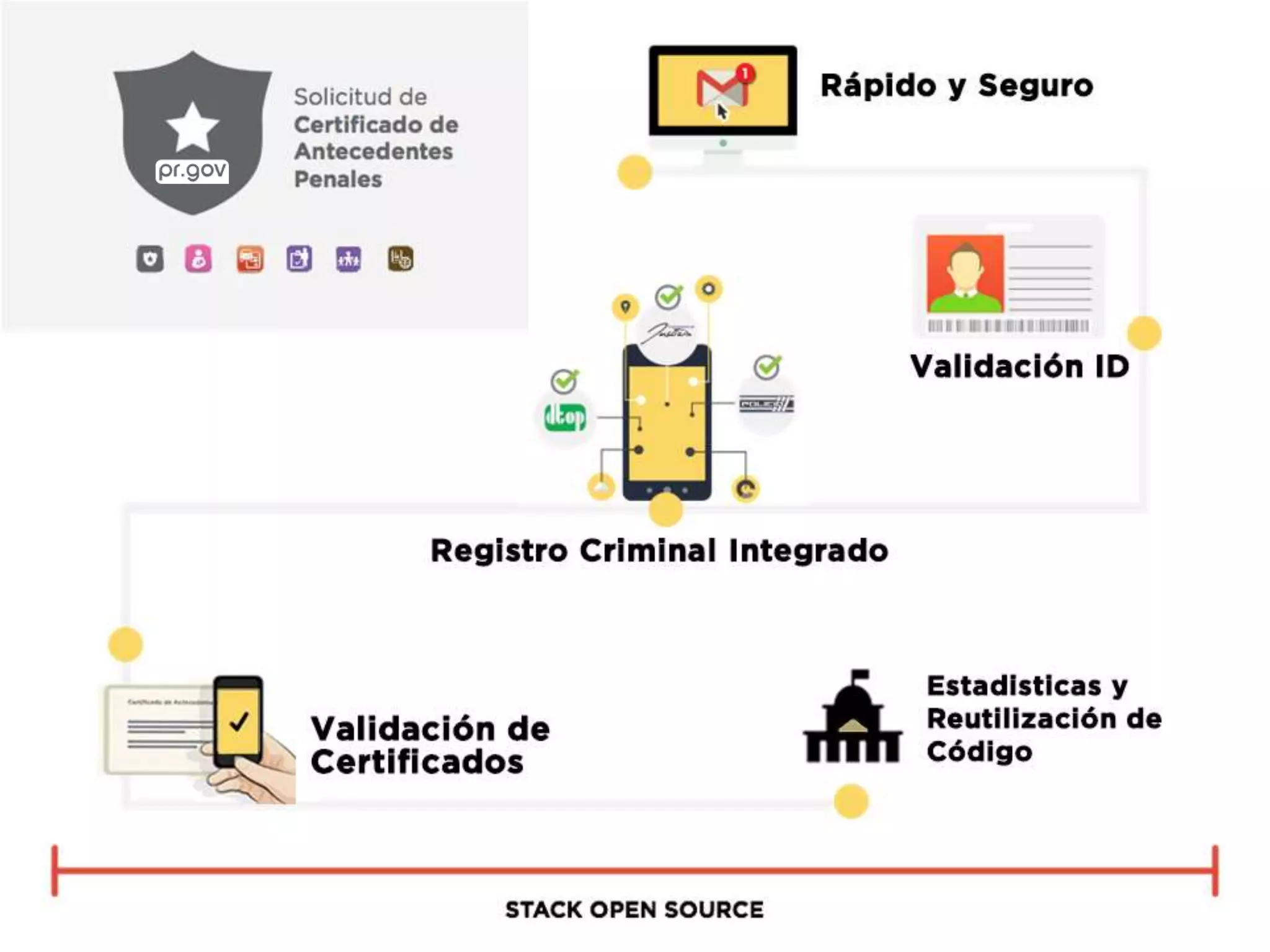
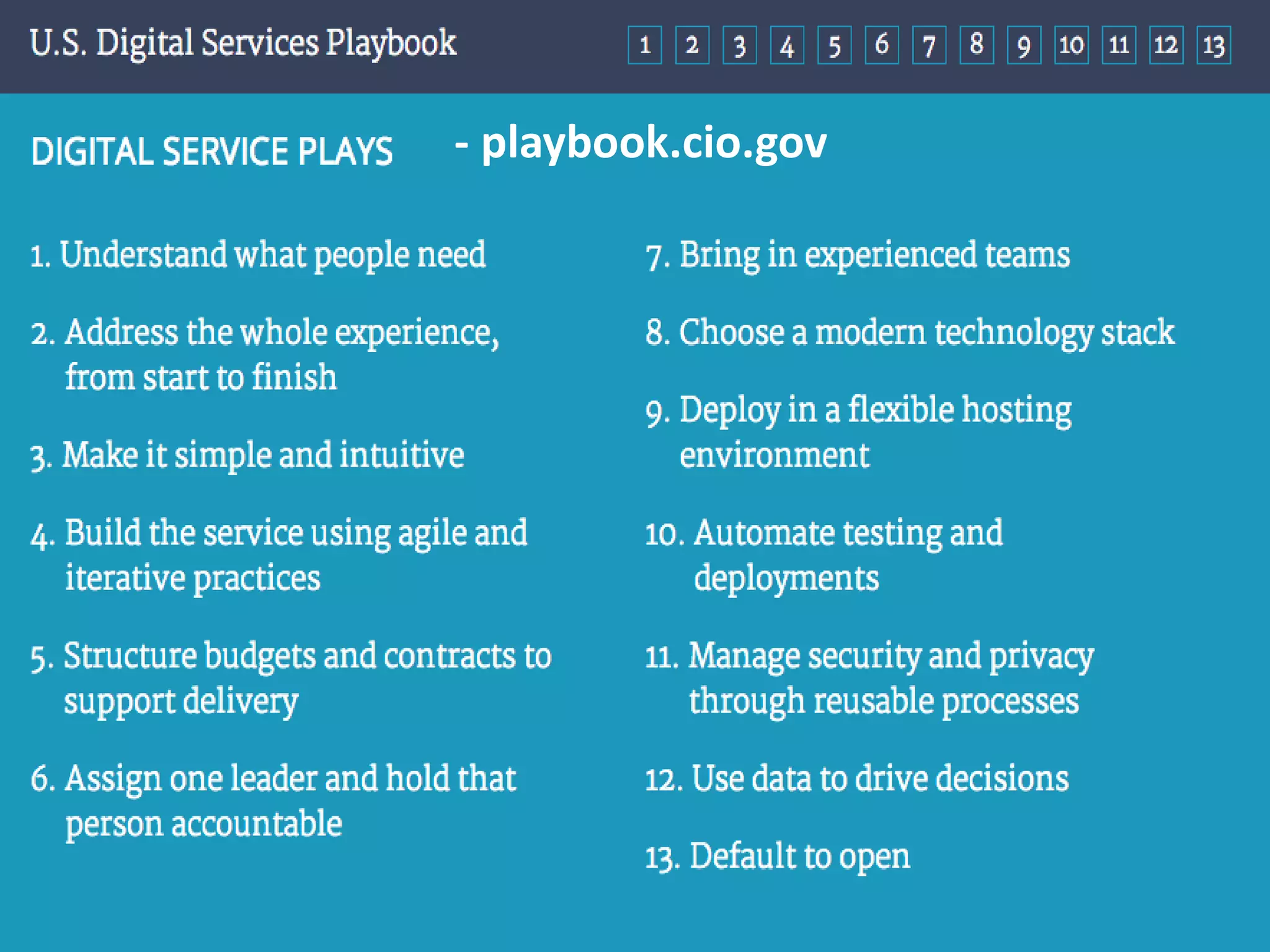
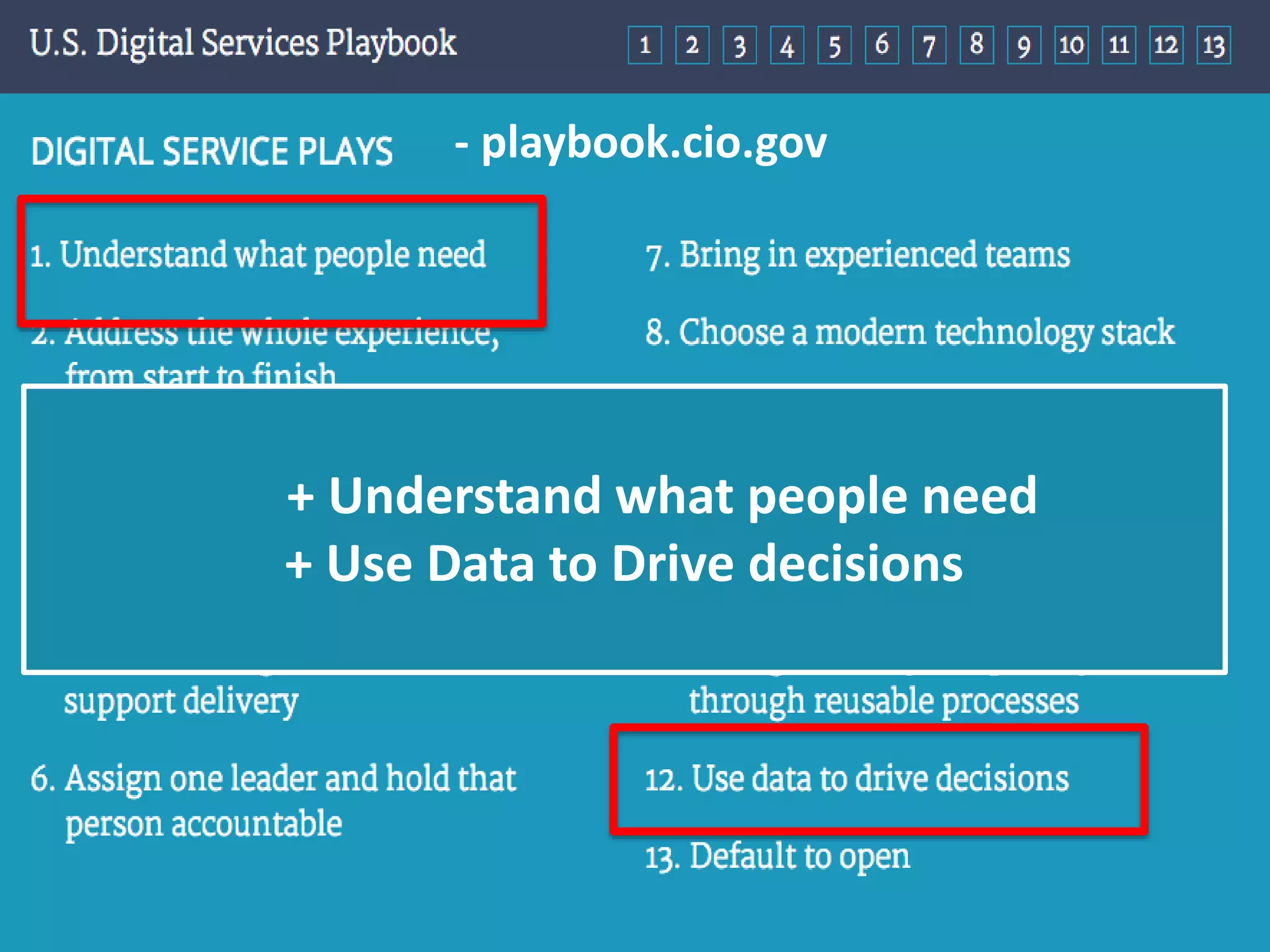
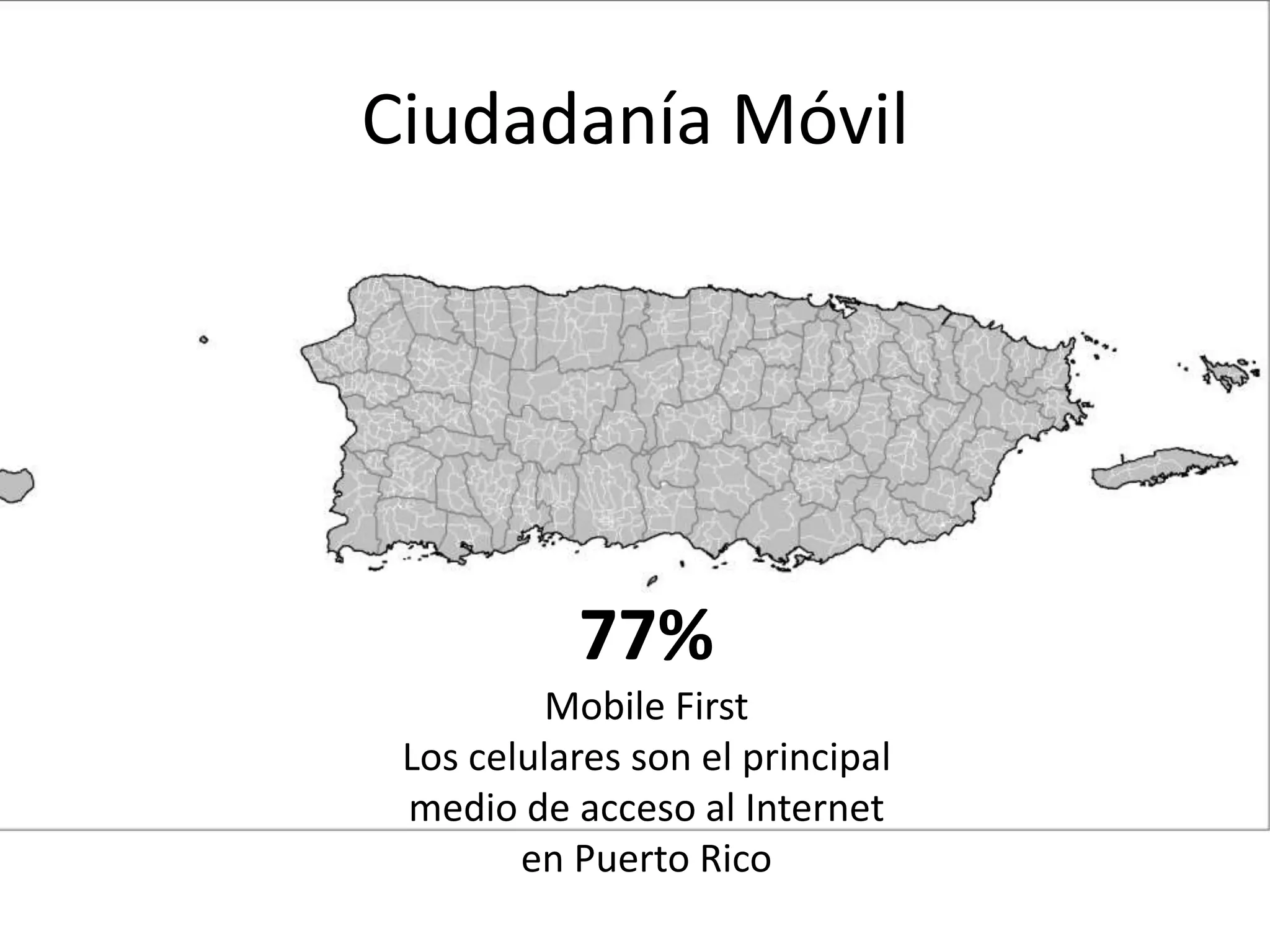
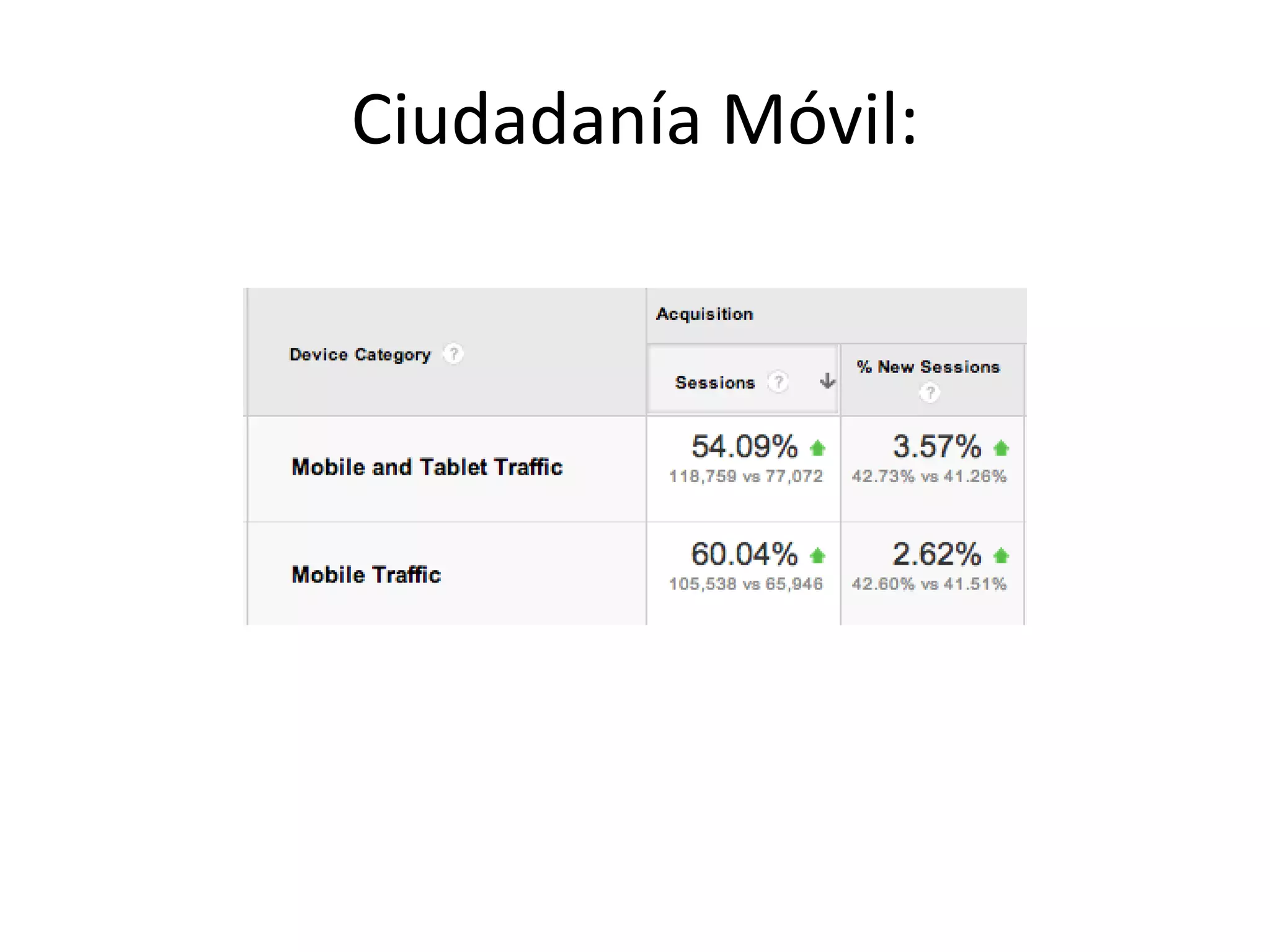
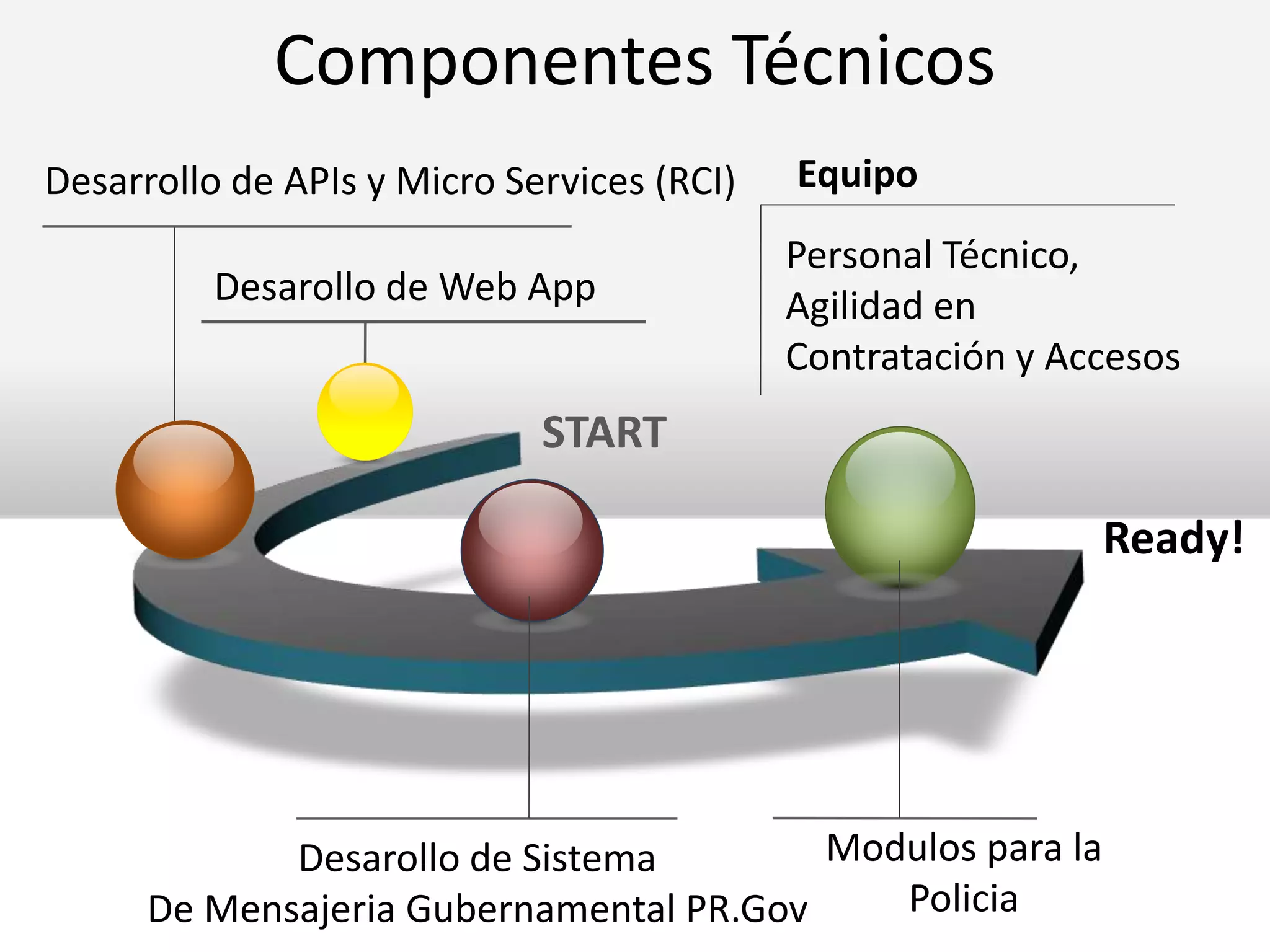
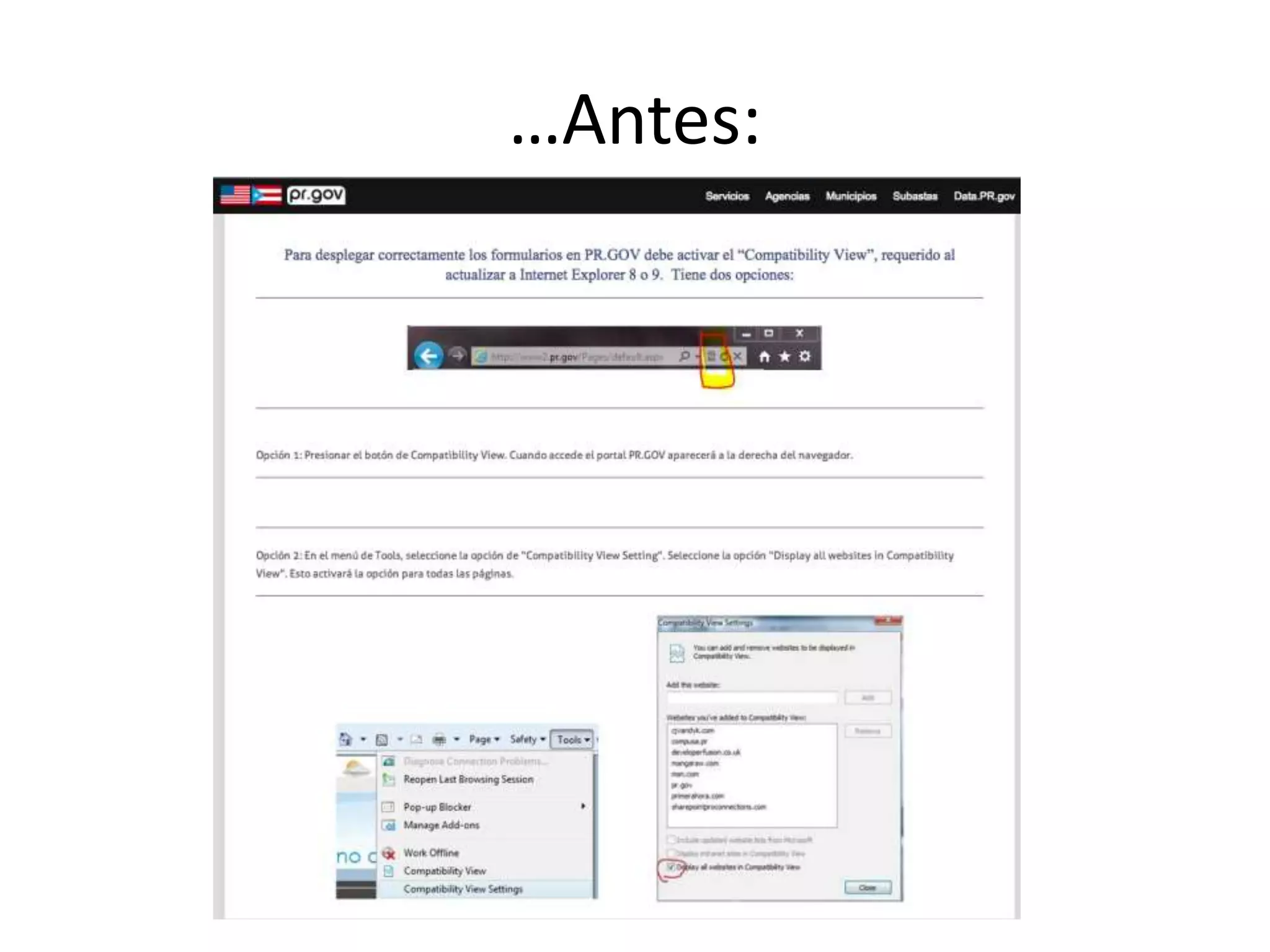
