATION IPS

Preview delle ultime novità di prodotto Sourcefire IPS Entriamo in dettaglio delle novità di prodotto annunciate da Sourcefire nell\’ultimo mese, incluso:
New 3D8000 Series Sensors with FirePOWER
New Defense Center Models
New IPSx Solution
Intrusion detection system

It's power-point presentation on software application that monitors a network or systems for malicious activity or policy violations.
Intrusion detection and prevention system

This presentation describes how to implement Network based Intrusion Detection System (SNORT) in the network. Detecting and analyzing alerts generated and blocking the Attacker using Access Control List.
Using Genetic algorithm for Network Intrusion Detection

Using Genetic algorithm for Network Intrusion Detection : Genetic Algorithm IDS involves detecting the intrusion based on the log history, possible intrusions that are likely to occur. In Genetic Algorithm, each connection will be considered as a chromosome” which consists of many “genes” ( properties of the connection like : sourceIP, targetIP, port no., protocol …), One has to find the fitness value of each such chromosomes to detect intrusion.
INTRUSION DETECTION TECHNIQUES

Computer Application- INTRUSION DETECTION TECHNIQUES
Statistical anomaly detection
Threshold detection
Rule-based detection
Anomaly detection
Penetration identification
Time-Stamp
Resource-Usage
Exception-Condition
apl5iy2ftxiwofbhsmxj-signature-584e2459f99b5370bda435f09b42cc84cc8c063b8cd454...

apl5iy2ftxiwofbhsmxj-signature-584e2459f99b5370bda435f09b42cc84cc8c063b8cd454...Chrysostomos Christofi
IPS (intrusion prevention system)

IPS (Intrusion Prevention System) is definitely the next level of security technology with its capability to
provide security at all system levels from the operating system kernel to network data packets. It
provides policies and rules for network traffic along with an IDS for alerting system or network
administrators to suspicious traffic, but allows the administrator to provide the action upon being
alerted. Where IDS informs of a potential attack, an IPS makes attempts to stop it. Another huge leap
over IDS, is that IPS has the capability of being able to prevent known intrusion signatures, but also
some unknown attacks due to its database of generic attack behaviours. Thought of as a combination of
IDS and an application layer firewall for protection, IPS is generally considered to be the "next
generation" of IDS.
DTS Solution - Wireless Security Protocols / PenTesting 

DTS Solution presents wireless security protocols and attack vectors to break into the wireless security protocols.
Hunting: Defense Against The Dark Arts

This presentation was delivered at BSides Augusta in September 2016. The A/V portion is available here: https://www.youtube.com/watch?v=i6p71t9PFWM
Abstract:
"We can all agree that threat ("Evil") detection is an essential component of a functioning security monitoring program. Let's start thinking about how to take our tradecraft to the next level and hunt for insecure conditions ("Ways for Evil to do Evil things") that might allow threat actors to succeed in their mission.
This talk will run through some of the observations gathered during hunting expeditions inside the networks of multiple Fortune-ranked organizations and challenge you to expand your security operations thinking beyond signature-based detection.
- What is Hunting?
- How have we done it?
- What have we found, and what should be done about those findings?
- How might you achieve similar outcomes in your own environment?"
Speakers:
- Jacqueline Stokes (@find_evil) is an infosec enthusiast who picked up hacking as a preteen and cut her teeth over multiple years in Iraq. Her ongoing mission is to assess and advise clients on the most actionable and forward-thinking methods to improve detection, response, and containment of advanced threats. Jackie likes long walks on the beach, 90's nostalgia, and is the president and founding member of the Kevin Mandia Fan Club.
- Danny Akacki (@dakacki) was a Lead Analyst with GE Capitals' Applied Intelligence team prior to his employment with Mandiant, and now works for Bank of America's hunt team. He is a pragmatic optimist and believes we are probably screwed, but hopes we aren't. Danny enjoys finding evil on the weekends.
- Stephen Hinck (@stephenhinck) is a Senior Security Analyst at Oracle, Inc. Stephen stumbled into the information security world years ago and has since only managed to dig his way deeper to the rabbit hole. With a background in security operations, incident response and threat hunting, Stephen's experience is multi-faceted. Although he enjoys many things, he absolutely hates writing silly bios like this one.
What's hot (19)
Cloudslam09:Building a Cloud Computing Analysis System for Intrusion Detection

