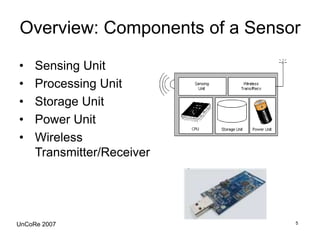
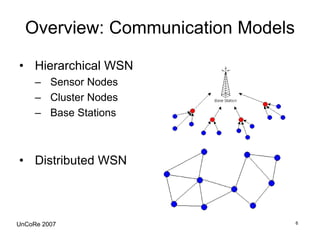
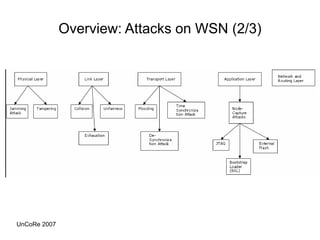
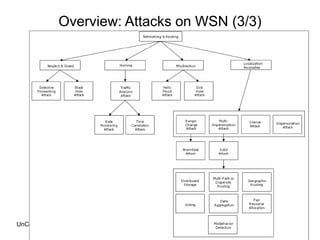
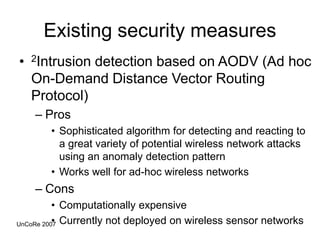
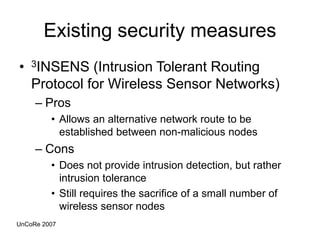
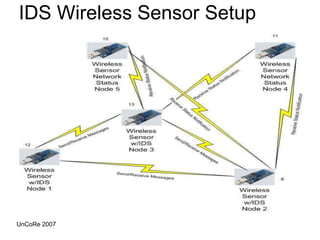
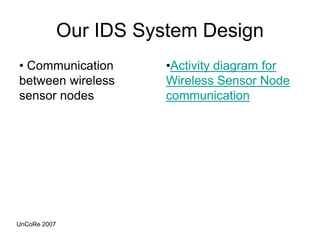
This document outlines the design, implementation, and evaluation of an intrusion detection system for wireless sensor networks. It begins with an overview of wireless sensor networks, including their applications, components, and communication models. It then discusses the objective of the project, which is to design an IDS to detect attacks on wireless sensor networks. The document reviews existing IDS approaches and their limitations before describing the design of the proposed anomaly-based IDS, which establishes a baseline of normal traffic and detects deviations that could indicate denial of service attacks. It provides details on using MoteIV sensors and its programming tools to implement and test the IDS.