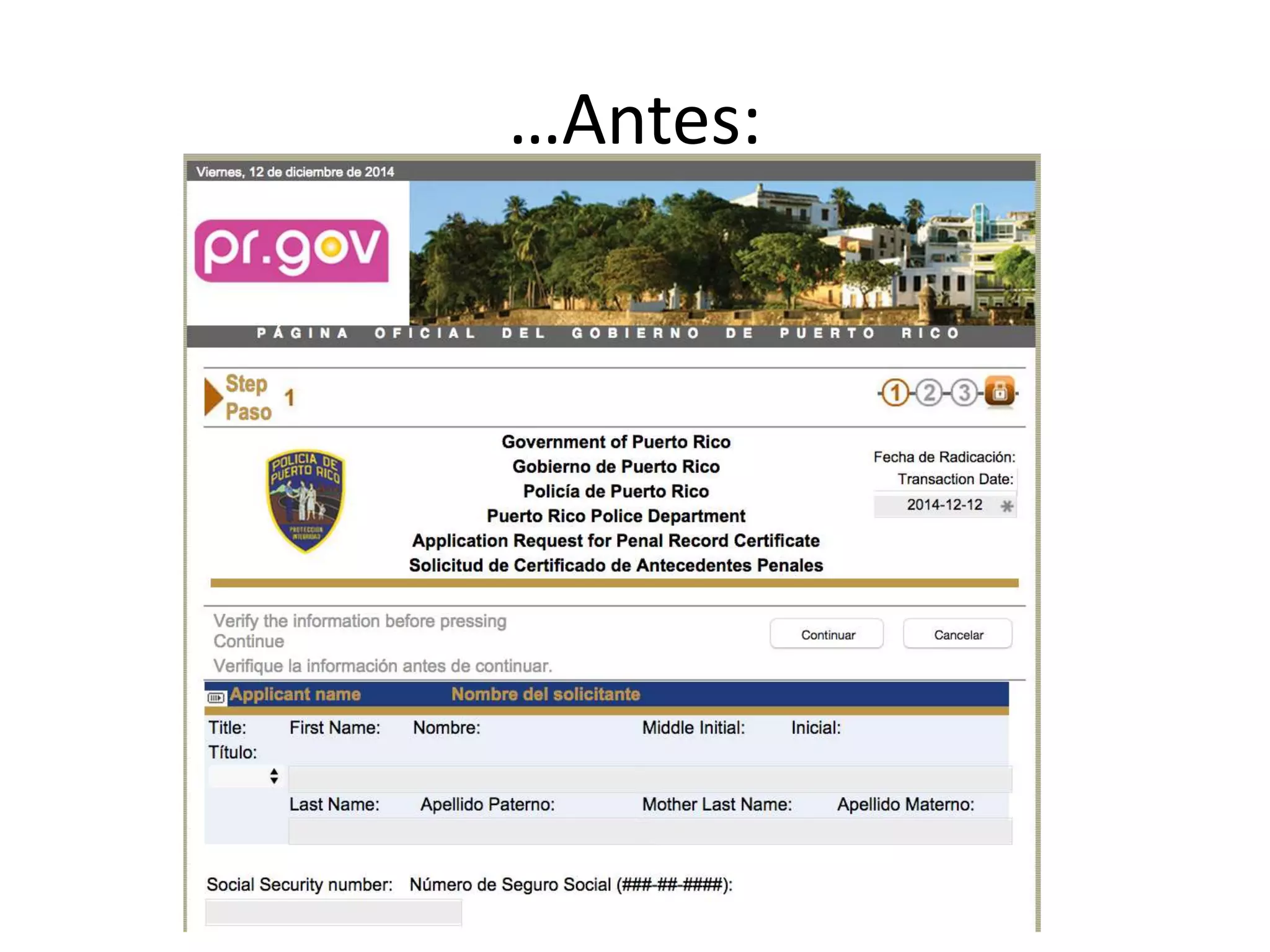
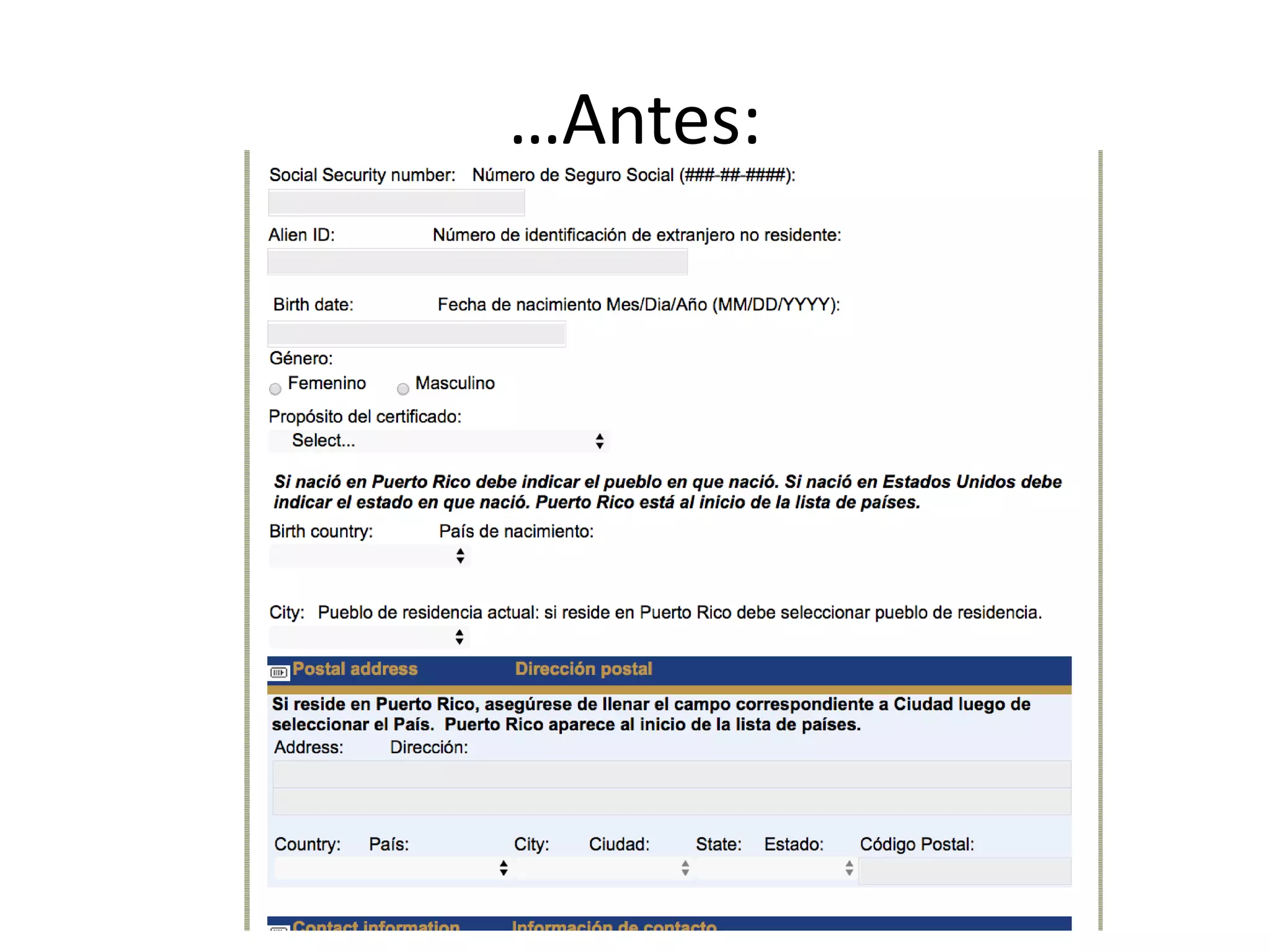
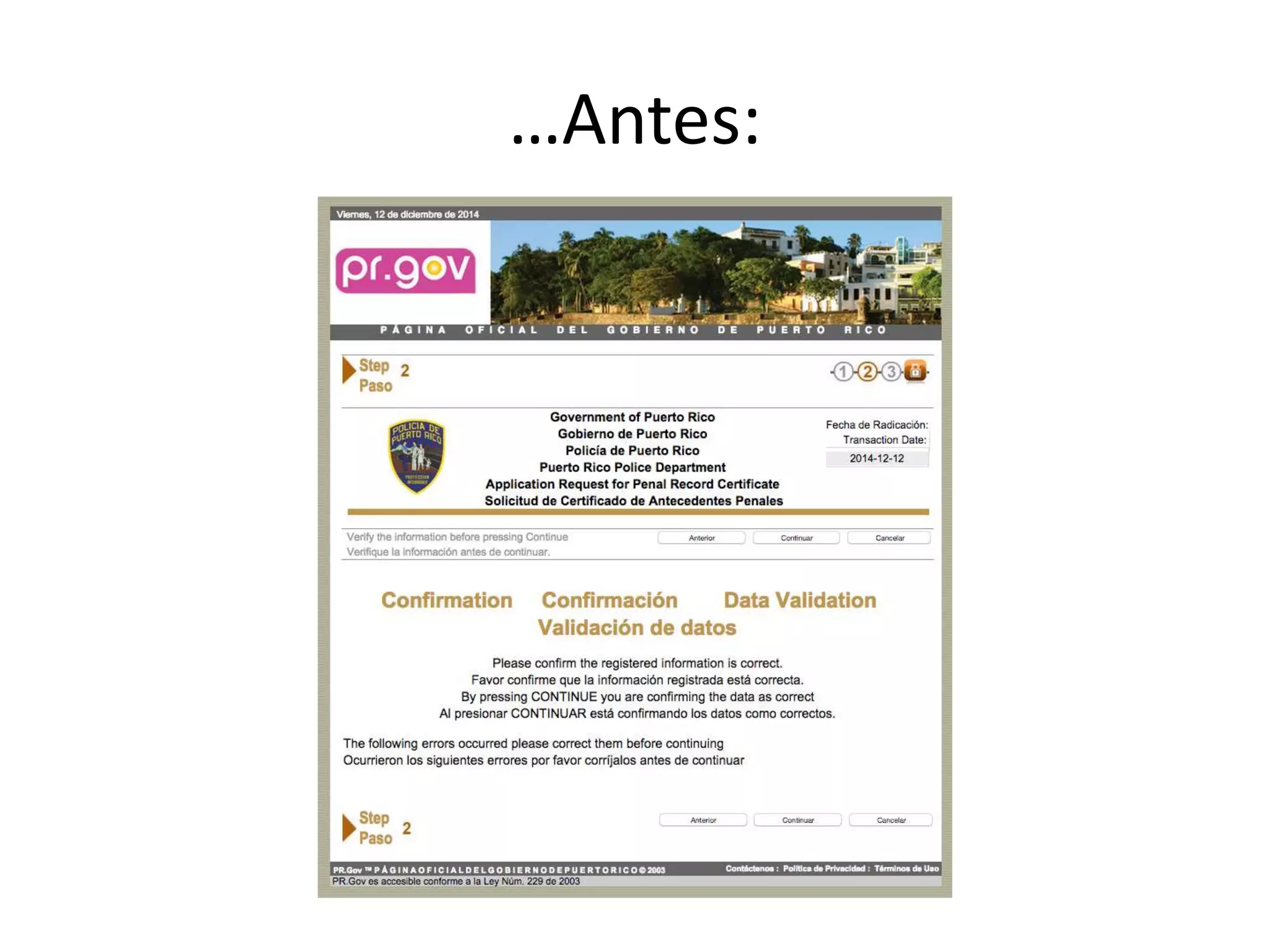
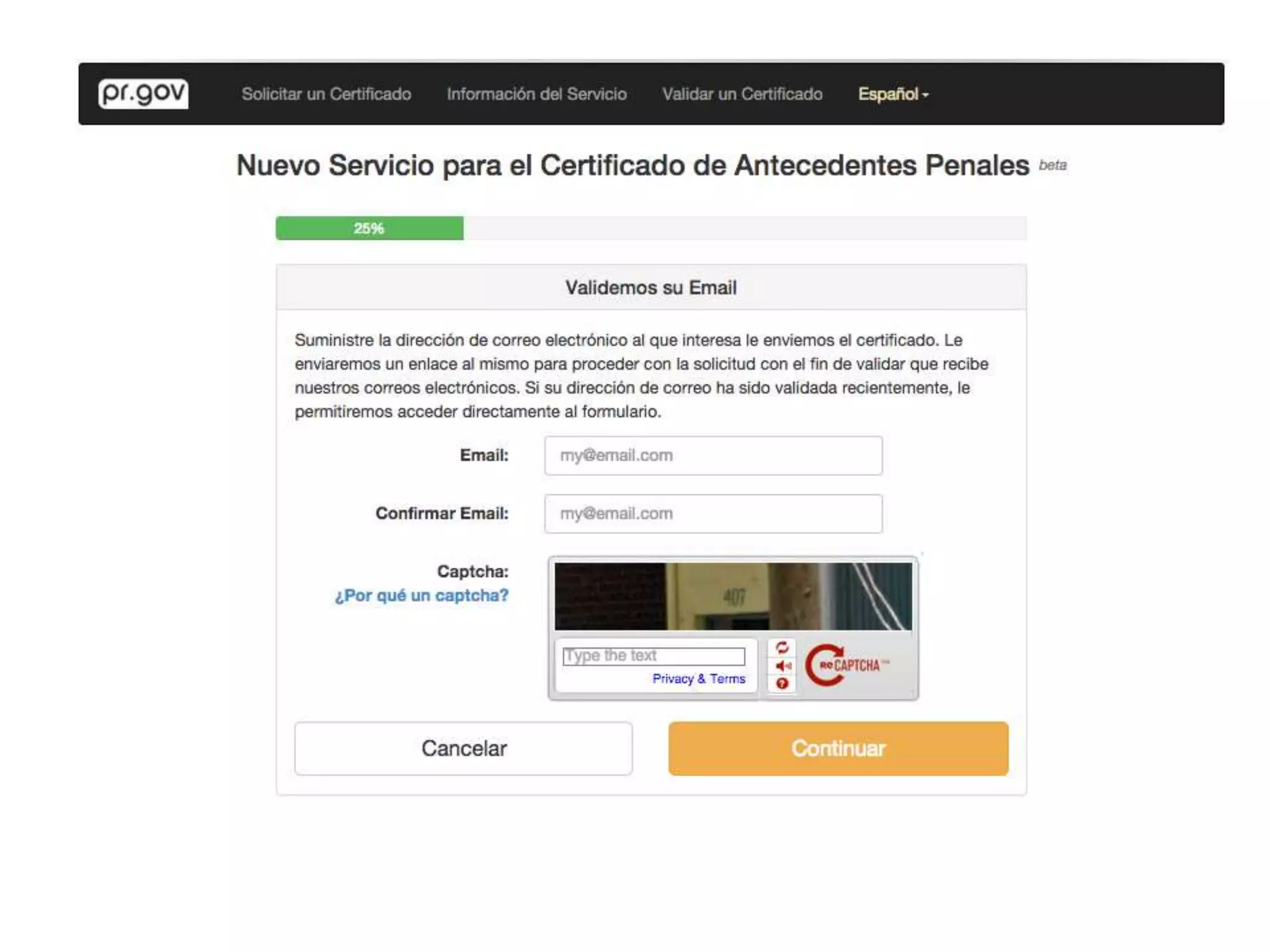
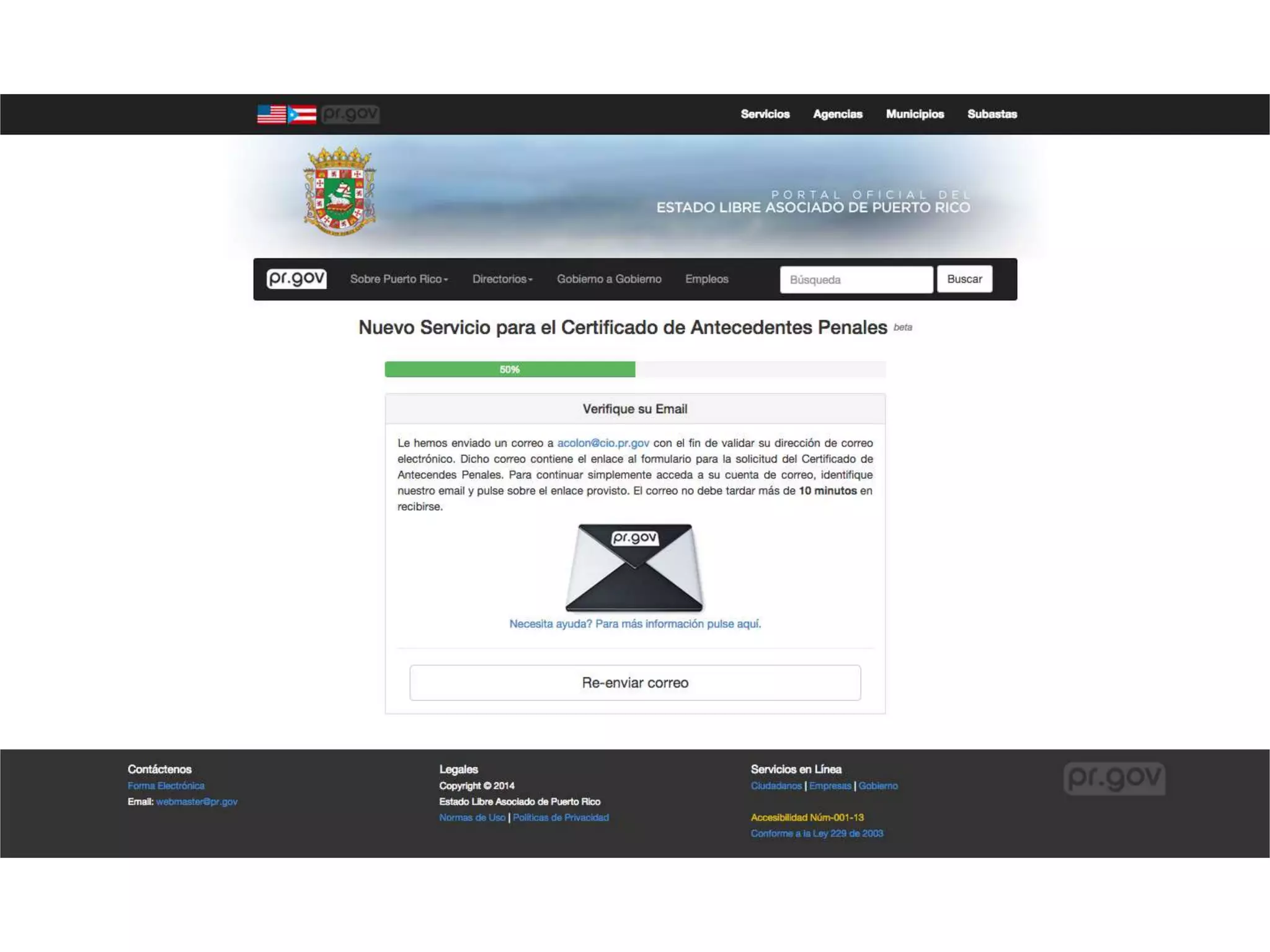
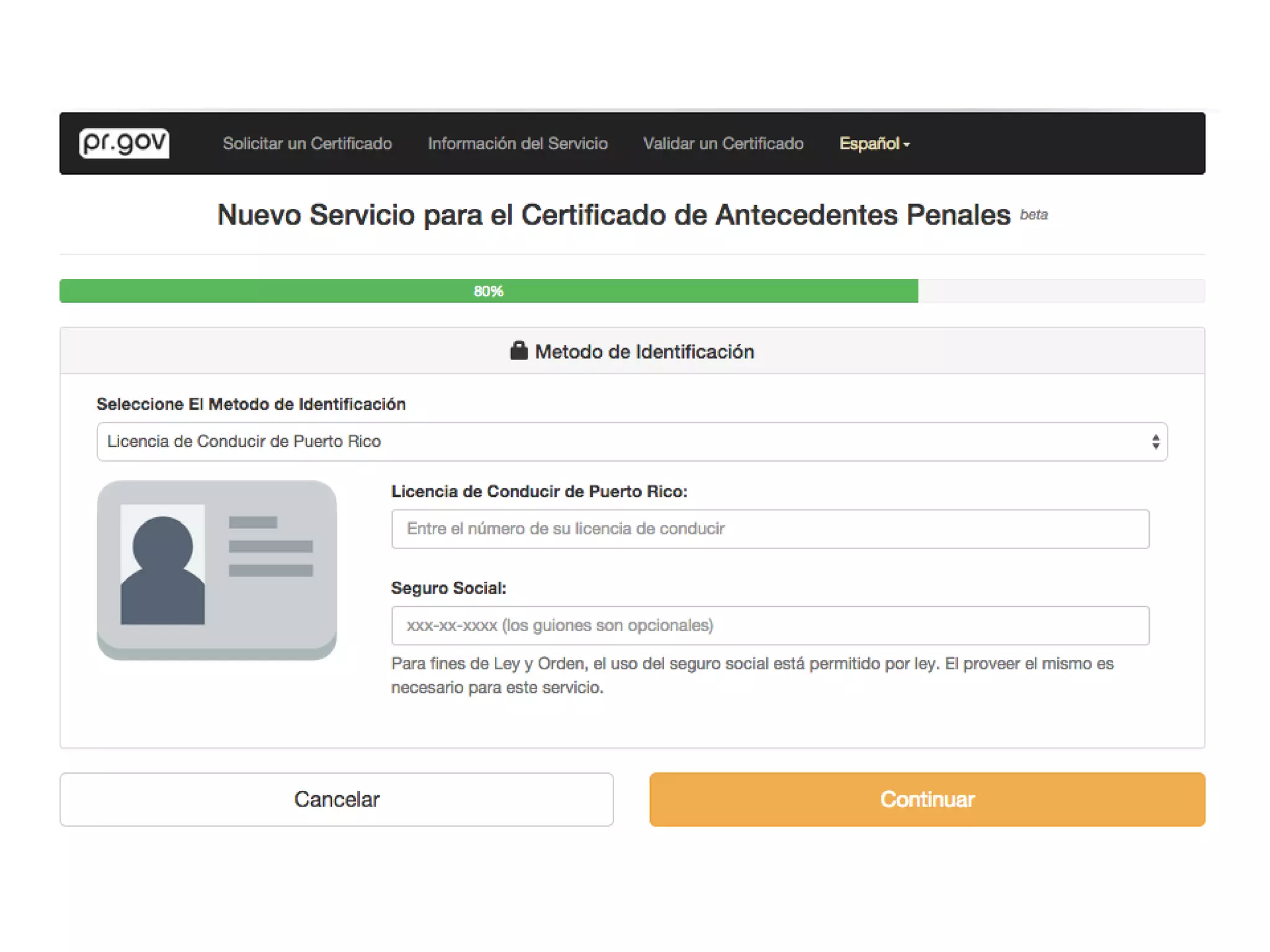
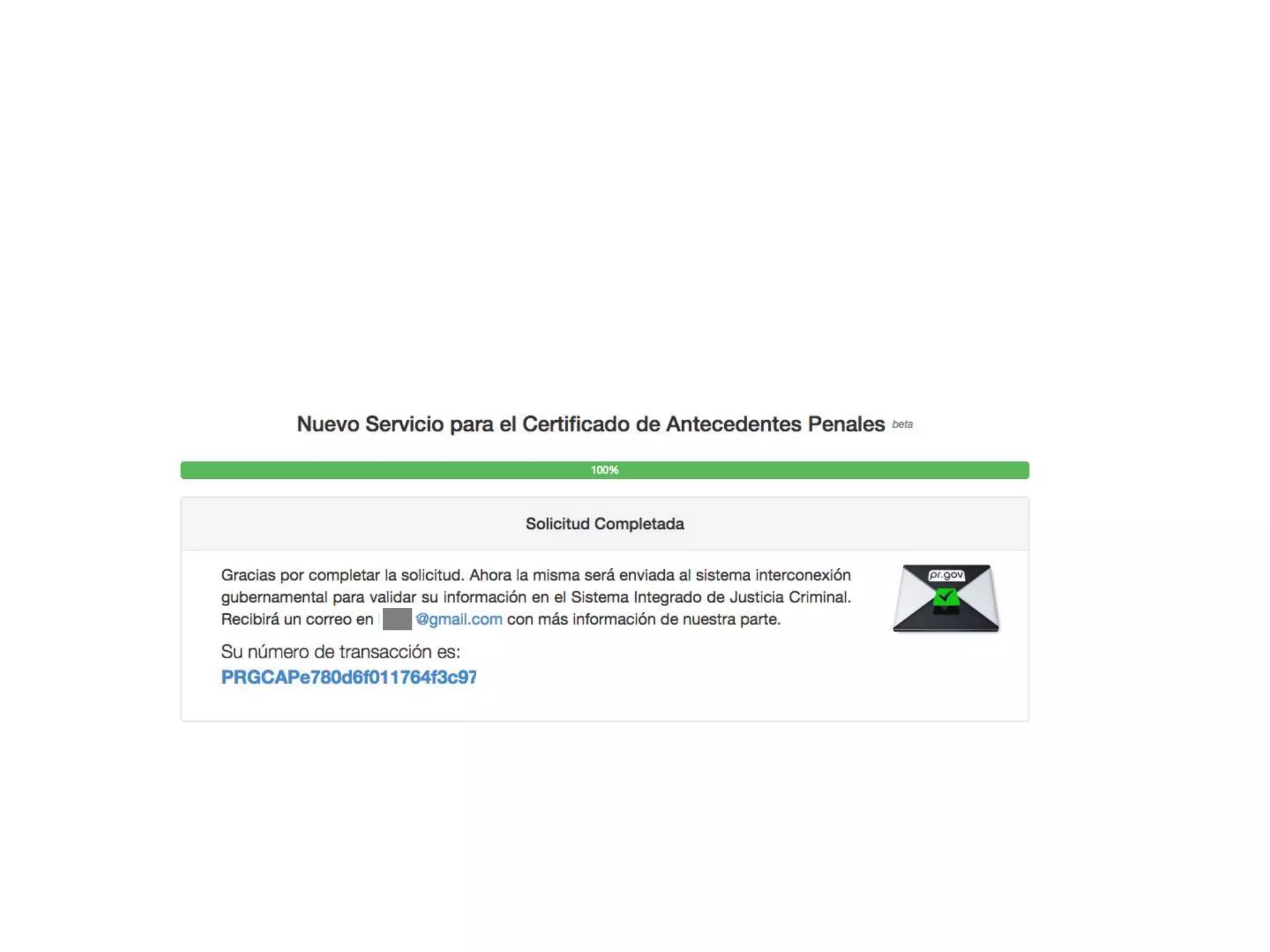
