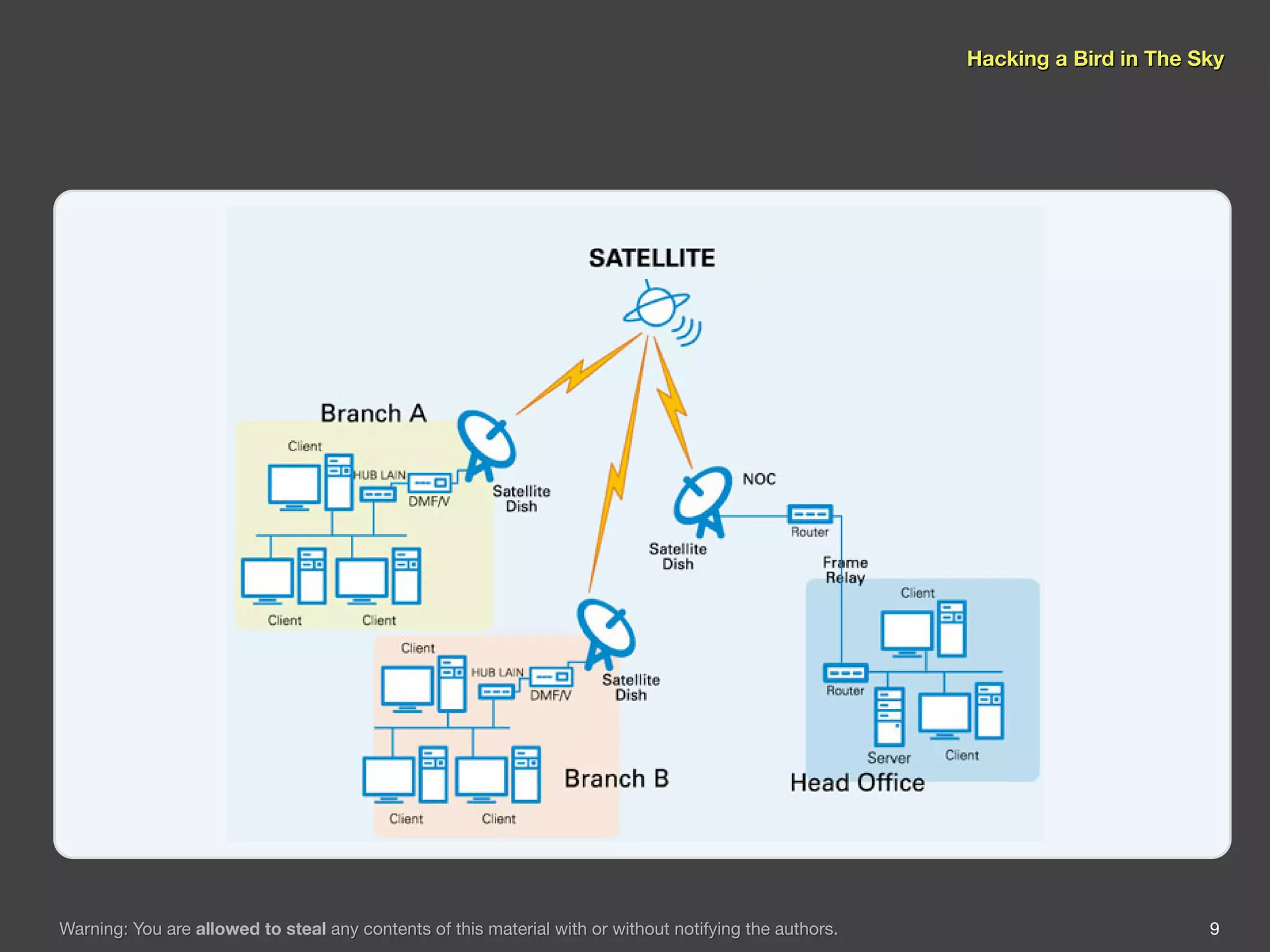
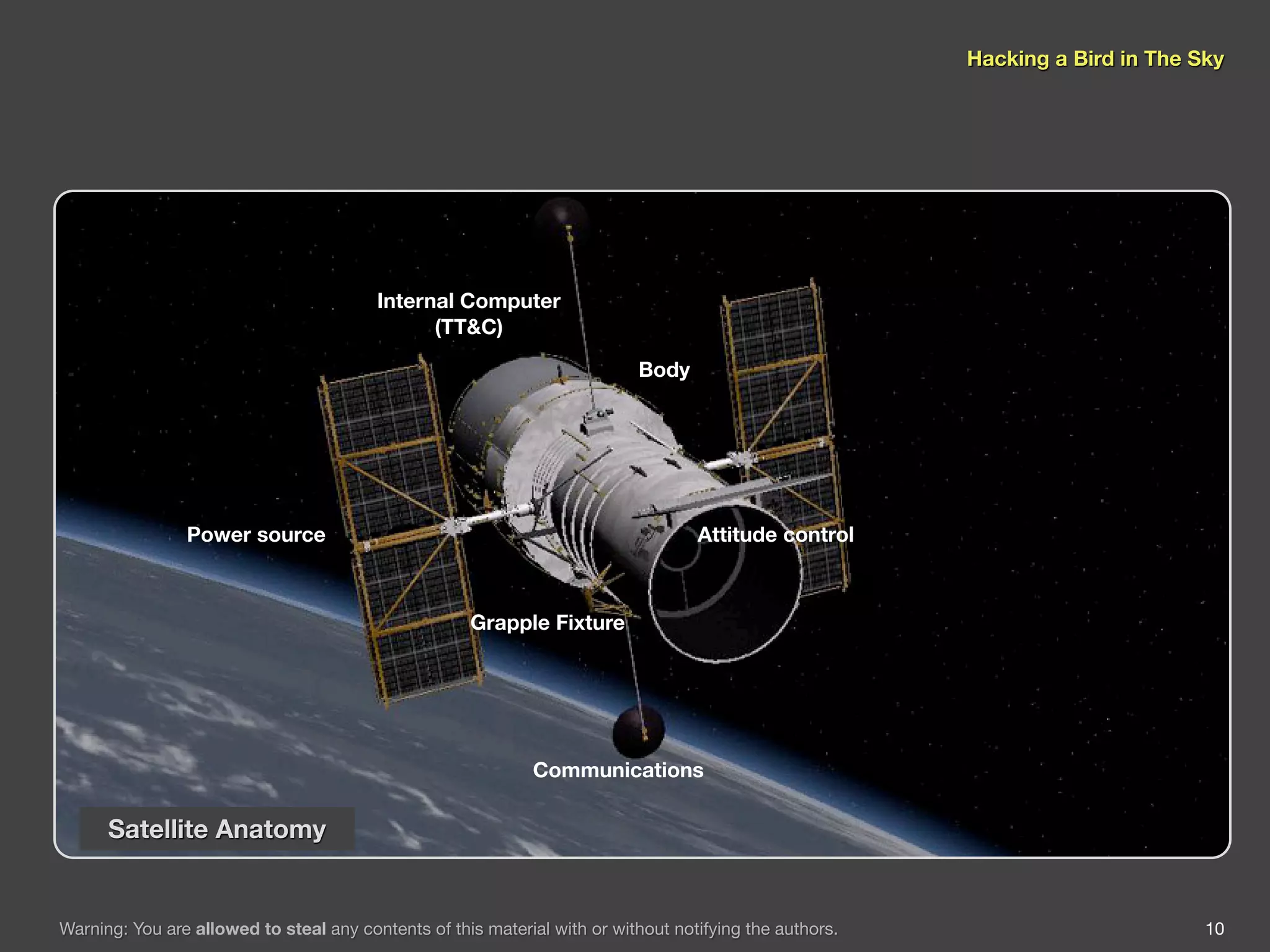
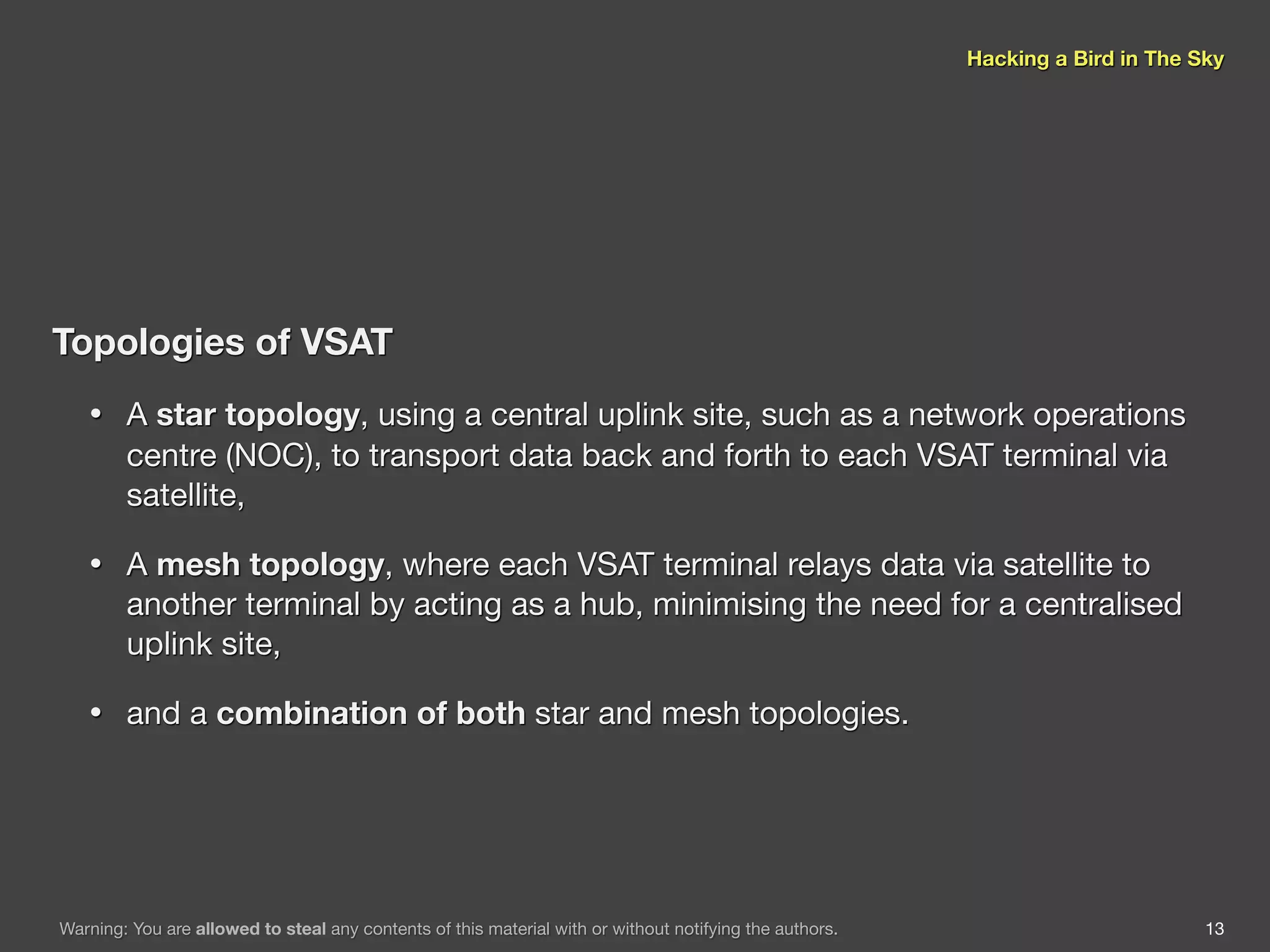
