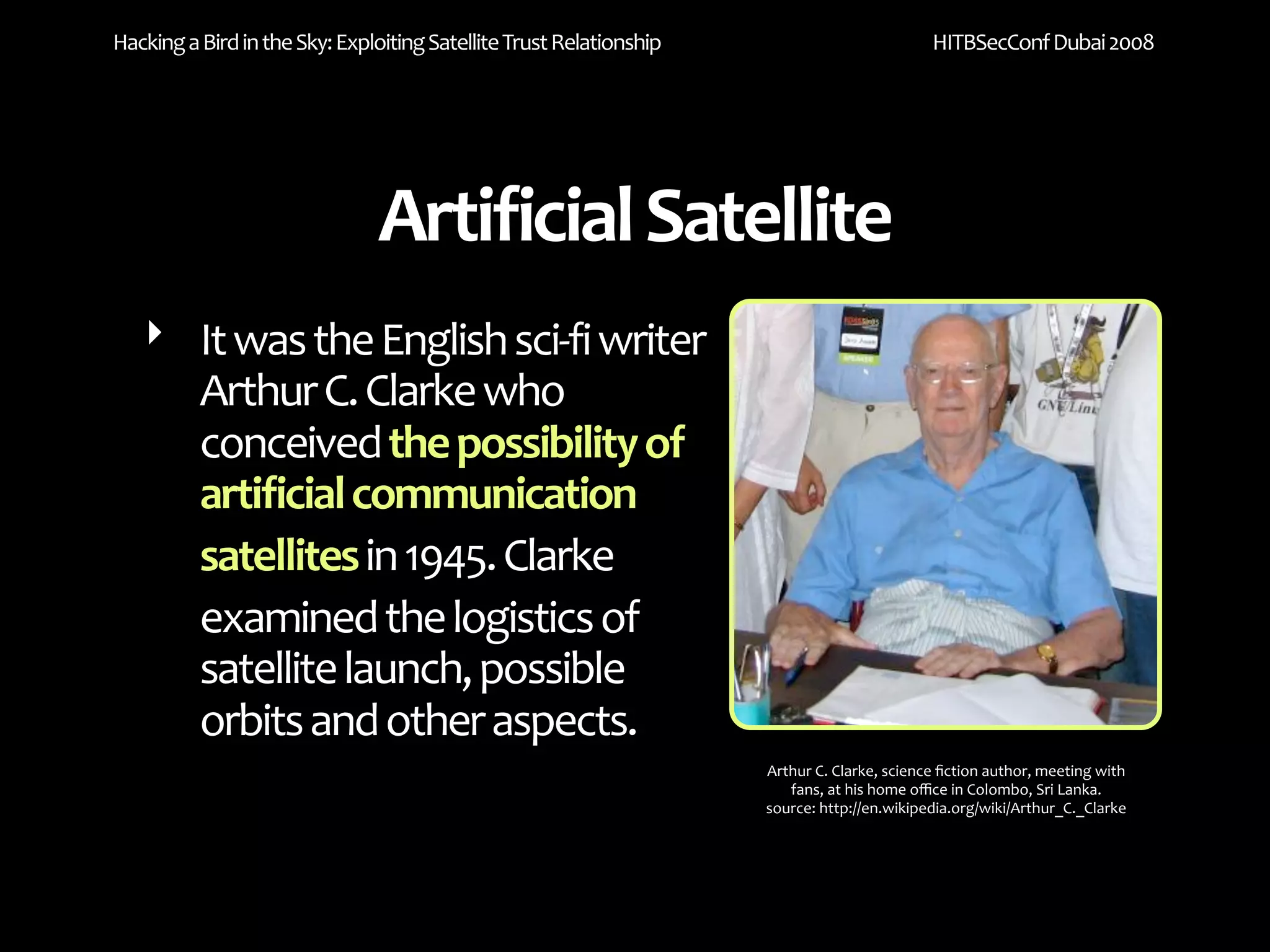
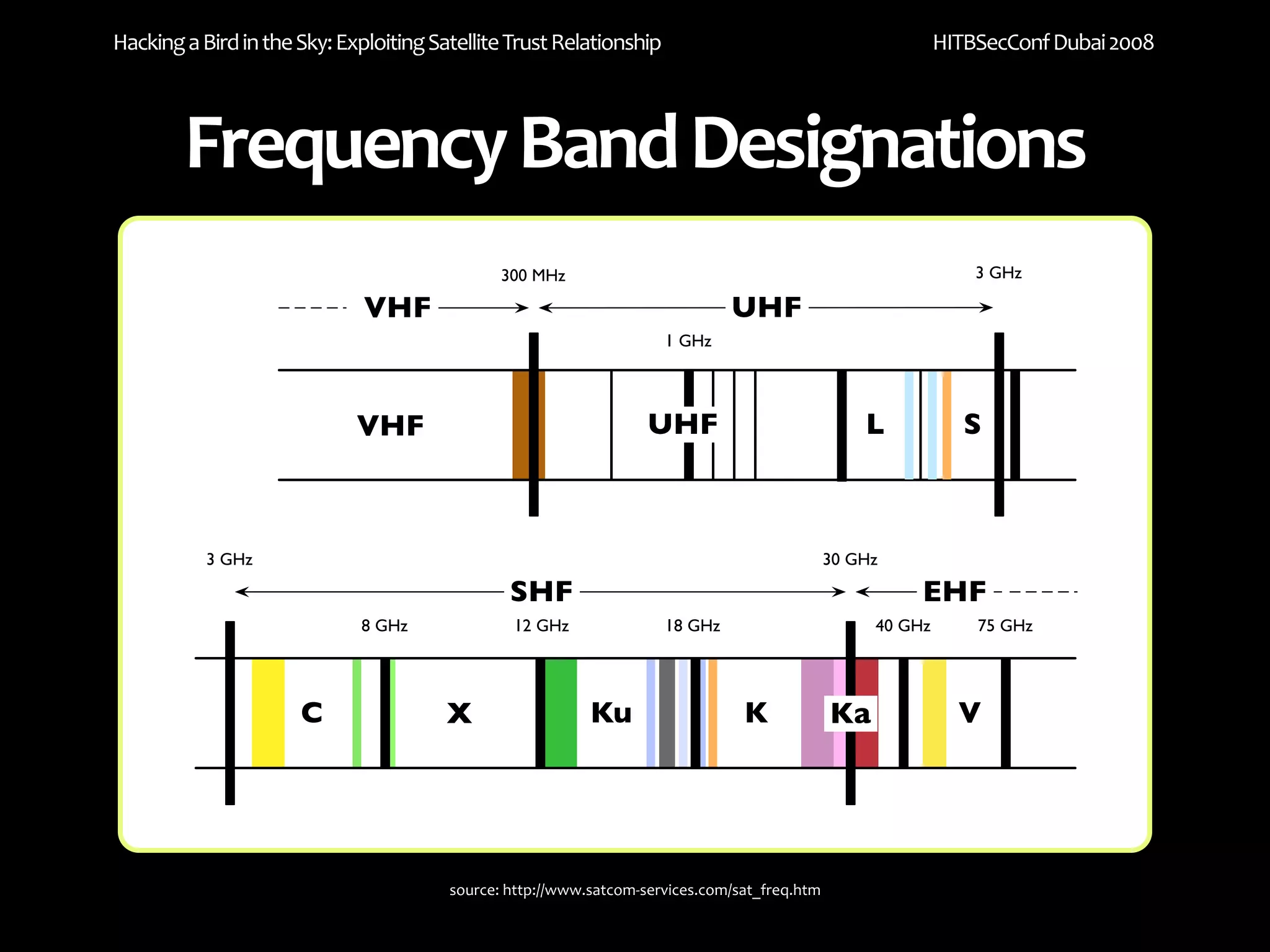
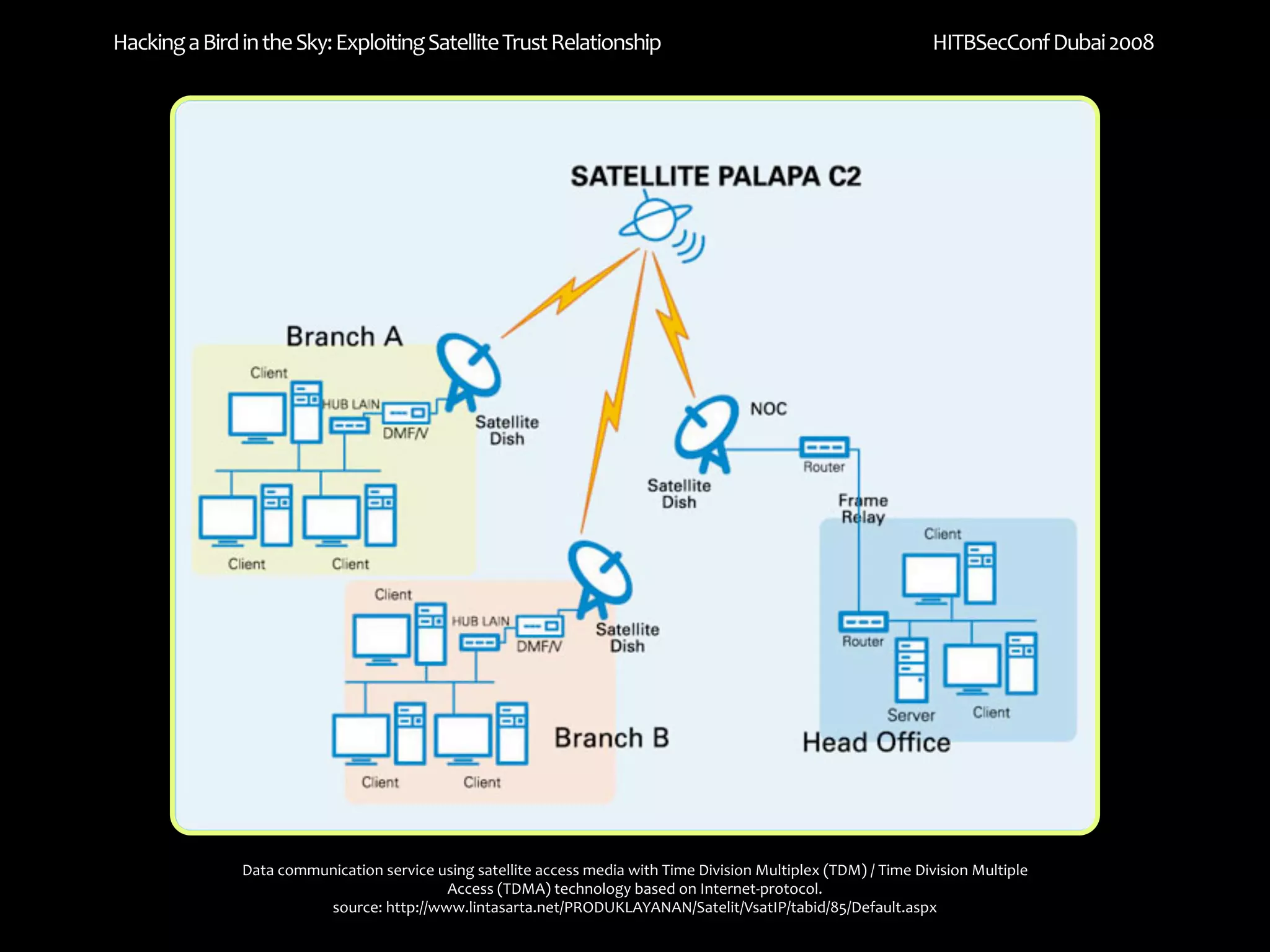