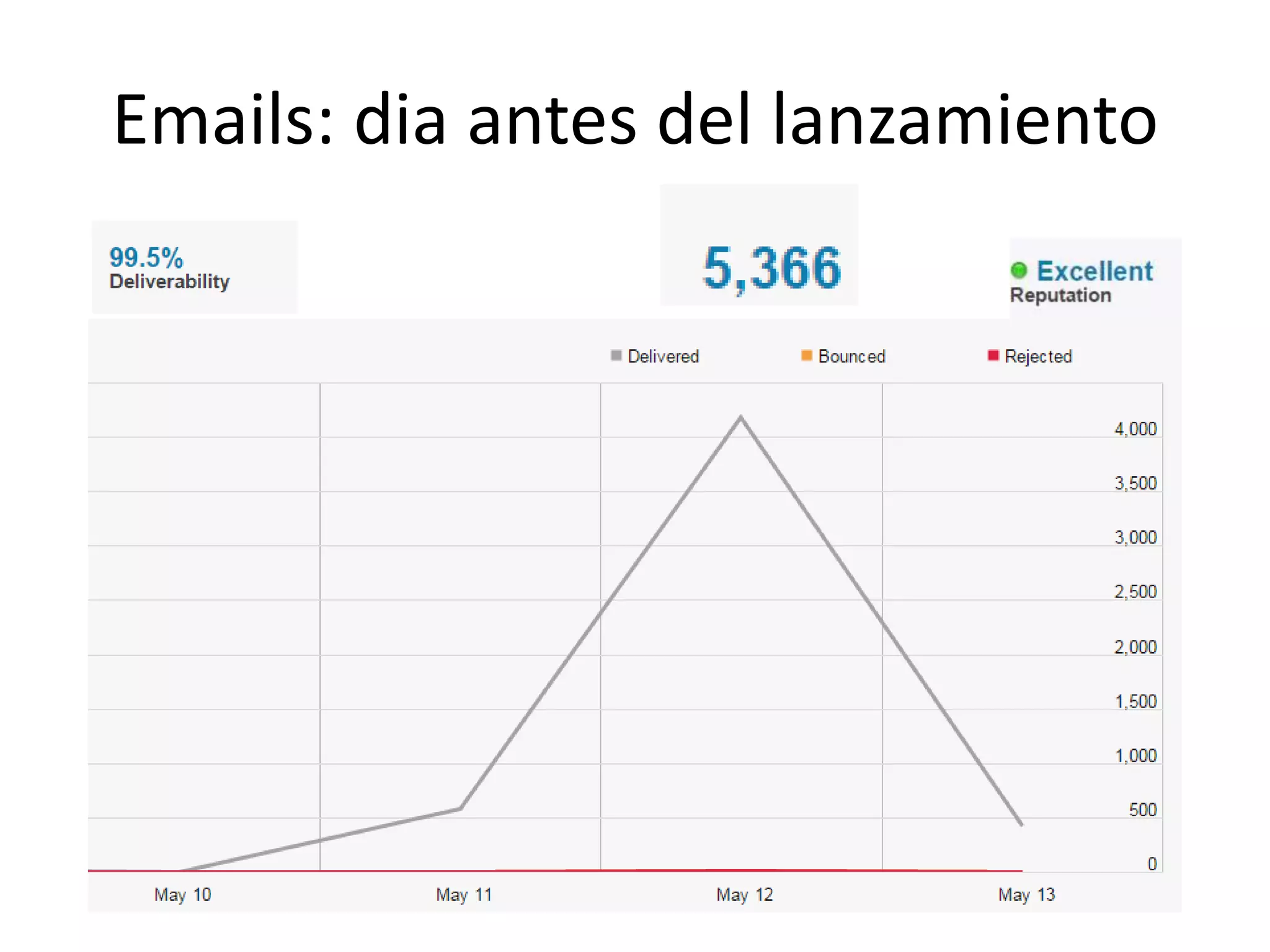
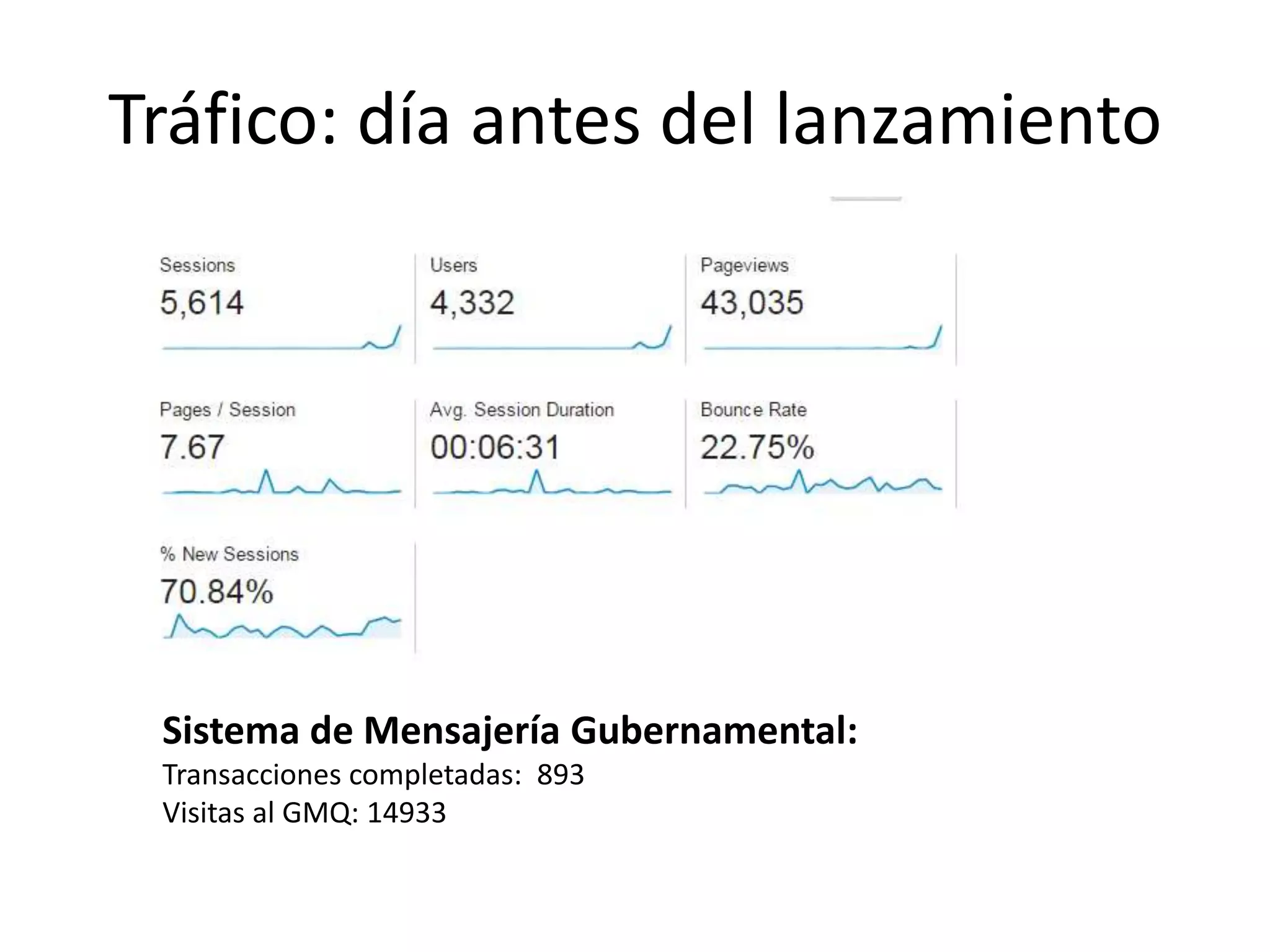
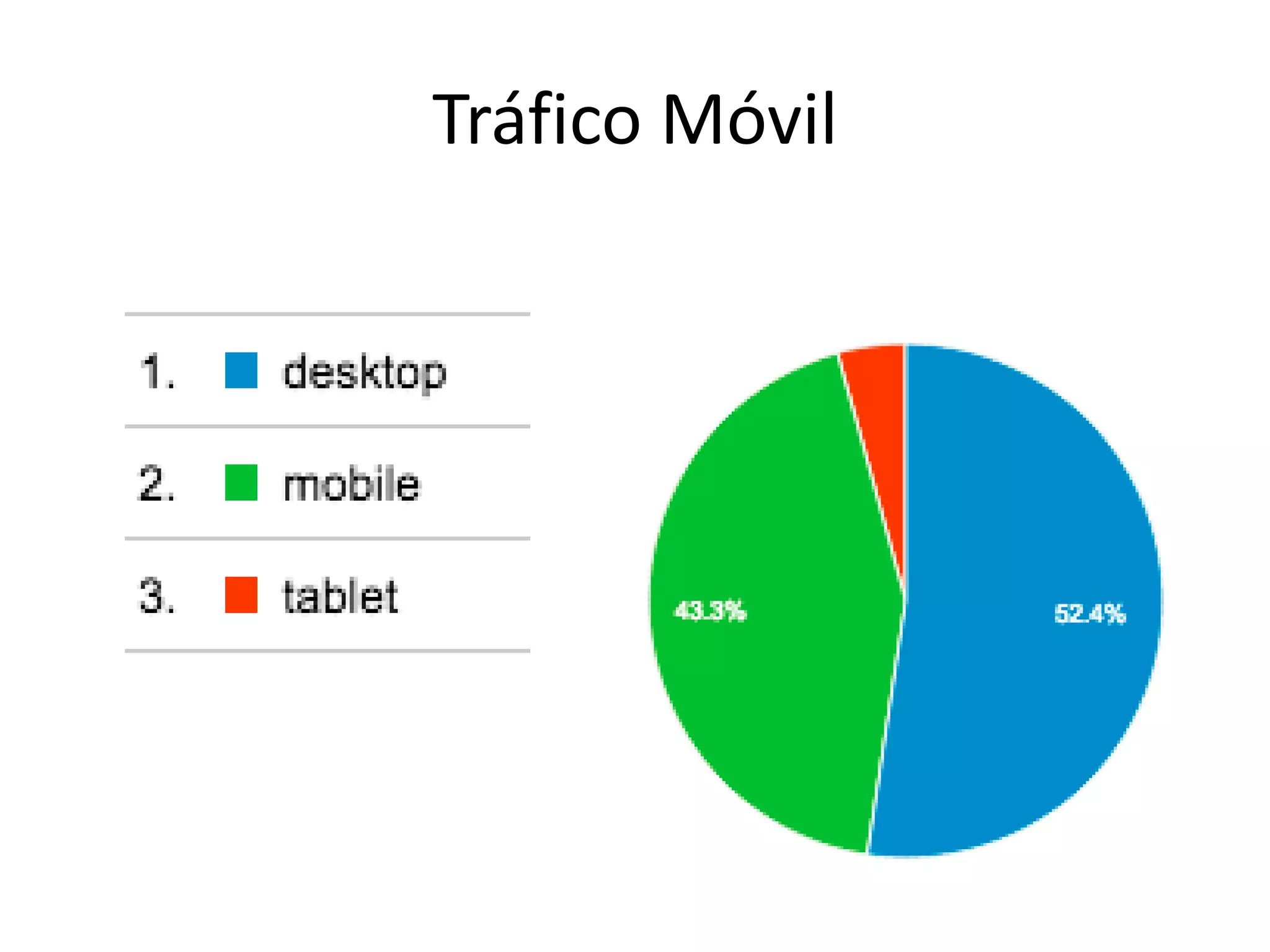
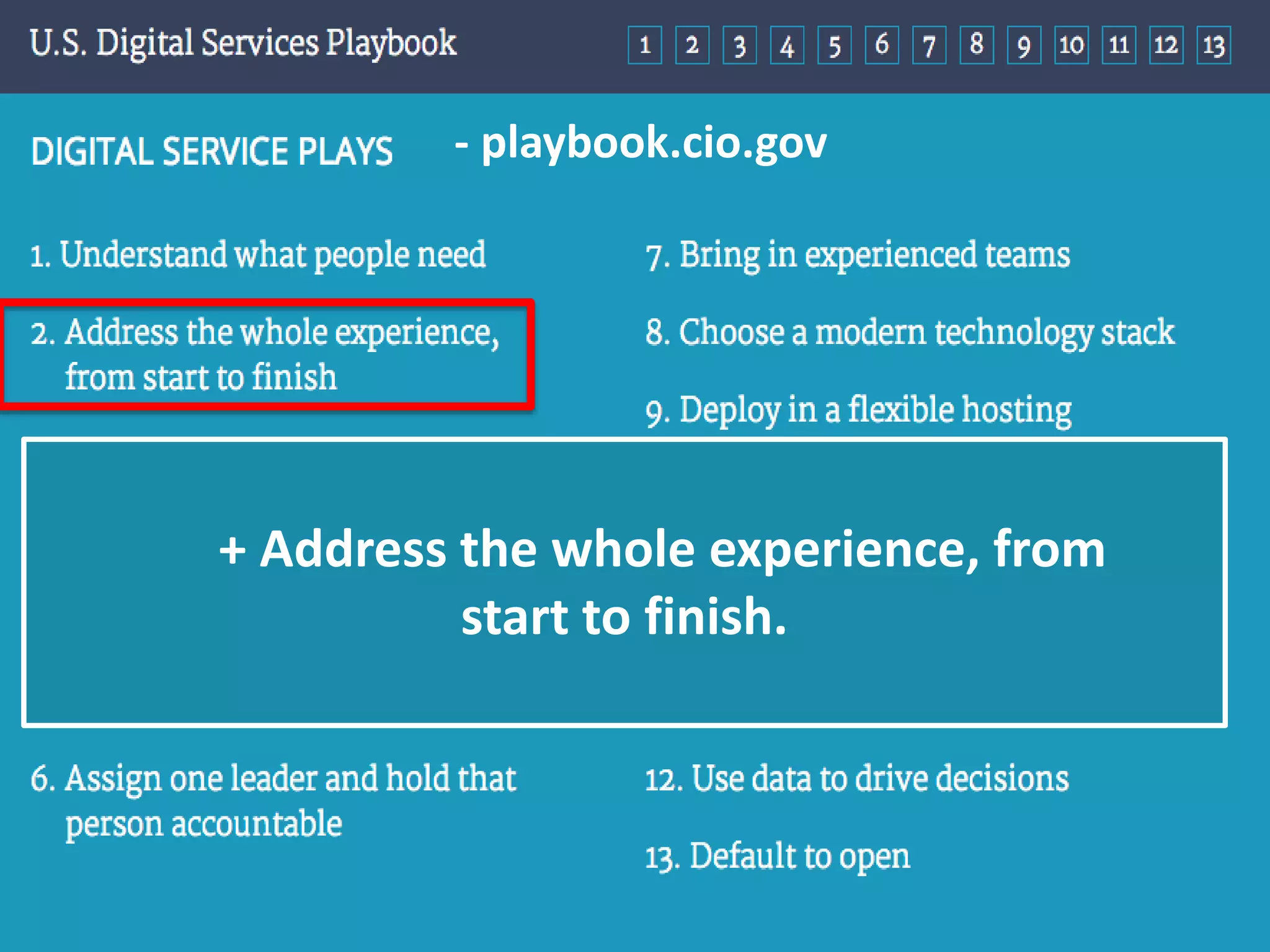
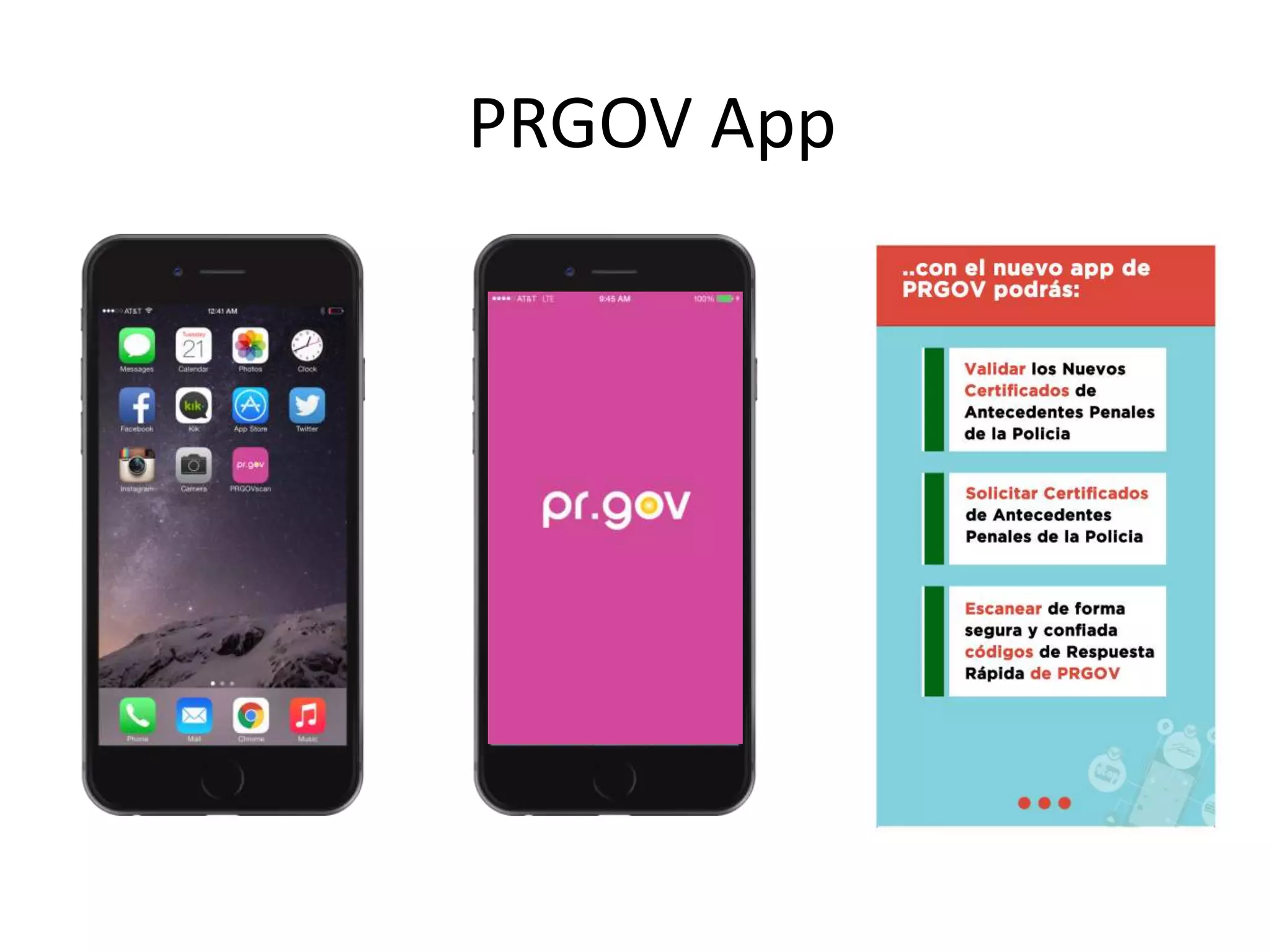
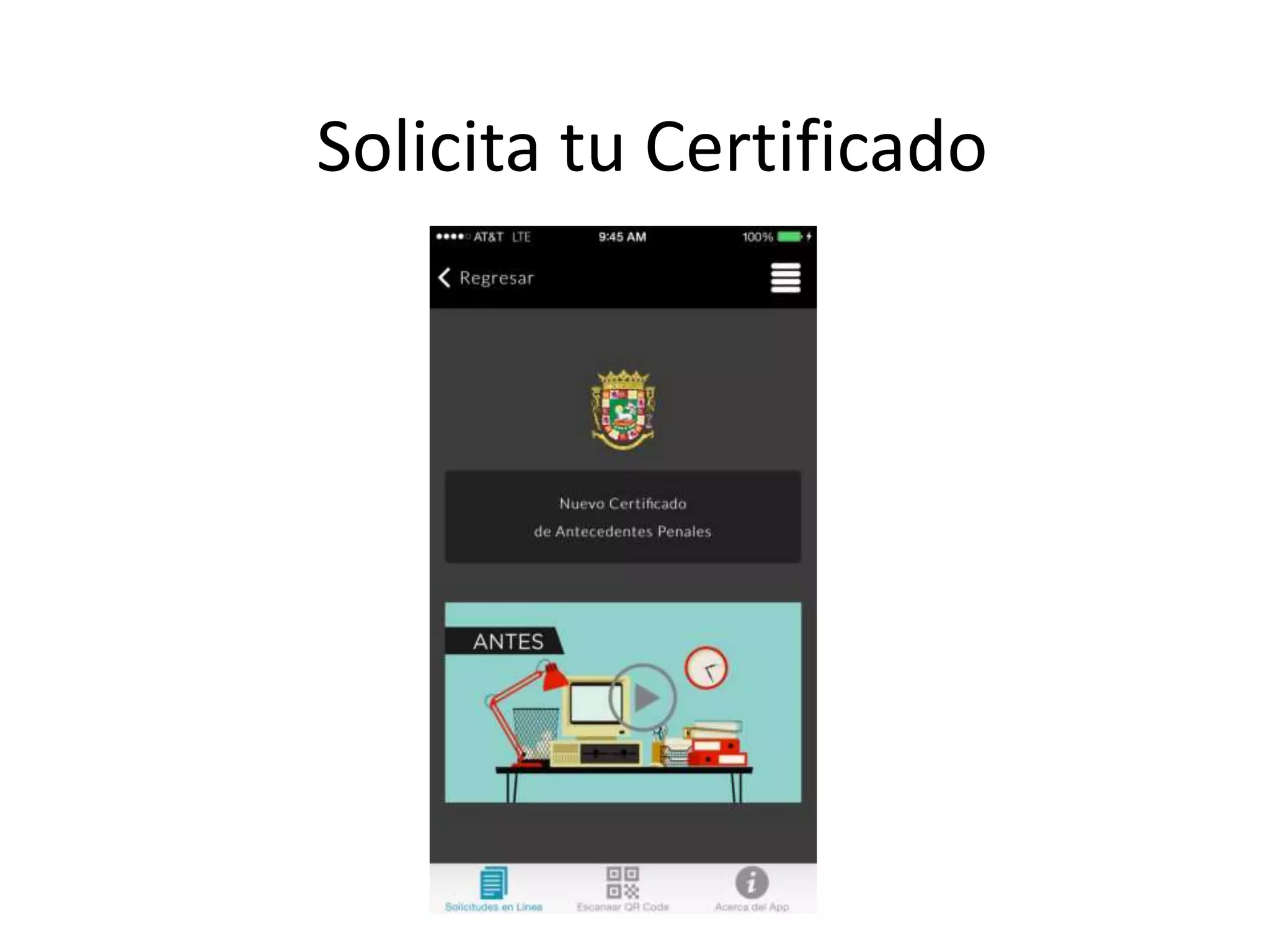
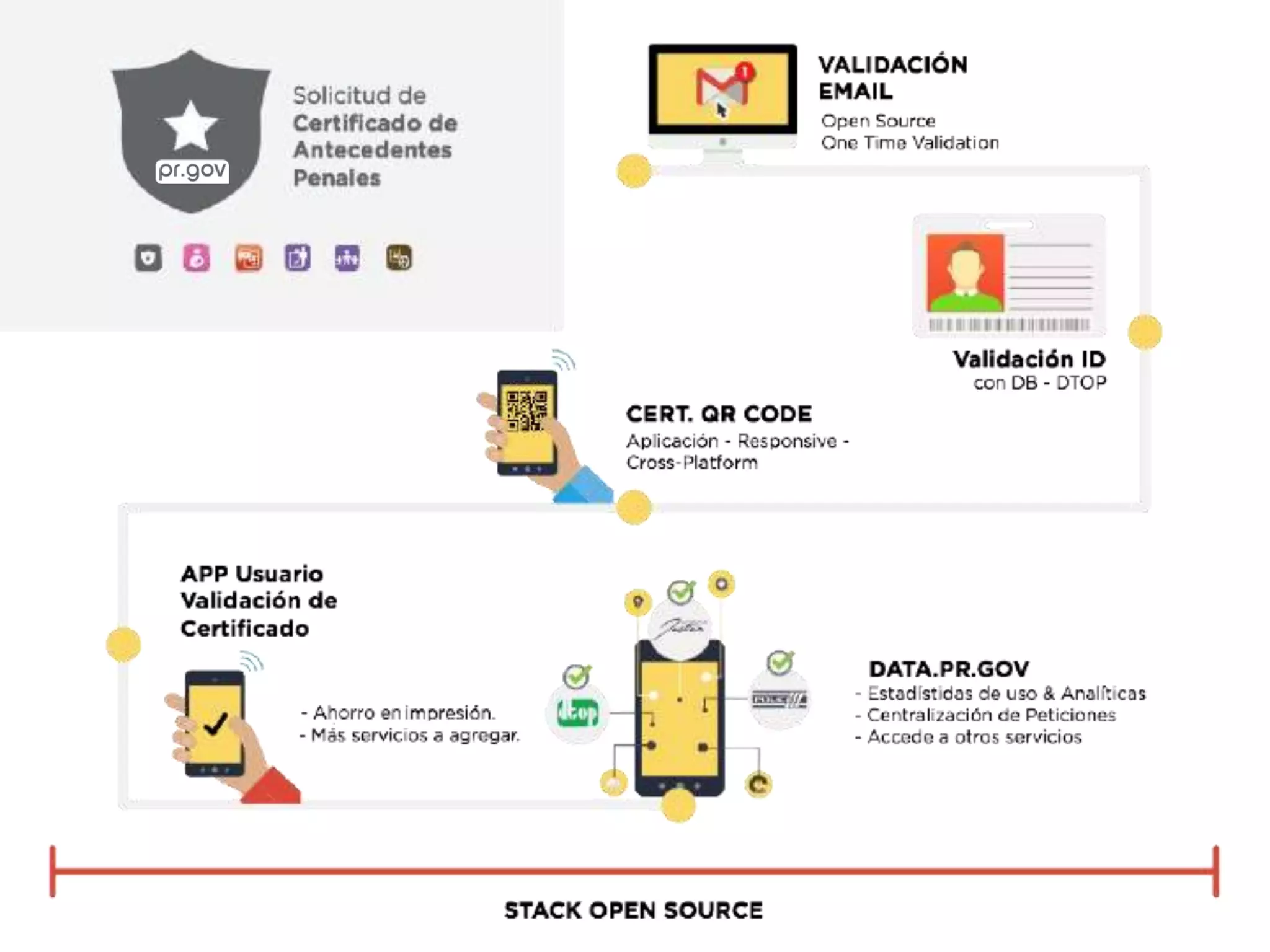
