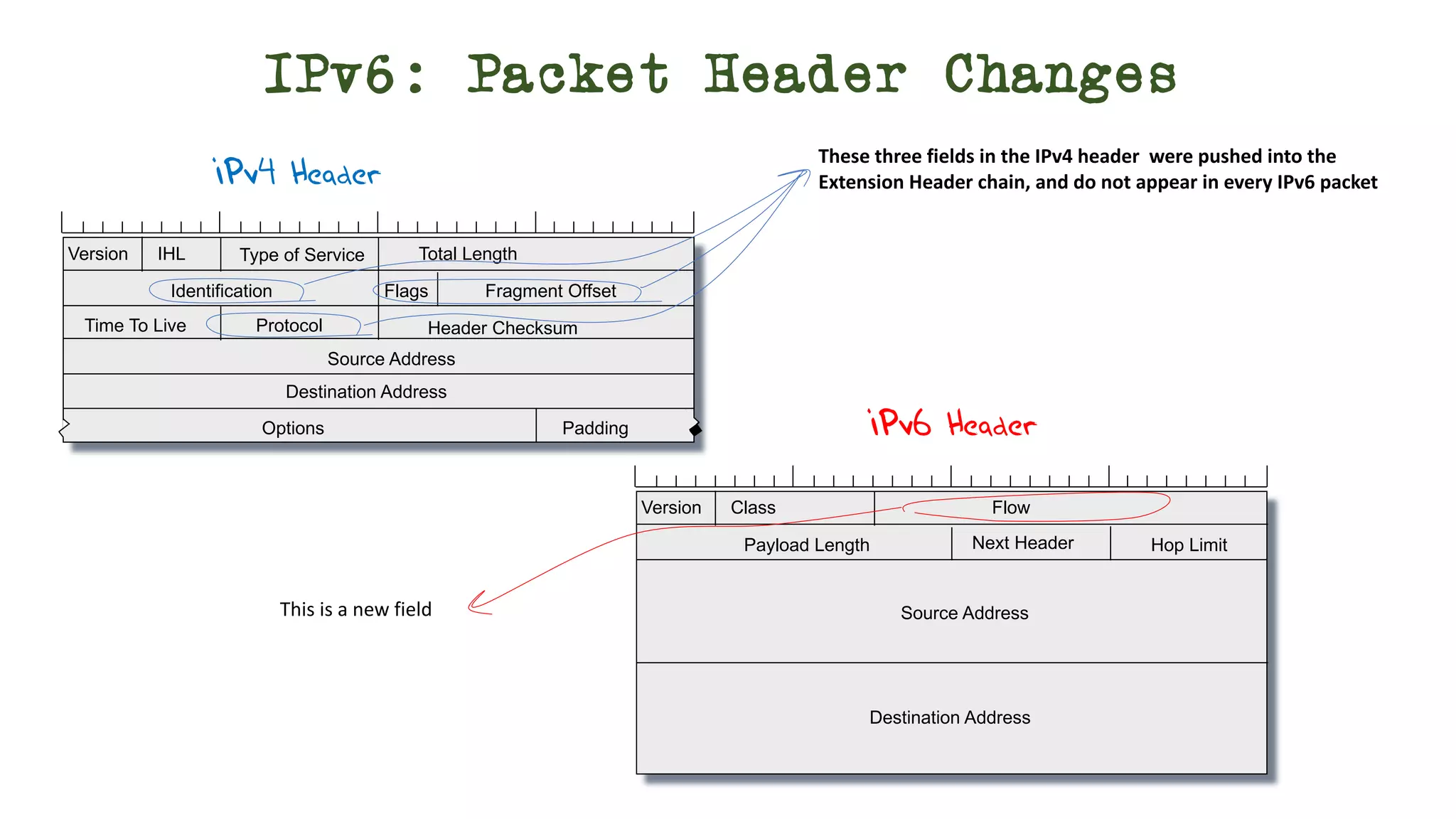
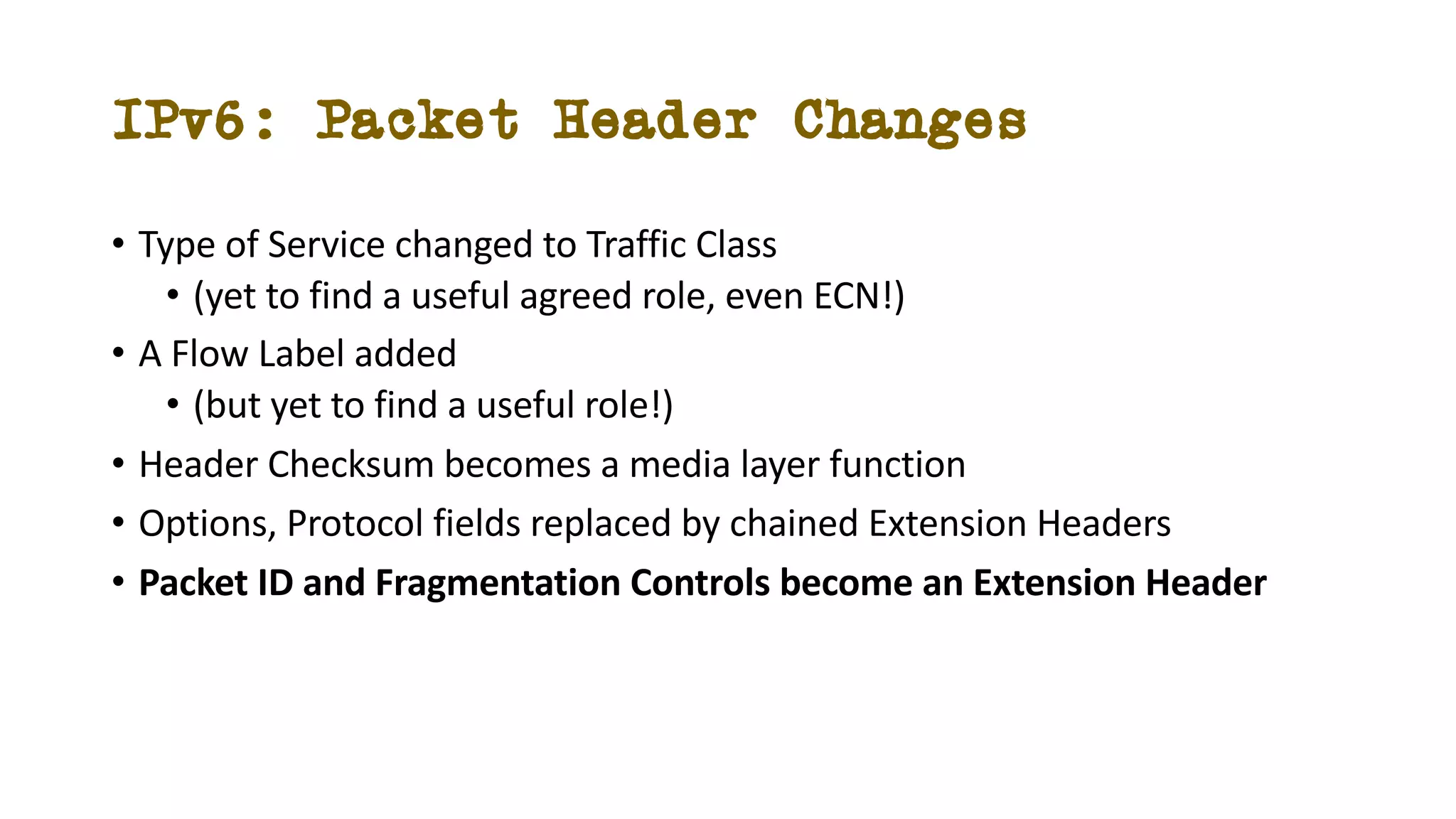
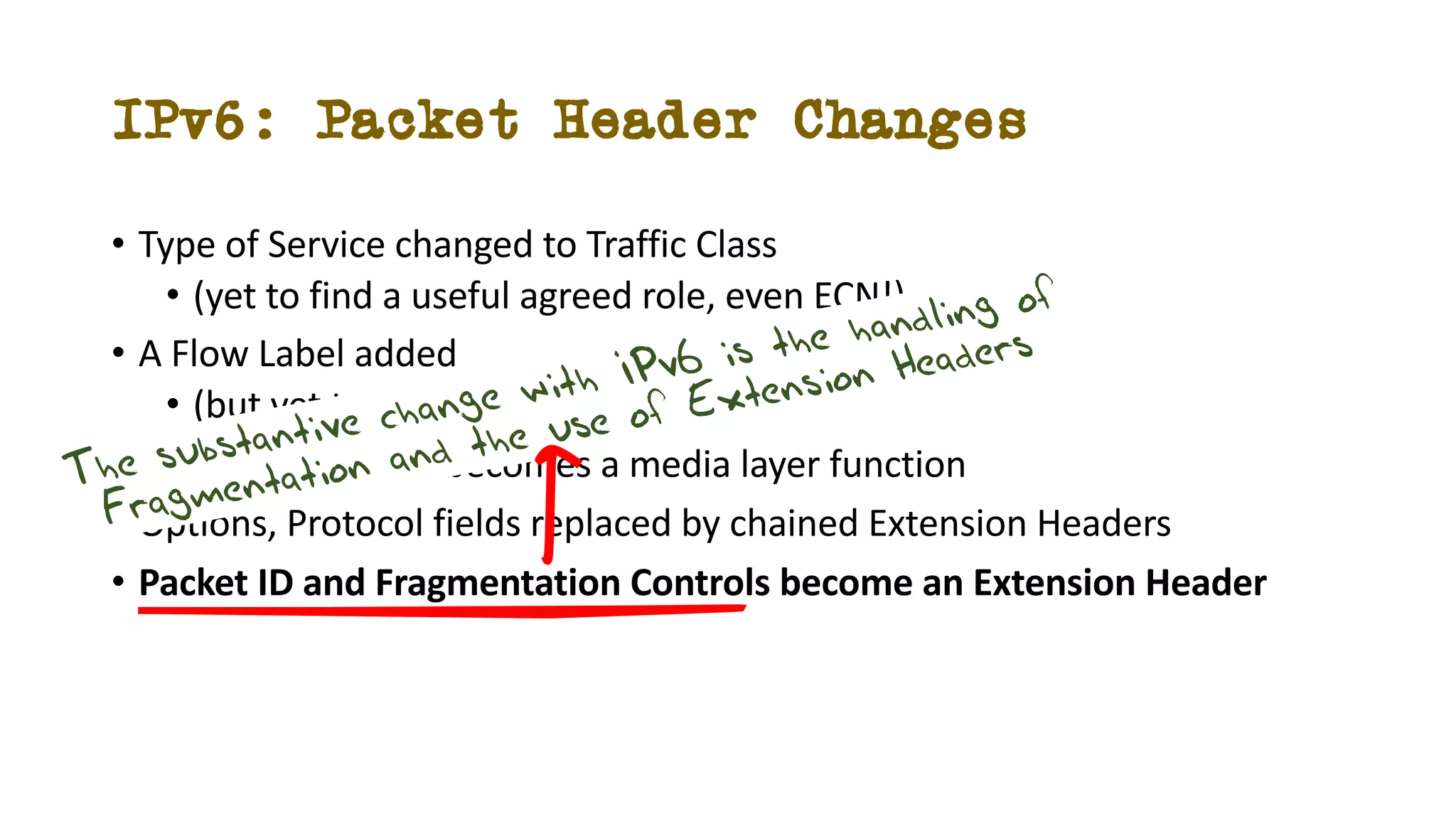
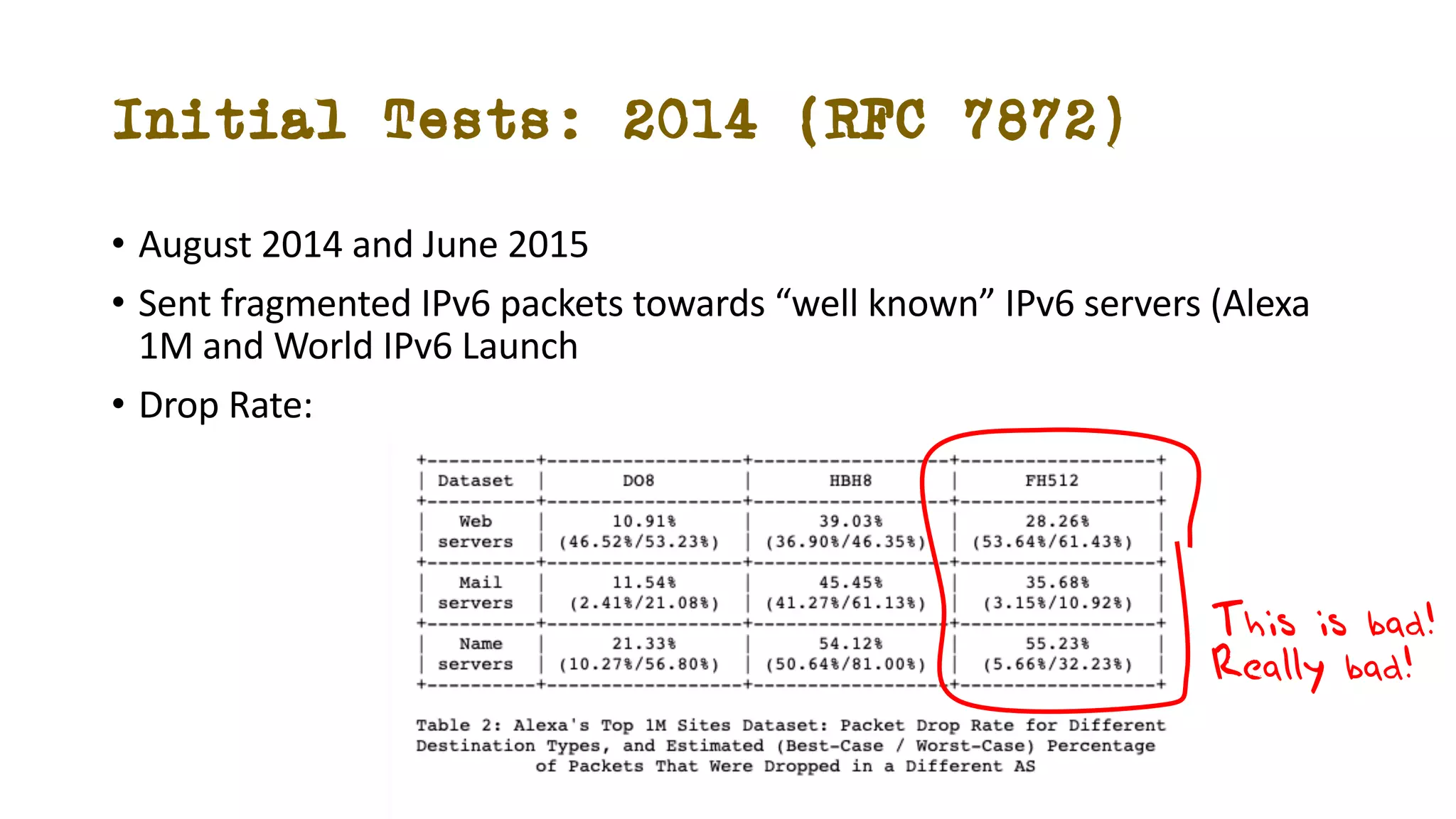