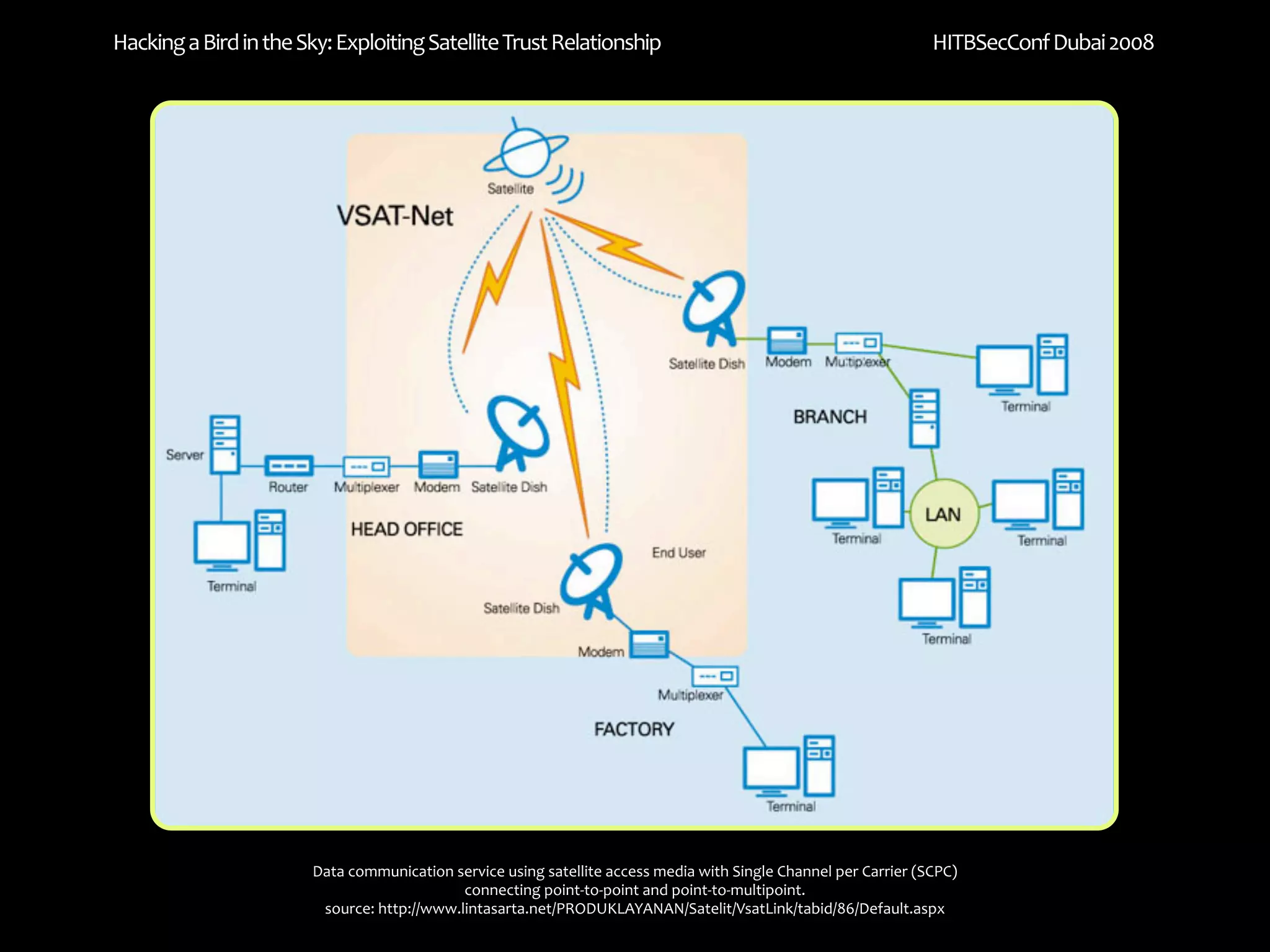
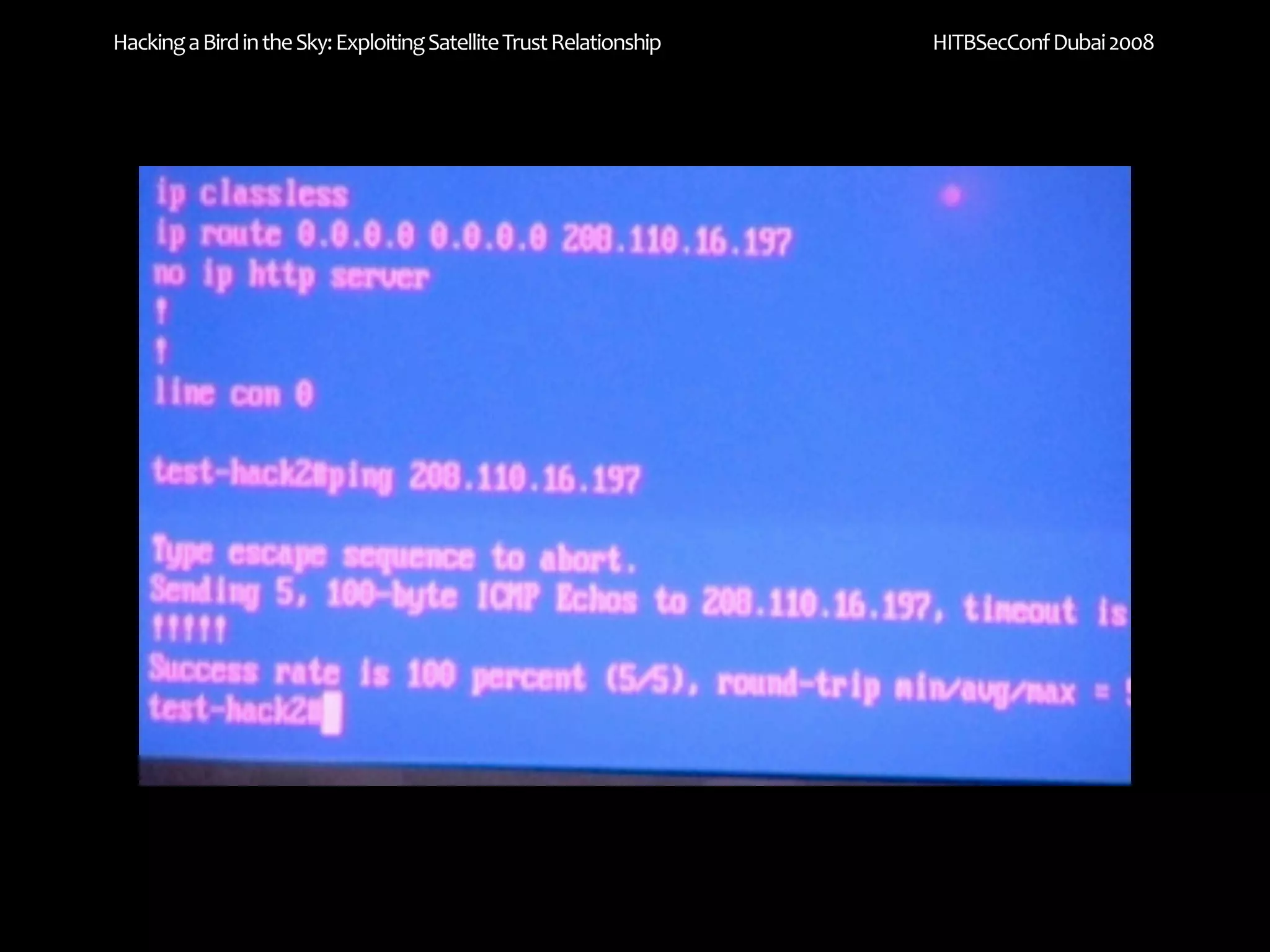
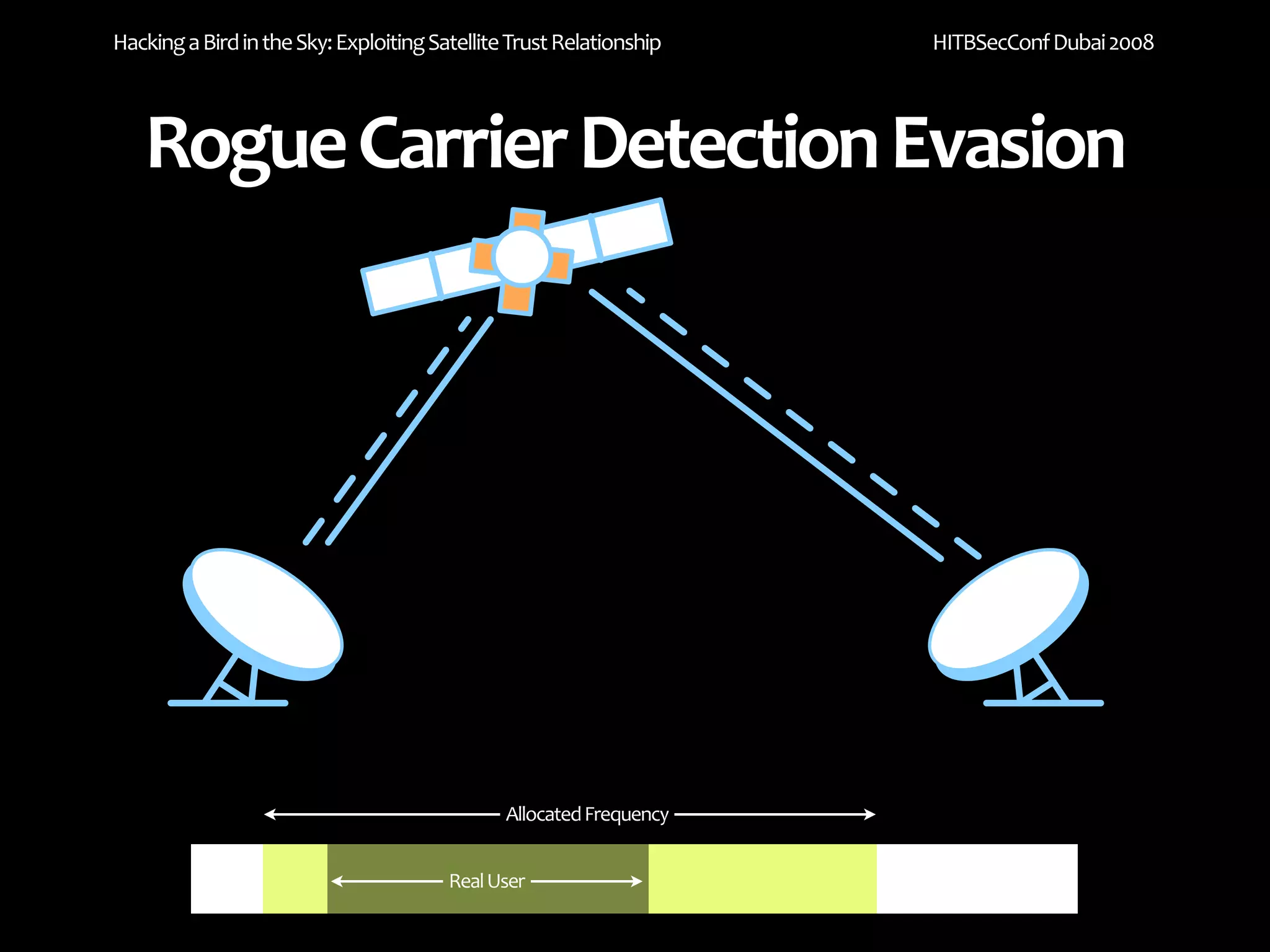