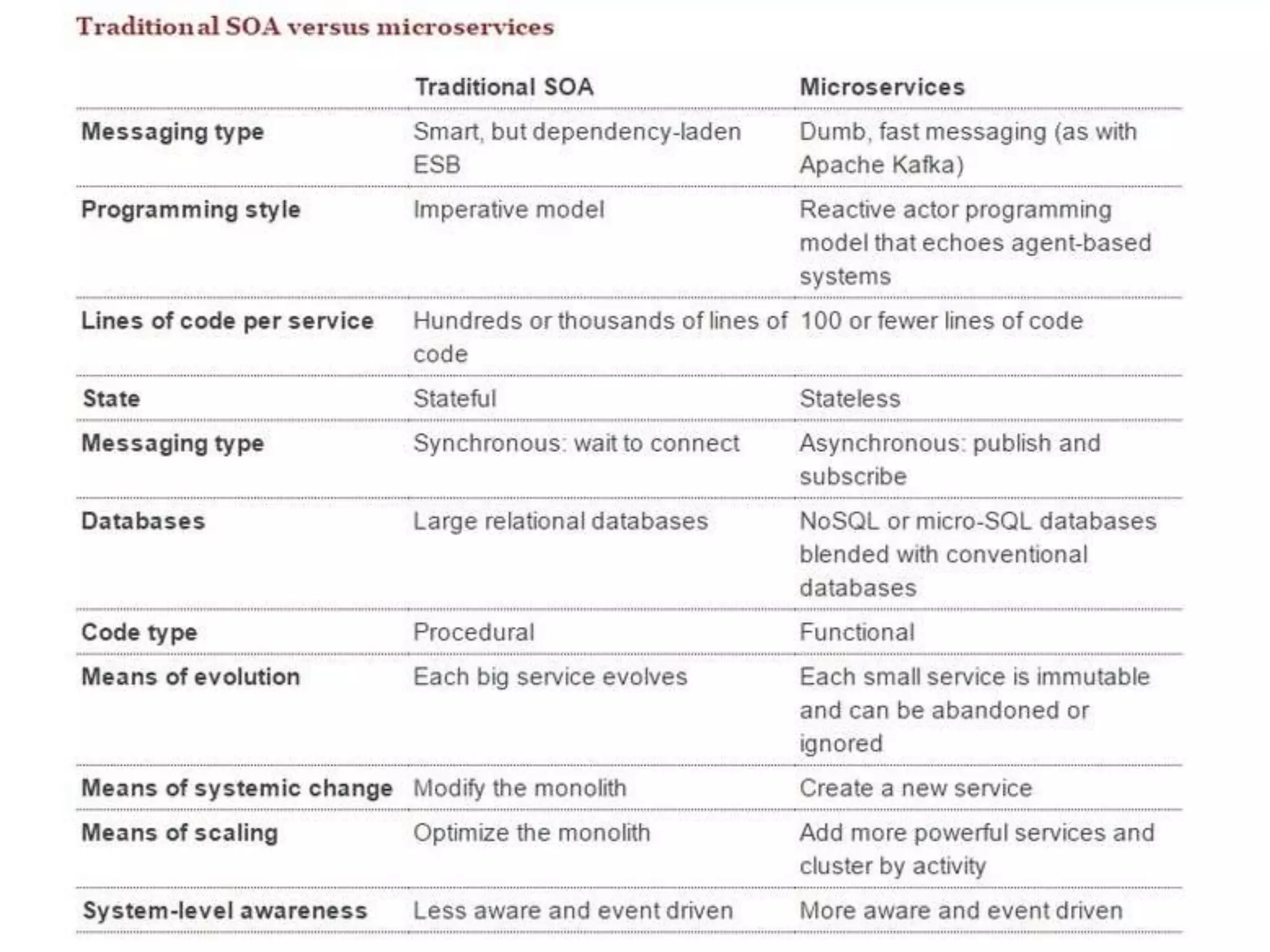
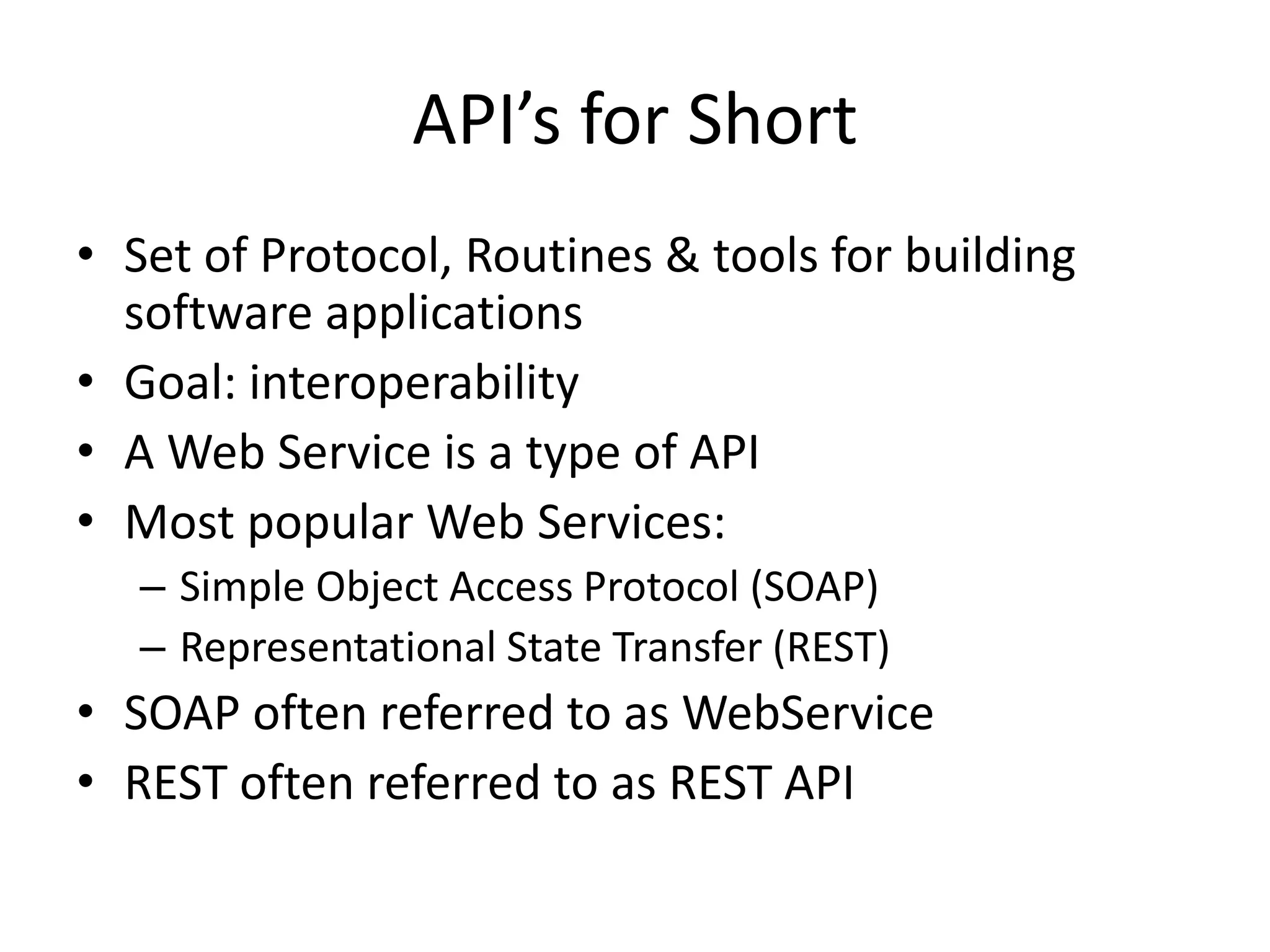
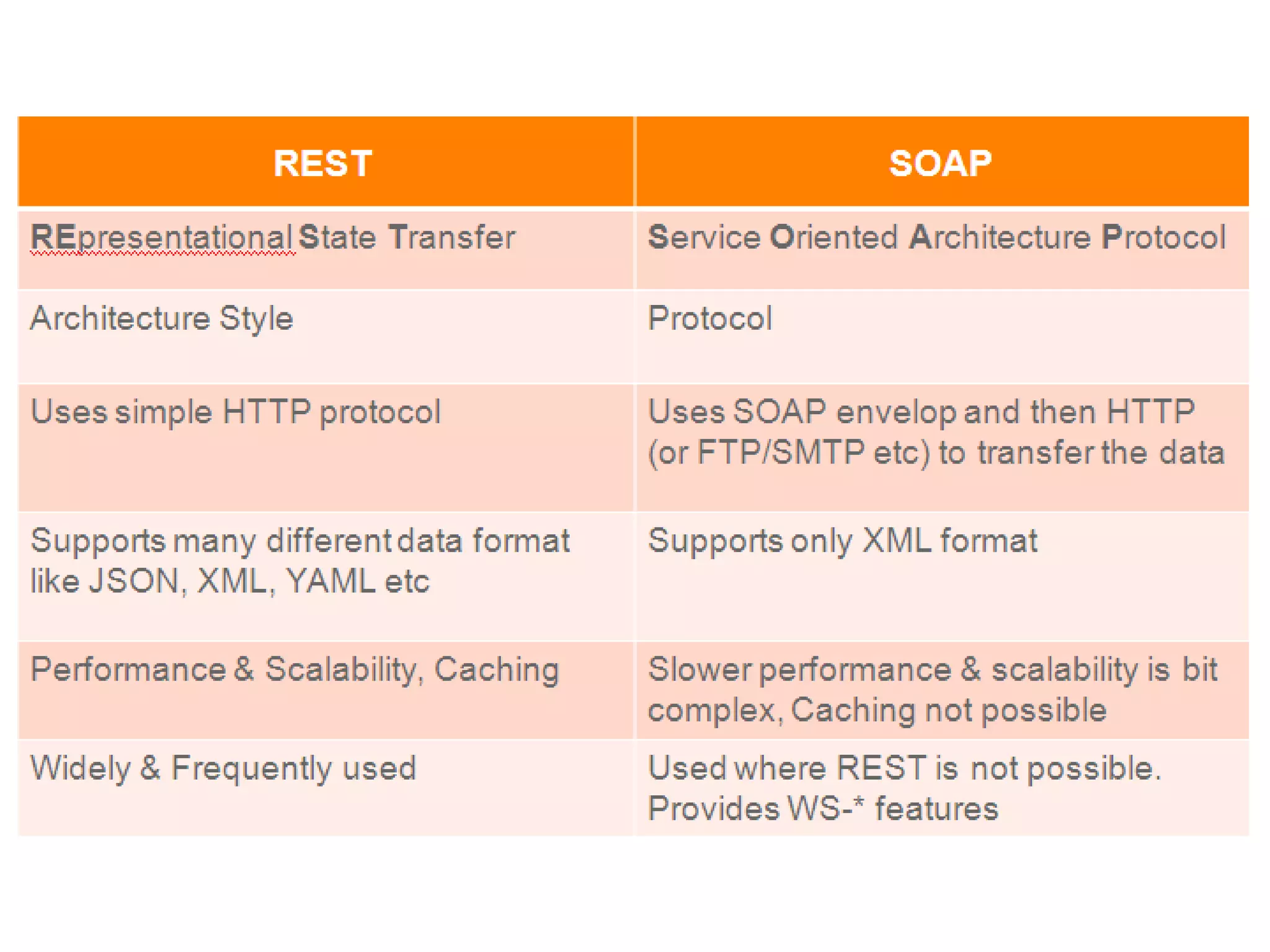
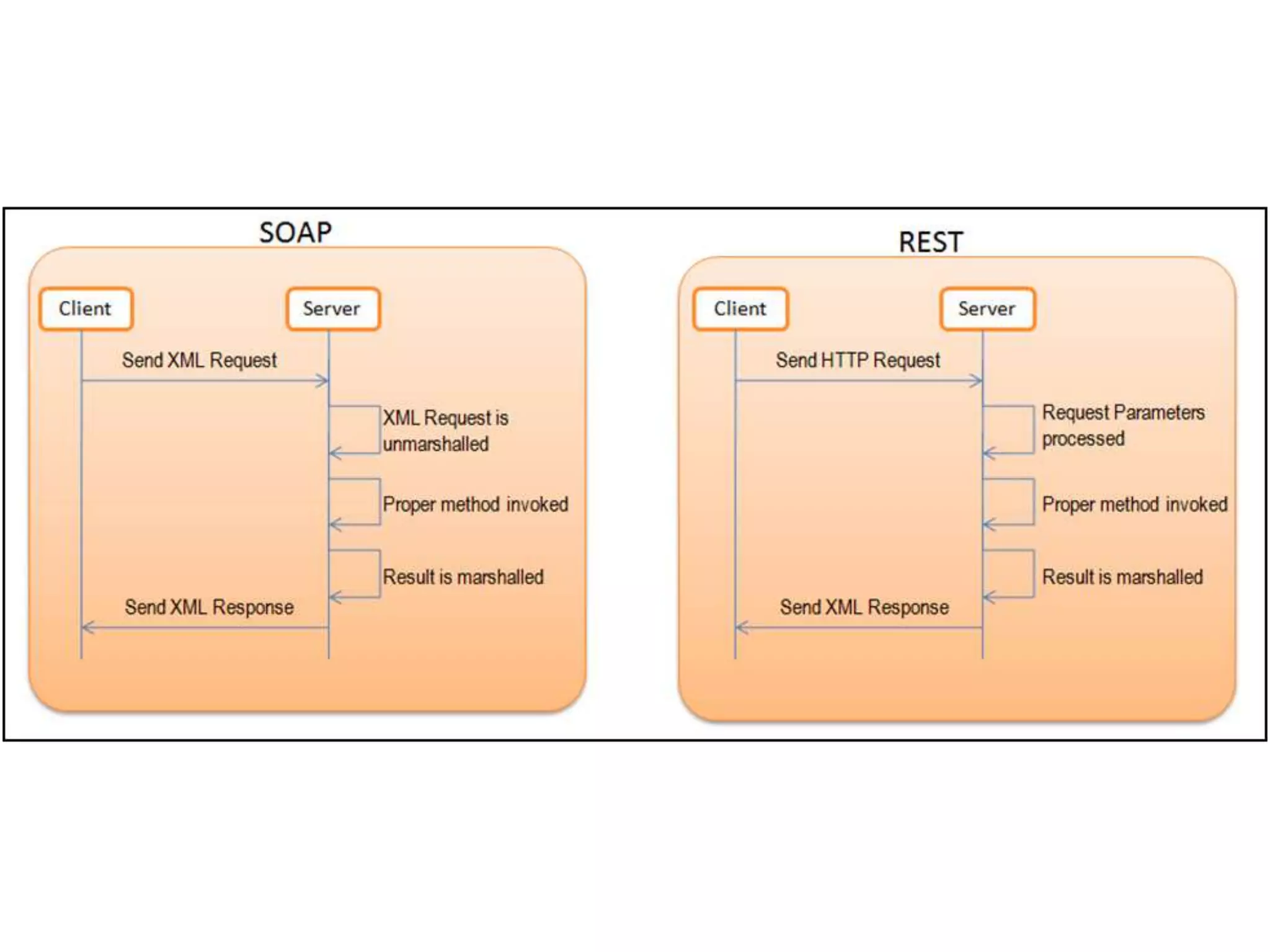
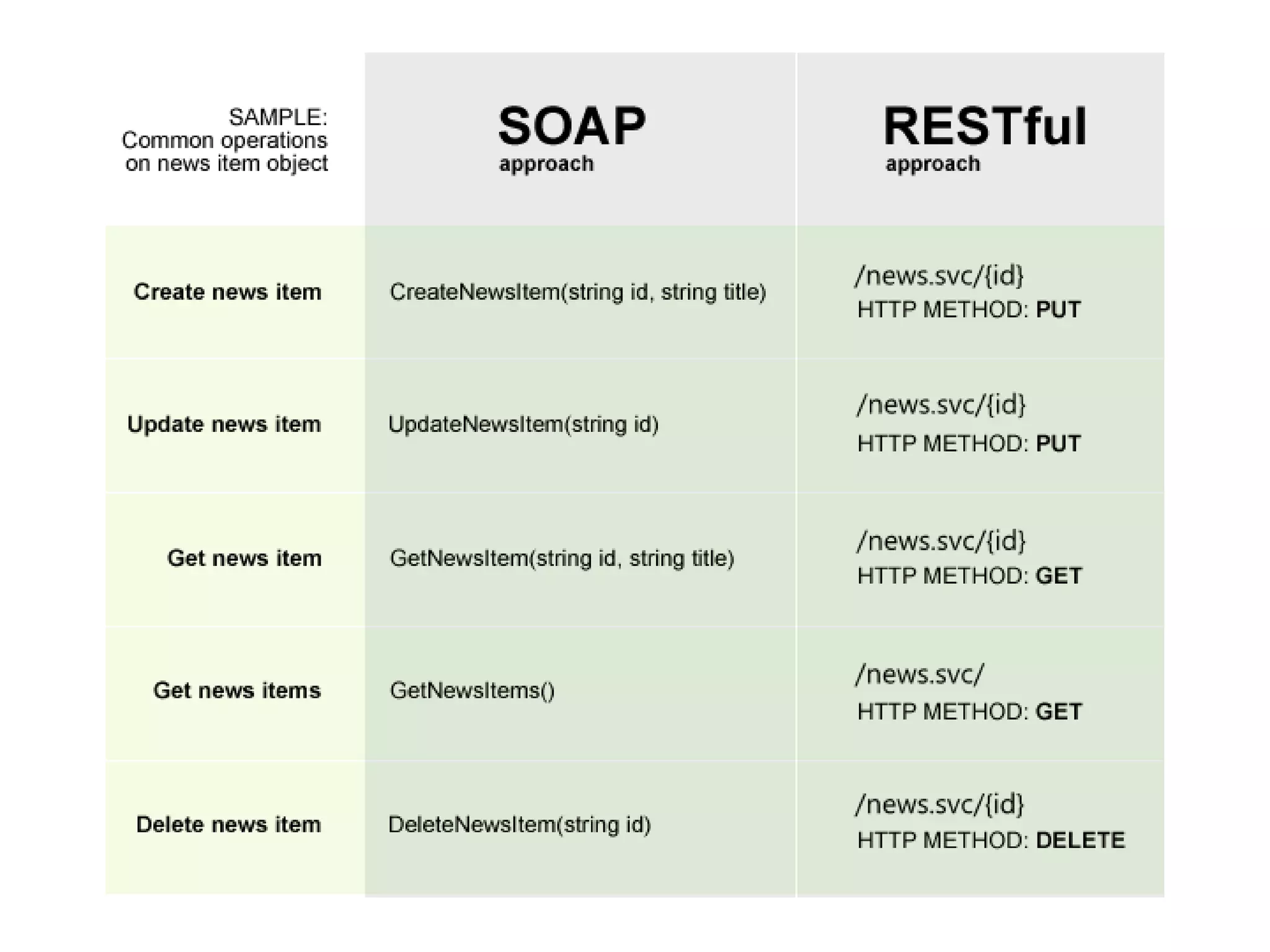
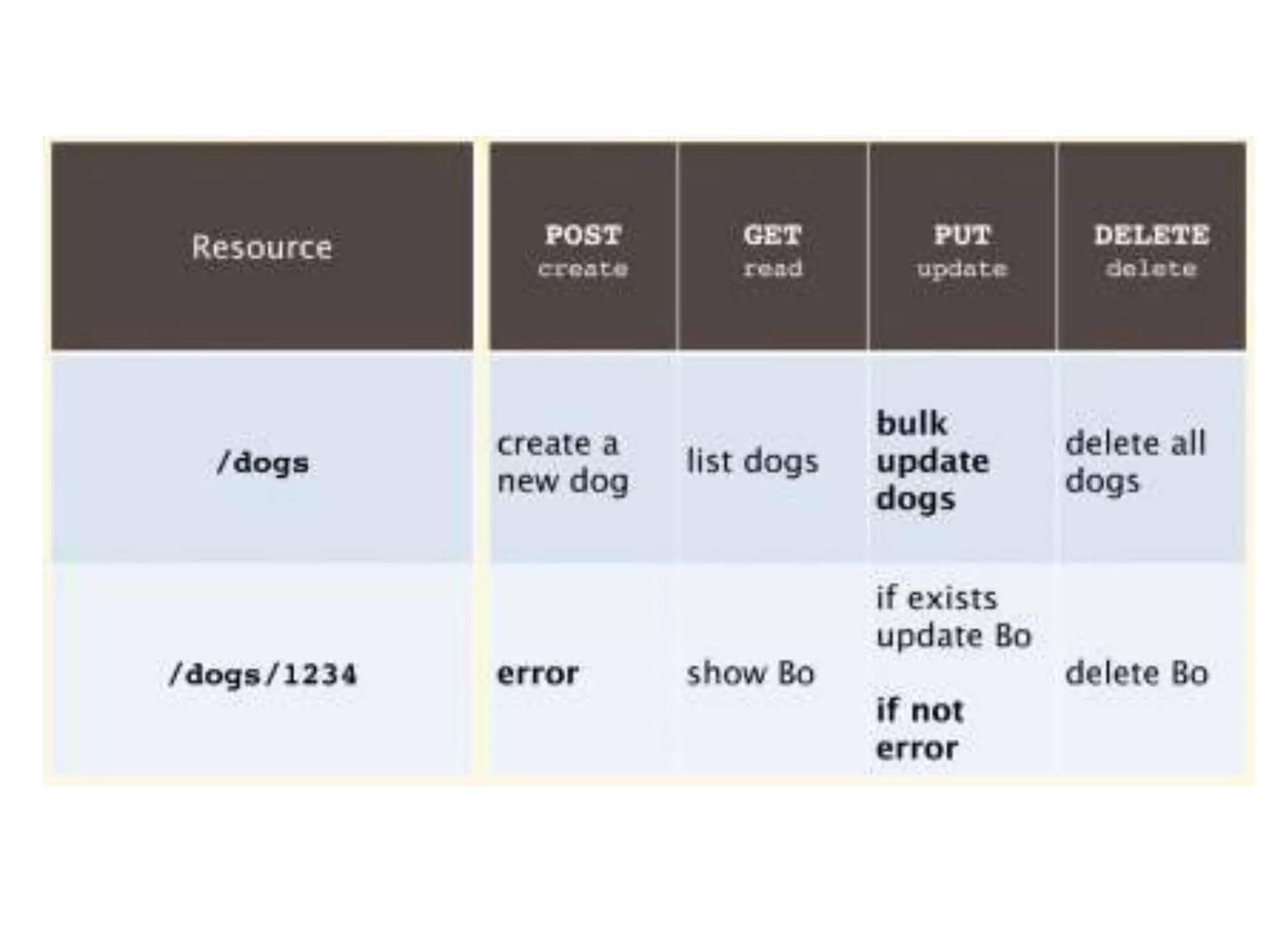
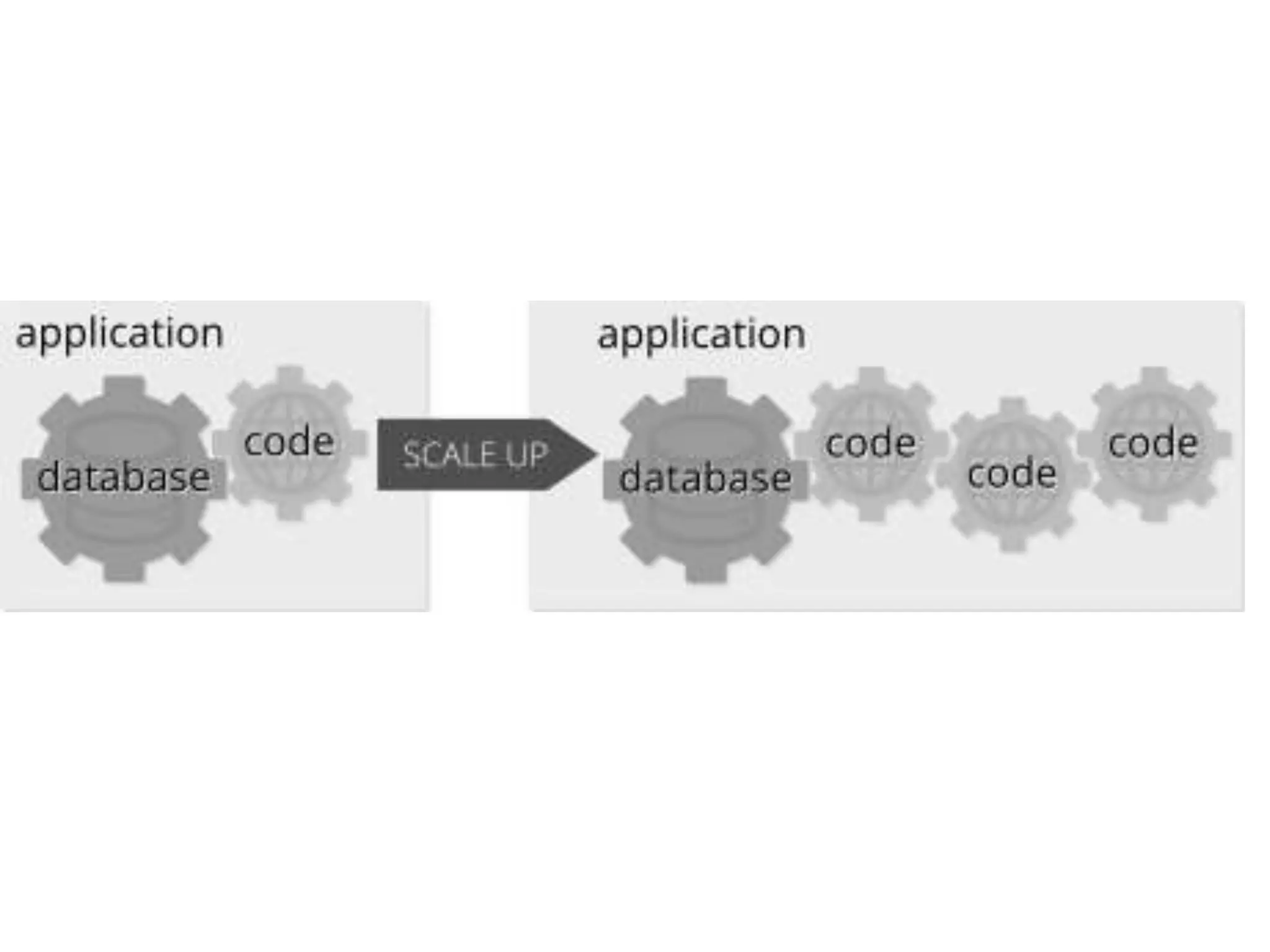