Cloudslam09:Building a Cloud Computing Analysis System for Intrusion Detection
Using Genetic algorithm for Network Intrusion Detection

Using Genetic algorithm for Network Intrusion Detection
apl5iy2ftxiwofbhsmxj-signature-584e2459f99b5370bda435f09b42cc84cc8c063b8cd454...

apl5iy2ftxiwofbhsmxj-signature-584e2459f99b5370bda435f09b42cc84cc8c063b8cd454...
DTS Solution - Wireless Security Protocols / PenTesting 

DTS Solution - Wireless Security Protocols / PenTesting
Similar to Intercept product
Proactive Security That Works

Presentation on the first proactive and collaborative anti-cyber warfare technology.
Why Penetration Testing Services Cyber51

Penetration Testing Services and Vulnerability Assessment Services.
UEBA

IntroSpect User and Entity Behavior Analytics (UEBA) uses AI-based machine learning to spot changes in user behavior that often indicate inside attacks that have evaded perimeter defenses. Security teams are armed with insights into malicious, compromised or negligent users, systems and devices – cutting off the threat before it does damage.
information security (Audit mechanism, intrusion detection, password manageme...

this slides contains the contents of Audit mechanism, intrusion detection, password management, general principals of system security and IP security
Securing E-commerce networks in MIS and E-Commerce

Securing E-commerce networks in MIS and E-Commerce
Light sec for service providers brochure

The Cloud and Mobility revolution, intensified by the quickly evolving threat landscape, heightens the
challenge for businesses to secure their IT infrastructure. Now they must fight security threats that target
their employees, applications, and other assets - not just on-premises, but throughout all of cyberspace.
CYBER SECURITY CAREER GUIDE CHEAT SHEET

In an increasingly interconnected and digital world, the importance of cybersecurity cannot be overstated. "Cybersecurity Mastery" is your essential guide to mastering the art and science of cybersecurity. This comprehensive book not only provides a roadmap for studying cybersecurity effectively but also delves into the essential tools, strategies, and certifications required to excel in this critical field.
Cybersecurity relies on a diverse set of tools to detect, prevent, and respond to threats. "Cybersecurity Mastery" introduces you to these tools and guides you on how to leverage them effectively. From antivirus software and firewalls to intrusion detection systems (IDS) and vulnerability scanners, you'll gain practical insights into the tools that protect digital environments.
To validate your expertise in cybersecurity, this book also outlines the certifications that hold significant weight in the industry. Certifications such as Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), CompTIA Security+, and Certified Information Security Manager (CISM) are recognized globally and serve as valuable credentials in your cybersecurity career. "Cybersecurity Mastery" provides guidance on how to prepare for these certifications, ensuring you're well-prepared to pass the exams.
Upon completing your journey through "Cybersecurity Mastery," you'll be well-prepared to pursue a range of exciting career opportunities. Designations such as Cybersecurity Analyst, Information Security Manager, Network Security Engineer, and Ethical Hacker are within reach for those who master the principles and techniques outlined in this book.
AI for Cybersecurity Innovation

I will talk about innovation in the area of cyber security analytics - developing machine learning methods to detect and block cyber attacks (e.g. detecting ransomware within 4 seconds of execution and killing the underlying processes). Rather than just focusing on this as a 'black box', I'll pull it apart and talk about how we can use these methods to enable security practitioners (SOC/CIRT etc) to ask and answer questions about 'what' and 'why' these methods are flagging attacks. I'll also talk about resilience of machine learning methods to manipulation and adversarial attacks - how stable these approaches are to diversity and evolution of malware for example.
Lessons Learned Fighting Modern Cyberthreats in Critical ICS Networks

A presentation given in April 2019 in London during ICS Cyber Security Conference. I discuss an anonymized investigation conducted by our team to identify a real malware infection on a production network, the tools and techniques used to contain this threat and how to use threat intelligence and visibility to stay ahead of cyber adversaries.
Asset visibility and network baselining
Continuous network monitoring
Threat intelligence ingestion
Thorough incident response plans
Similar to Intercept product (20)
information security (Audit mechanism, intrusion detection, password manageme...

information security (Audit mechanism, intrusion detection, password manageme...
Securing E-commerce networks in MIS and E-Commerce

Securing E-commerce networks in MIS and E-Commerce
Lessons Learned Fighting Modern Cyberthreats in Critical ICS Networks

Lessons Learned Fighting Modern Cyberthreats in Critical ICS Networks
Recently uploaded
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Mission to Decommission: Importance of Decommissioning Products to Increase E...