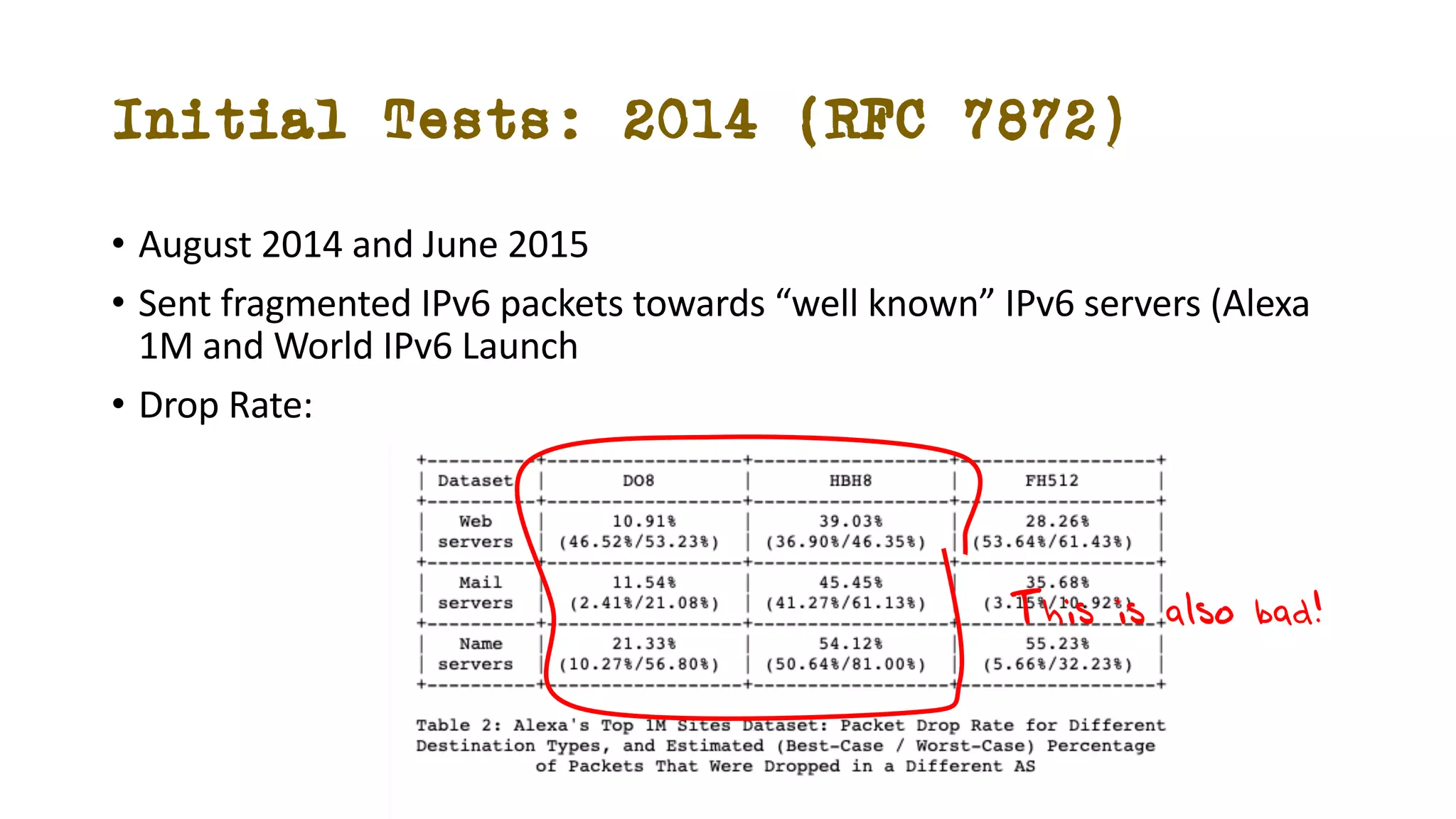
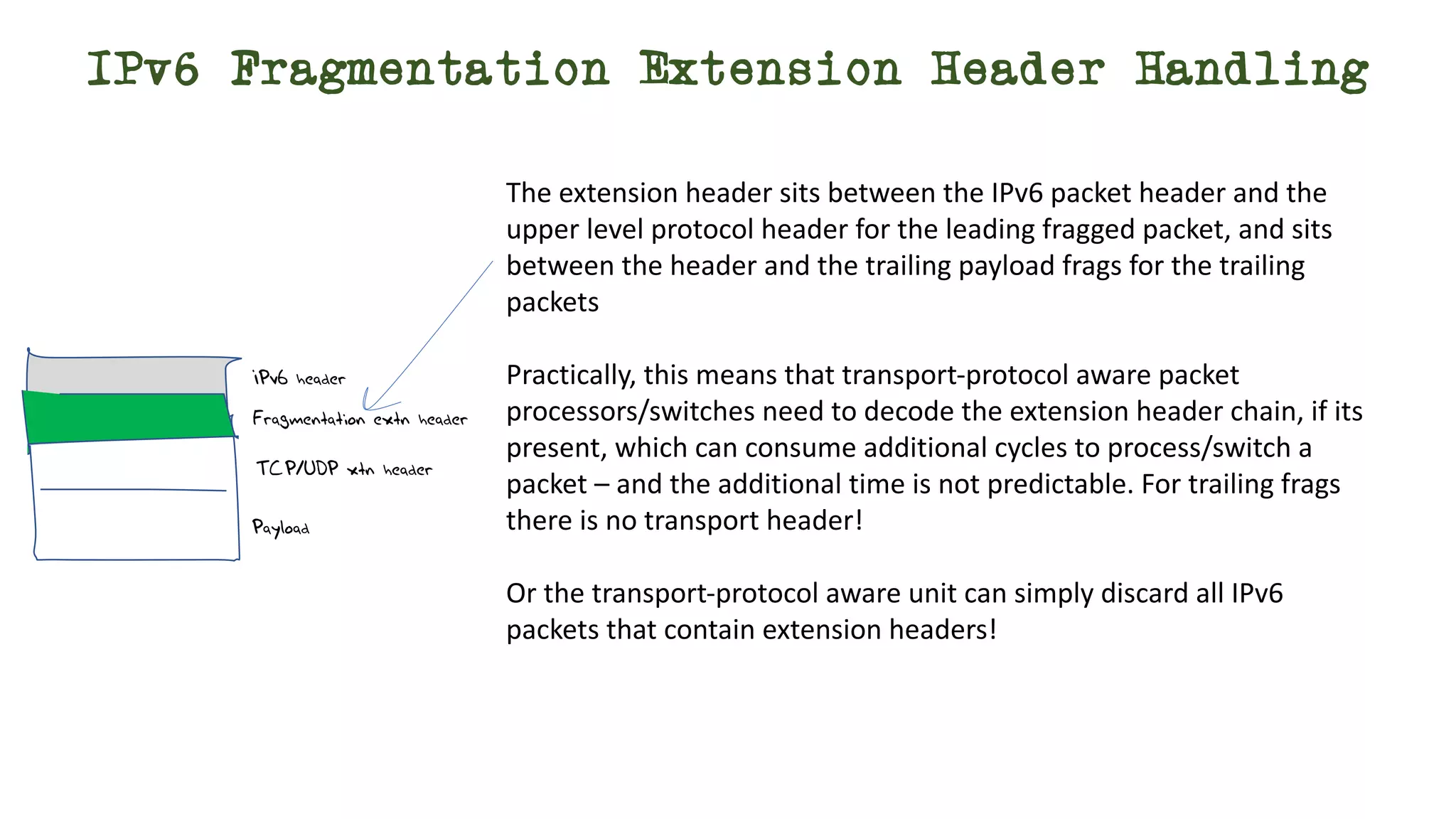
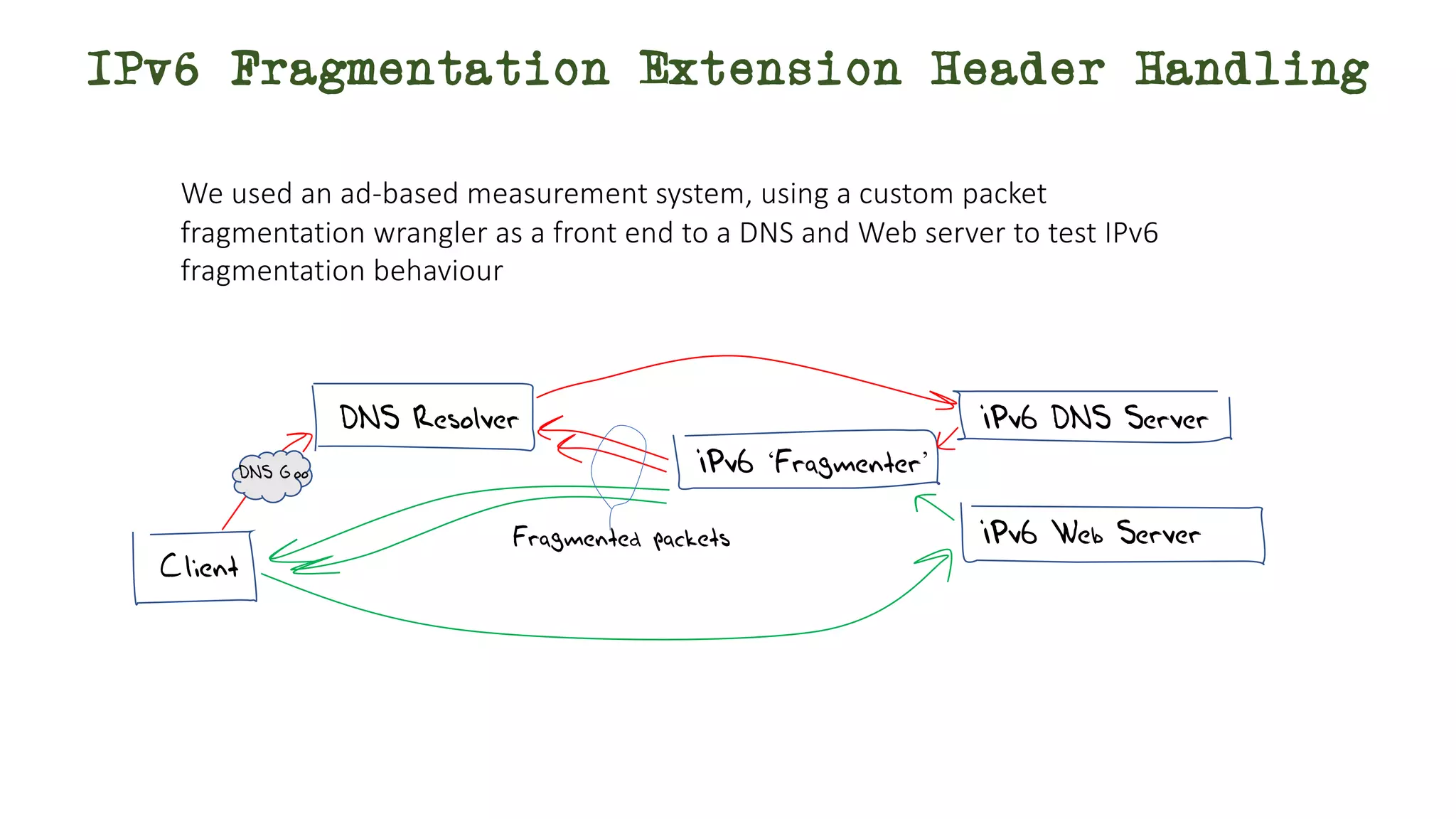
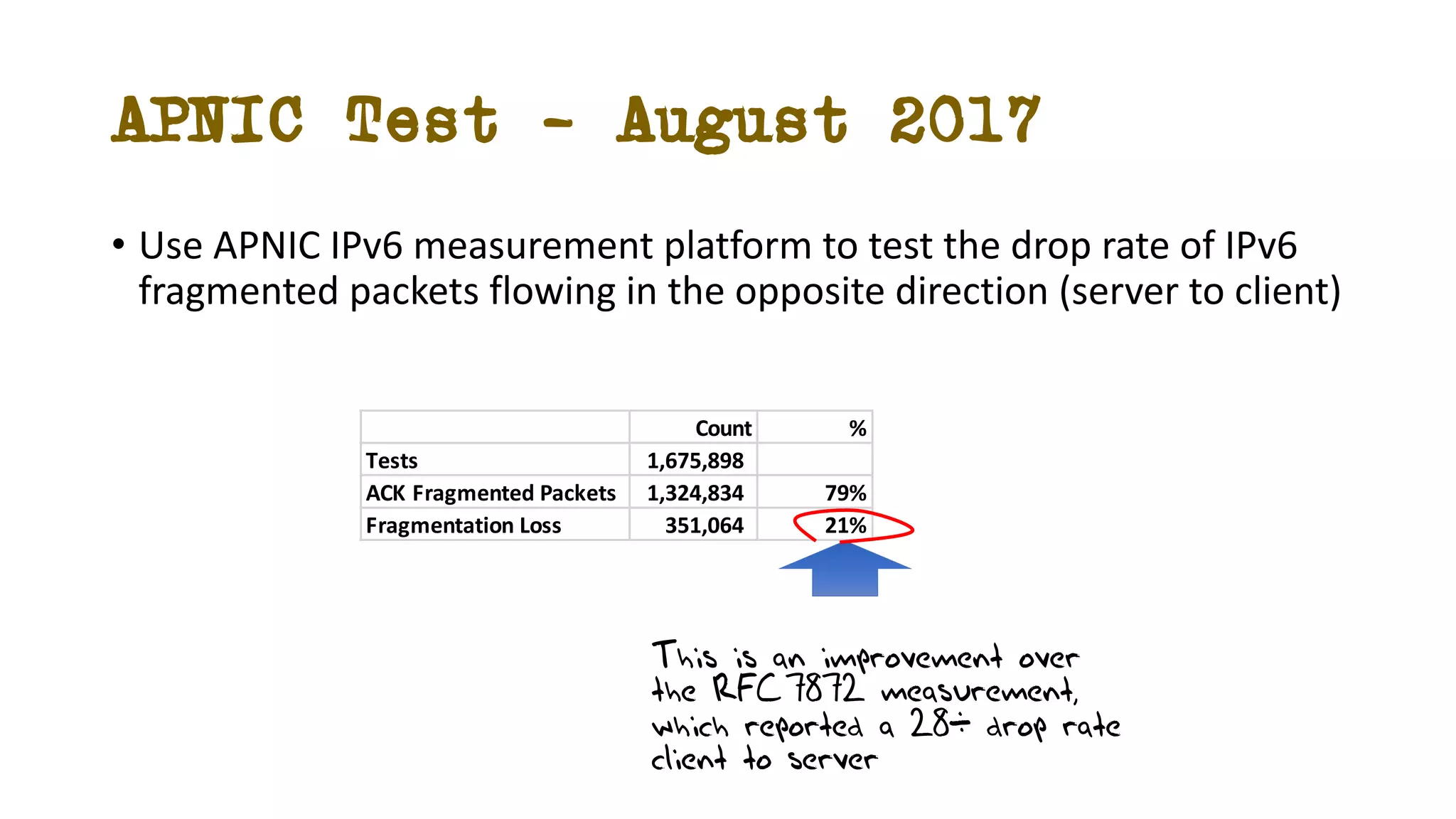