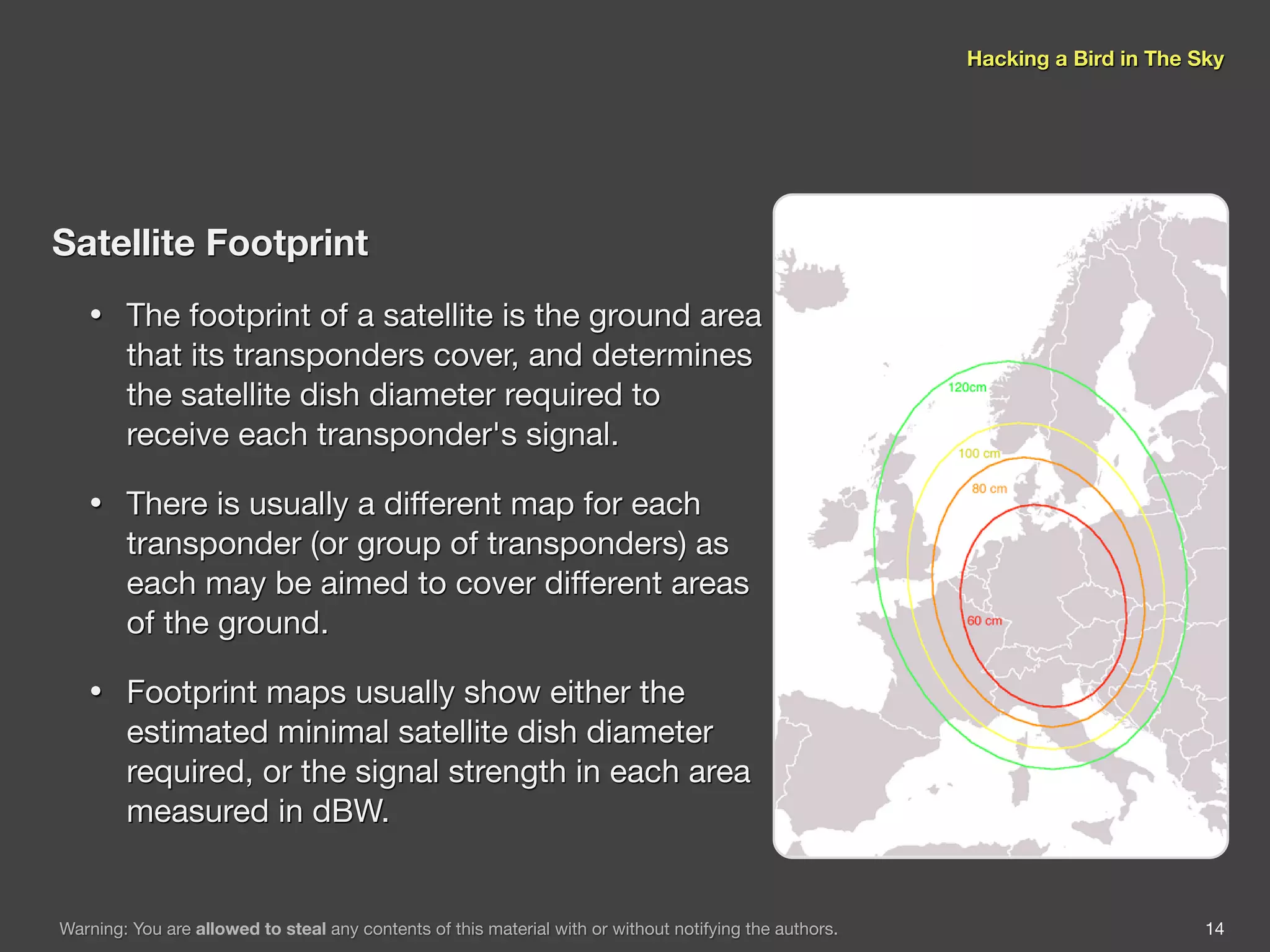
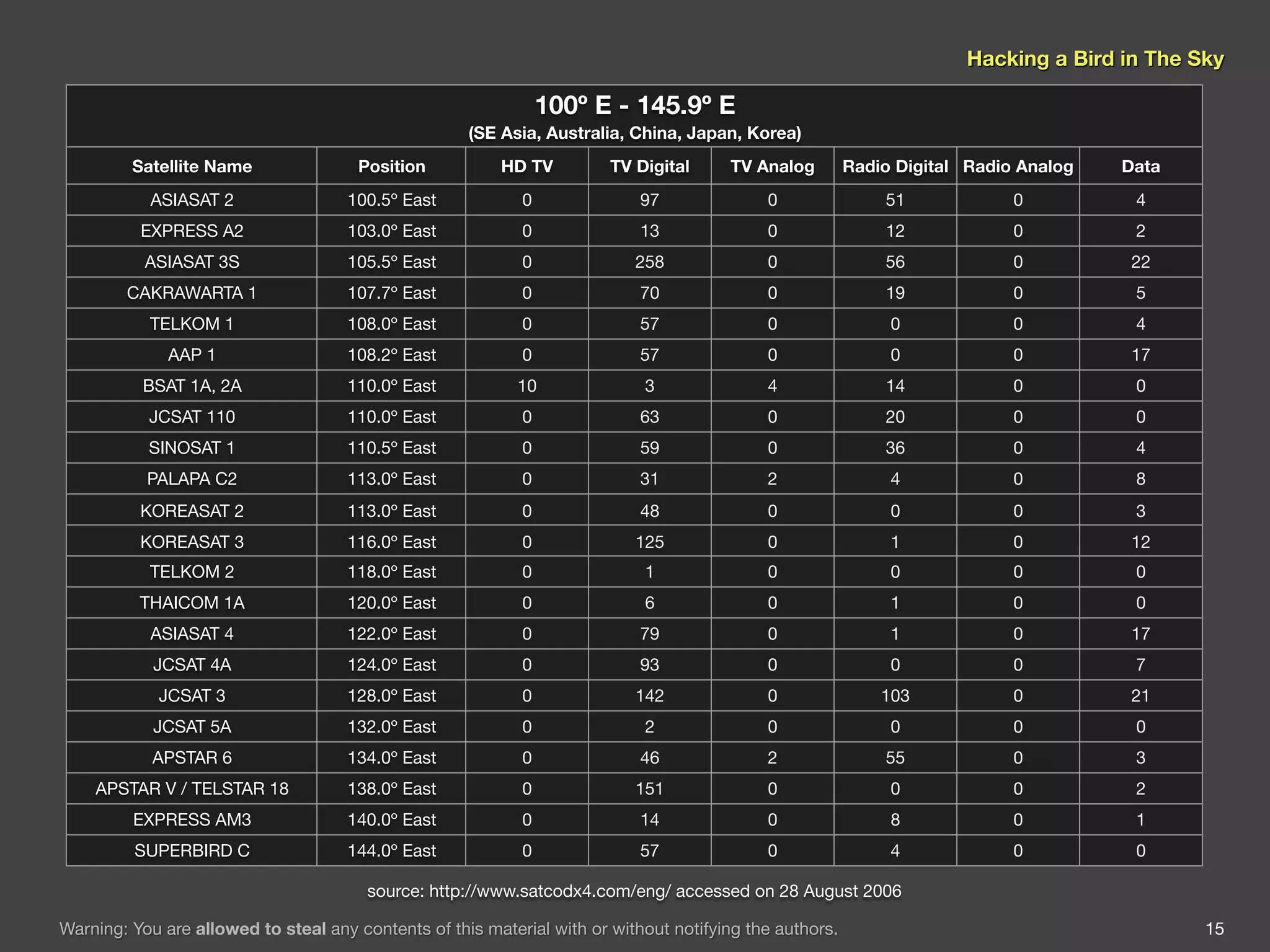
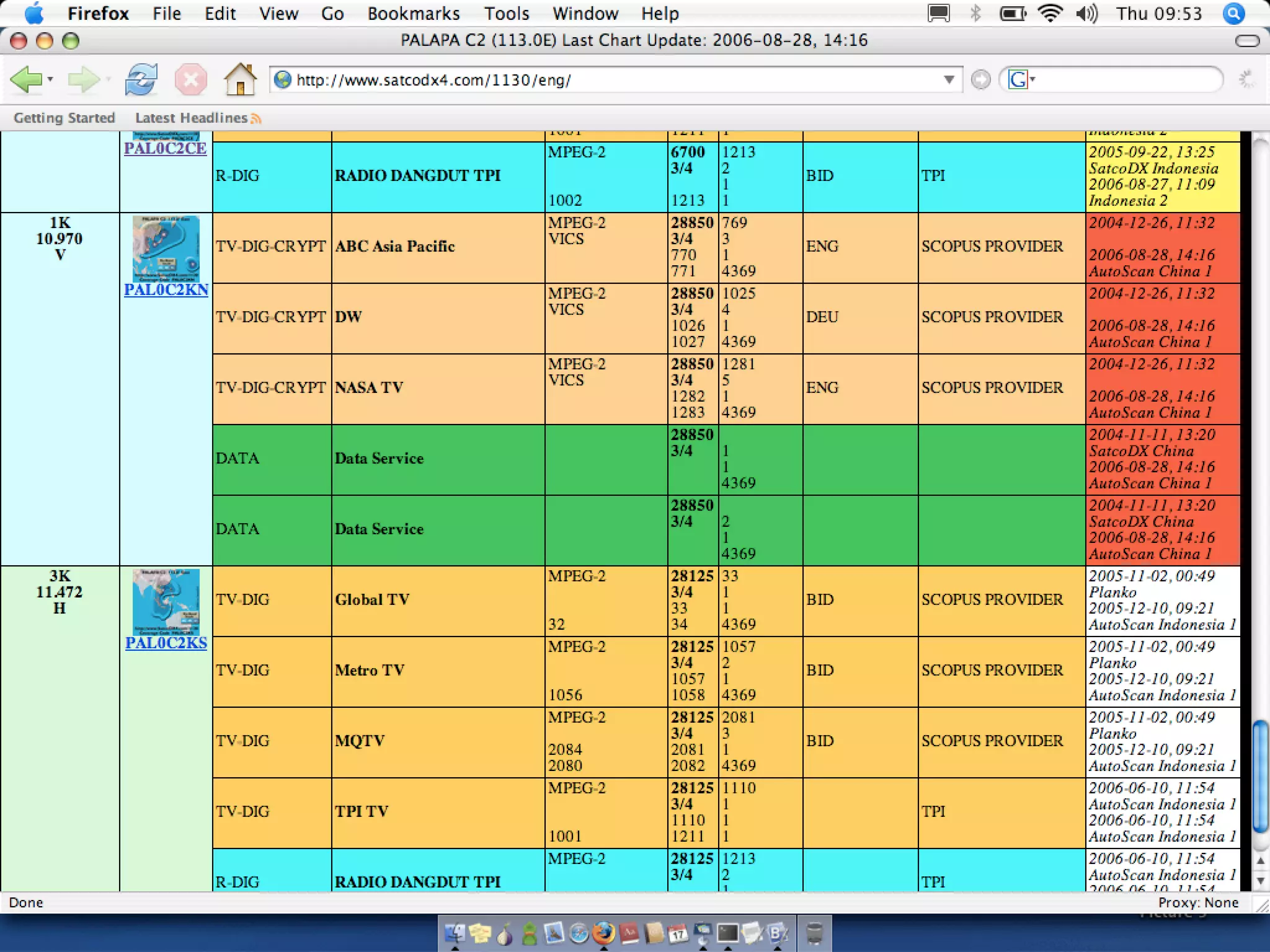
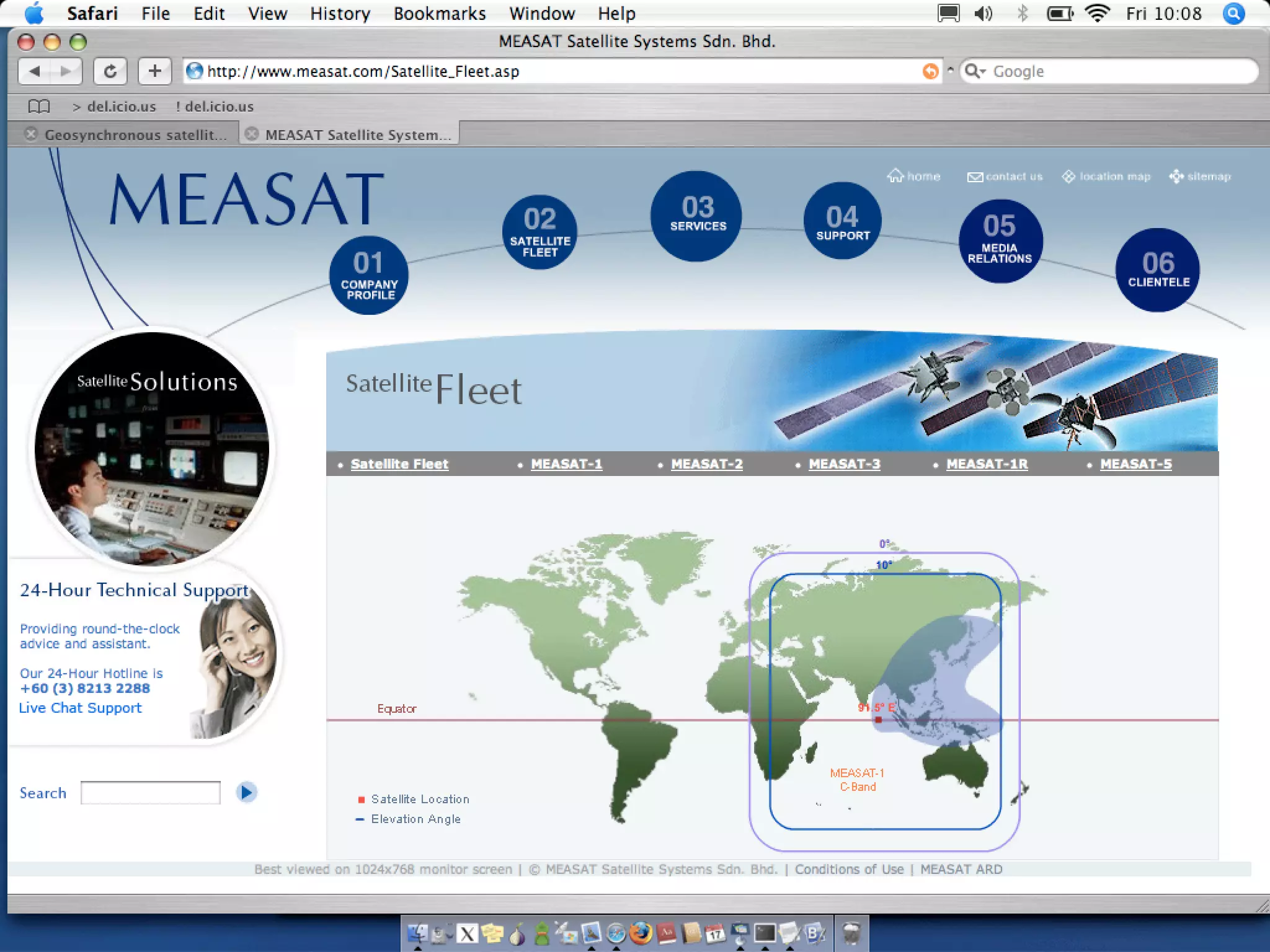