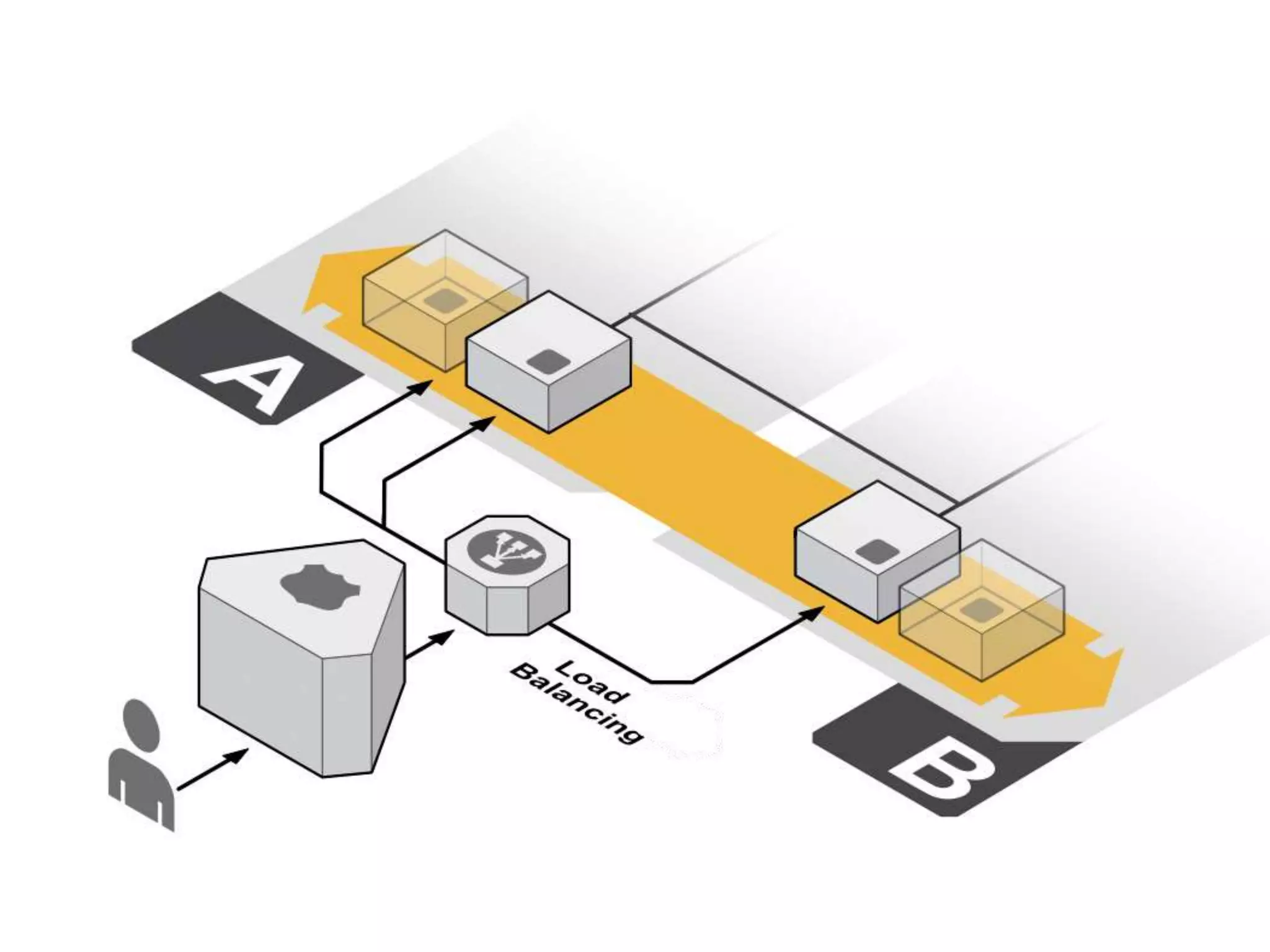
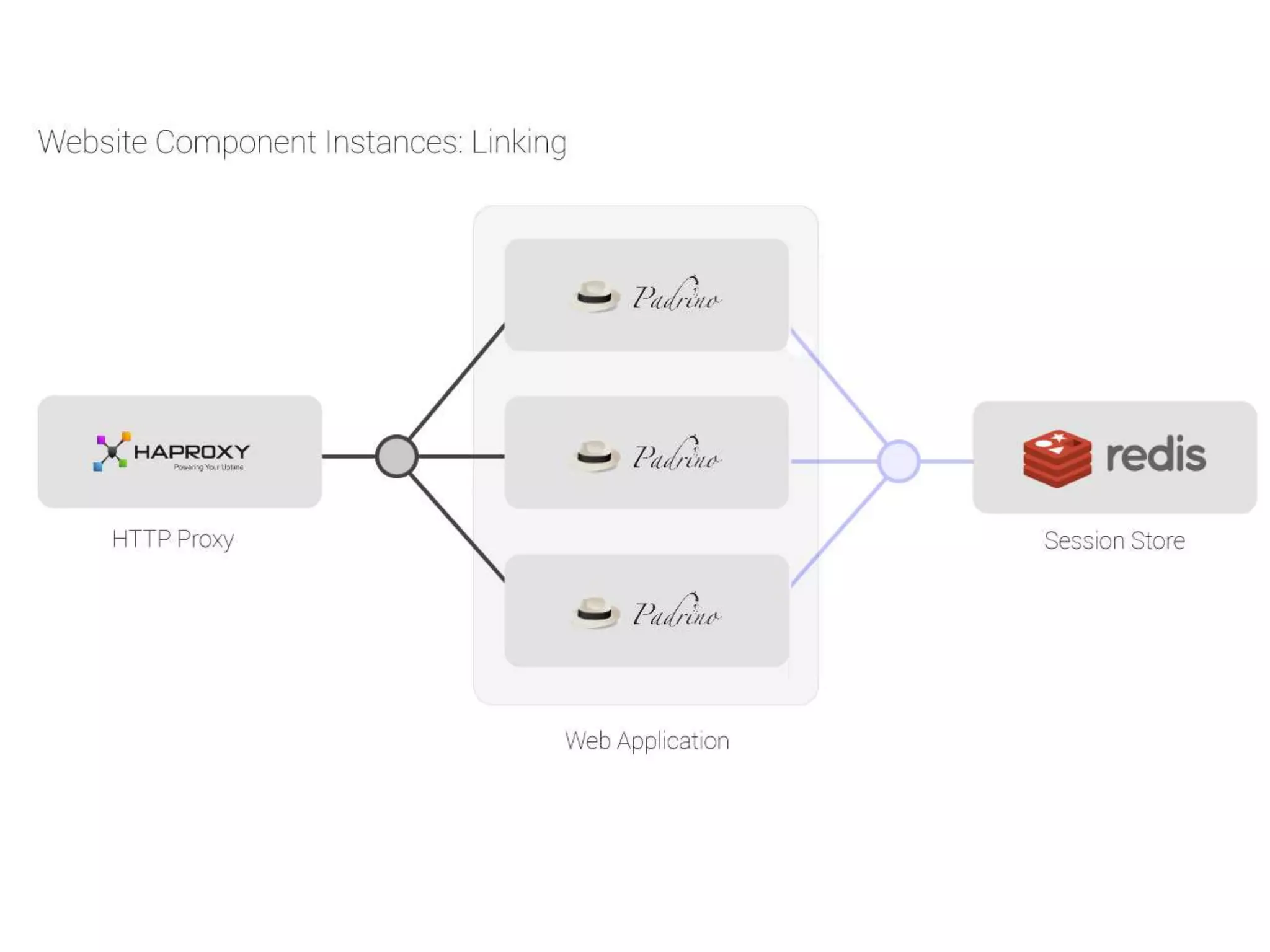
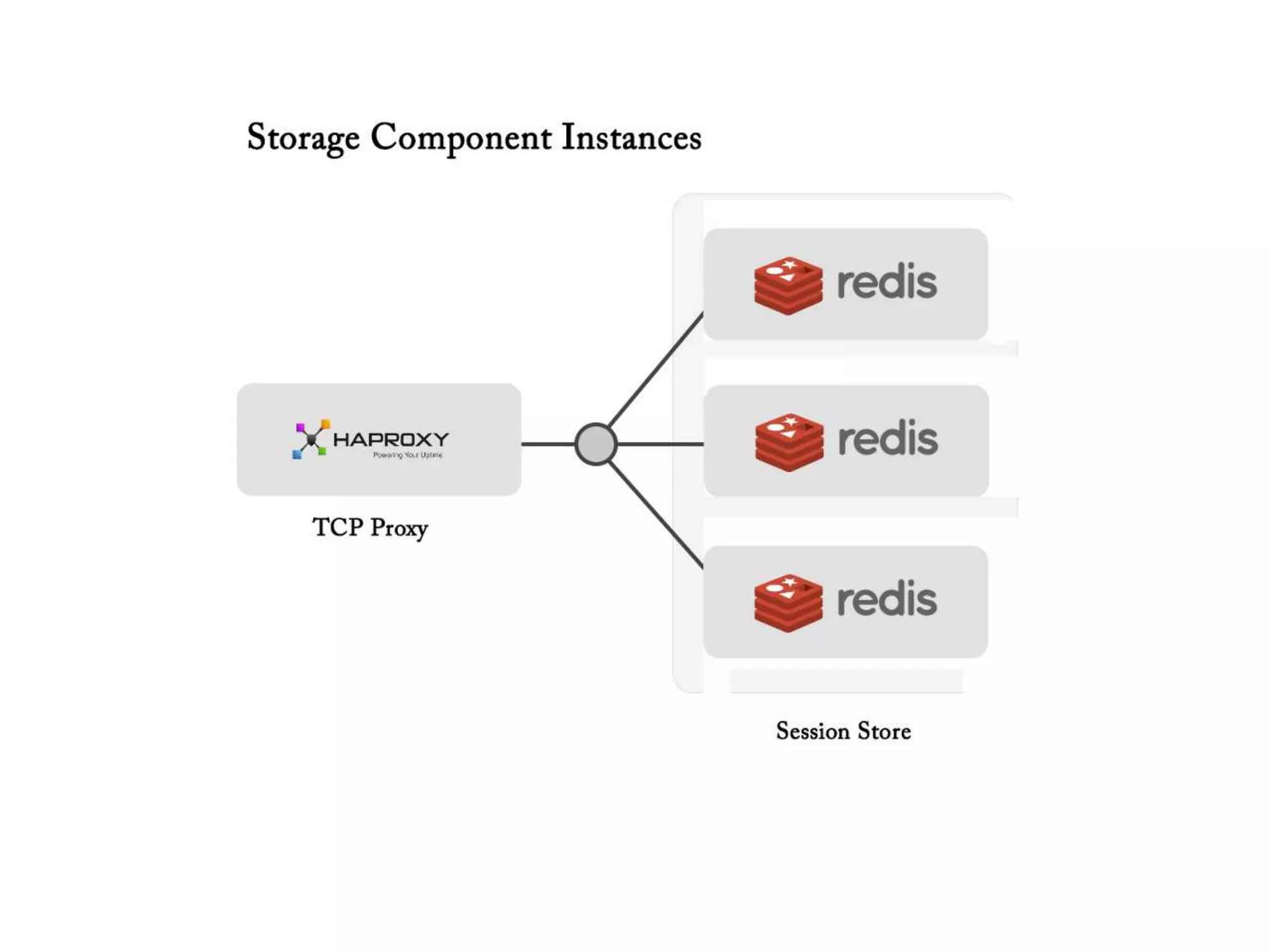
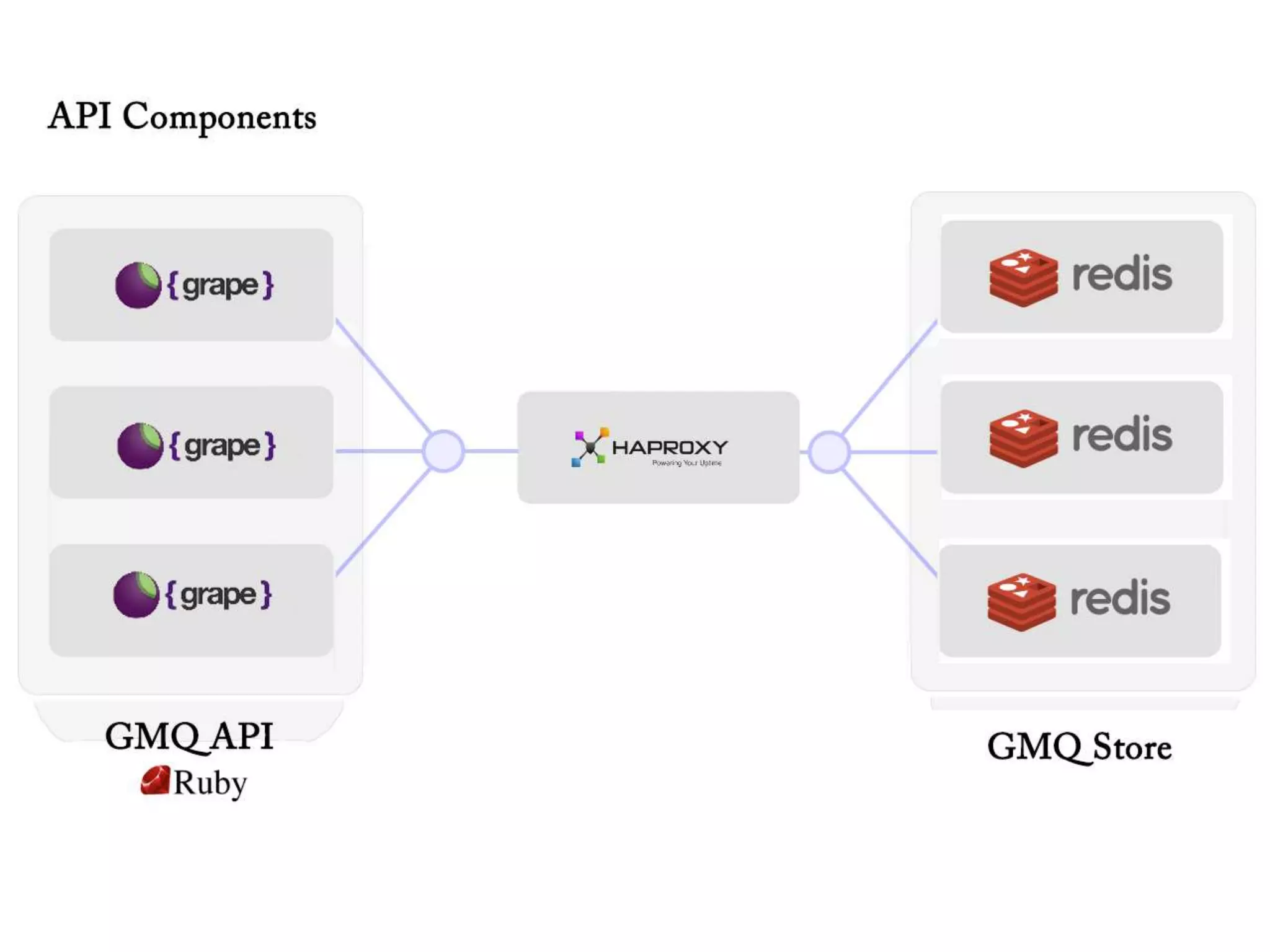
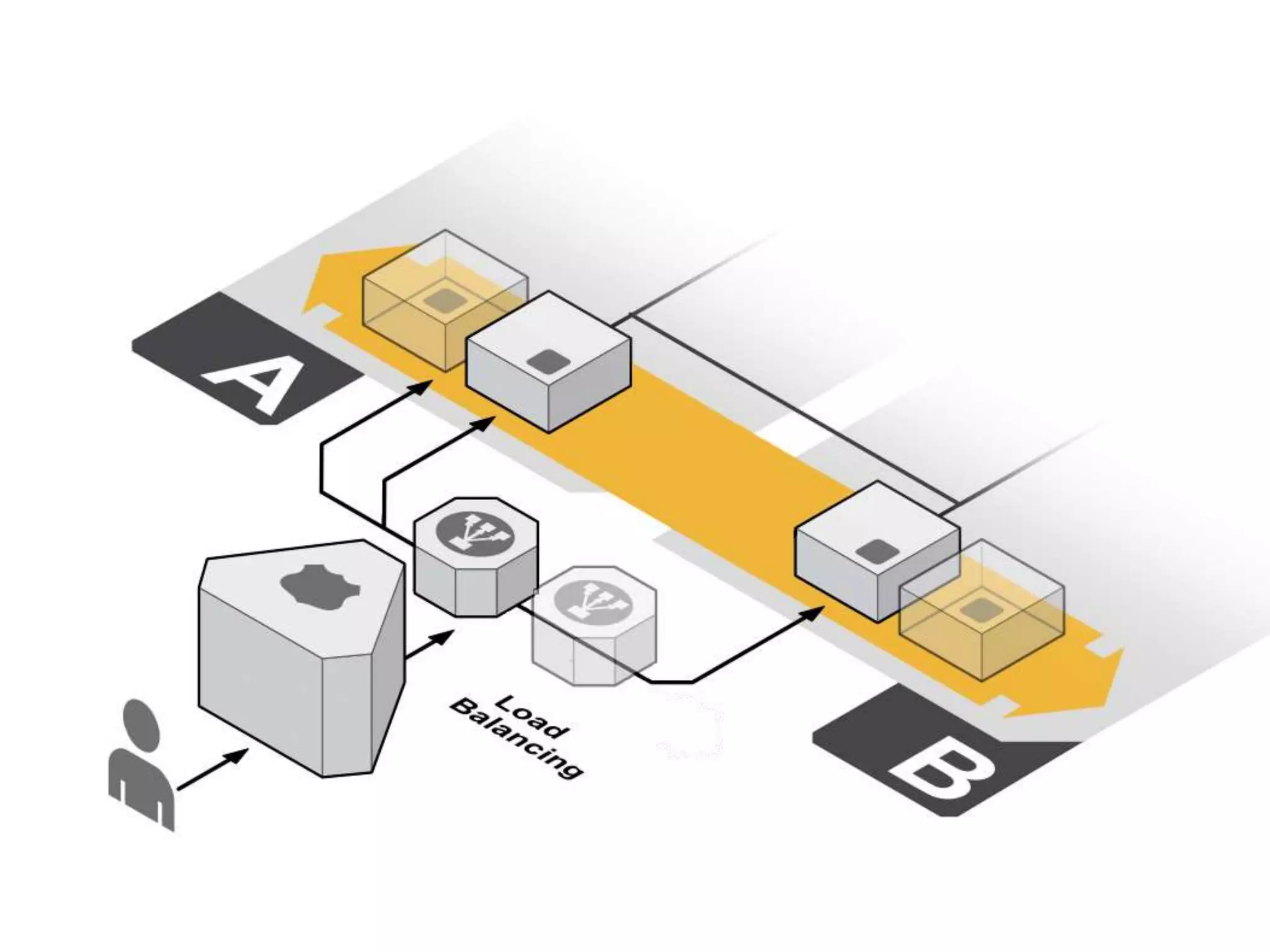
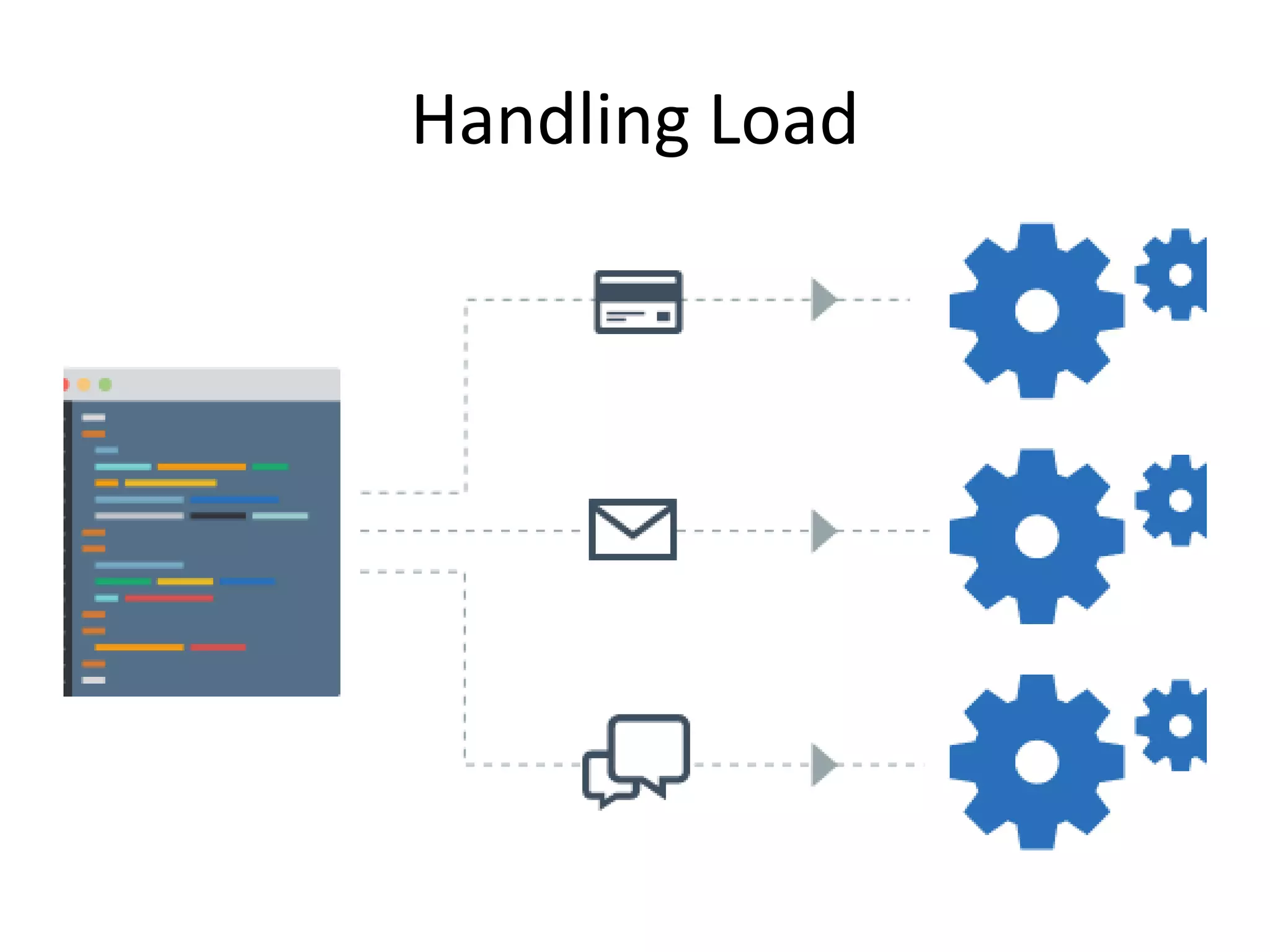
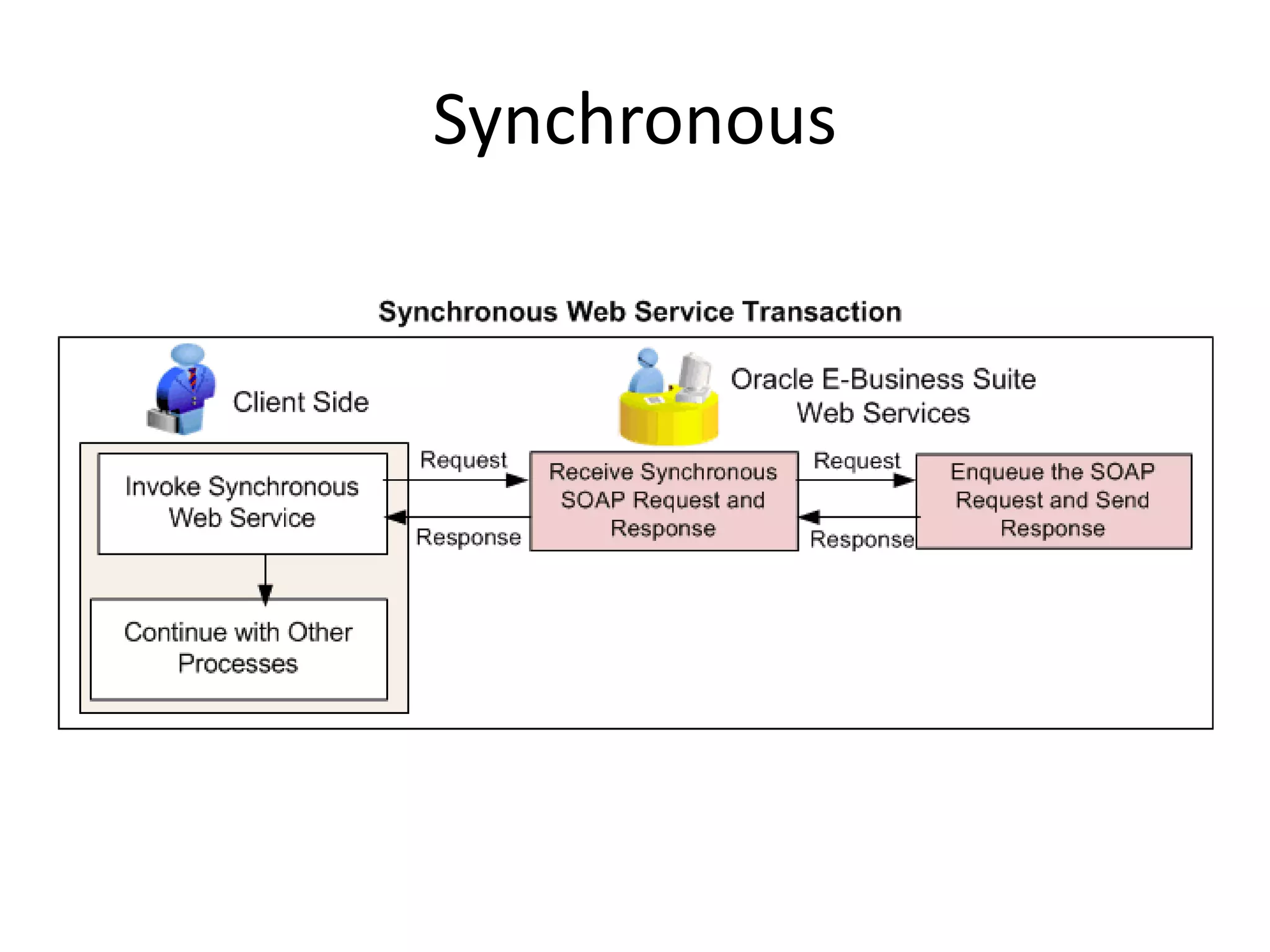
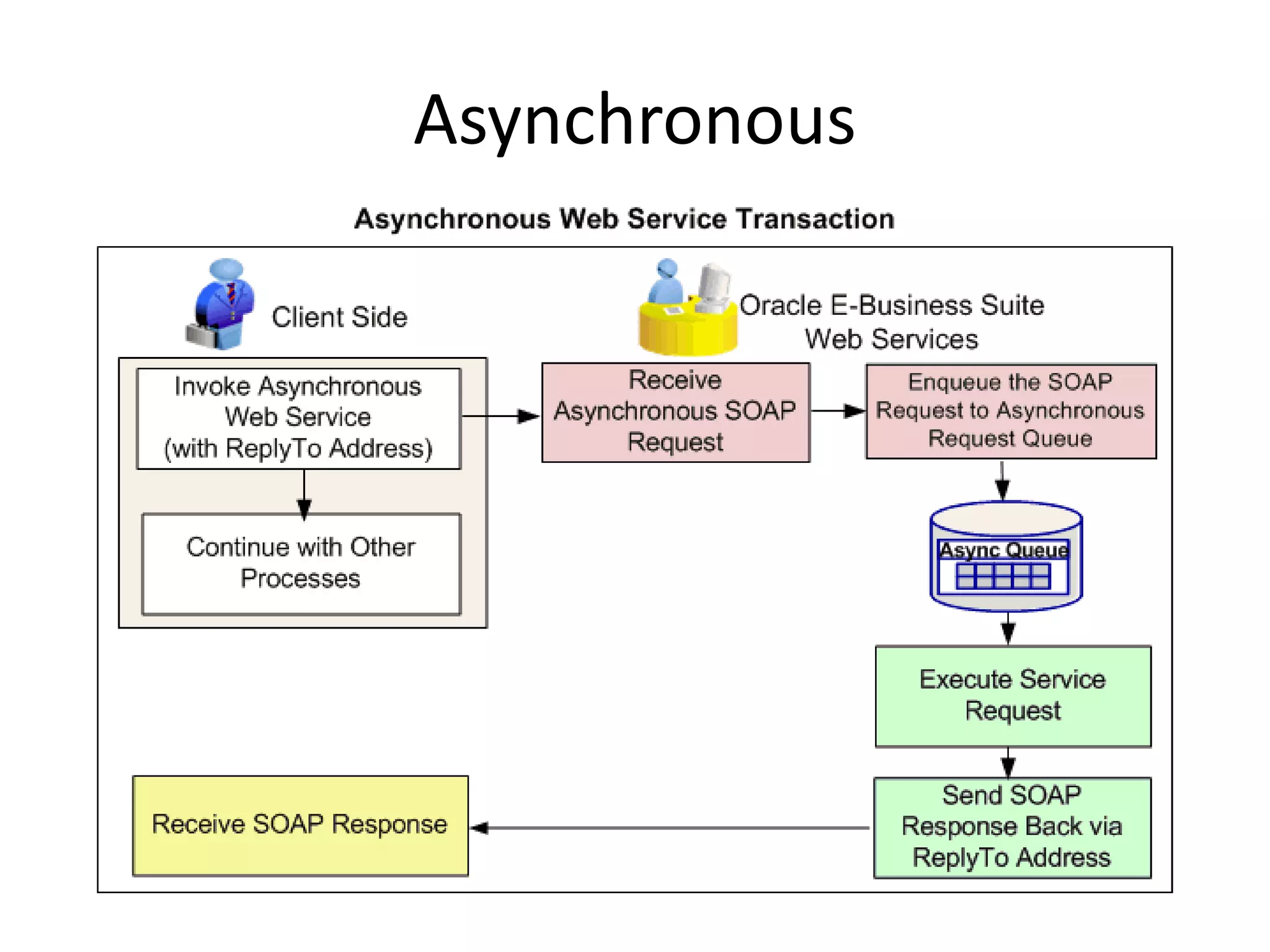
