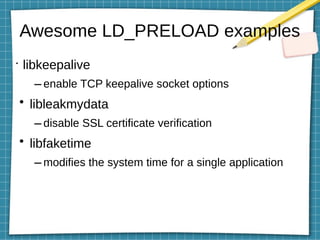
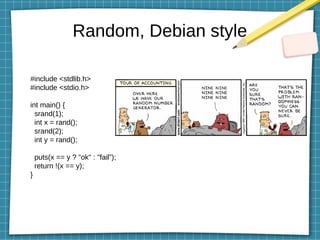
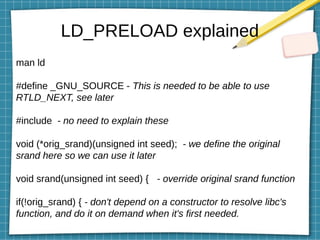
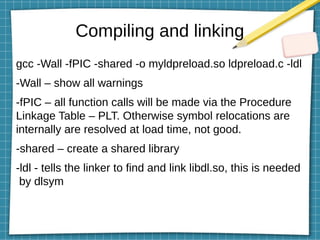
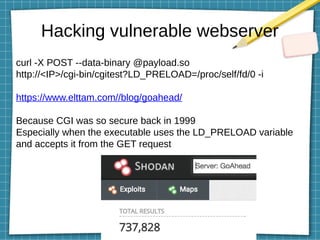
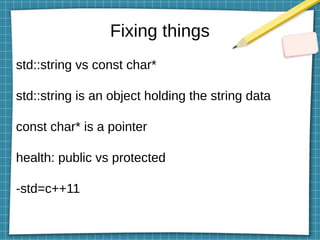
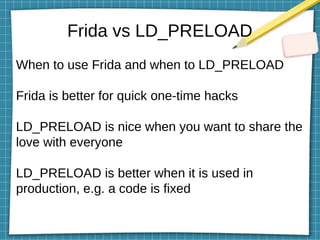
This document discusses using LD_PRELOAD and DYLD_INSERT_LIBRARIES to inject code into processes via shared object preloading on Linux and macOS respectively. It provides examples of modifying system calls and injecting code into applications at runtime. It also explains how to compile shared objects for injection and discusses some techniques for preventing injection, such as using setuid/setgid bits.












![Basic macOS syntax
#include <stdio.h>
#include <syslog.h>
__attribute__((constructor))
static void customConstructor(int argc, const char **argv)
{
printf("Hello from dylib!n");
syslog(LOG_ERR, "Dylib injection successful in %sn", argv[0]);
}
gcc -dynamiclib inject.c -o inject.dylib
DYLD_INSERT_LIBRARIES=inject.dylib ./test](https://image.slidesharecdn.com/hackersulildpreload-200325145255/85/Hackersuli-Linux-game-hacking-with-LD_PRELOAD-21-320.jpg)