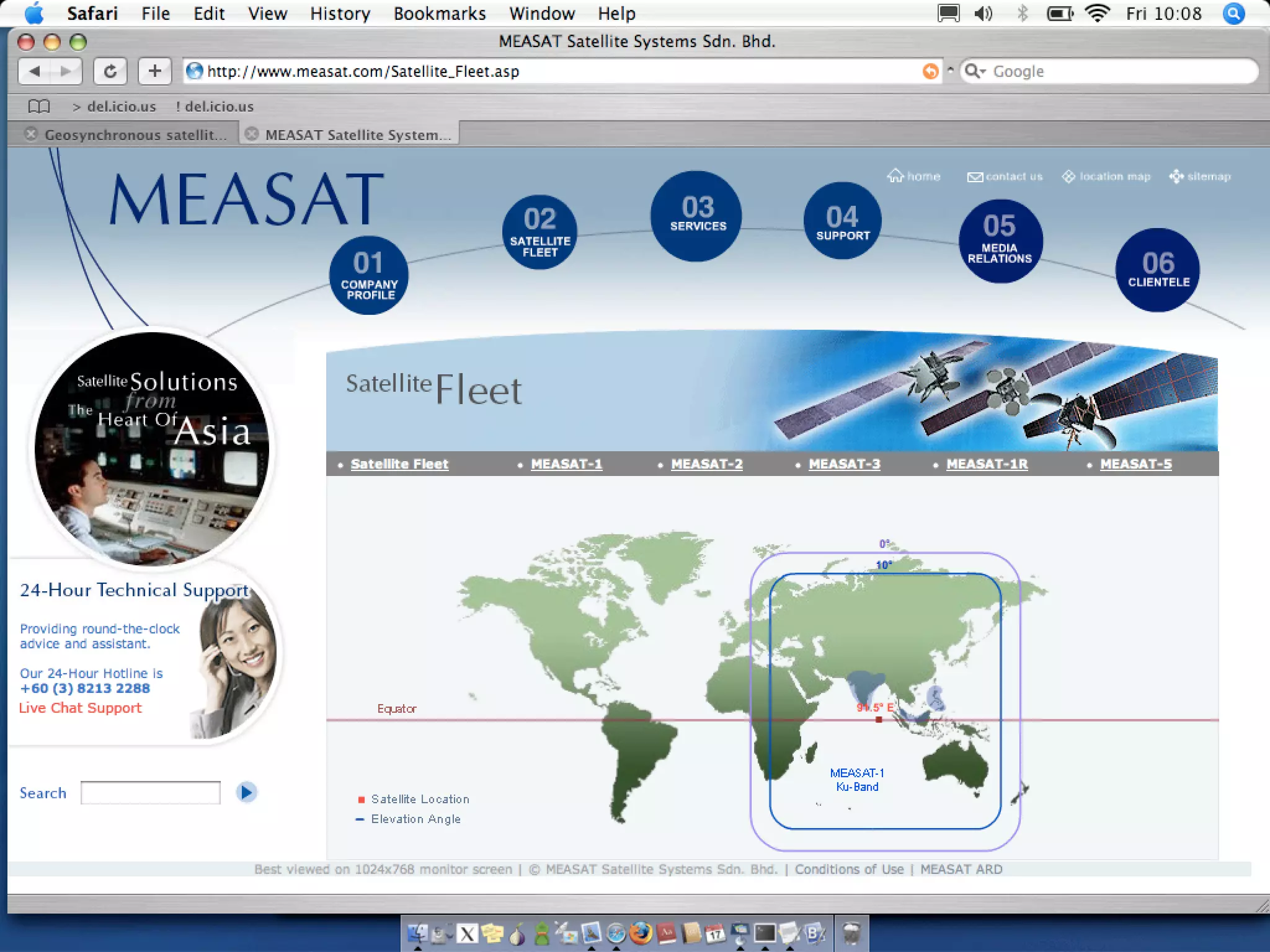
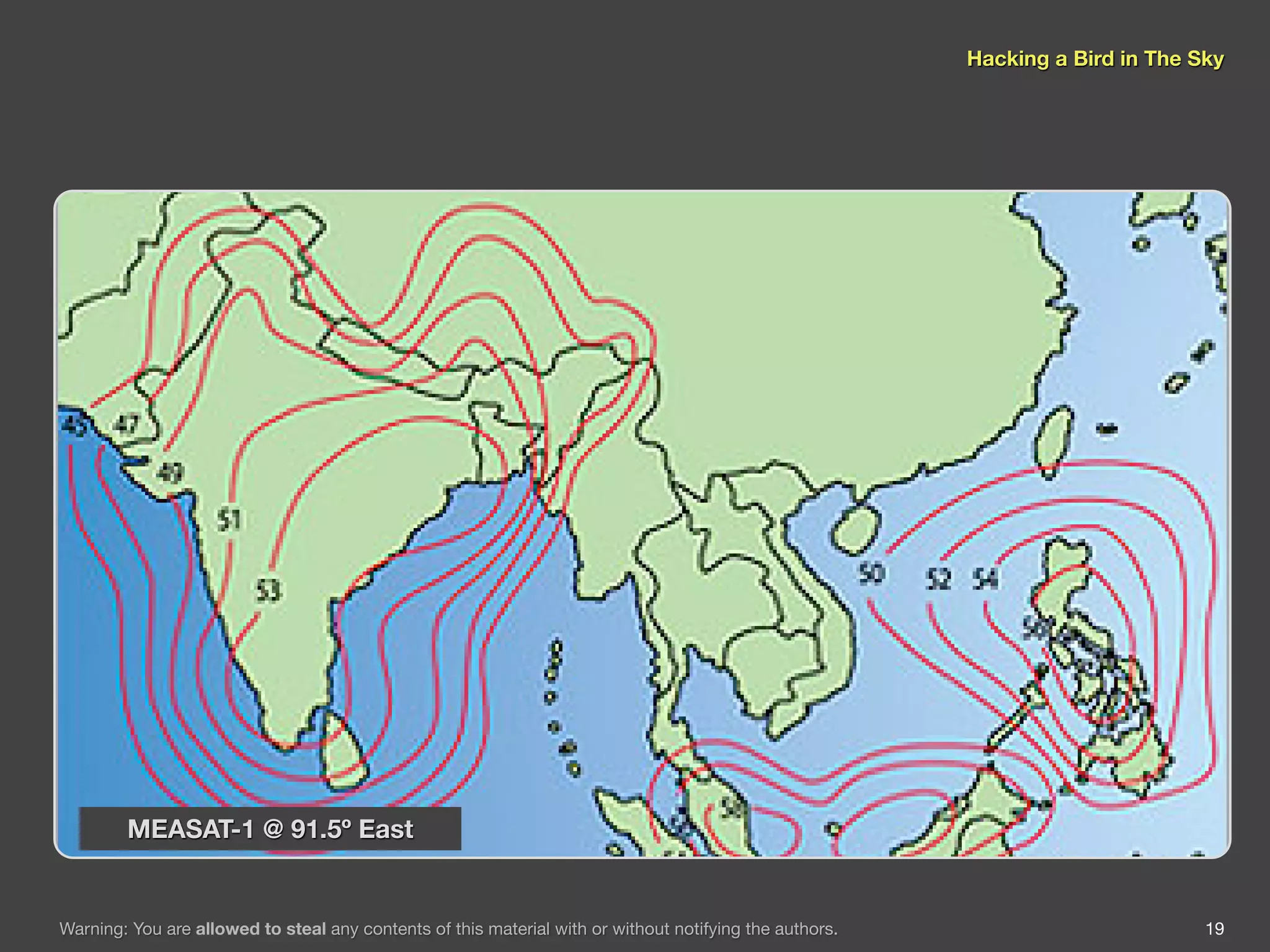
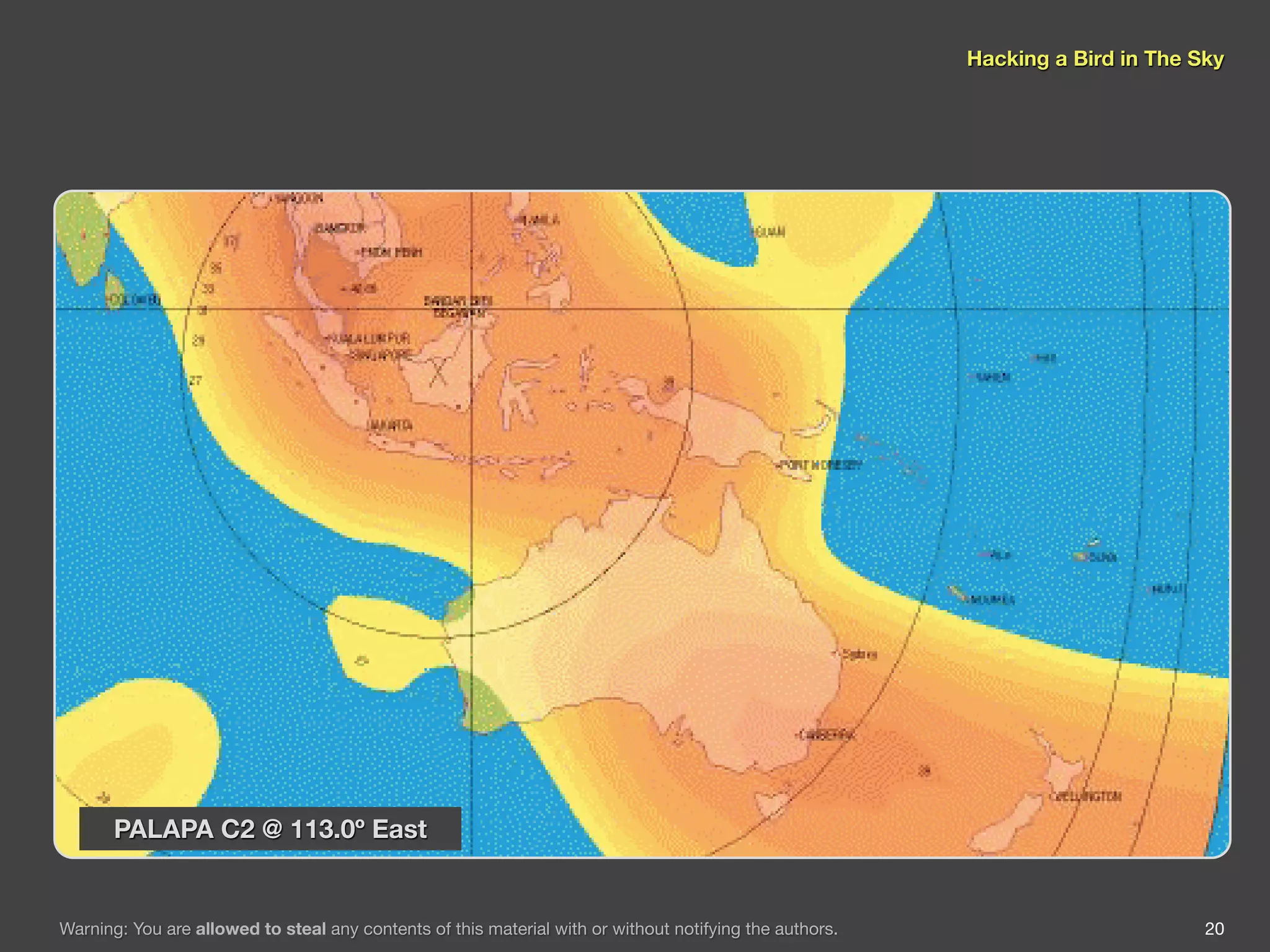