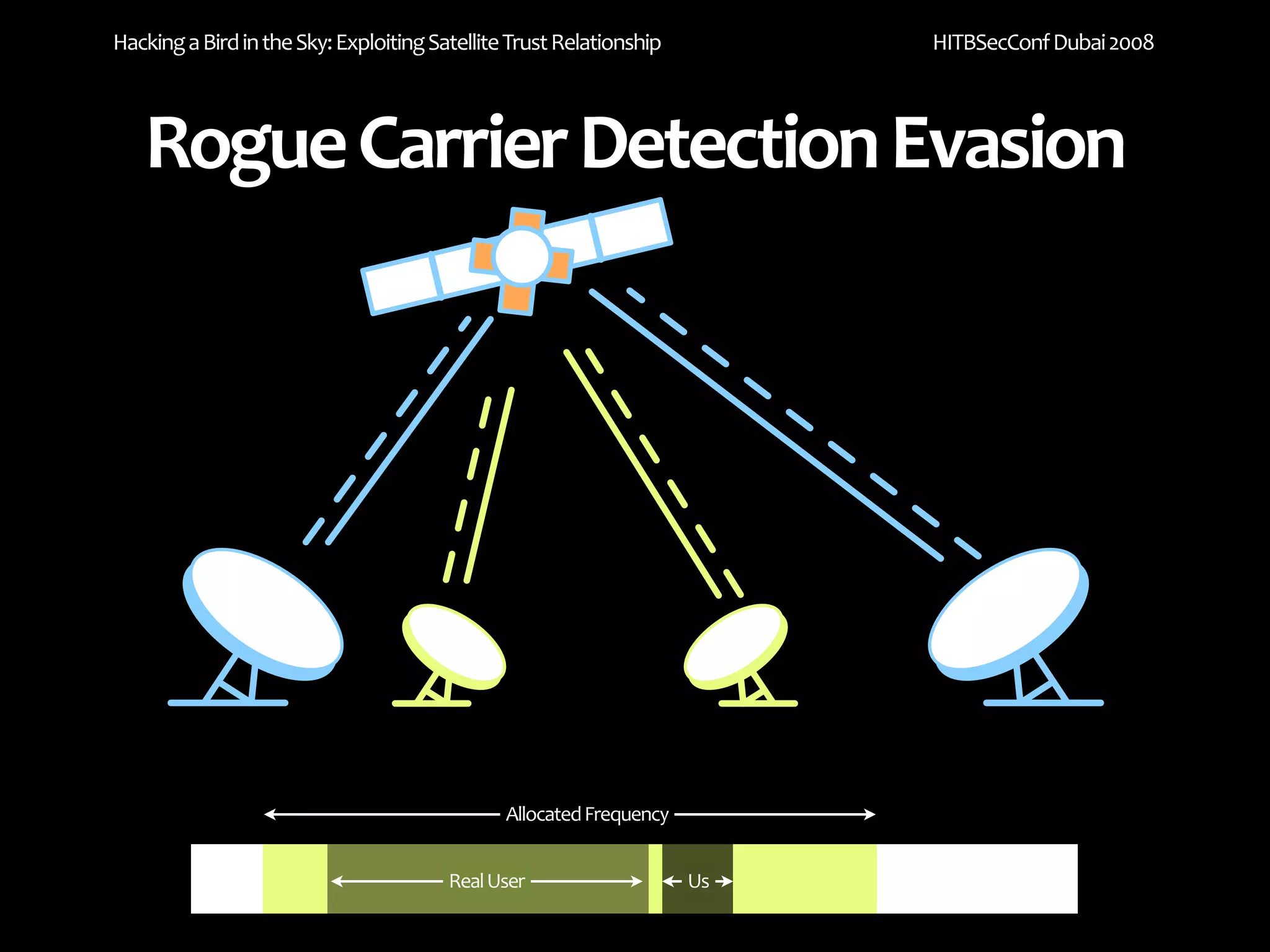
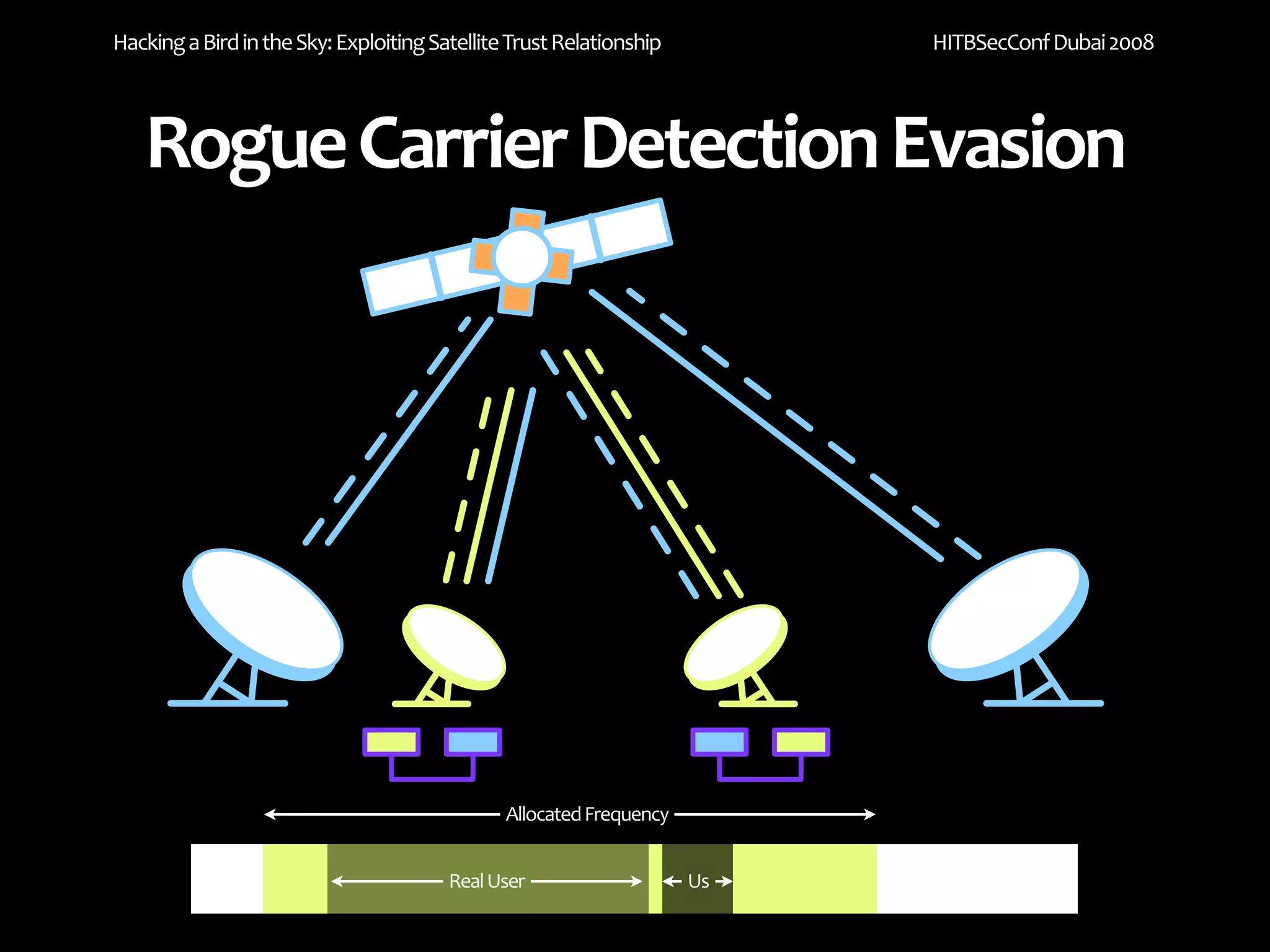
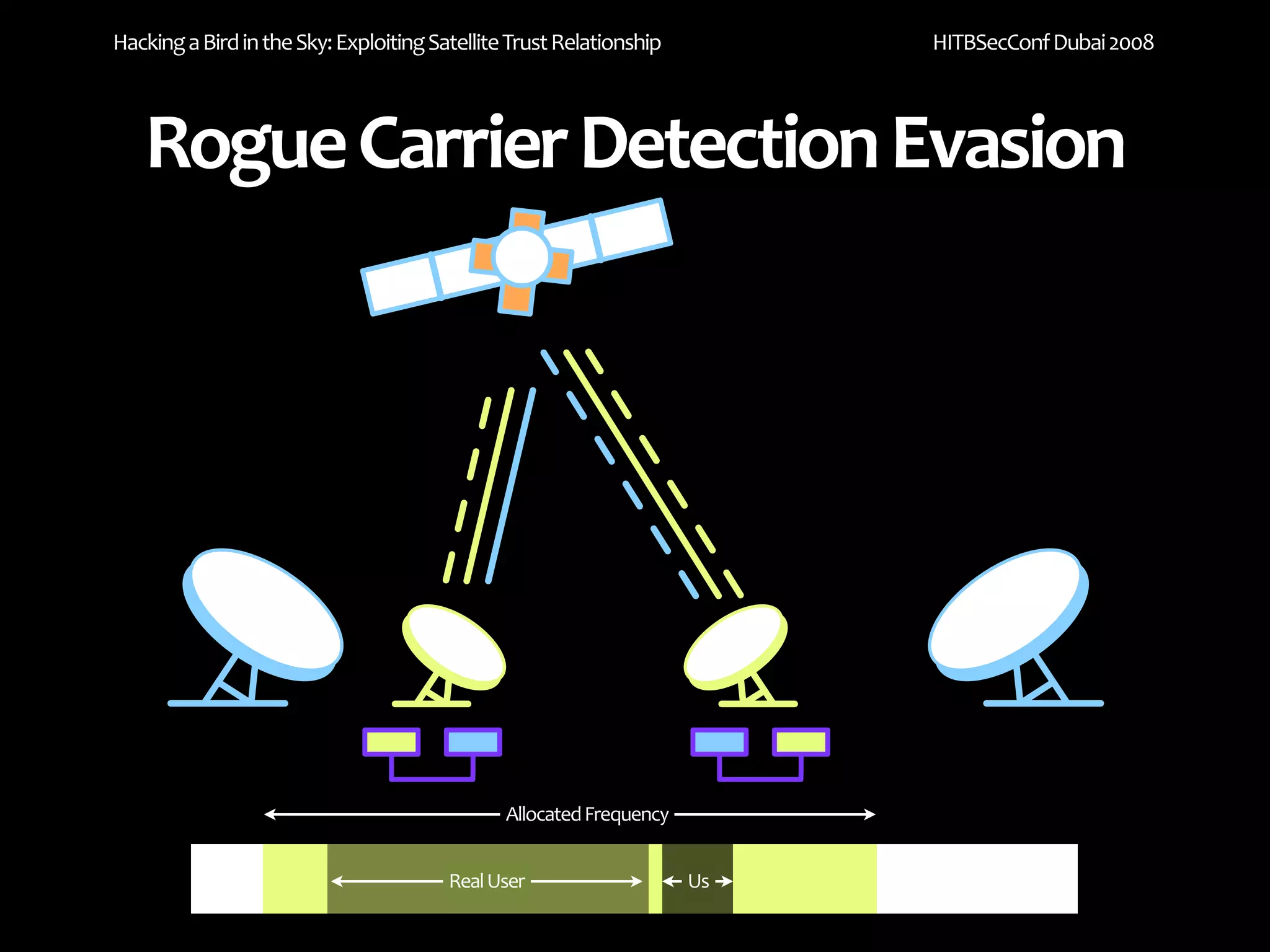