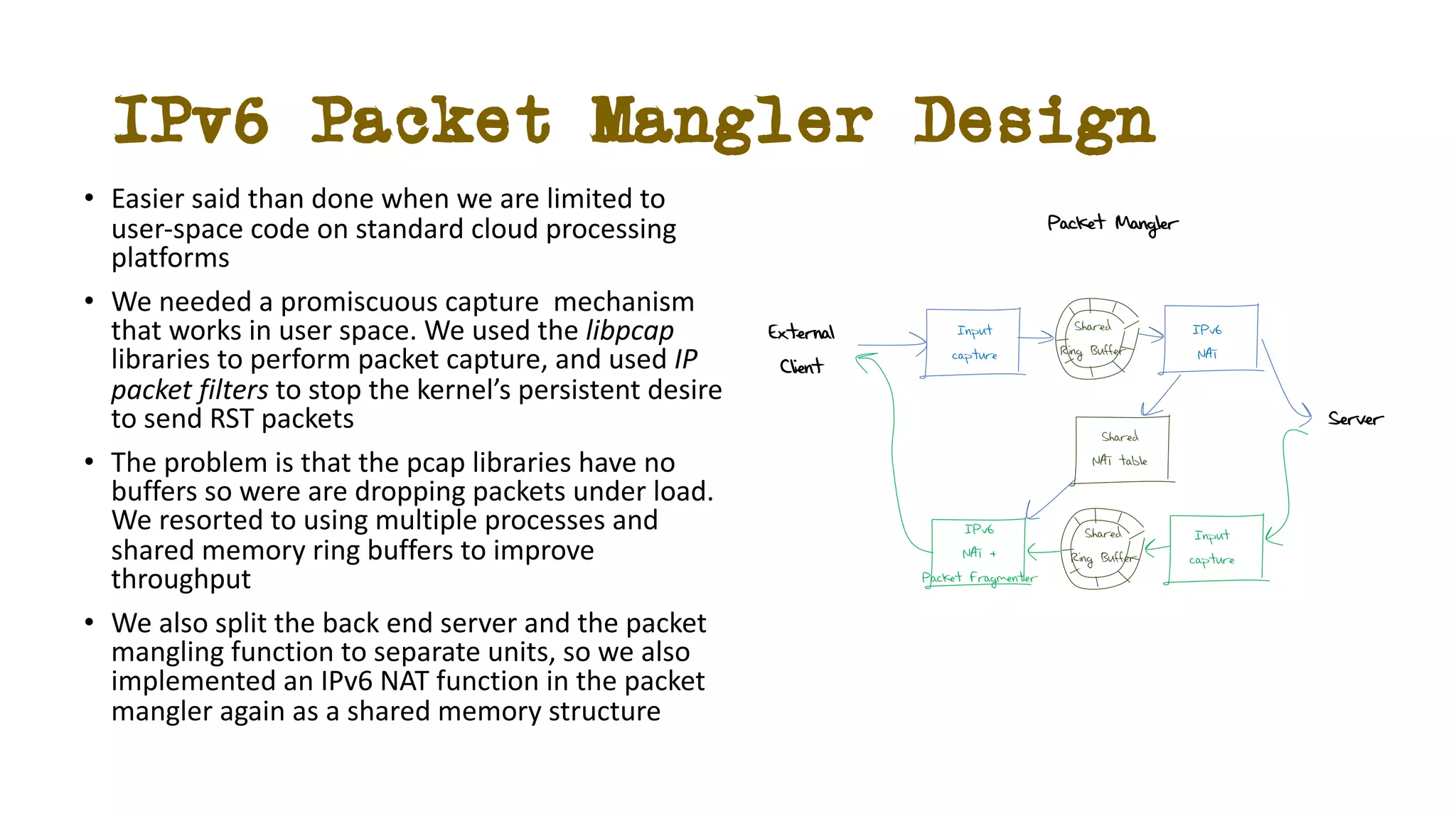
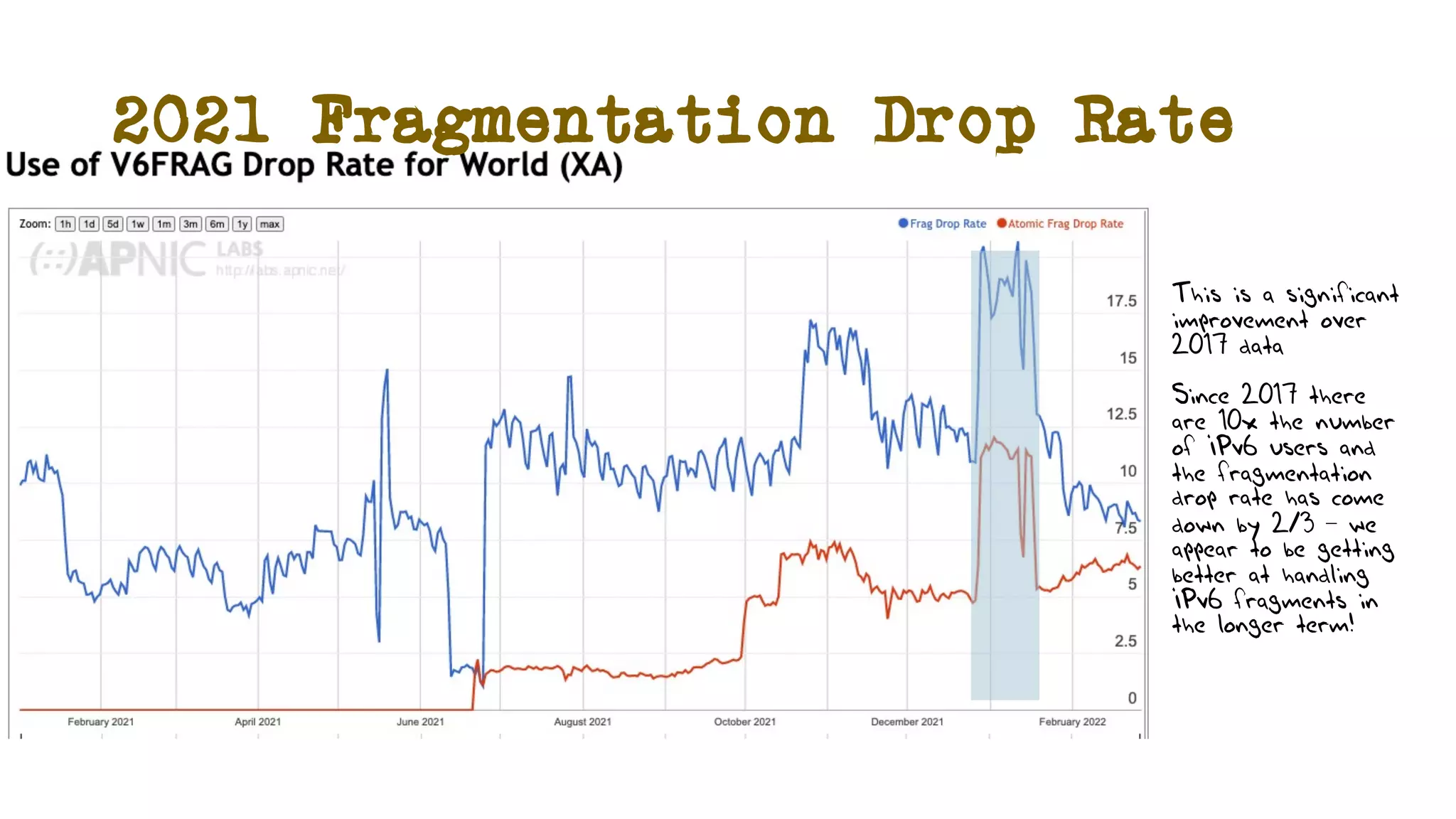
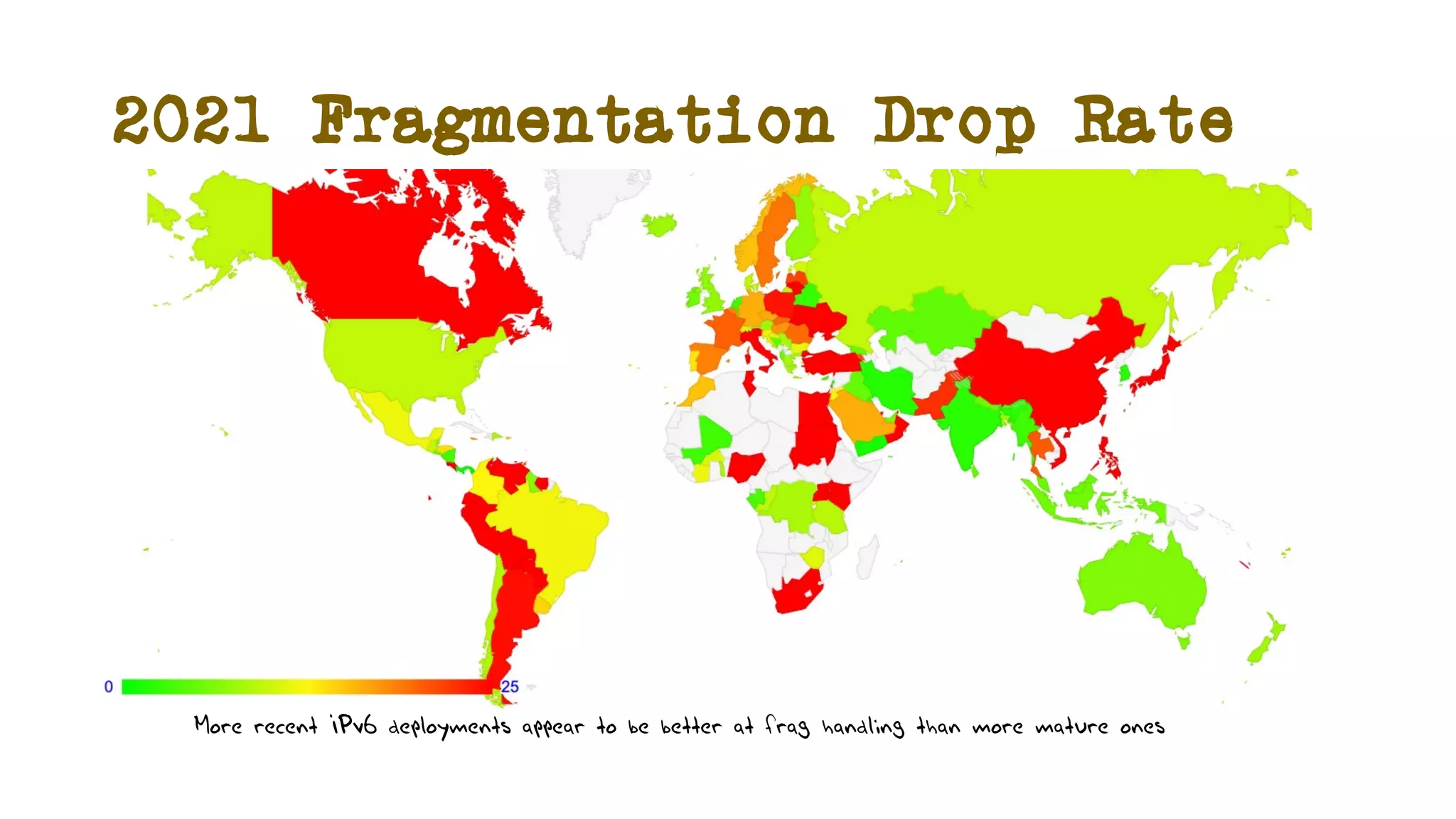