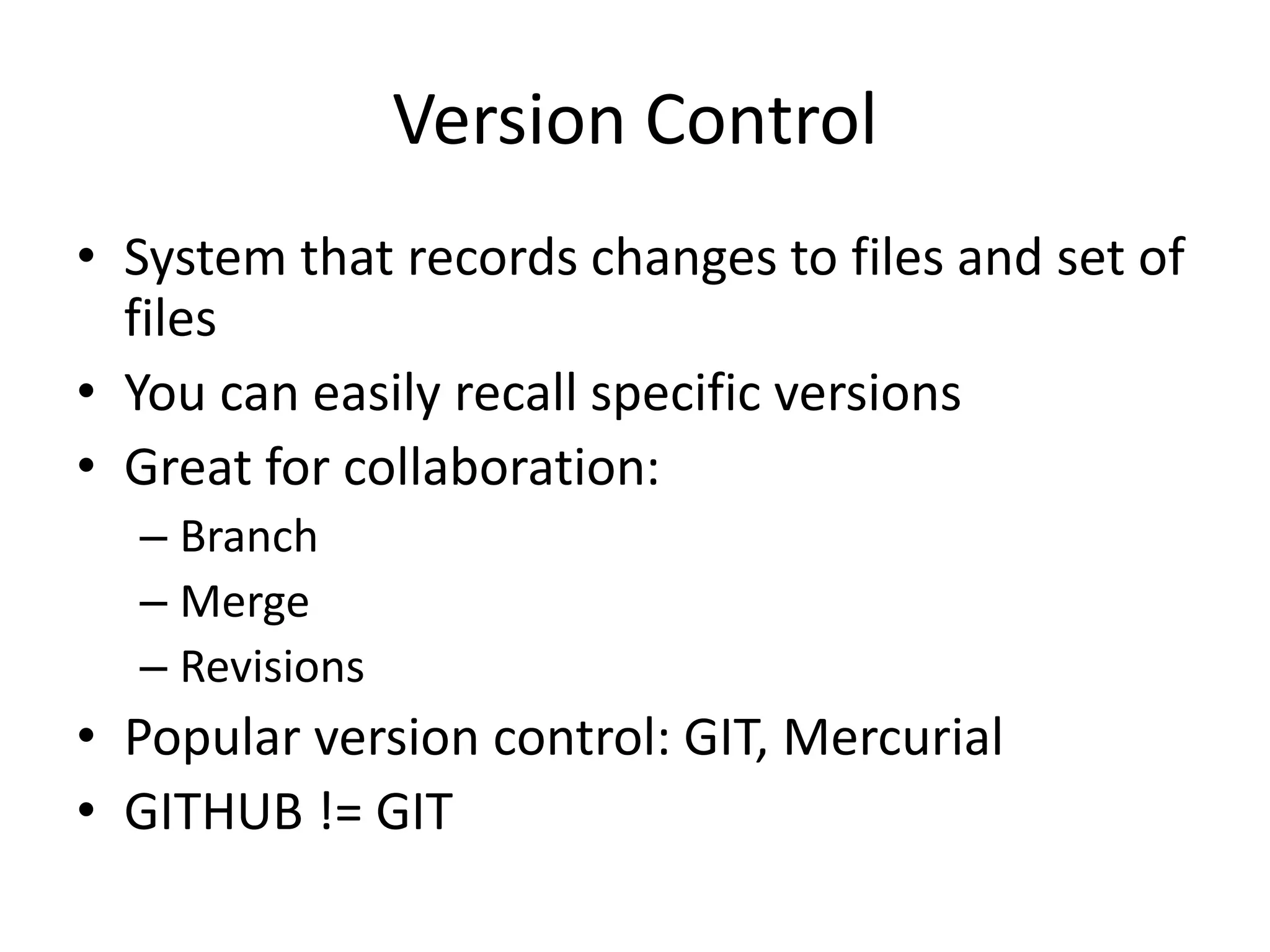
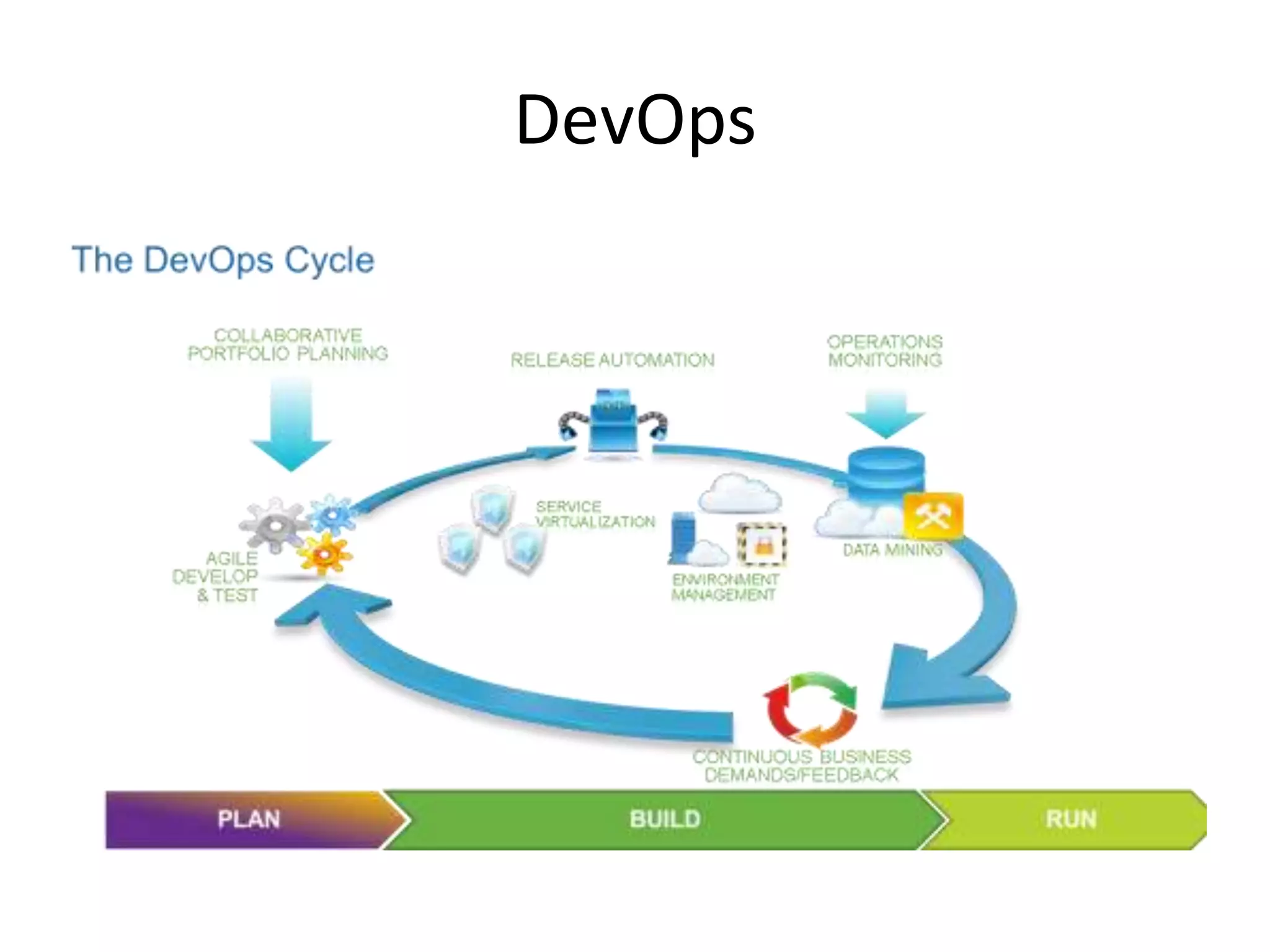
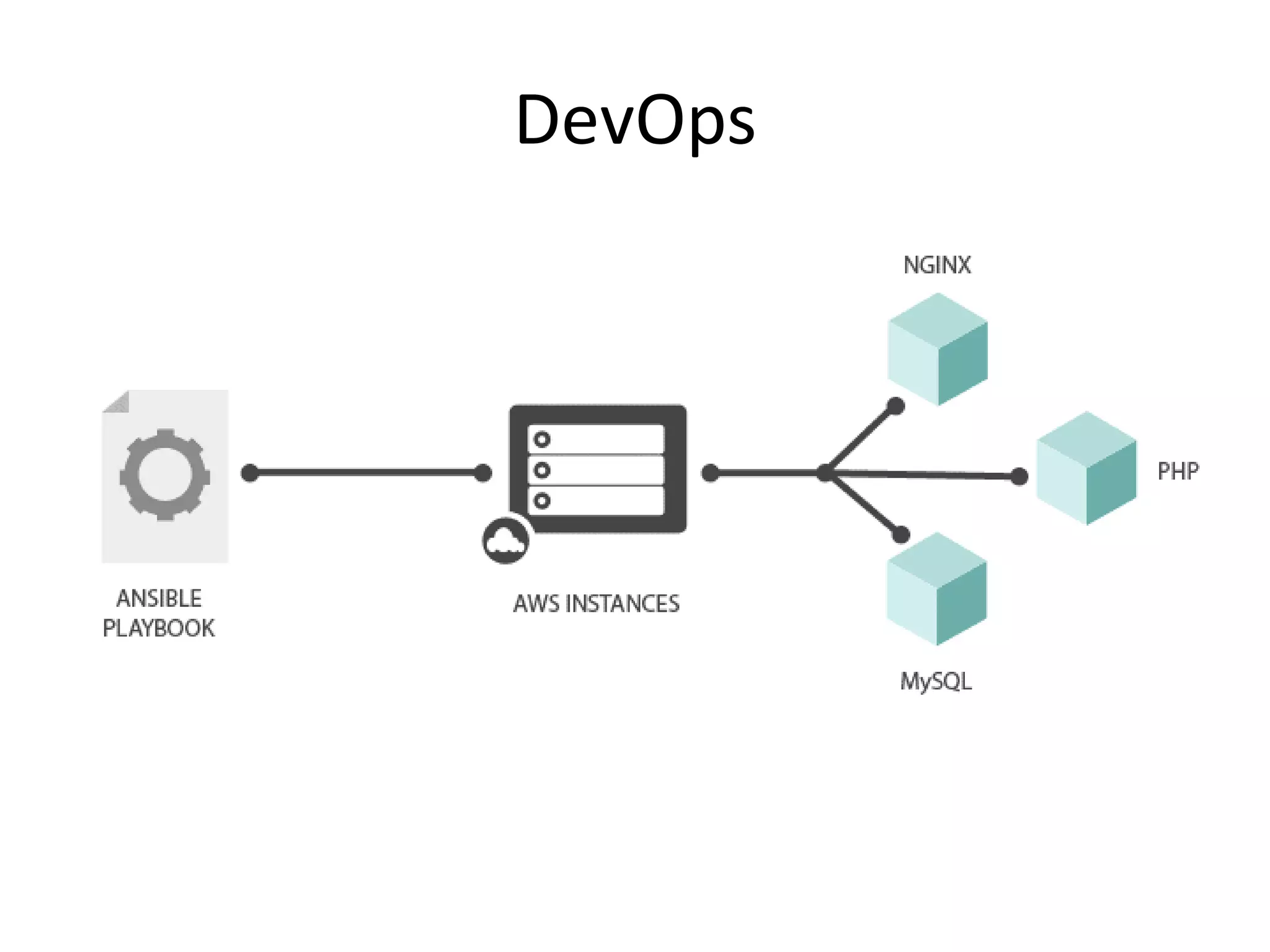
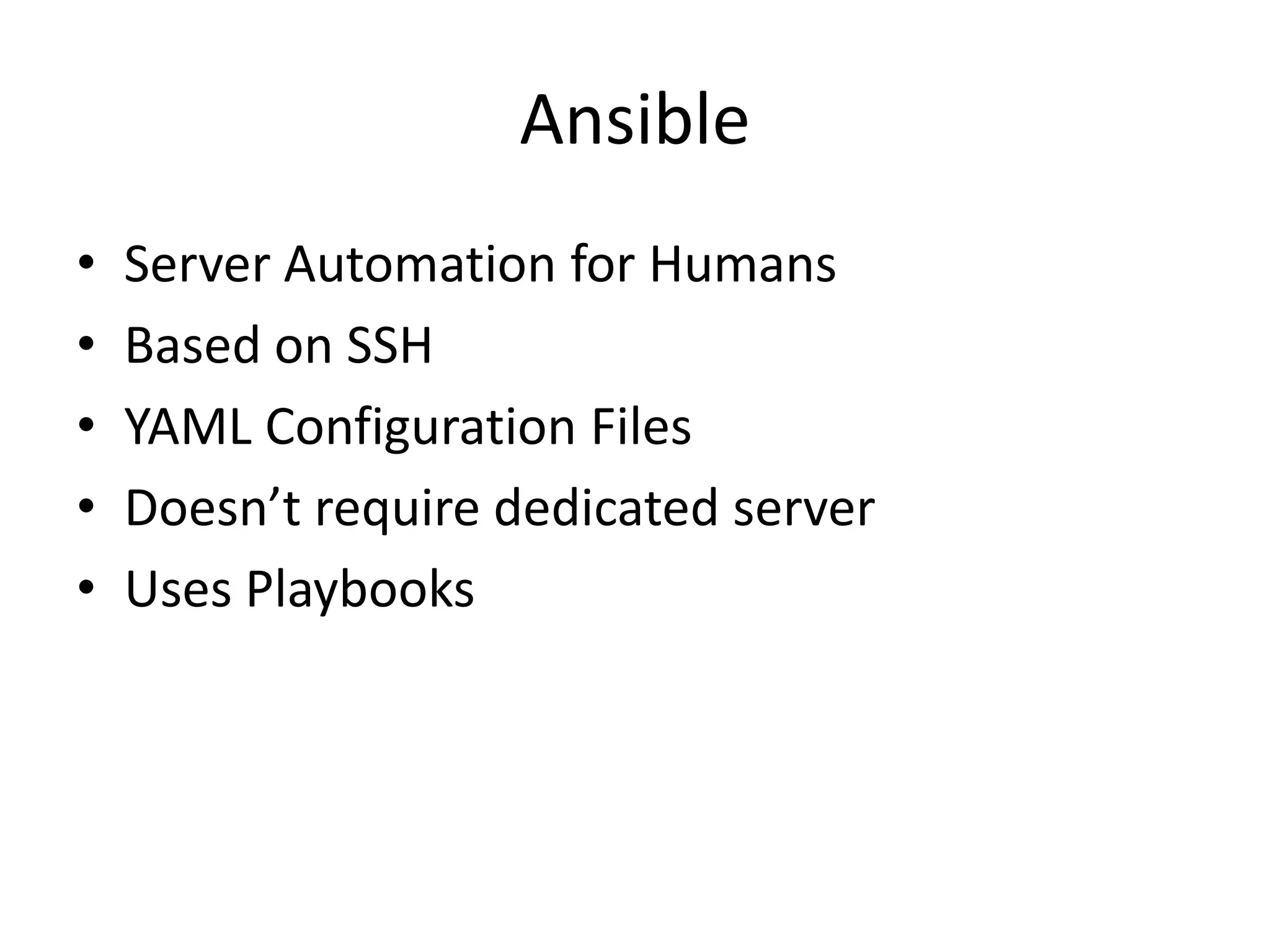
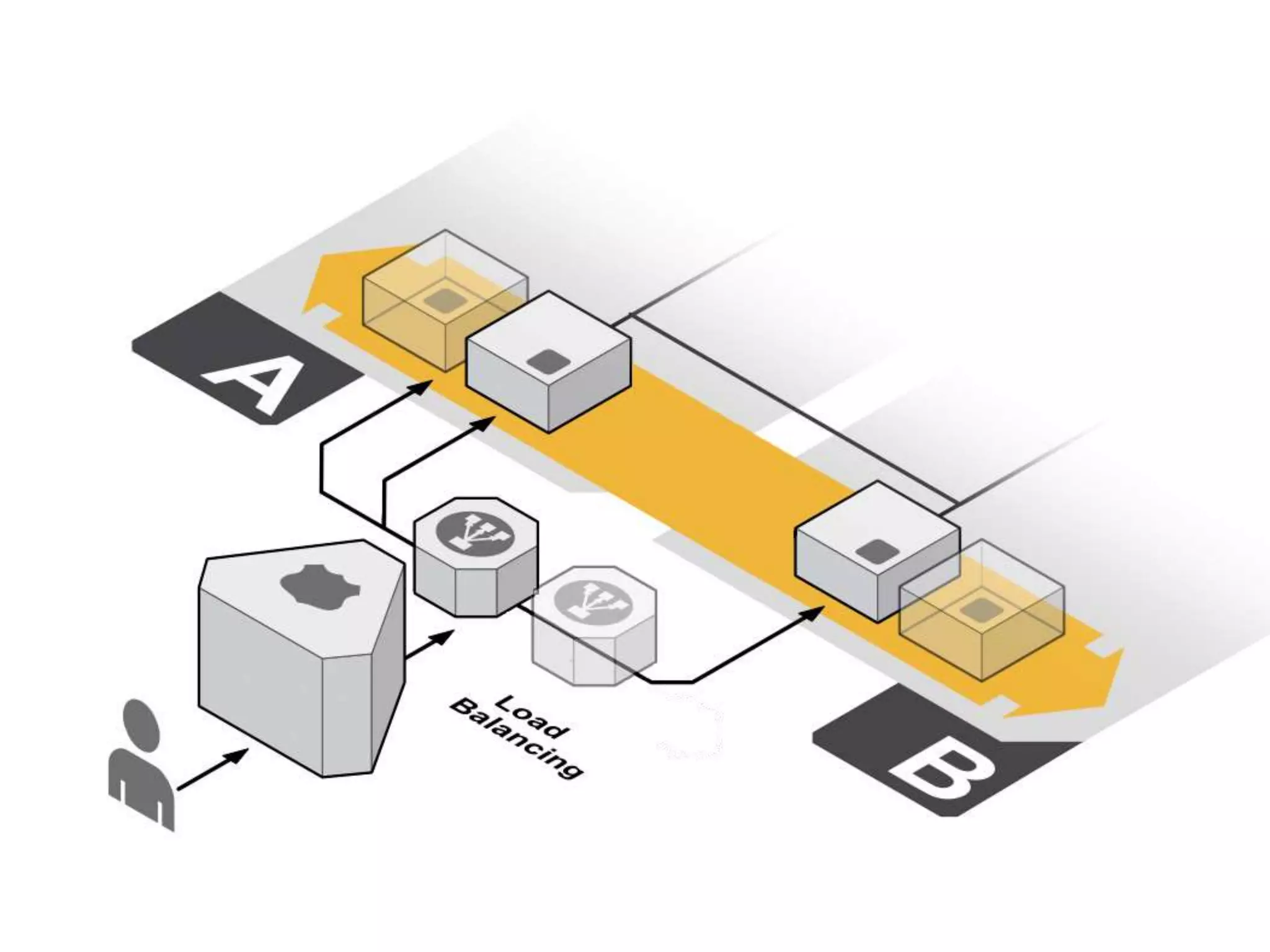
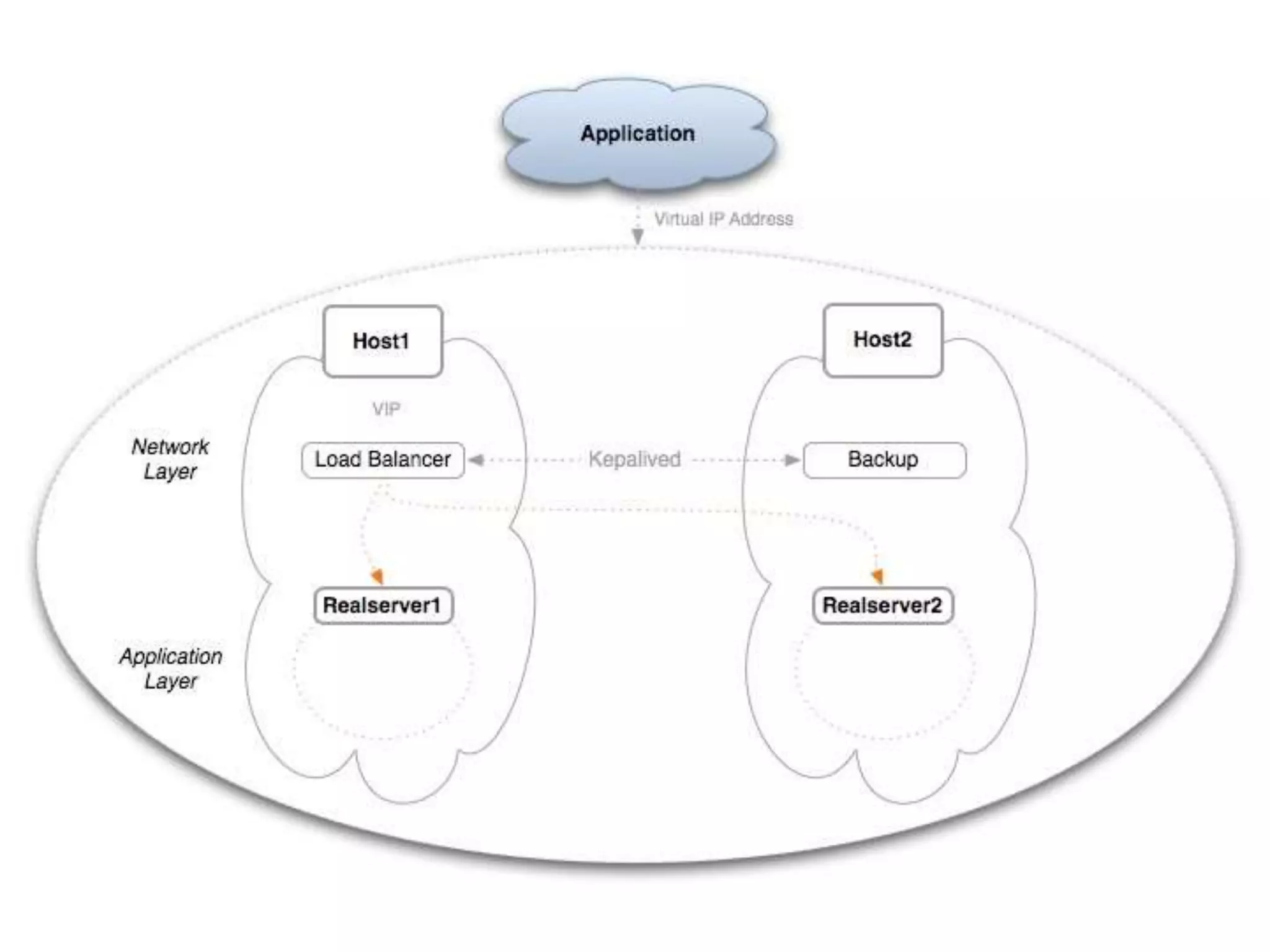
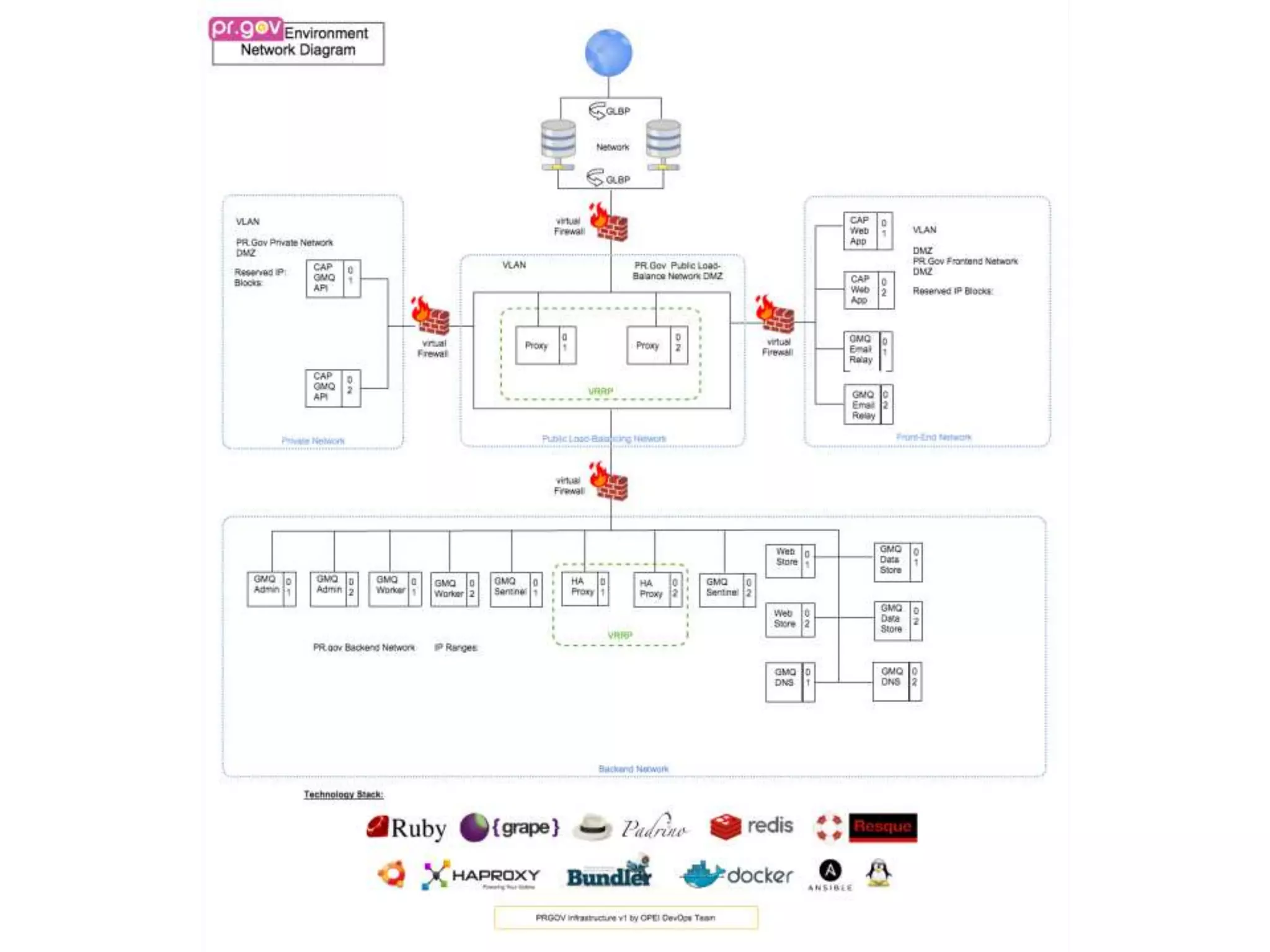
