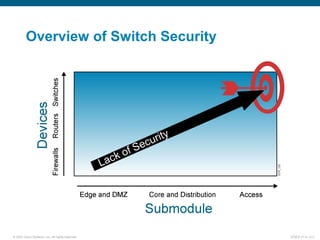
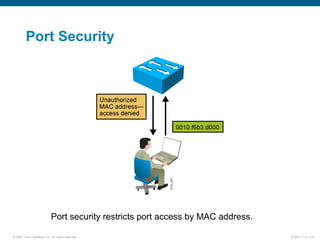
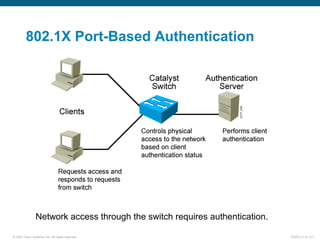
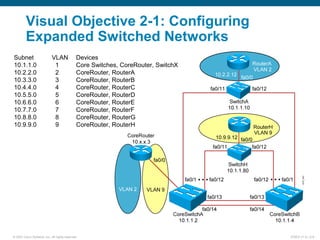
The document discusses recommended practices for securing a switched network, including: securing switch access through passwords and physical security, securing switch protocols like Cisco Discovery Protocol and spanning tree, and mitigating compromises through switches by securing trunk links and ports. It also covers using port security to restrict access by MAC address and 802.1X authentication to require network access through switches be authenticated.