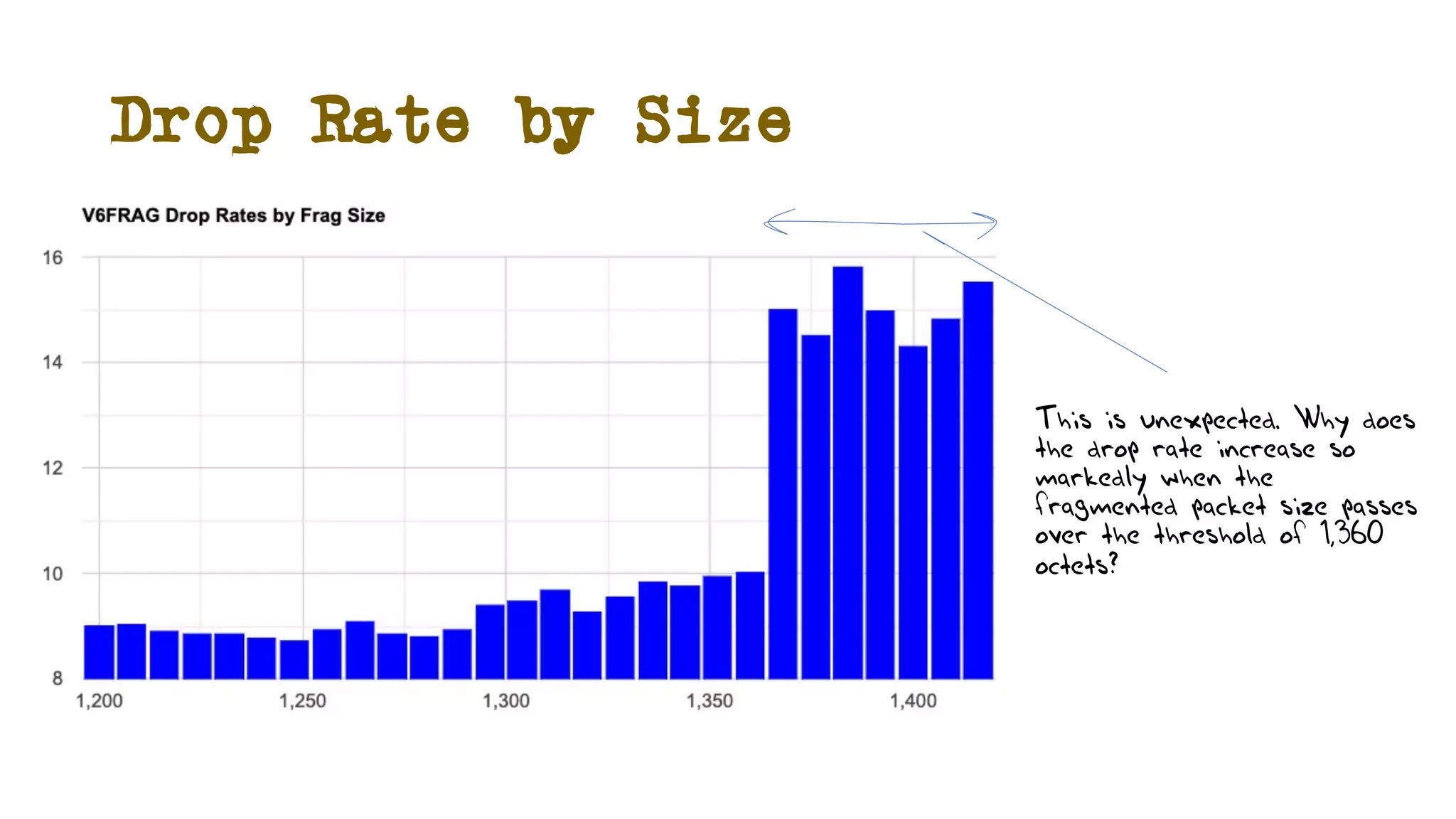
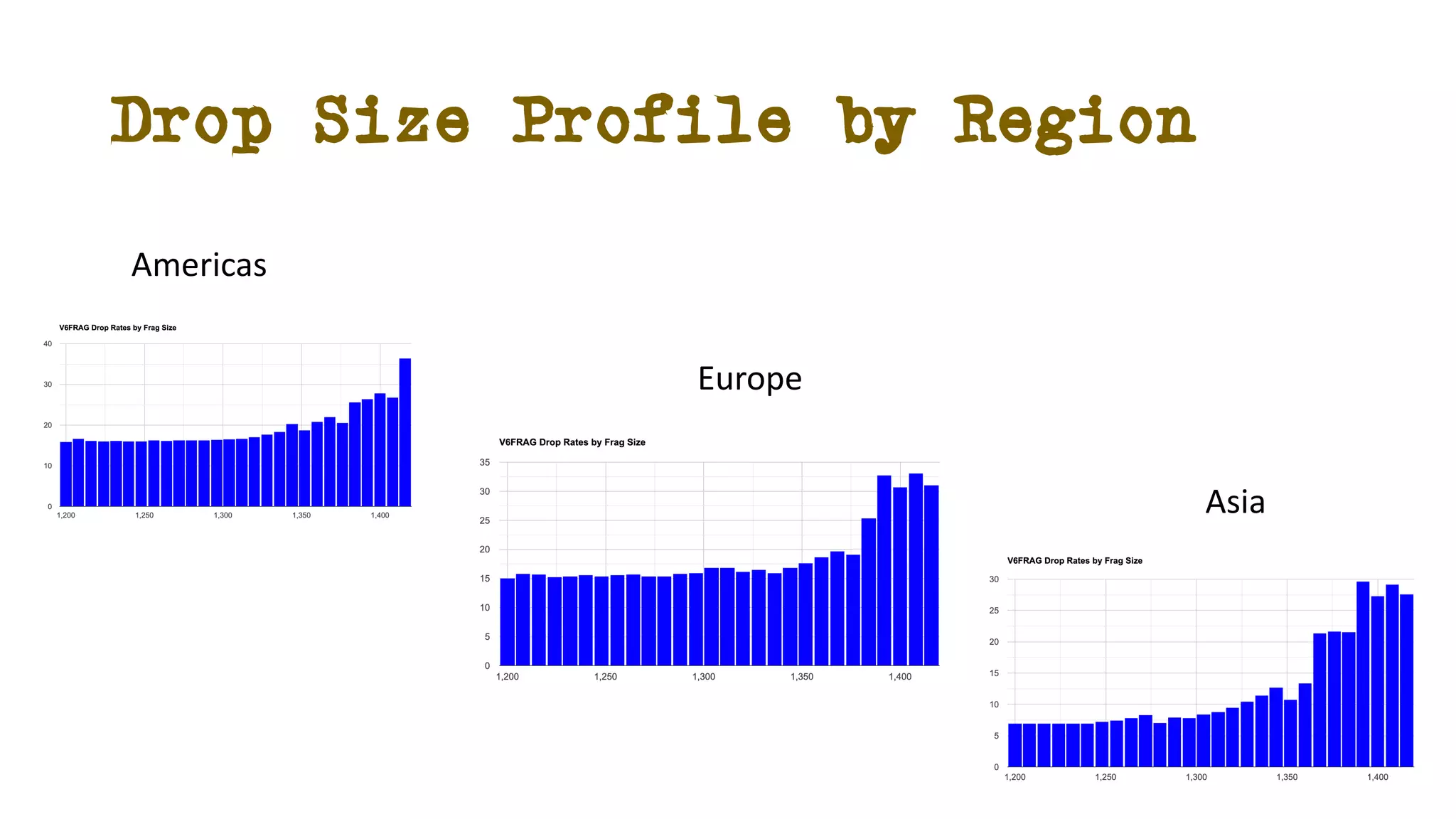
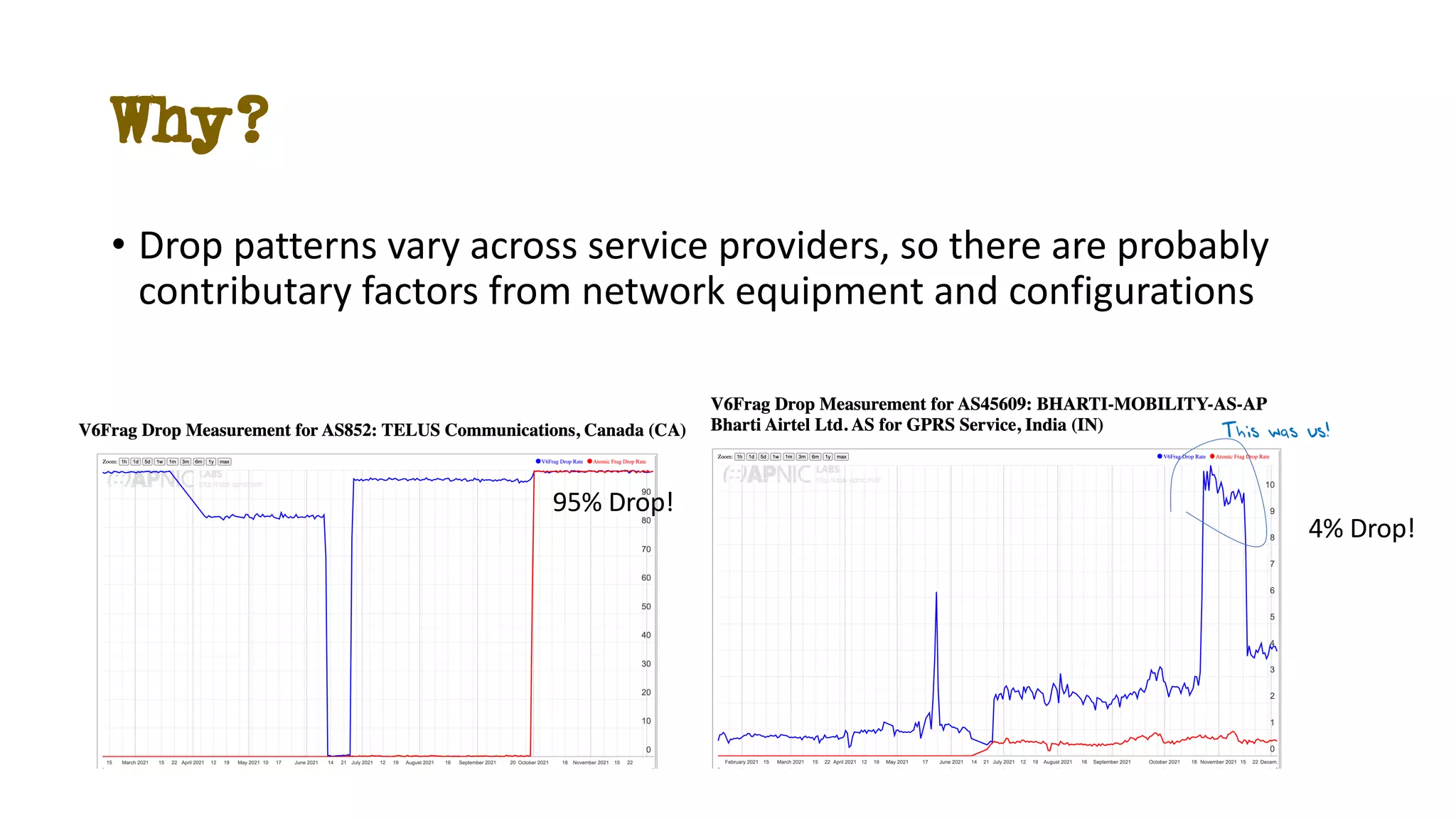
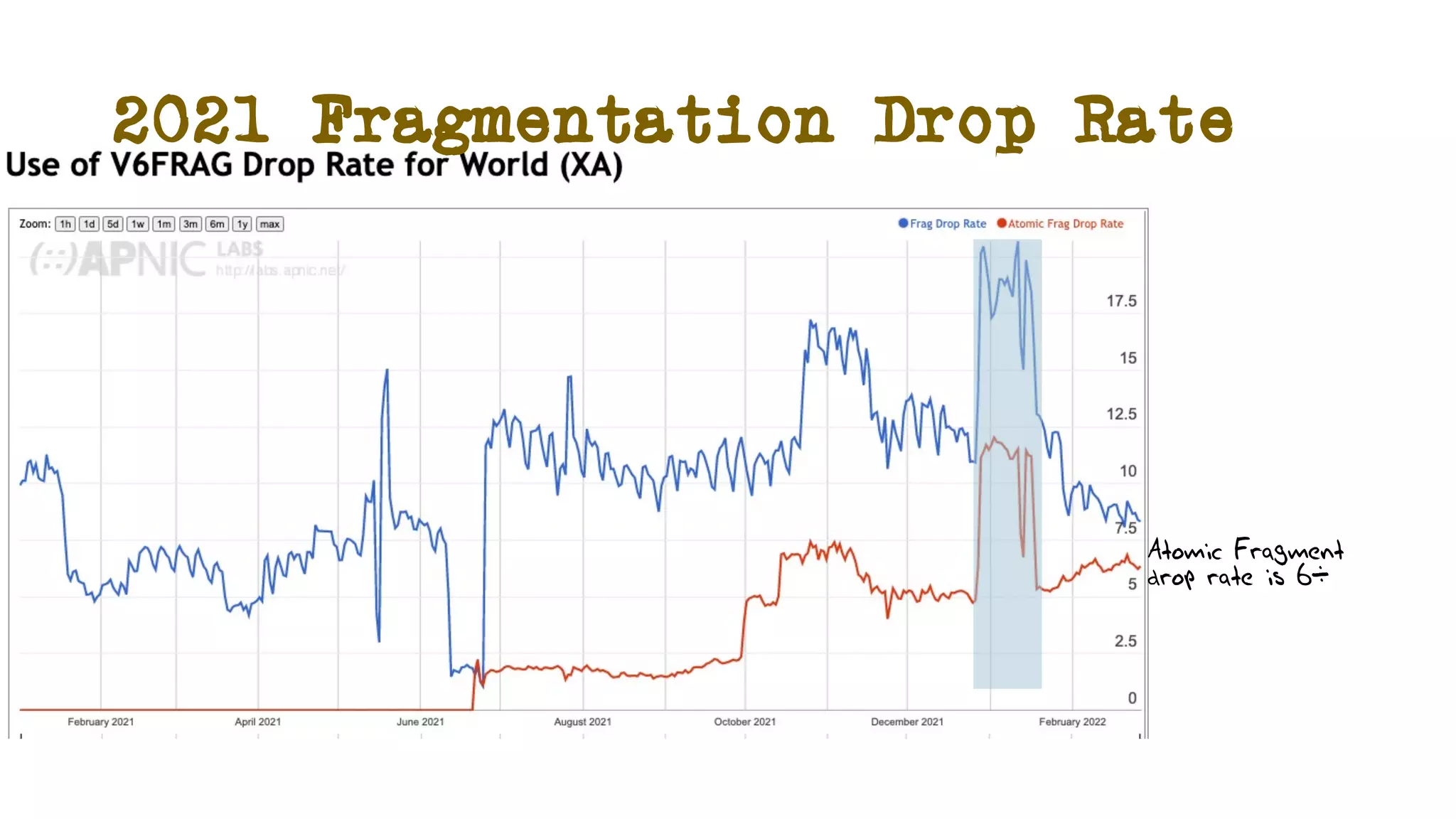
