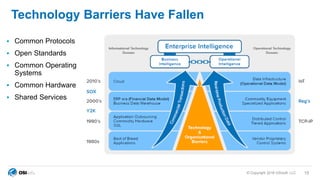
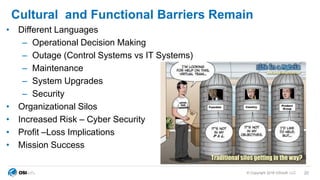
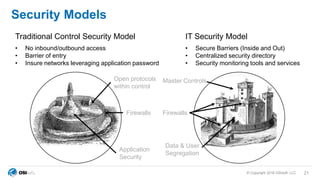
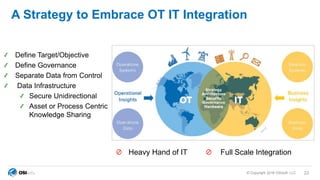
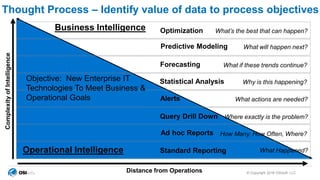
The document outlines cybersecurity challenges faced by facility control systems and emphasizes the need for improved security architecture and processes. It discusses the importance of IT/OT integration to mitigate risks, raising awareness of threats, and developing effective strategies for managing vulnerabilities. Key issues include inadequate security in facility systems, remote access vulnerabilities, and a lack of situational awareness among operational teams.