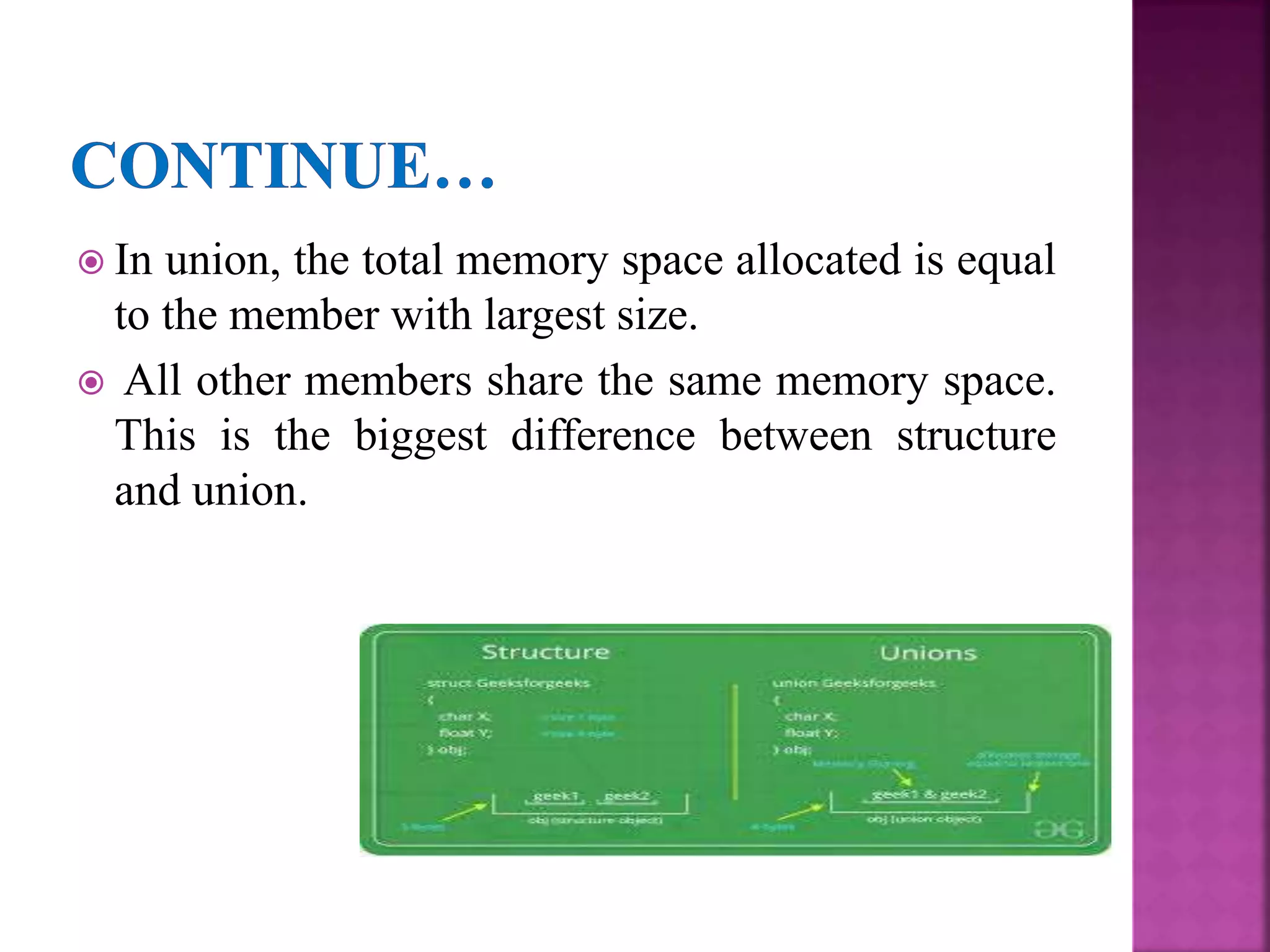
This document discusses unions in programming. It explains that in a union, all members share the same memory location, whereas a structure contains separate memory for each member. Only one member value can exist in a union at a time. There are two approaches to applying union operations: union by height, which makes the tree with the smaller height a subtree of the other; and union by weight, which makes the tree with fewer elements a subtree. Path compression is an optimization technique for union-find that flattens the tree structure during find operations by making each found root the new parent of its children, improving worst-case time complexity from linear to logarithmic.