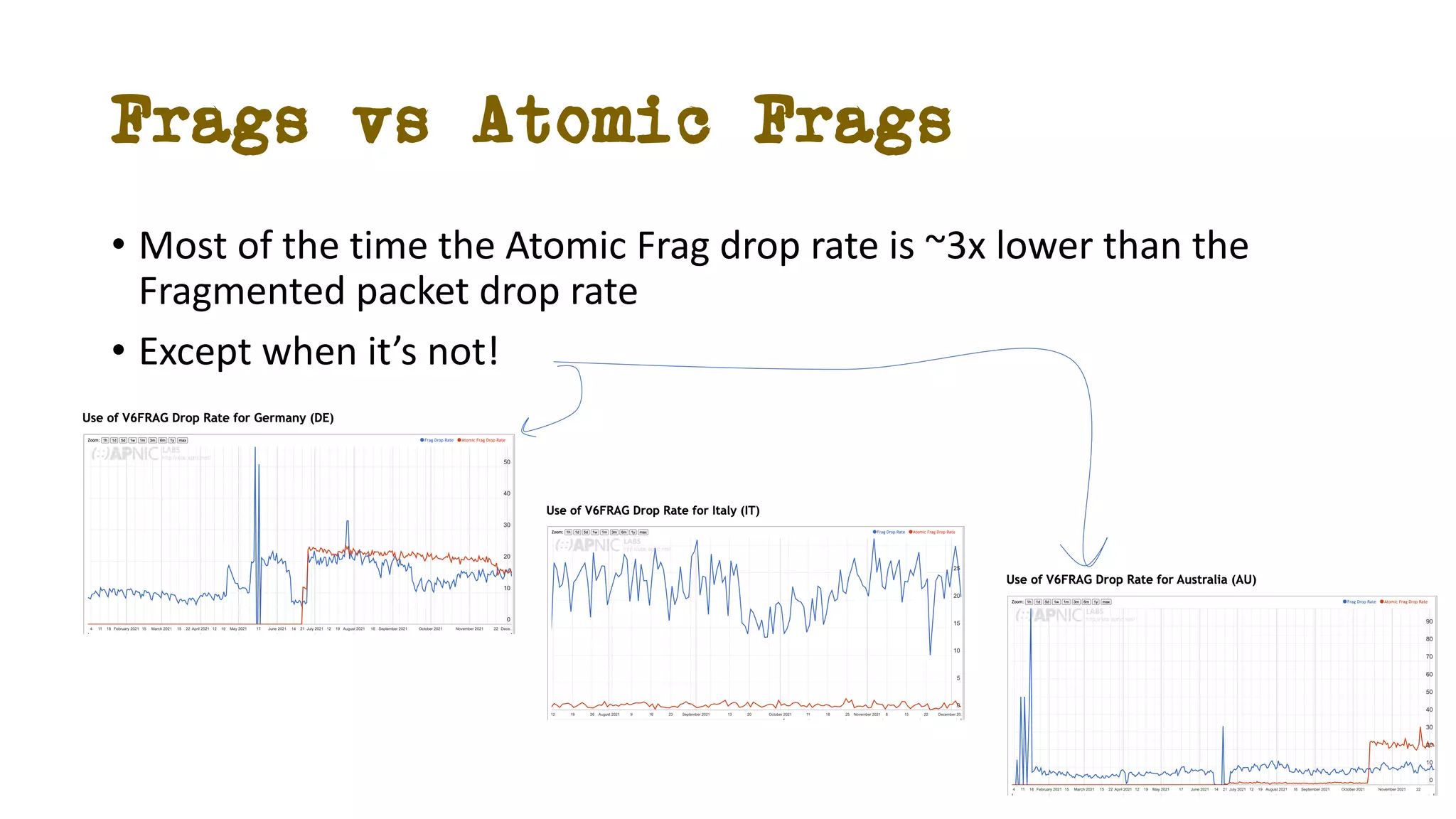
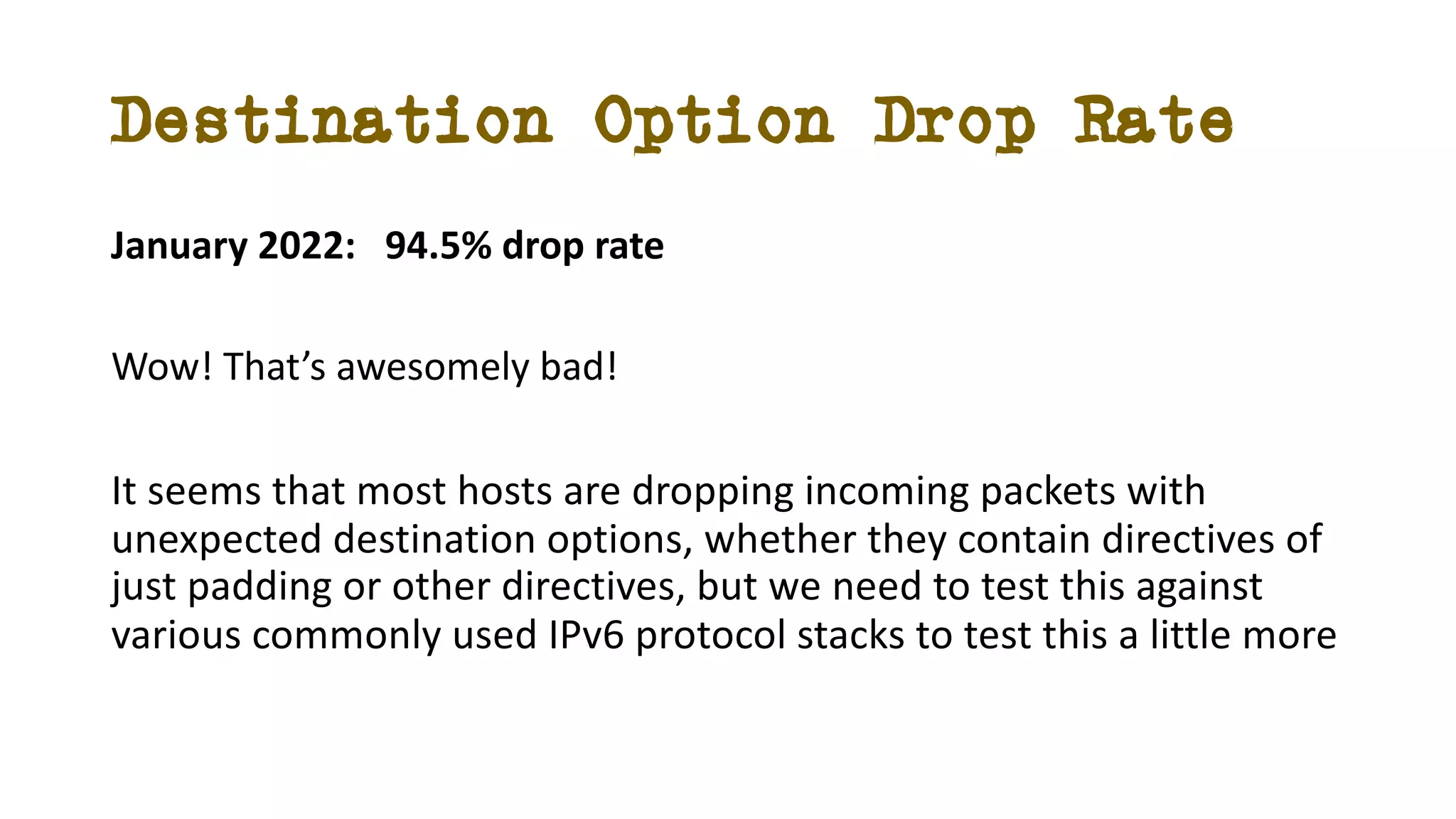
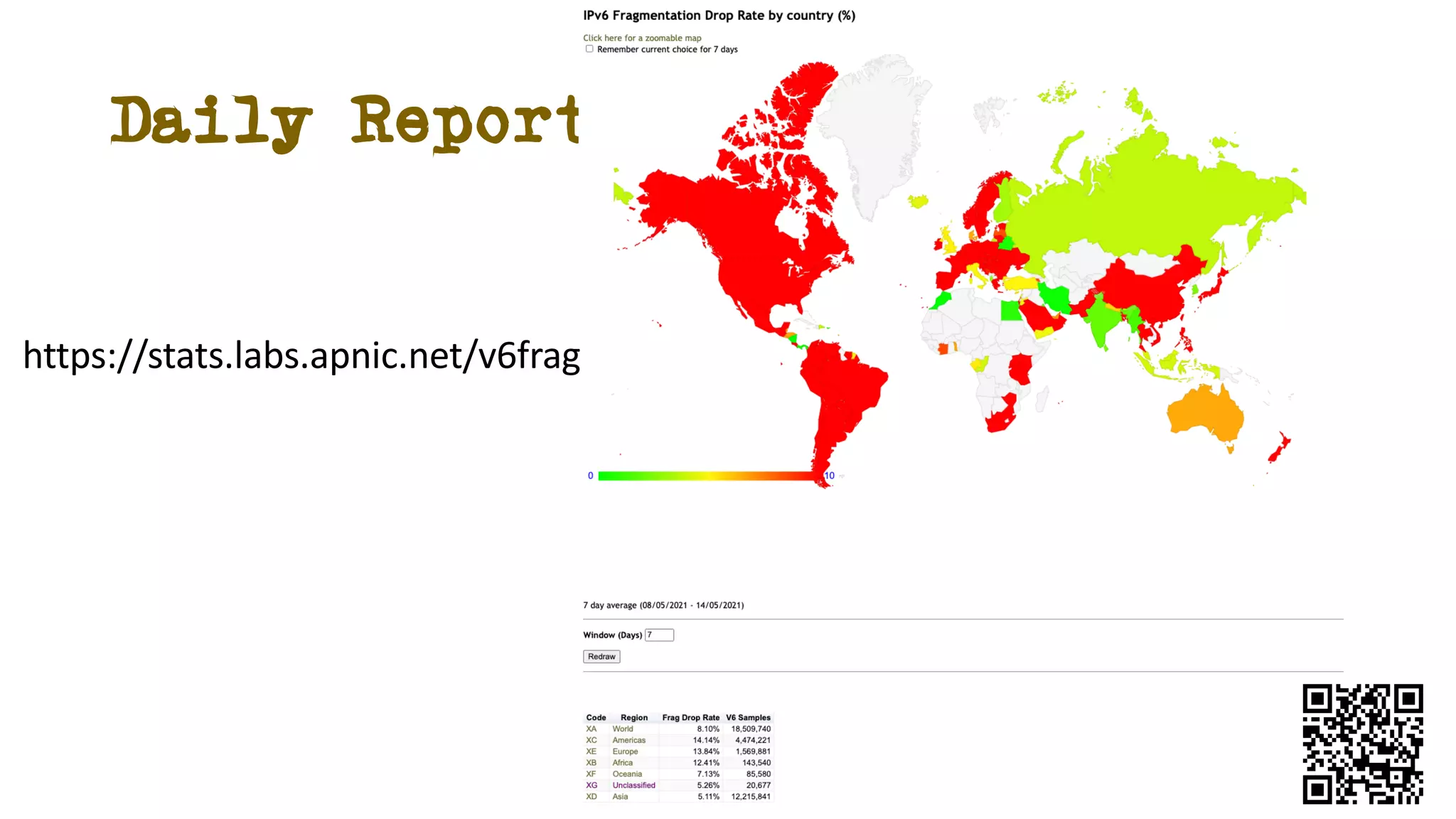
The document discusses IPv6 fragmentation and the behaviors of extension headers, highlighting significant changes from IPv4. Initial tests revealed high drop rates for fragmented packets, attributed to firewalls and ICMPv6 blockages, with improvements noted in later experiments. Recent findings indicate that while the overall handling of fragmented IPv6 packets has improved, extension headers like destination and hop-by-hop options face severe support issues across public internet infrastructure.