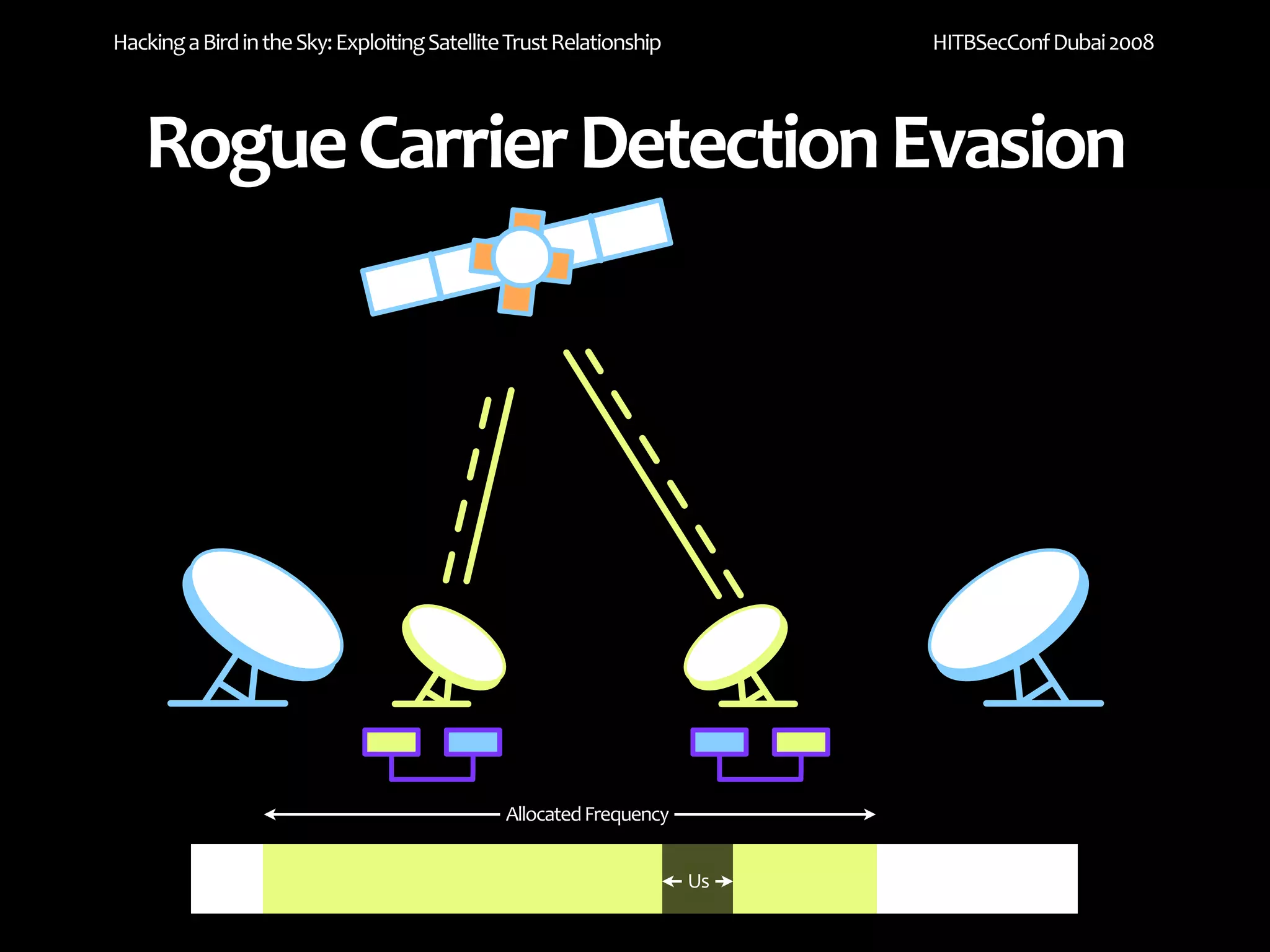
The document discusses exploiting trust relationships in satellite communication networks. It describes how an attacker could potentially "piggyback" on a satellite network by finding an unused frequency and transmitting data without authorization, akin to adding a "rogue carrier." The document notes challenges in detecting such rogue transmissions and suggests cooperation across satellite operators could help with detection. It concludes by noting previous work compromising the data link layer and suggests combined attacks on the data link and network layers could allow more serious exploitation of satellite systems.