Mission to Decommission: Importance of Decommissioning Products to Increase Enterprise-Wide Efficiency by VP Data Platform, American Express
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scalable Platform by VP of Product, The New York Times
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Presented by Suzanne Phillips and Alex Marcotte
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

91mobiles recently conducted a Smart TV Buyer Insights Survey in which we asked over 3,000 respondents about the TV they own, aspects they look at on a new TV, and their TV buying preferences.
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Key Trends Shaping the Future of Infrastructure.pdf

Keynote at DIGIT West Expo, Glasgow on 29 May 2024.
Cheryl Hung, ochery.com
Sr Director, Infrastructure Ecosystem, Arm.
The key trends across hardware, cloud and open-source; exploring how these areas are likely to mature and develop over the short and long-term, and then considering how organisations can position themselves to adapt and thrive.
Recently uploaded (20)
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
Mission to Decommission: Importance of Decommissioning Products to Increase E...

Mission to Decommission: Importance of Decommissioning Products to Increase E...
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Assuring Contact Center Experiences for Your Customers With ThousandEyes
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Key Trends Shaping the Future of Infrastructure.pdf

Key Trends Shaping the Future of Infrastructure.pdf
Intercept product
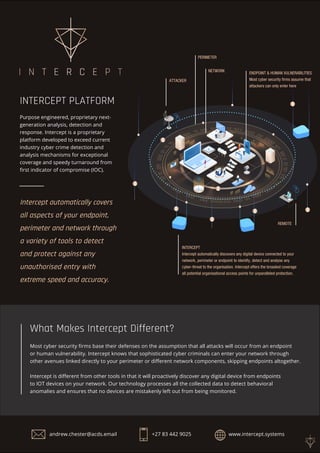
- 1. INTERCEPT Intercept automatically discovers any digital device connected to your network, perimeter or endpoint to identify, detect and analyse any cyber-threat to the organisation. Intercept offers the broadest coverage all potential organisational access points for unparalleled protection. ENDPOINT & HUMAN VULNERABILITIES Most cyber security firms assume that attackers can only enter here NETWORK ATTACKER REMOTE PERIMETER INTERCEPT PLATFORM Purpose engineered, proprietary next- generation analysis, detection and response. Intercept is a proprietary platform developed to exceed current industry cyber crime detection and analysis mechanisms for exceptional coverage and speedy turnaround from first indicator of compromise (IOC). Most cyber security firms base their defenses on the assumption that all attacks will occur from an endpoint or human vulnerability. Intercept knows that sophisticated cyber criminals can enter your network through other avenues linked directly to your perimeter or different network components, skipping endpoints altogether. Intercept is different from other tools in that it will proactively discover any digital device from endpoints to IOT devices on your network. Our technology processes all the collected data to detect behavioral anomalies and ensures that no devices are mistakenly left out from being monitored. What Makes Intercept Different? Intercept automatically covers all aspects of your endpoint, perimeter and network through a variety of tools to detect and protect against any unauthorised entry with extreme speed and accuracy. andrew.chester@acds.email +27 83 442 9025 www.intercept.systems
- 2. Offering: • Our response time is 30-minutes* from IOC to locating and isolating the attackers. The industry average is 24-hours • Seamlessly integrates with any other tool and works in conjunction with existing mechanisms • Proactively and automatically detects devices • Agents deployed to devices are resource light • Immediate detection and isolation/response to threats • Full coverage - Intercept is a Platform as a Service (PaaS) that defends every digital device in your environment • Seamlessly integrates with any other tool and works in conjunction with existing mechanisms • Proactively and automatically detects devices • Agents deployed to devices are resource light • Immediate detection and isolation/response to threats • Threat Hunting and Security Visibility within the first 24 hours • Cloud based analysis, works anywhere, YARA and Sigma compatible • Utilises proprietary as well as partner-based threat intelligence • Intercept Endpoint Detection and Response services per device costs approximately 82,5% less than its closest competitor • We see everything. We monitor 4 Billion IPv4 Addresses, which is scanned every 45 minutes. We have 2750 Class-C Networks