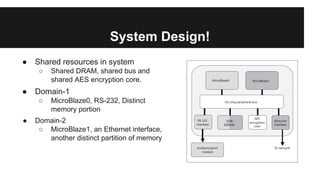
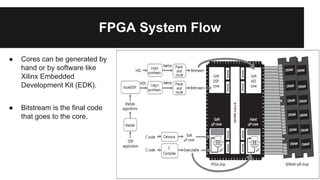
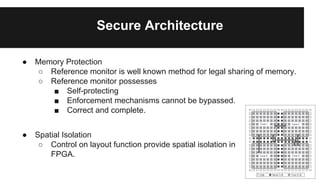
This document discusses managing securities in FPGA-based embedded systems. It begins by outlining benefits of FPGAs like better performance and flexibility. It then discusses using FPGAs for cryptographic applications and the need for isolating plaintext from ciphertext. The document presents a system design with separate memory partitions and cores for different domains. It provides examples of FPGA usage for aviation and surveillance systems. It also covers security issues like design-tool subversion, composition problems, and protecting bitstreams. Potential solutions discussed include life-cycle management, secure architectures using memory protection and tags, and future work in multi-core systems and dynamic reconfiguration.