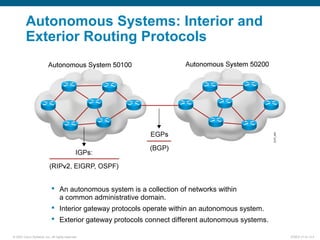
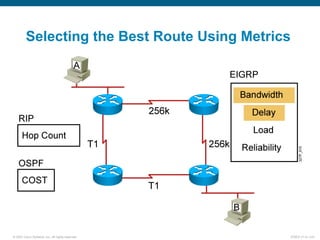
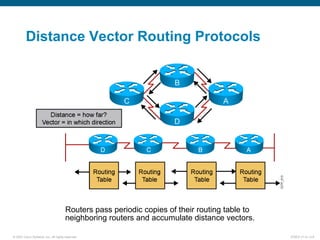
This document discusses routing protocols and their operation. It covers static and dynamic routing, interior and exterior routing protocols, classes of routing protocols including distance vector and link-state protocols. Distance vector protocols use split horizon, route poisoning, and hold-down timers to prevent routing loops from occurring. Link-state protocols have faster convergence but require more resources to run. The document provides information on how routing protocols work and their benefits and drawbacks.