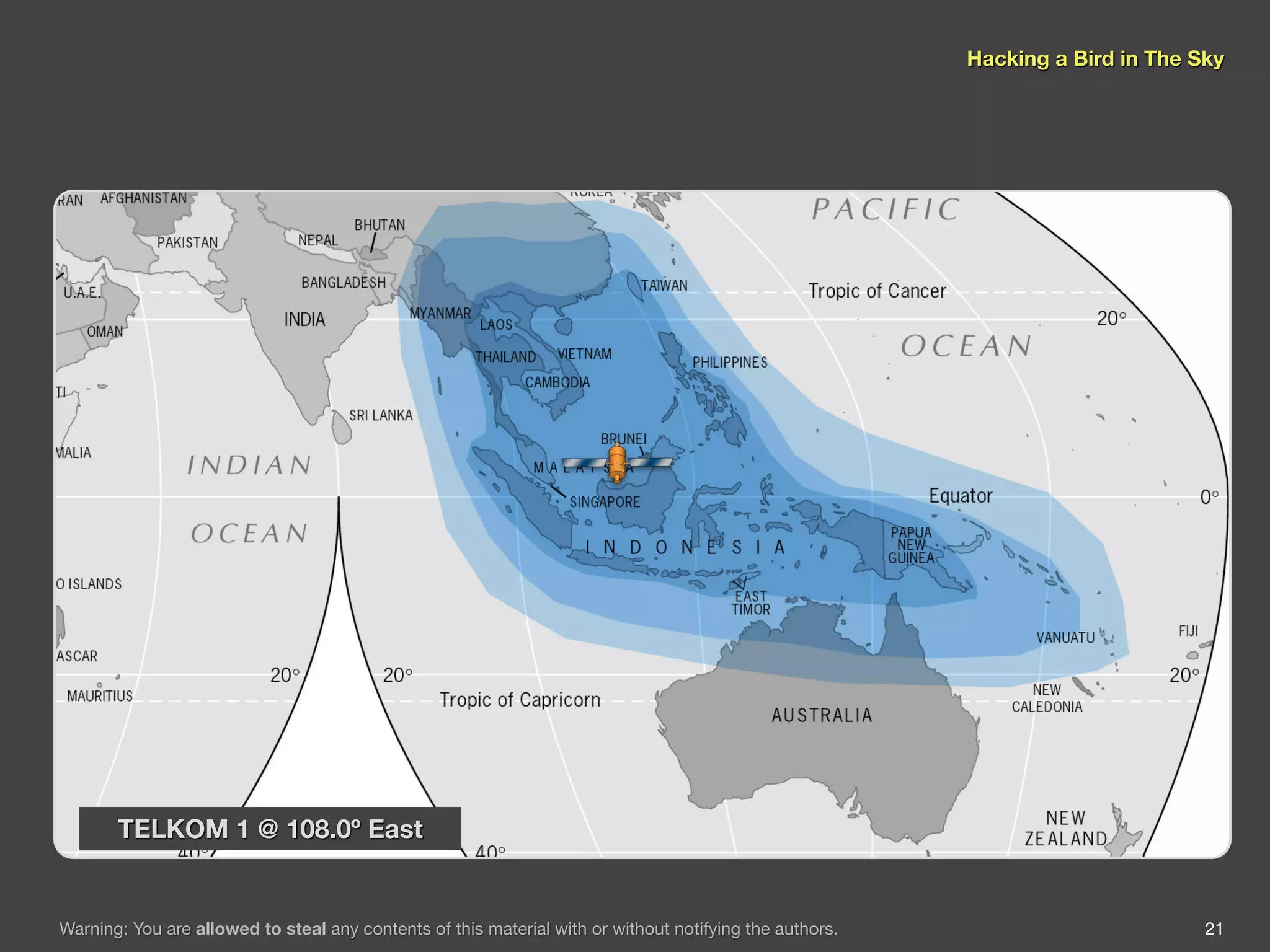
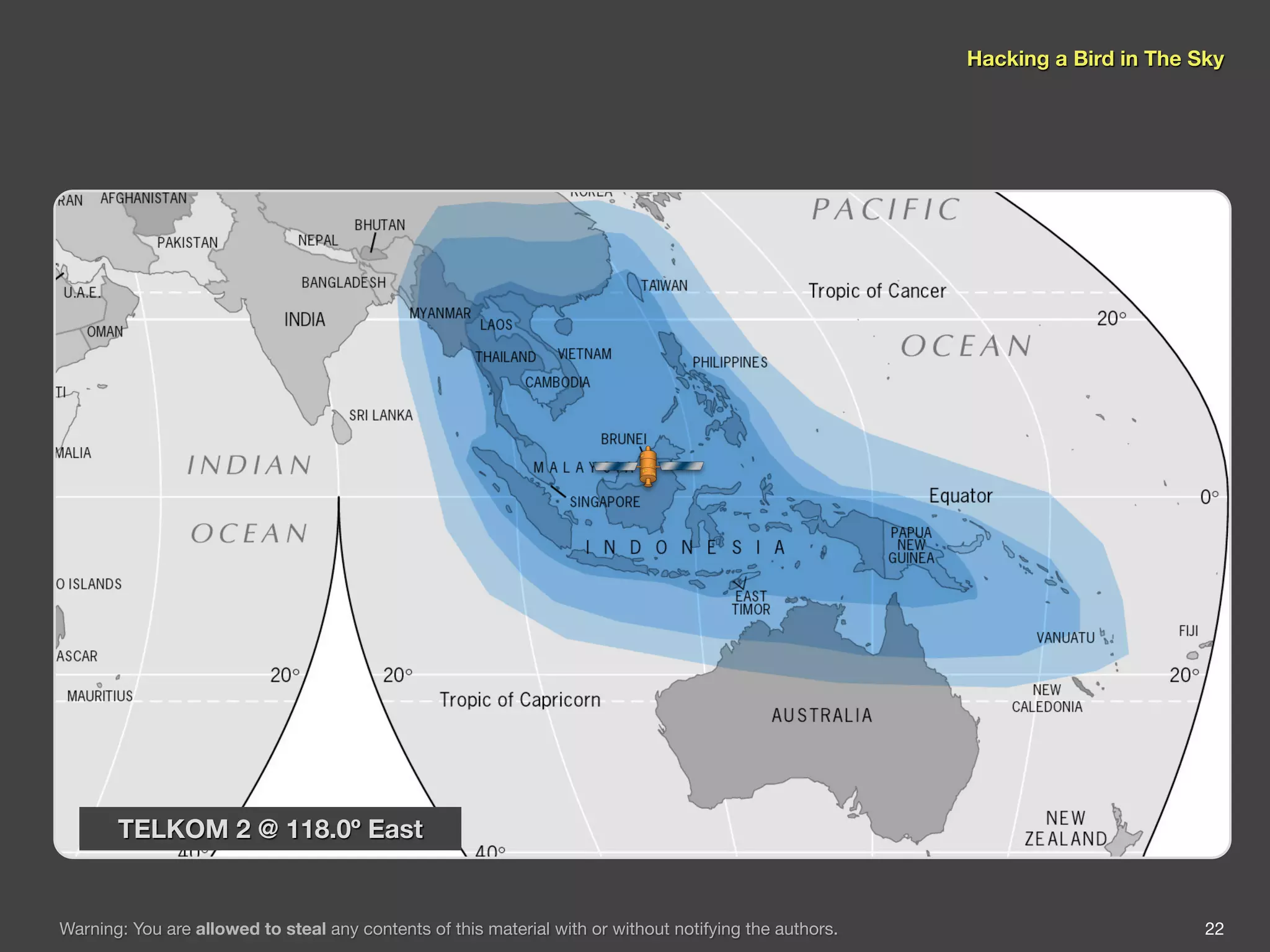
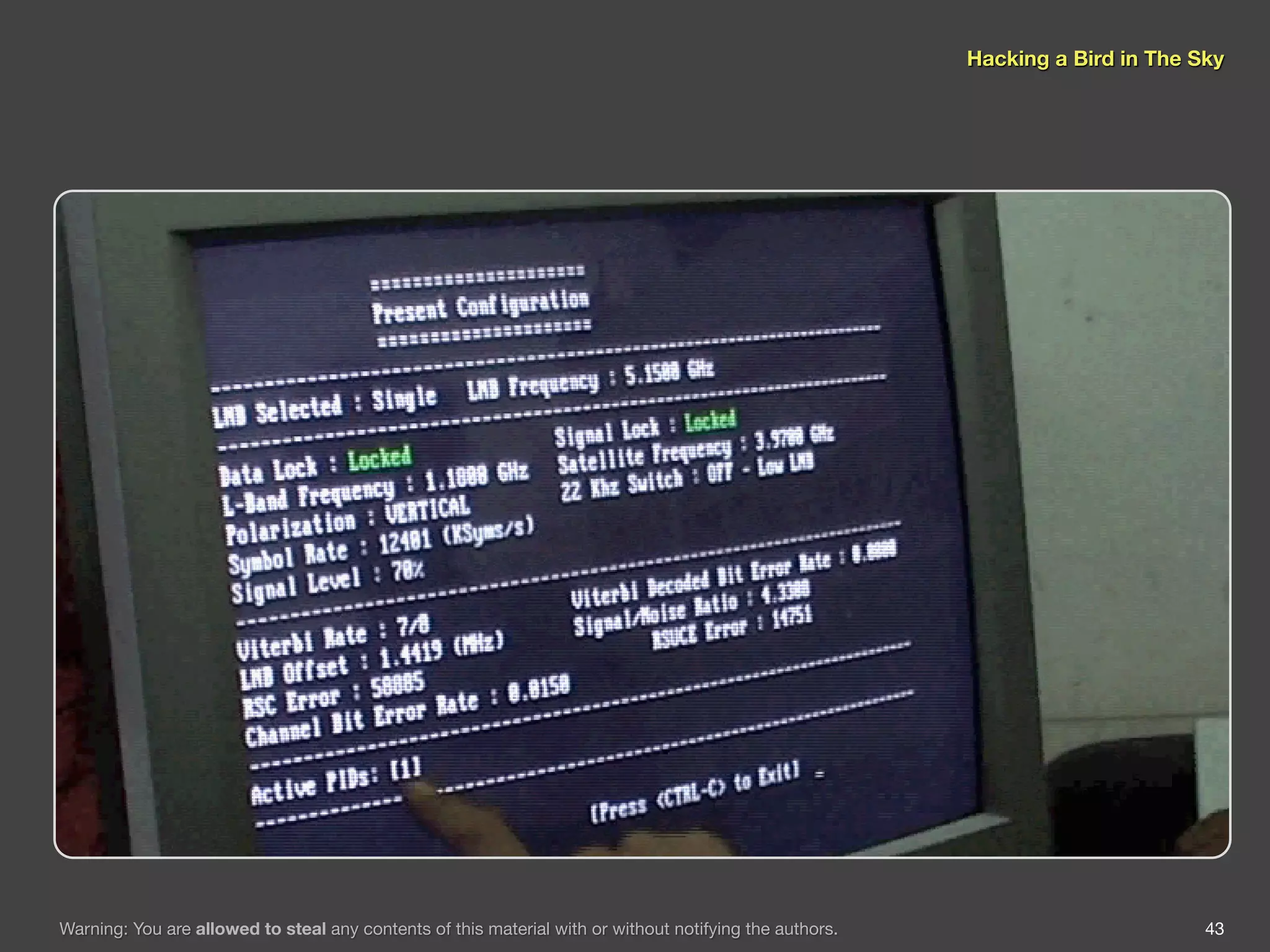