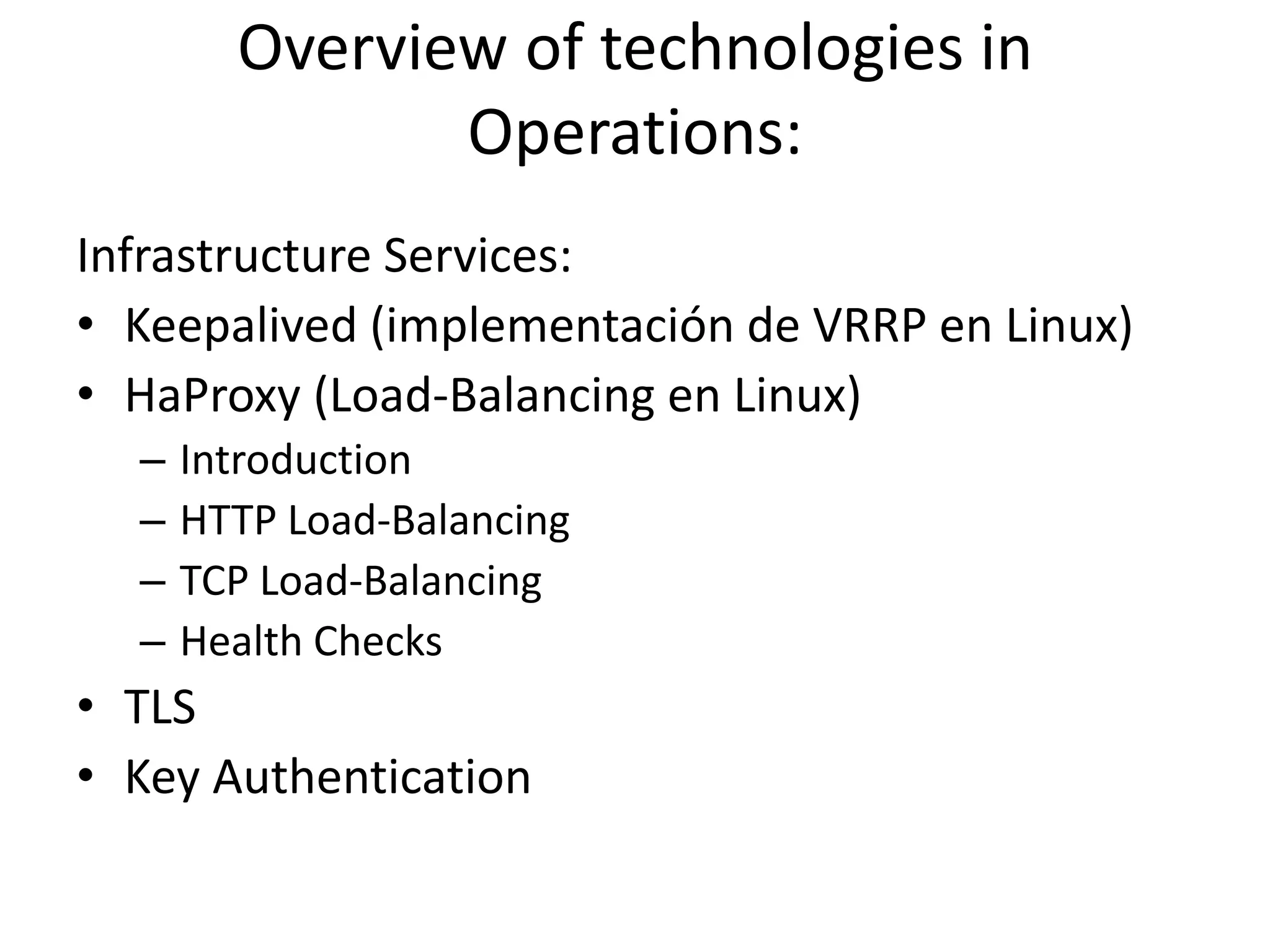
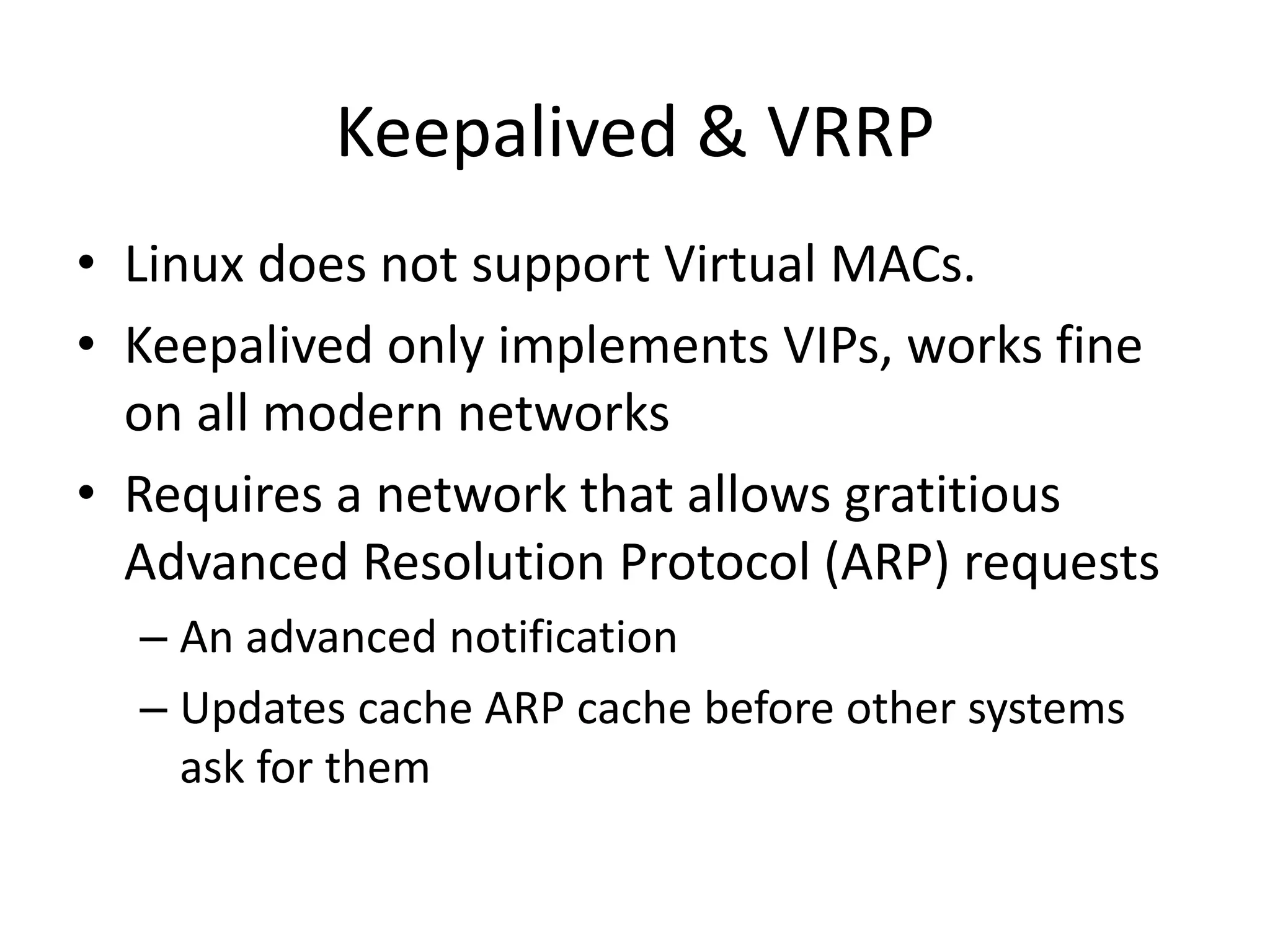
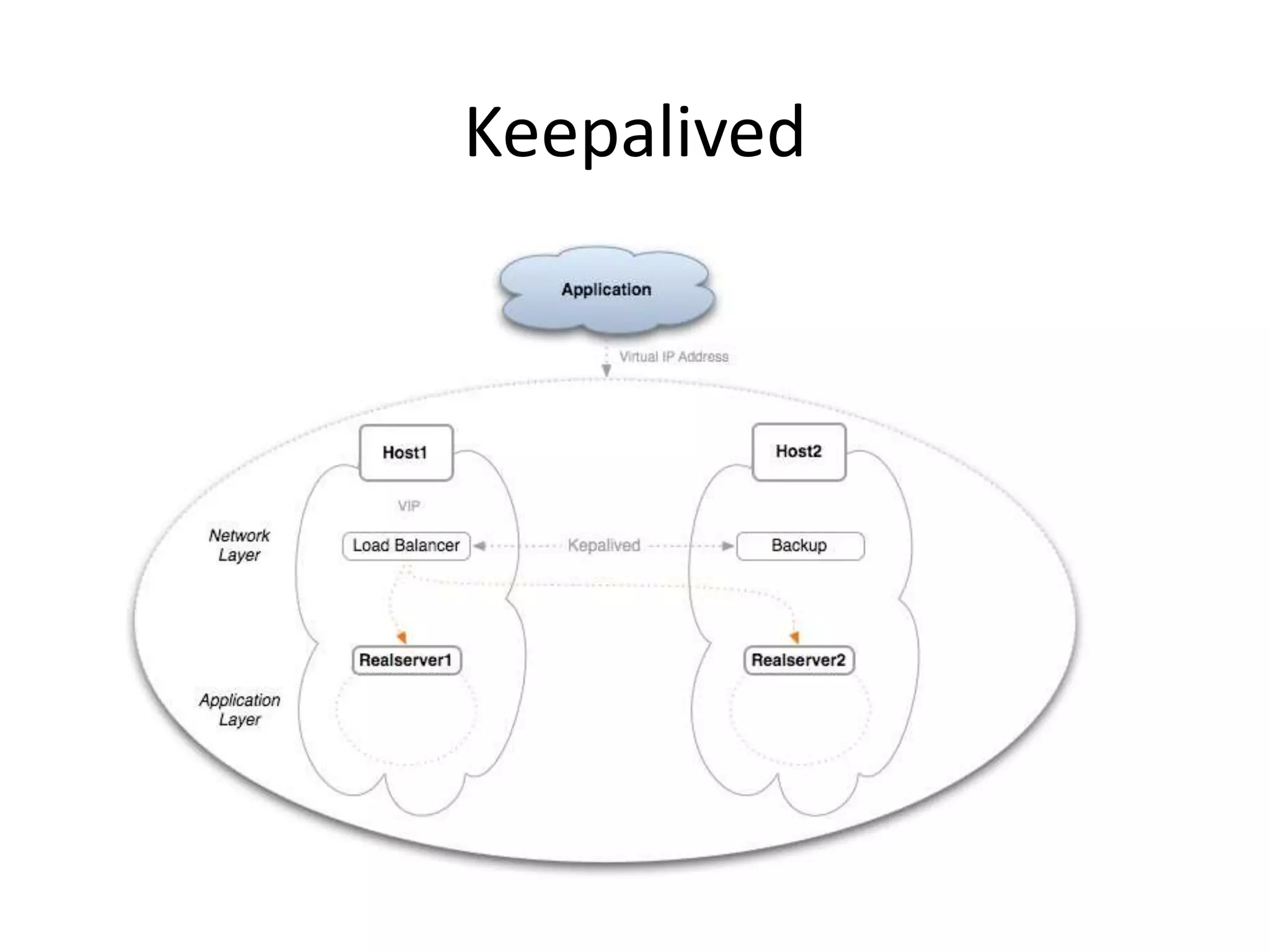
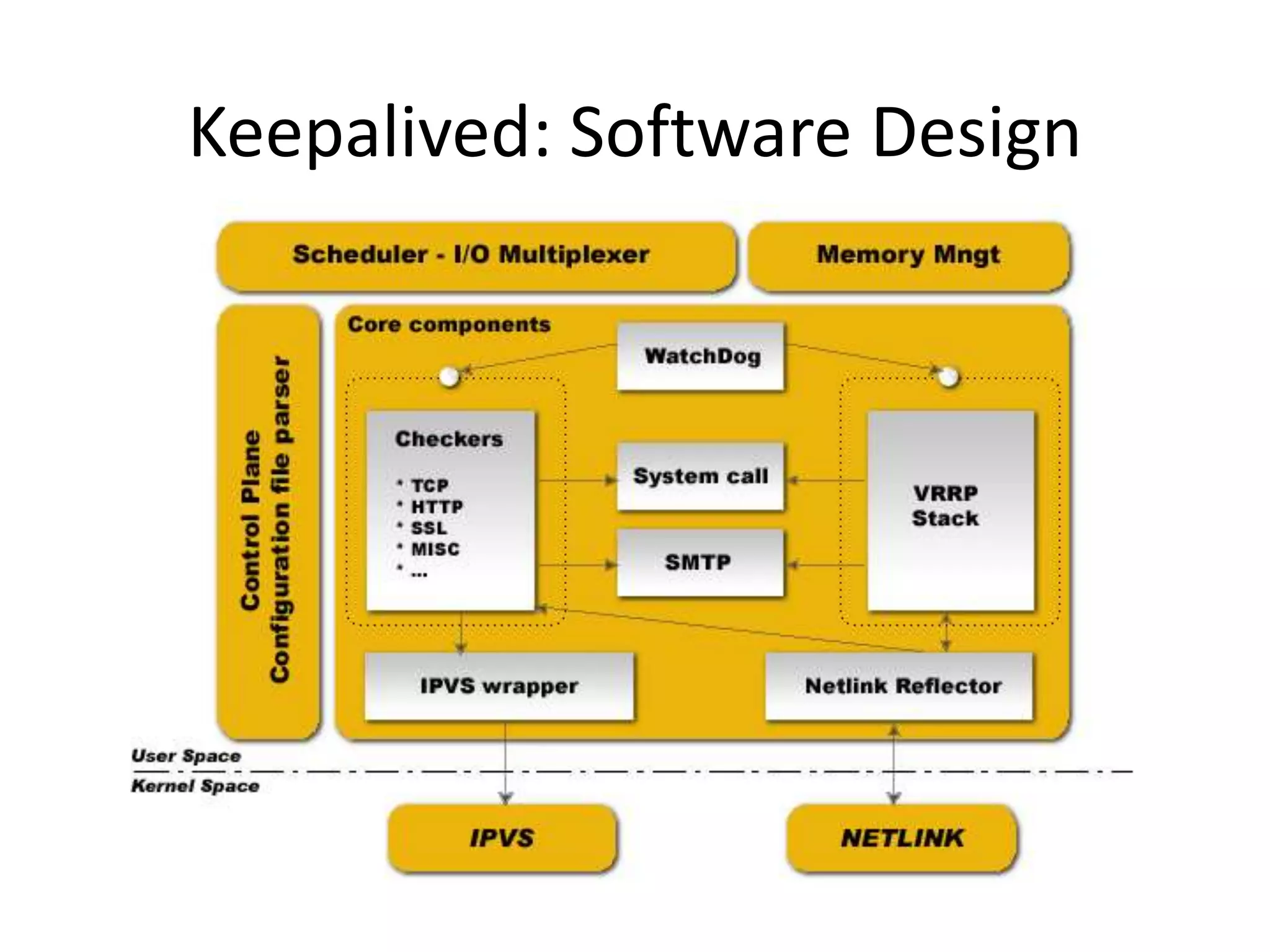
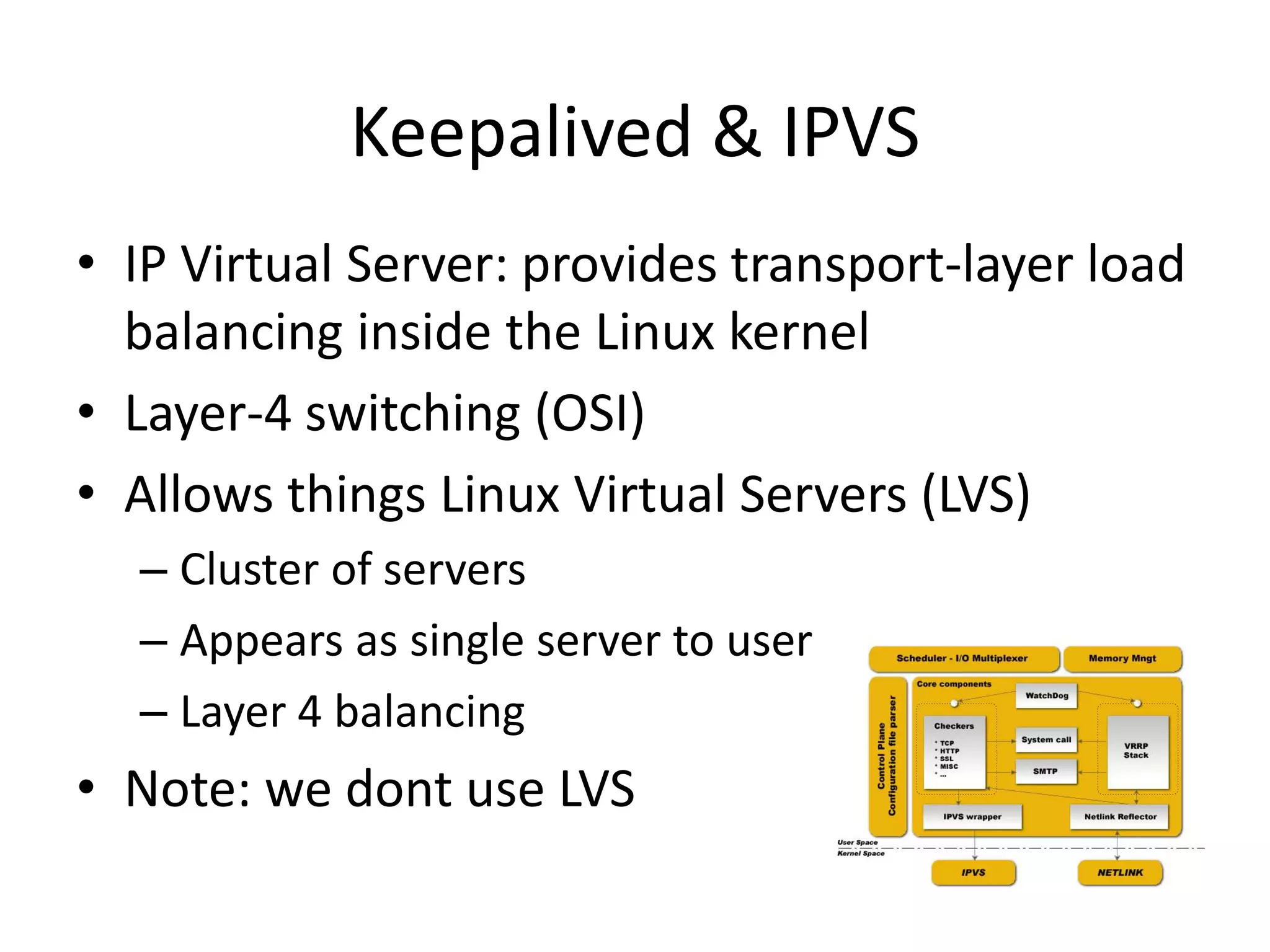
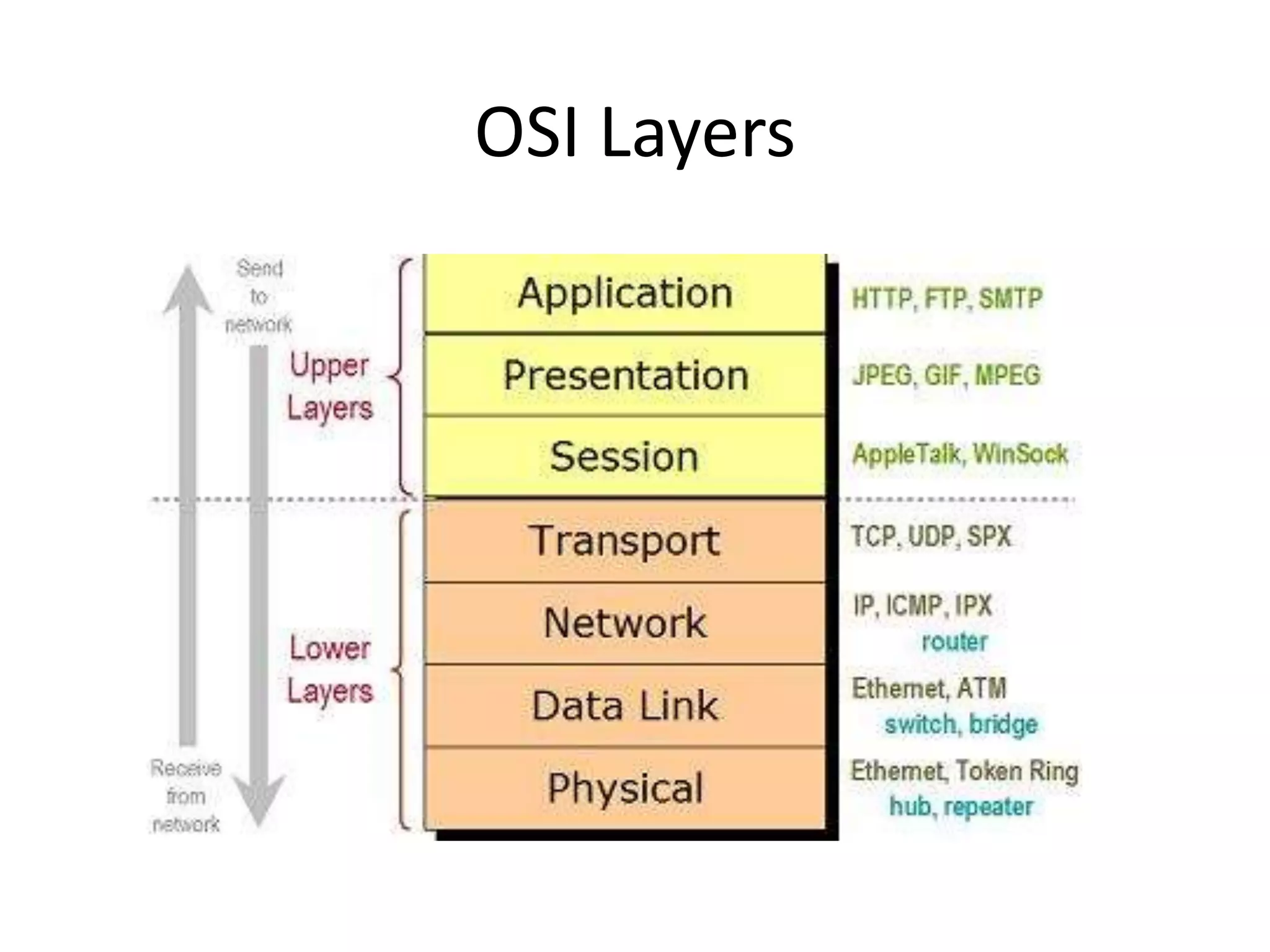
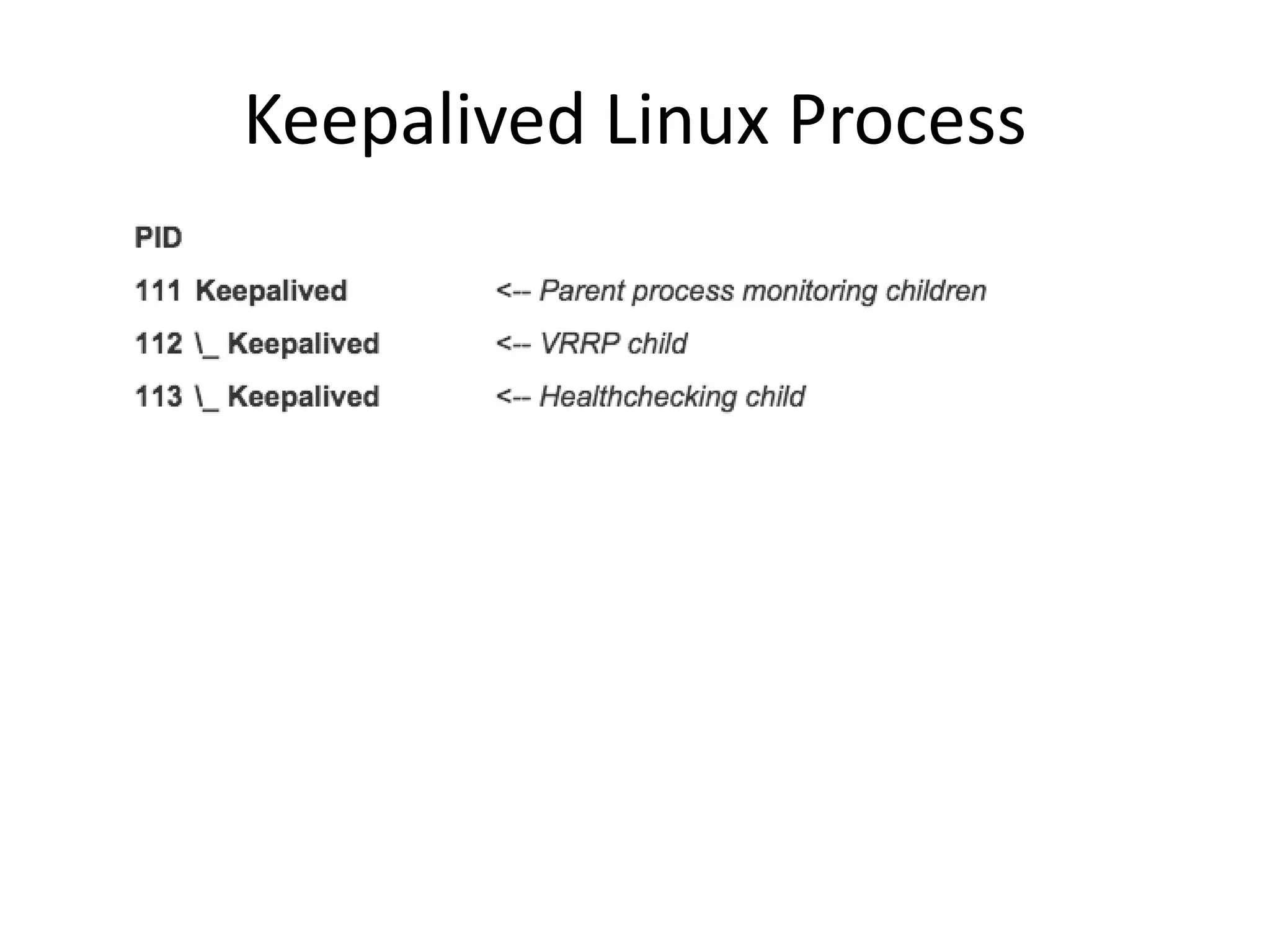
