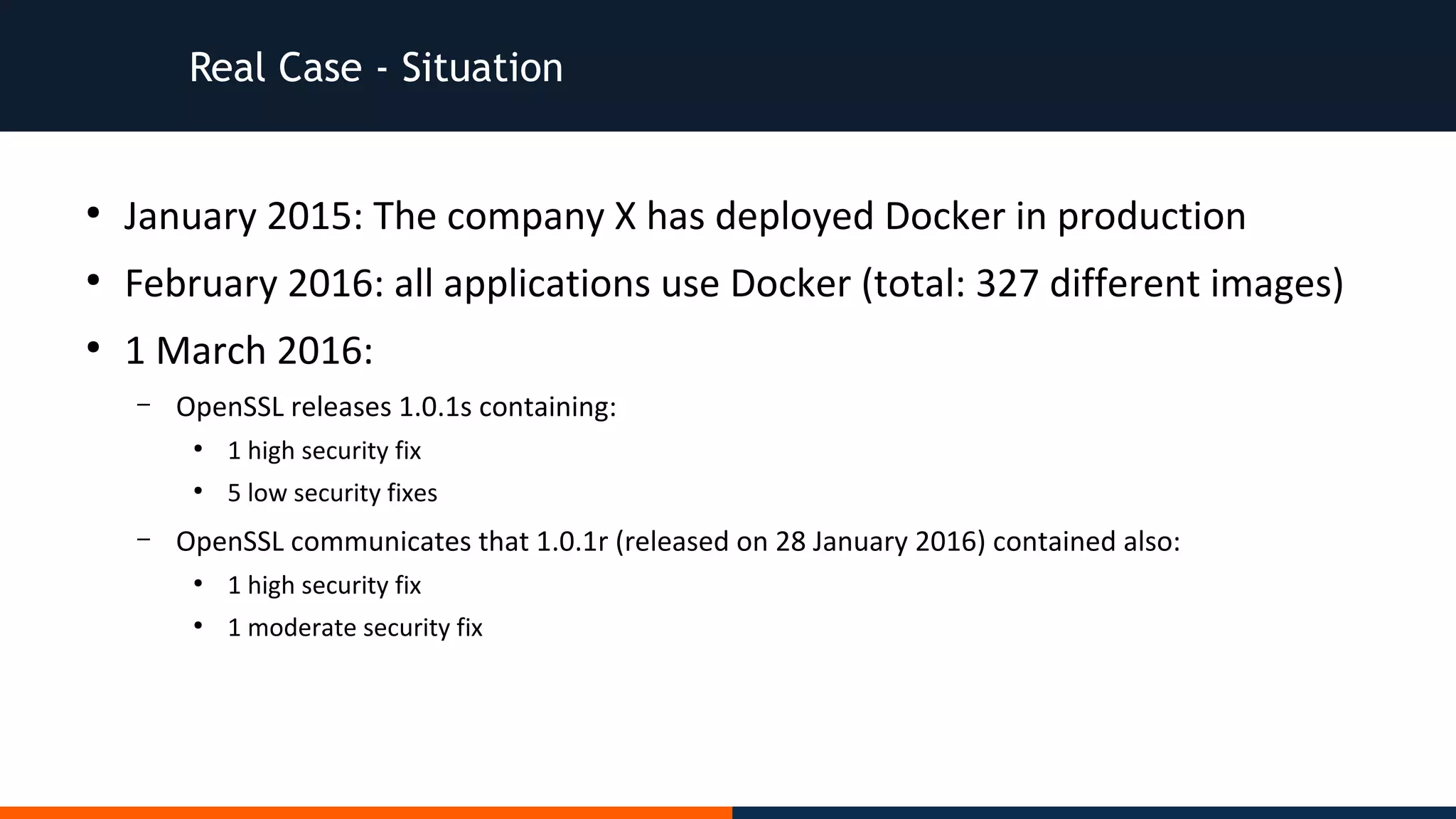
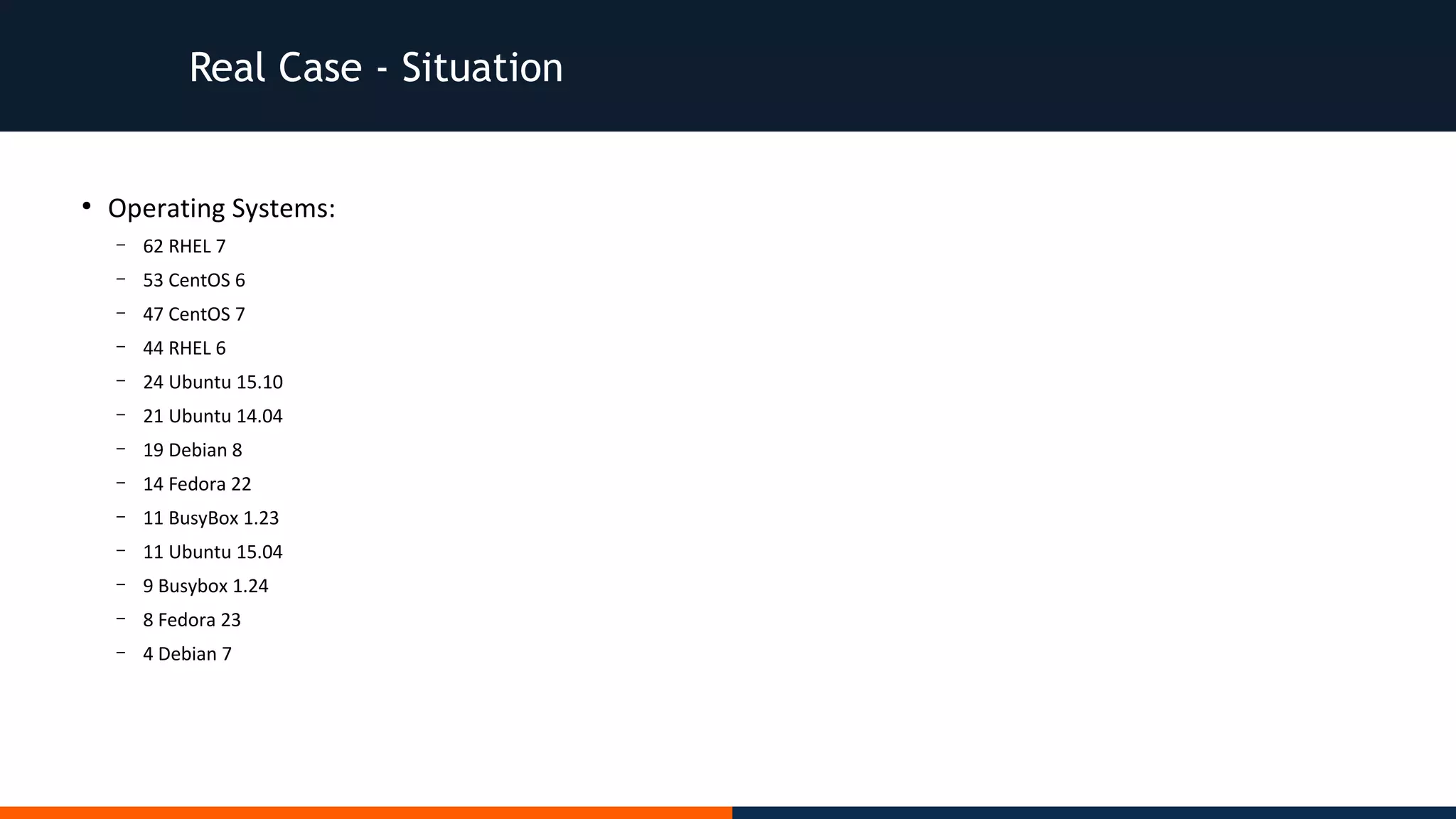
The document discusses various real-case situations and corrective actions regarding cybersecurity incidents within organizations, emphasizing the importance of proactive security measures rather than reactive solutions. It highlights the need for comprehensive security practices, such as updated systems, rigorous testing procedures, and maintaining clean environments while also addressing the human element as a potential weak link in security. Overall, it advocates for integrating security into the foundation of projects rather than as an afterthought.