hosting honeynets • We see 4 to 5 million IP Addresses sink-holed across 400 different malware variants everyday • We have over 700 000 unique malware samples ingested and analysed by our sandboxes every day • Our response time is 30-minutes (if deployed correctly*) from IOC to locating and isolating the attackers. The industry average is 24-hours Intercept is different: Other Tools • Manually linked to endpoint/IOT devices • Prone to human error - might miss a log source • Resource intensive on infrastructure Intercept • Actively discovers all endpoints/IOT devices • Automatically processes all data processors to conduct detection and analysis functions • Detects and isolates IOC within 30 minutes (if deployed correctly) Intercept Includes: Dedicated Services from Multidisciplinary (Purple team) SOC and Offensive Security teams Rapid Detection & Response Vulnerability Management and Validation Threat Intelligence Delivery & Validation Using Risk Scoring Threat Hunting and Validation Robust Advisory & Consulting Services
- 3. How Intercept Works Intercept’s Kill Chain INTERCEPT THREAT HUNTING DOMAININTERCEPT THREAT HUNTING DOMAIN INTERCEPT ALPHA SECURITY ENGINE USER BEHAVIOUR MONITORING ENDPOINT MONITORING SERVER MONITORING FIREWALL MONITORING ROUTER MONITORING SWITCH MONITORING SECURE OUTBOUND VPN UTILISING CLIENT EXISTING CONNECTIVITY INTERCEPT TEAM CLOUD SOC PREPARATION INTRUSION ACTIVE BREACH HOURSTOMINUTESSECONDSMONTHS RECONNAISSANCE Harvesting email addresses, conference information, etc WEAPONIZATION Coupling exploit with back door into deliverable payload DELIVERY Delivering weaponized bundle to the victim via email, web, USB etc EXPLOITATION Exploiting a vulnerability to execute code on victim’s system INSTALLATION Installing malware on the asset COMMAND & CONTROL (C2) Command channel for remote manipulation of victim’s system ACTION & OBJECTIVES Intruders get ‘hands on keyboard’ access to accomplish anything 1 2 3 4 5 6 7
- 4. Intercept License Pricing (per month) Managed Services Number of Endpoint Devices 1-300 301-500 501-700 701-1000 1000+ Per Perimeter Network Device (Any device that connects to an external network, Eg: routers, etc) $ 100.00 $ 100.00 $ 100.00 $ 100.00 Contact Us Per Endpoint Device (Laptop, Table, mobile phone, server, etc) $ 3.50 $ 3.41 $ 3.33 $ 3.24 Contact Us Per Node (Provide network-level threat detection, anomaly detection, intrusion detection & vulnerability analysis, & threat scoring) $ 850.00 $ 828.75 $ 808.03 $ 787.83 Contact Us Digital Forensic and Incident Response License for 365-days $ 1,550.00 $ 3,022.50 $ 4,533.75 $ 6,200.00 Contact Us MSSP Standard SLA Unlimited SLA Duration 1 year 1 year Support Method Help desk / Phone / On site Help desk / Phone / On site Response Time 30 Minutes for Premium Telephonic Calls 15 Minutes for Premium Telephonic Calls Support Hours 24/7 24/7 Included Incidents1 100 Unlimited Included Consulting Hours2 50 Unlimited 24/7 Threat Hunting, Rapid Detection and Response Yes Yes Cost Per Year $ 69 950.00 On Request3 All pricing is subject to Ts & Cs specific to a clients environment. Please chat to us for a more specific proposal dependent to your specific environment. 1. Pricing is based on 300 devices and 30-days worth of data storage in our cloud environment. Pricing is calculated on the amount of devices per year to ensure that we provide the correct amount of cloud compute & storage required to support them. On this pricing tier, we assume the client has a SIEM or event logging platform to send the data to, to store events and data for longer than 30 days. 2. One Node can support up to 350 devices, or one /24 subnet. This excludes any hardware required to run the software, or provide local storage, however hardware can be speced and provided as required, depending on the size of the network. It can be virtualized if the client has a supported virtual platform. It can also run on cloud networks. 3. Extends the endpoint data storage from 30-days to 365-days, allowing us/the client to retrospectively hunt for threats. This price is calculated to provide the correct amount of cloud compute and storage requirements for the size of the environment. Includes Intercept digital forensics suite, allowing anyone to hunt and carve digital forensic artifacts and IOC’s, as well as provide active response, automation and orchestration to security incident response. andrew.chester@acds.email +27 83 442 9025 www.intercept.systems