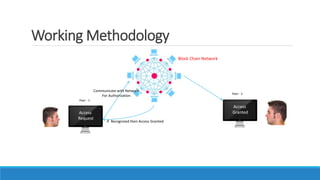
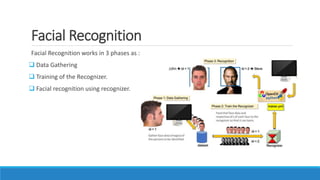
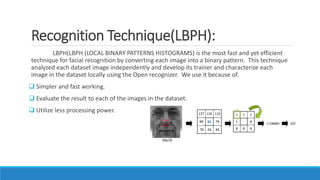
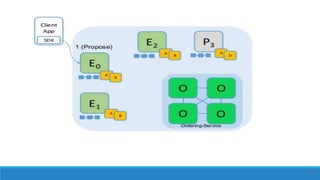
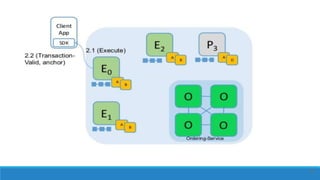
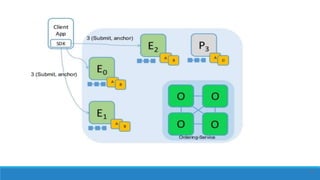
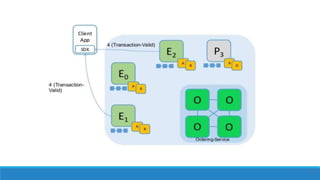
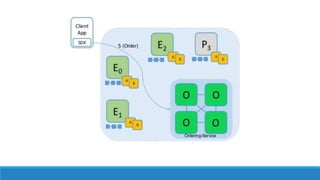
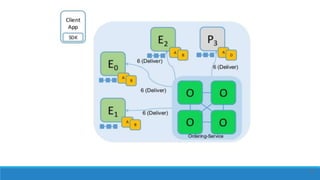
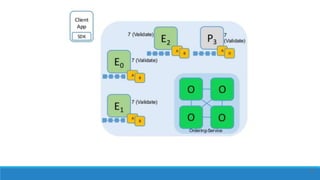
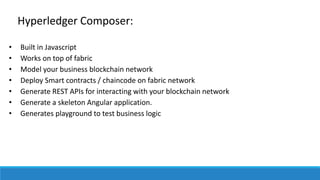
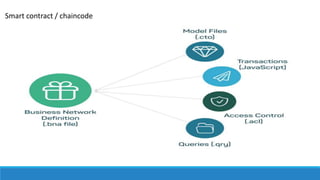
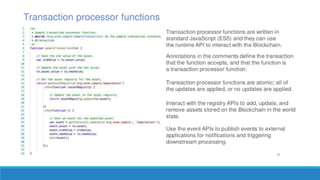
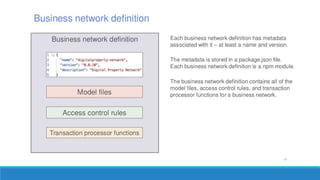
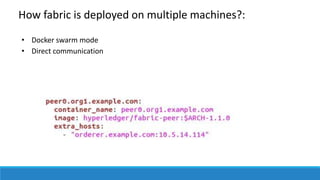
The document describes a project to create an "Army of Hidden Bots" using blockchain and facial recognition for cybersecurity. A team of 4 students led by Dr. Awais Hassan proposes a distributed network of bots connected by blockchain as a more reliable solution than centralized servers. The project will demonstrate a proof of concept using Python, Node.js, and facial recognition on multiple computers connected through a Hyperledger Fabric blockchain network.