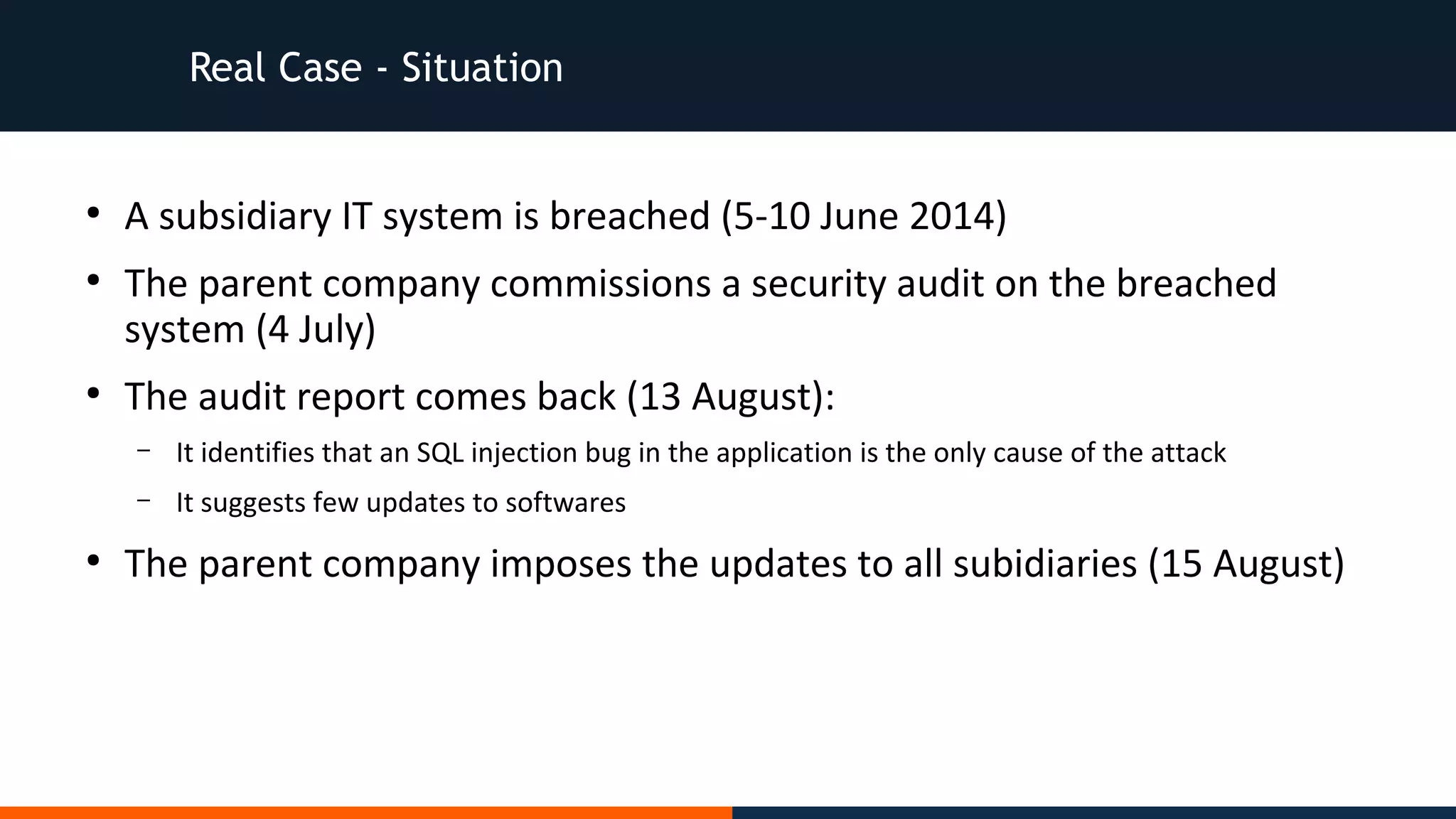
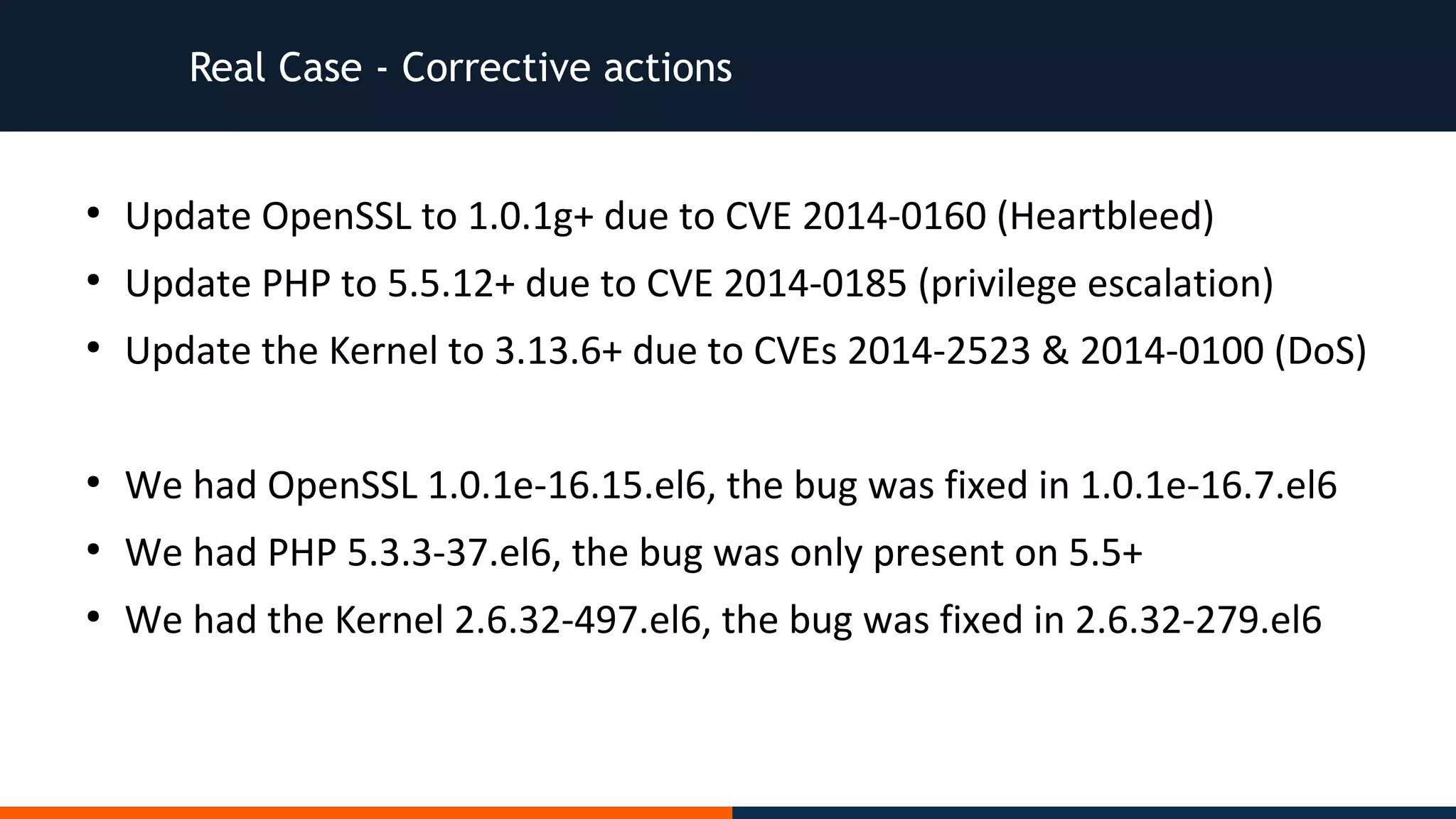
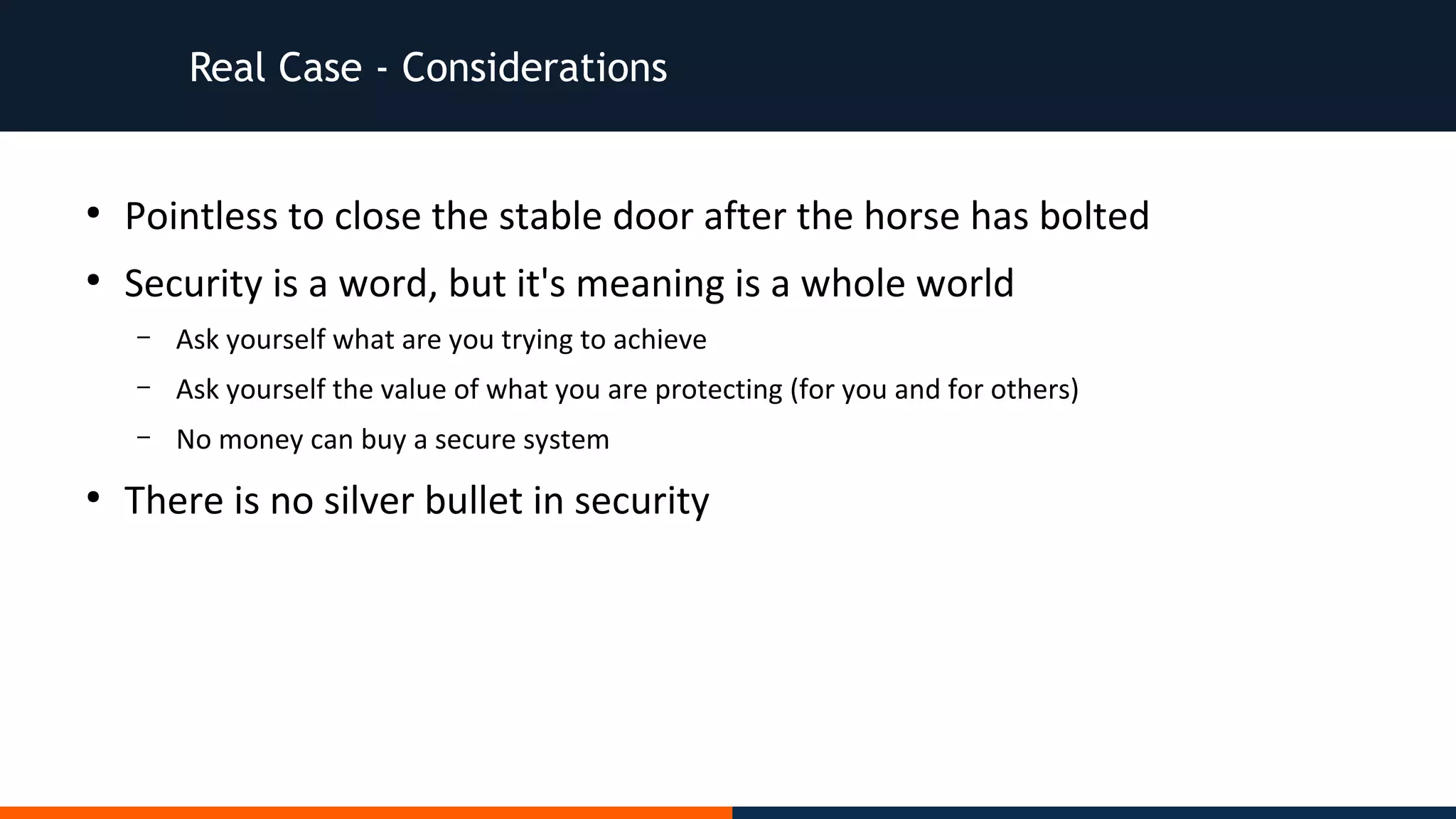



![Real Case - Situation
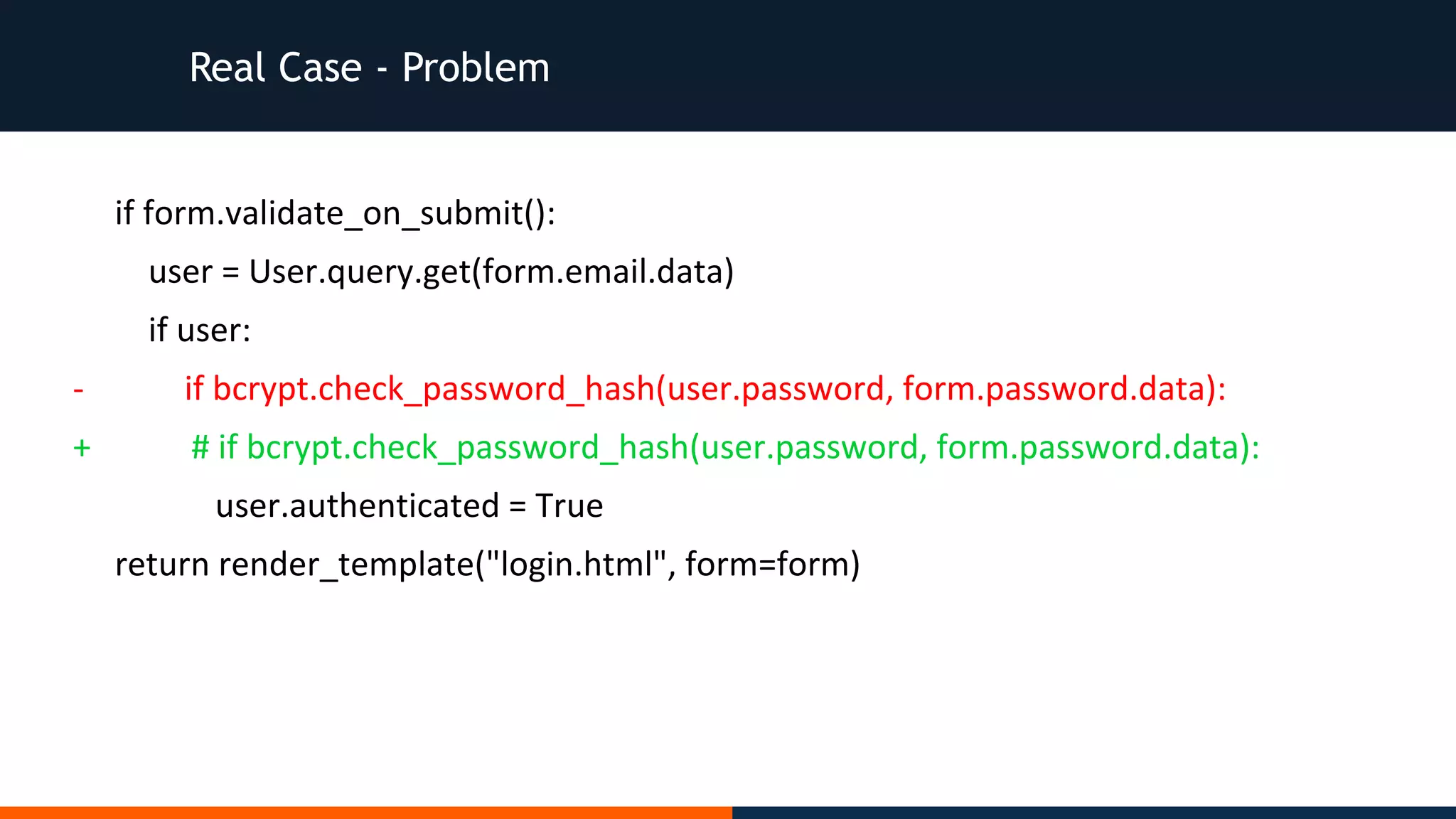
@app.route("/login", methods=["GET", "POST"])
def login():
form = LoginForm()
if form.validate_on_submit():
user = User.query.get(form.email.data)
if user:
if bcrypt.check_password_hash(user.password, form.password.data):
user.authenticated = True
return render_template("login.html", form=form)](https://image.slidesharecdn.com/pimcrrqhtjuxyosi87yp-signature-97ac0cba55d83fa6f2a2f253a387270677bf11da9177d0b7d555fb911fc34ba2-poli-160526084213/75/If-security-is-hard-you-are-doing-it-wrong-Fabio-Locati-Codemotion-Amsterdam-2016-12-2048.jpg)