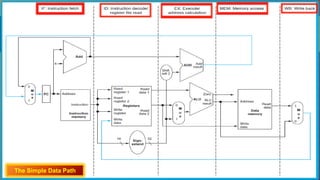
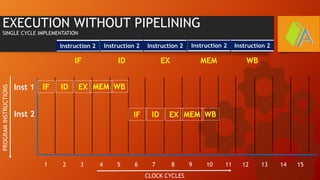
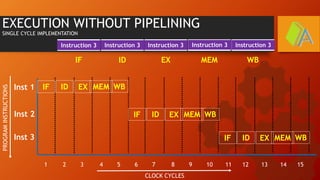
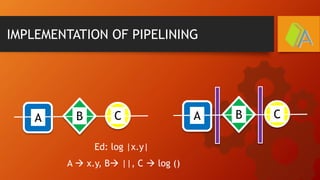
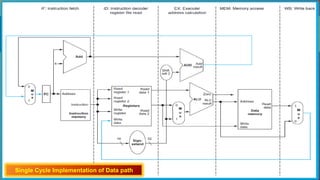
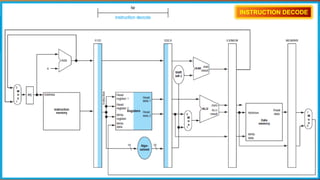
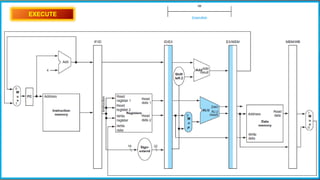
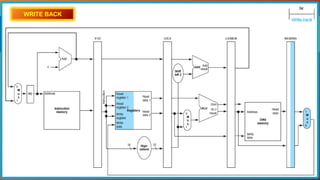
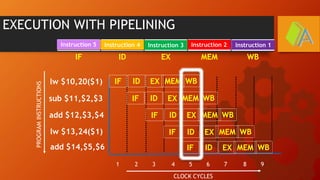
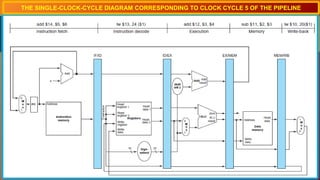
The document explains the MIPS pipeline instruction-execution process that consists of five stages: fetch, decode, execute, memory access, and write back. It contrasts pipelined execution, which enhances performance and instruction throughput, with single-cycle execution. Additionally, it illustrates the operations on a data path and the advantage of pipelining in reducing execution time.