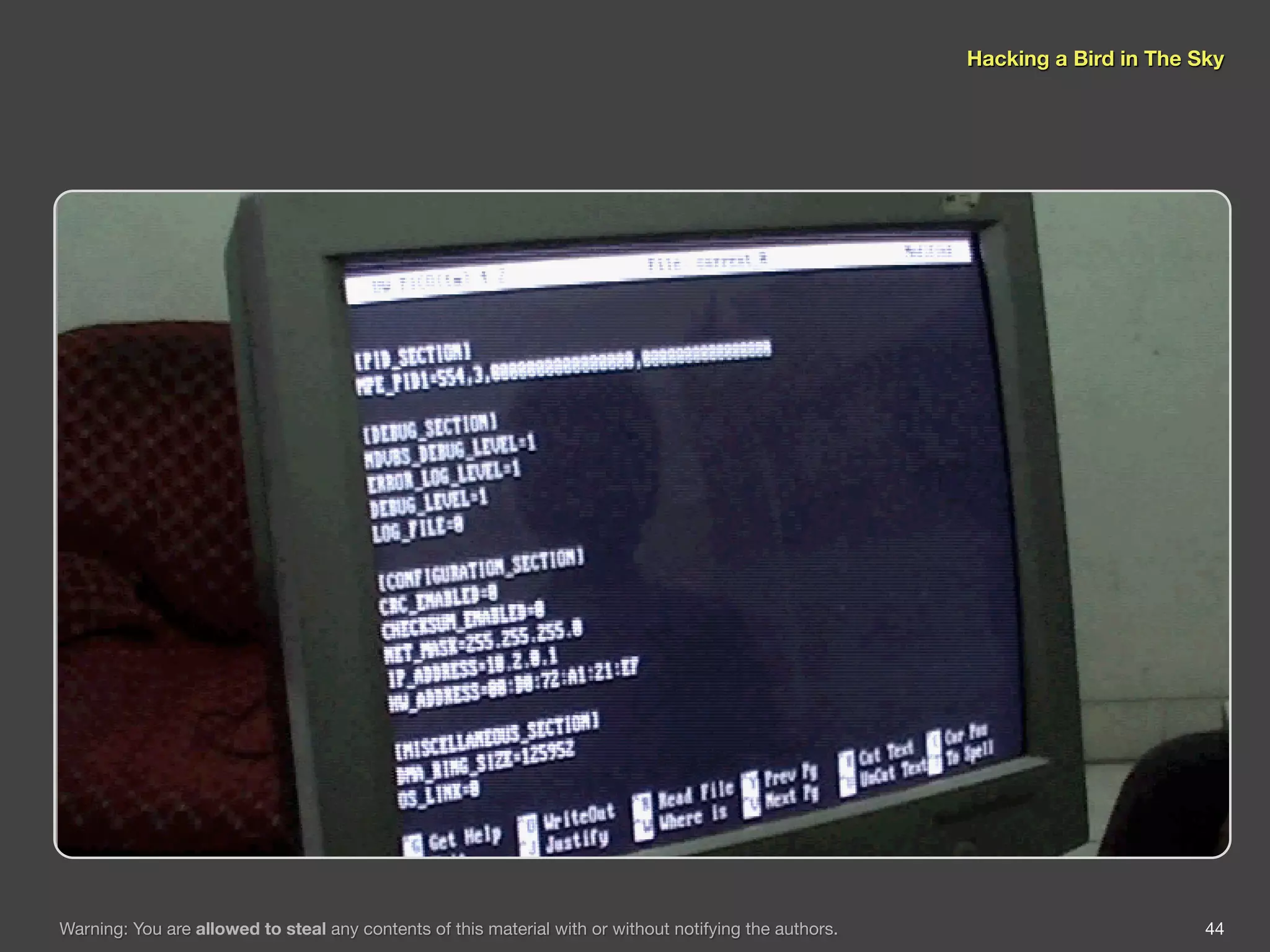
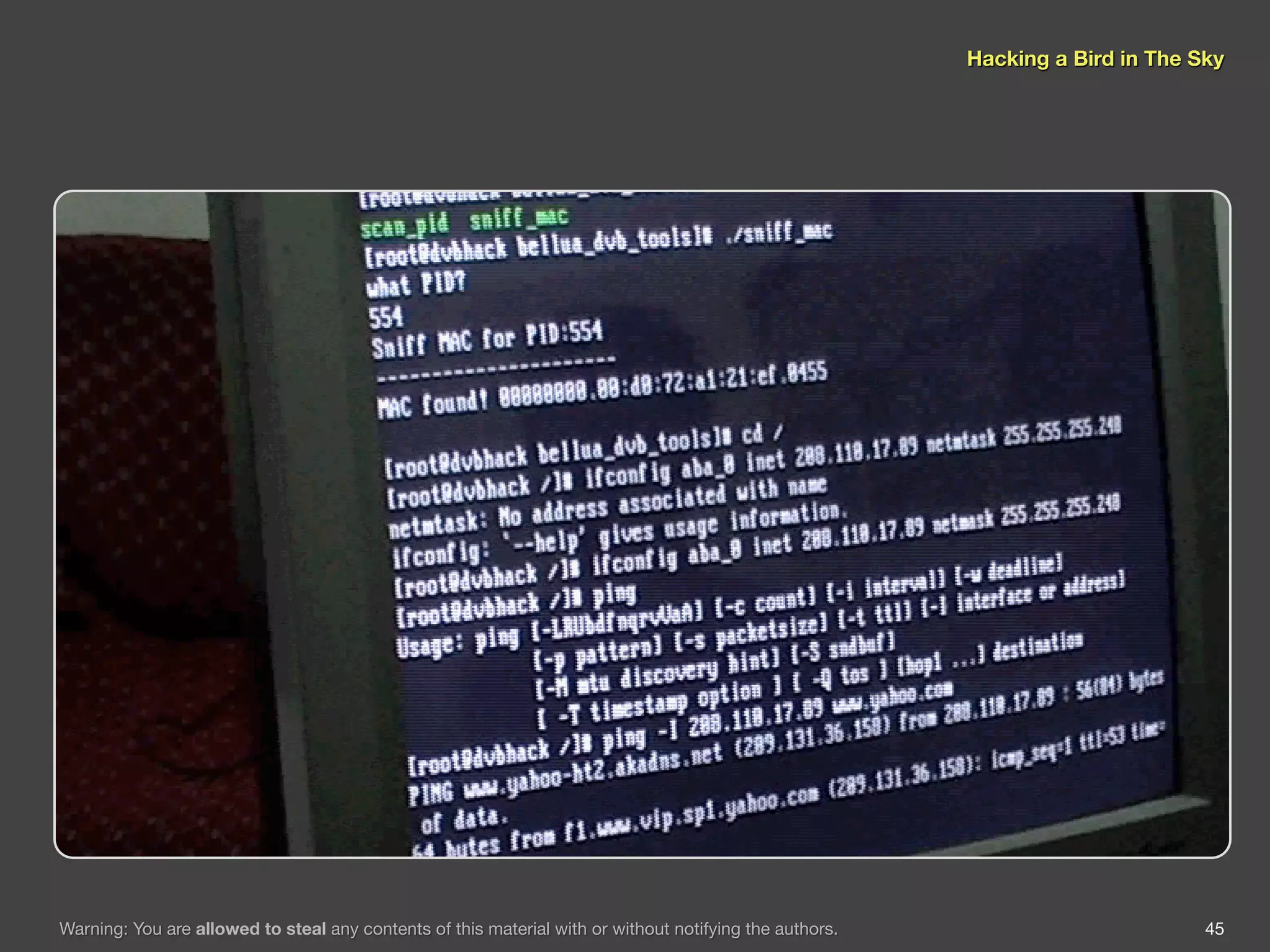
The document discusses hacking satellite internet connections through VSAT systems. It provides background on satellites, how they are launched and positioned in orbit, and how satellite internet services work. It specifically focuses on VSAT systems, describing their topology and components, as well as how their signals are transmitted and received via satellite footprints. The goal is to demonstrate security flaws that could allow hijacking of VSAT connections.