The document summarizes Keross' philosophy and portfolio of managed IT services. Keross believes business success comes from understanding conclusions inspired by unrelated events, which they call "Synchronicity." Their services include business intelligence, managed infrastructure, security, and voice services. They have clients in over 45 countries across 4 continents.










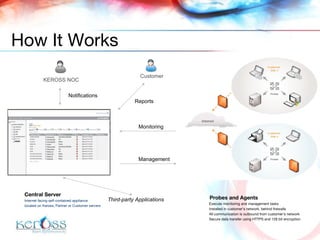

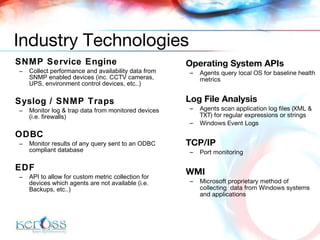




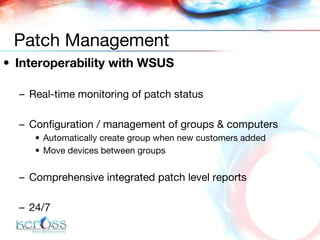






















![Chirag Desai [email_address] +971 50 559 0939 Cyril Simonnet [email_address] +971 50 220 9963 / +33 6 08 36 45 97 Contact Details](https://image.slidesharecdn.com/ikon-managed-services-83/85/Ikon-Managed-Services-43-320.jpg)