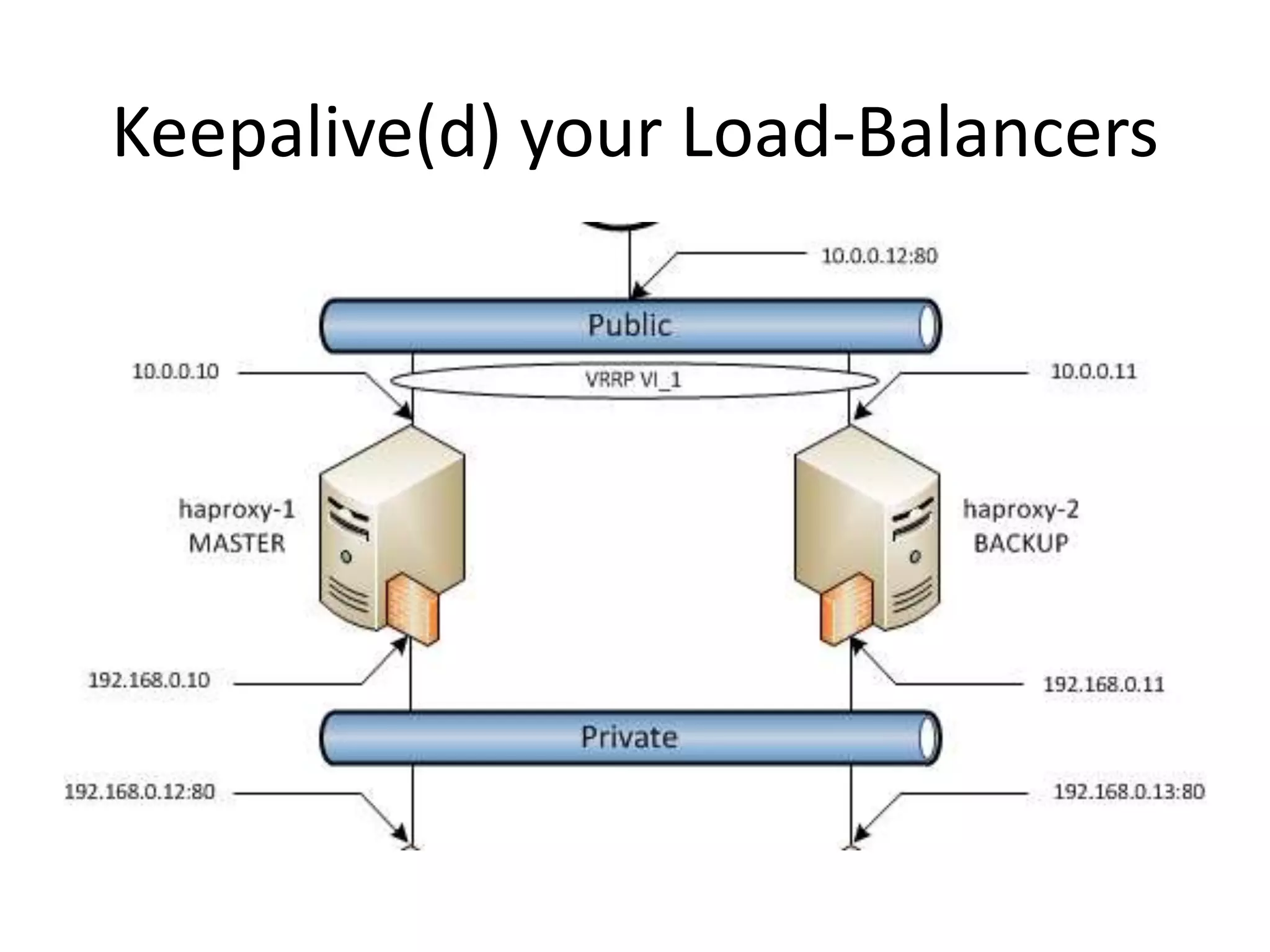
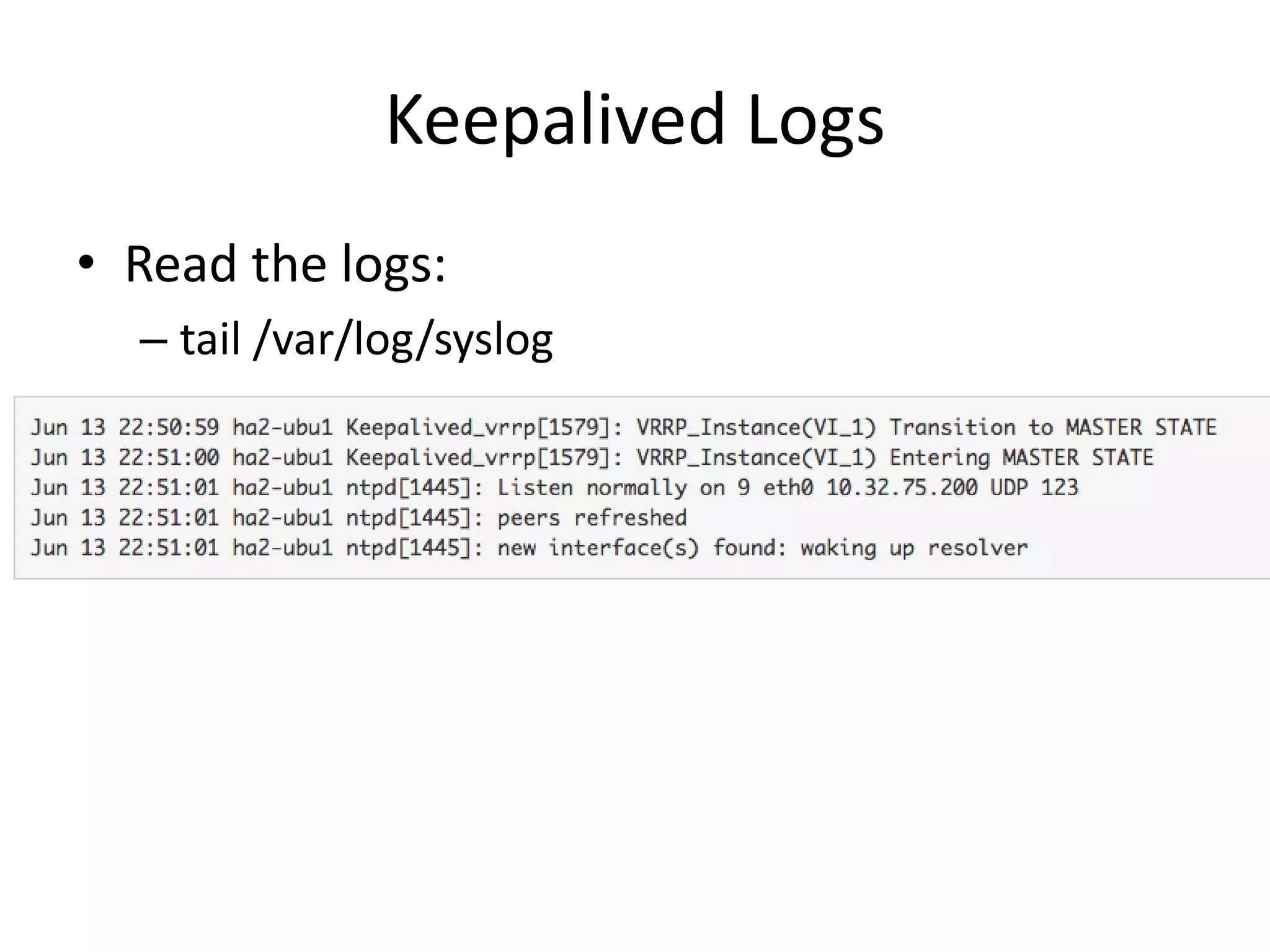
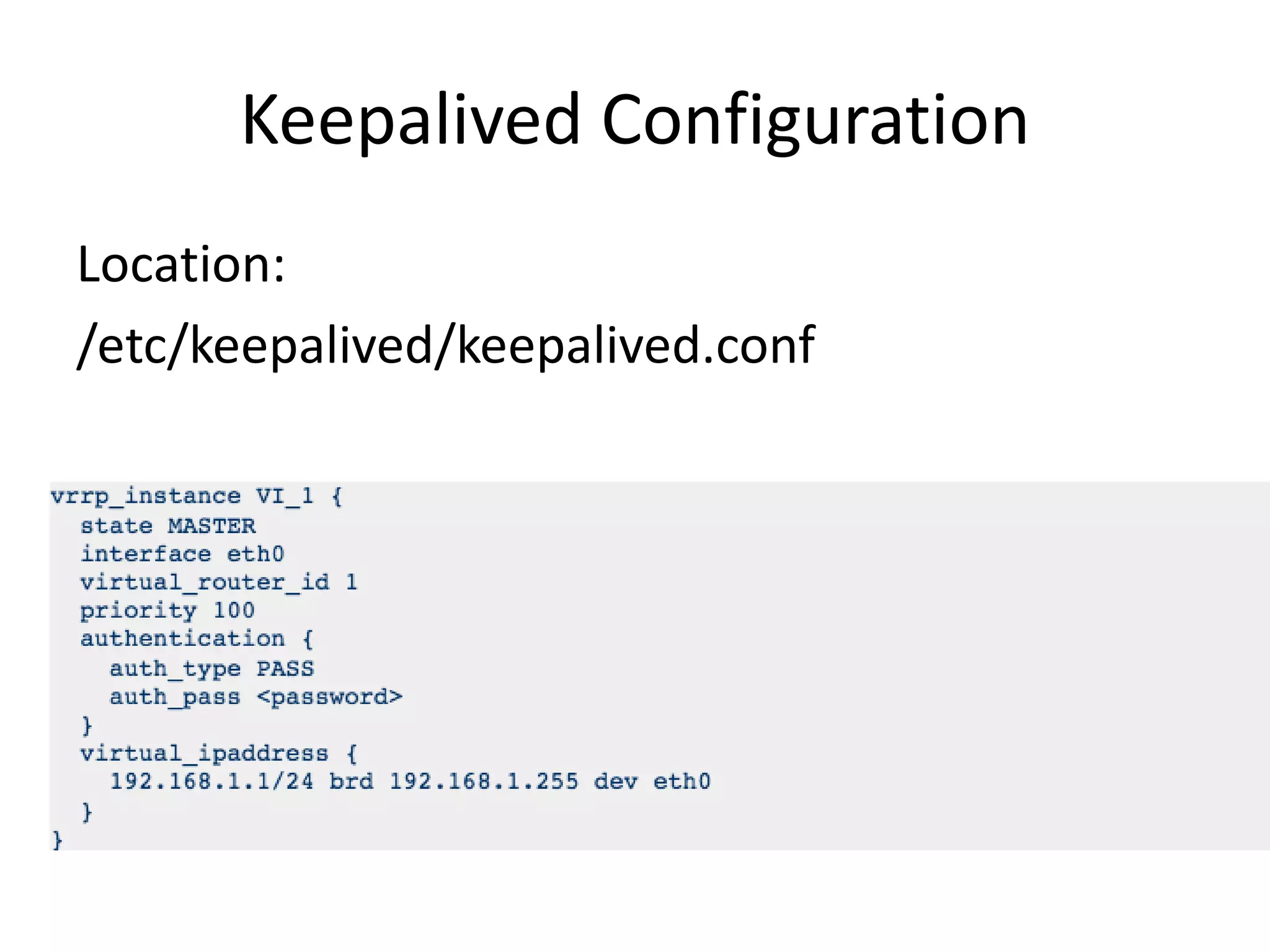
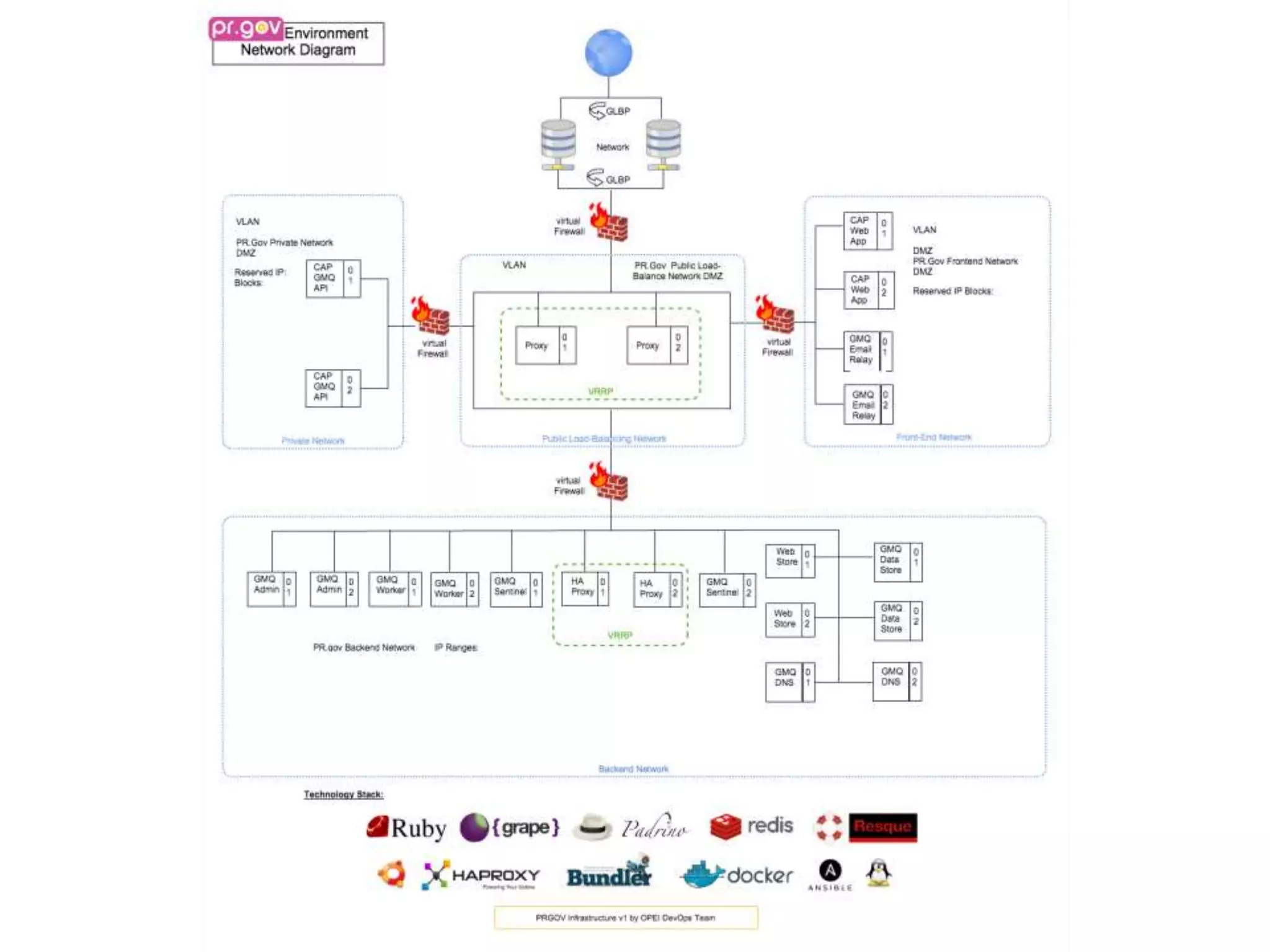
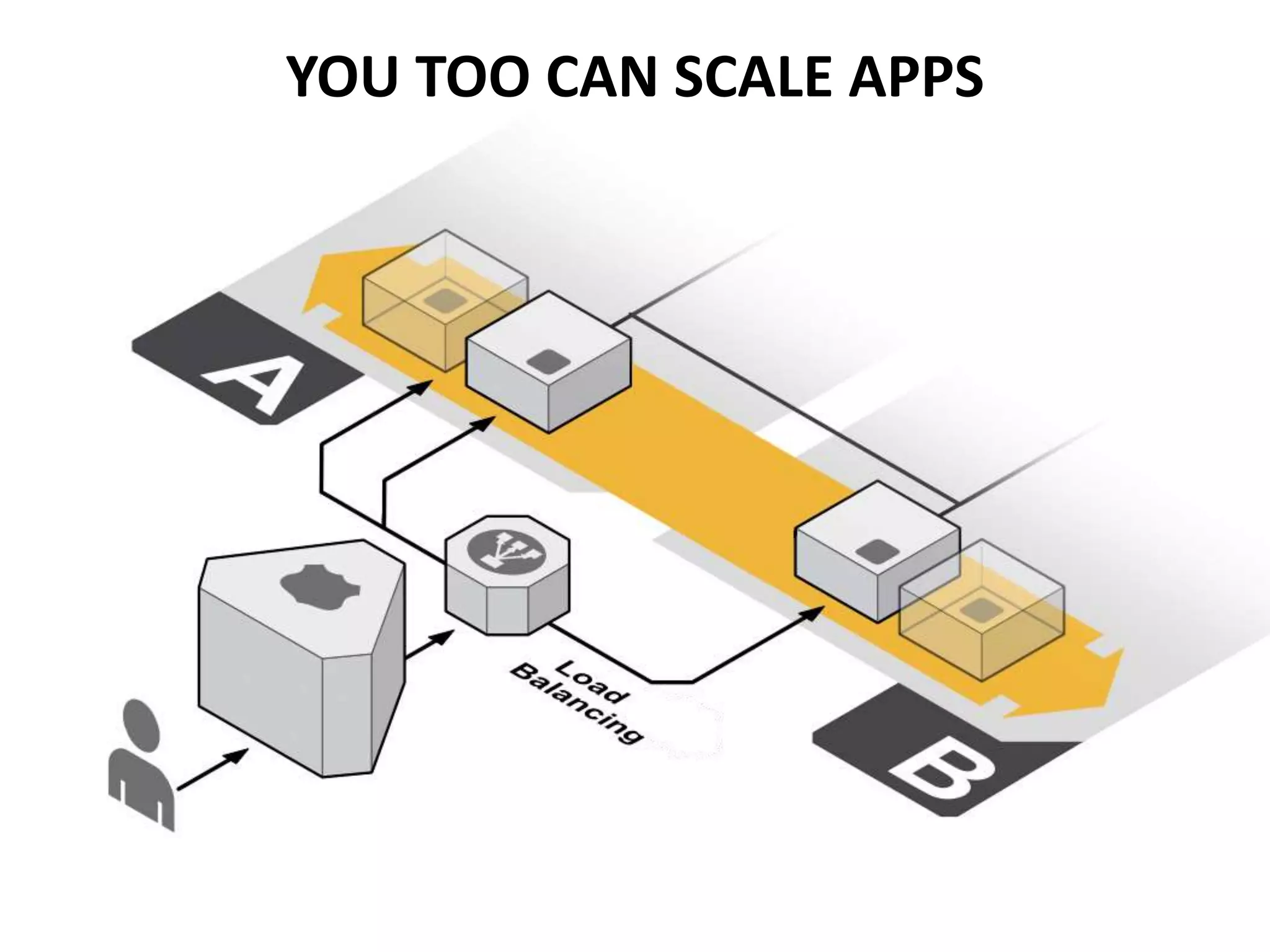
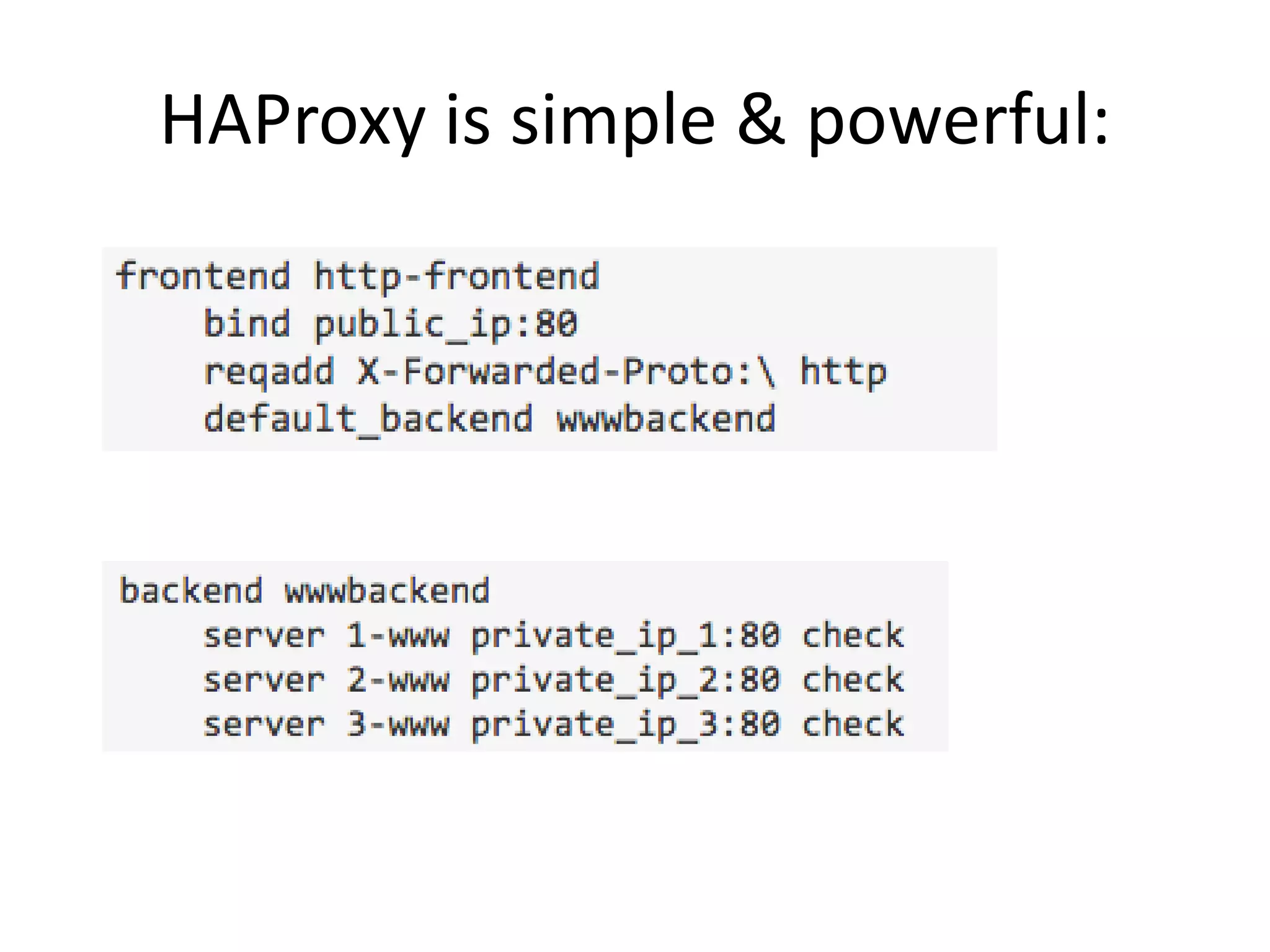
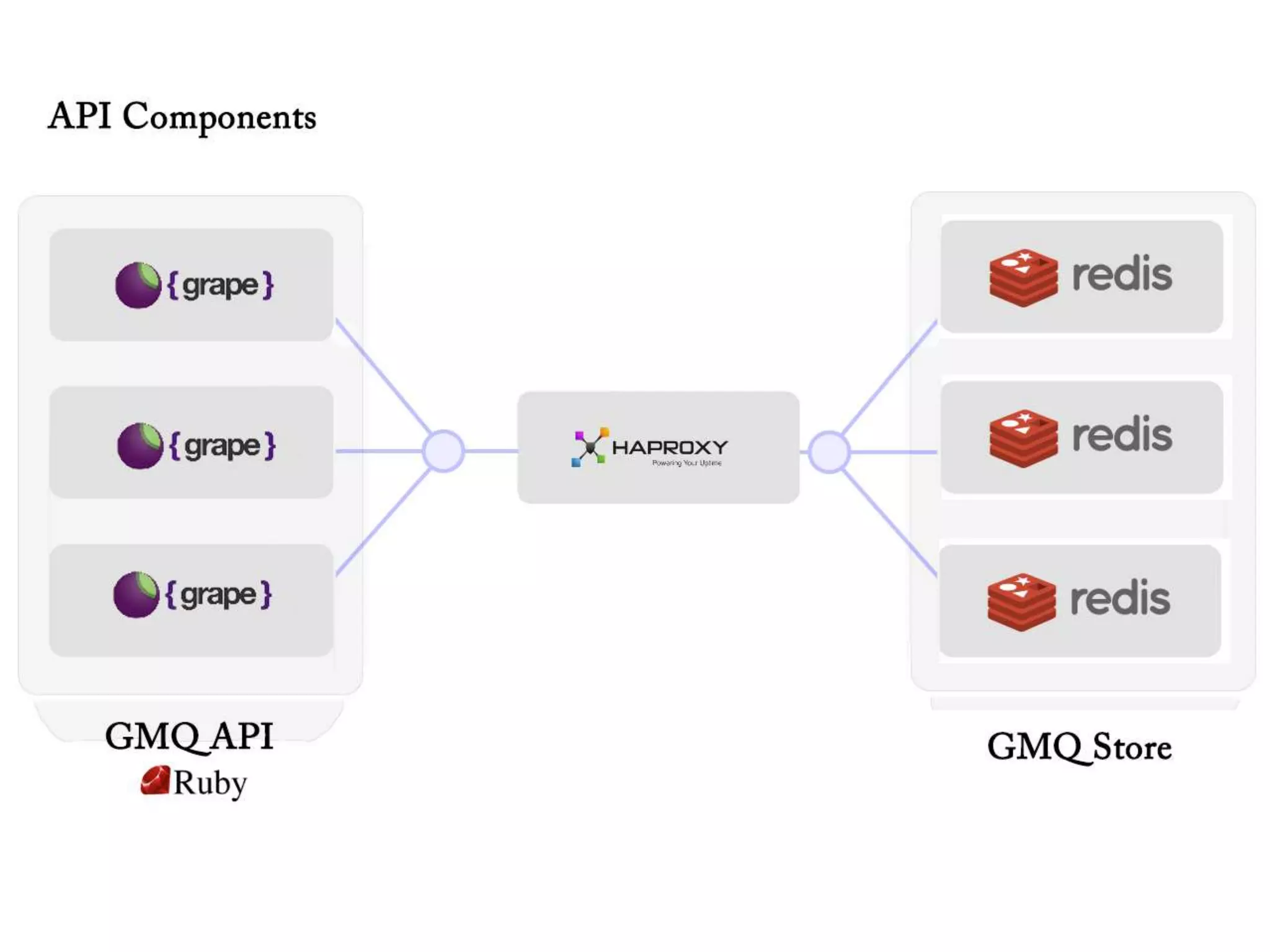
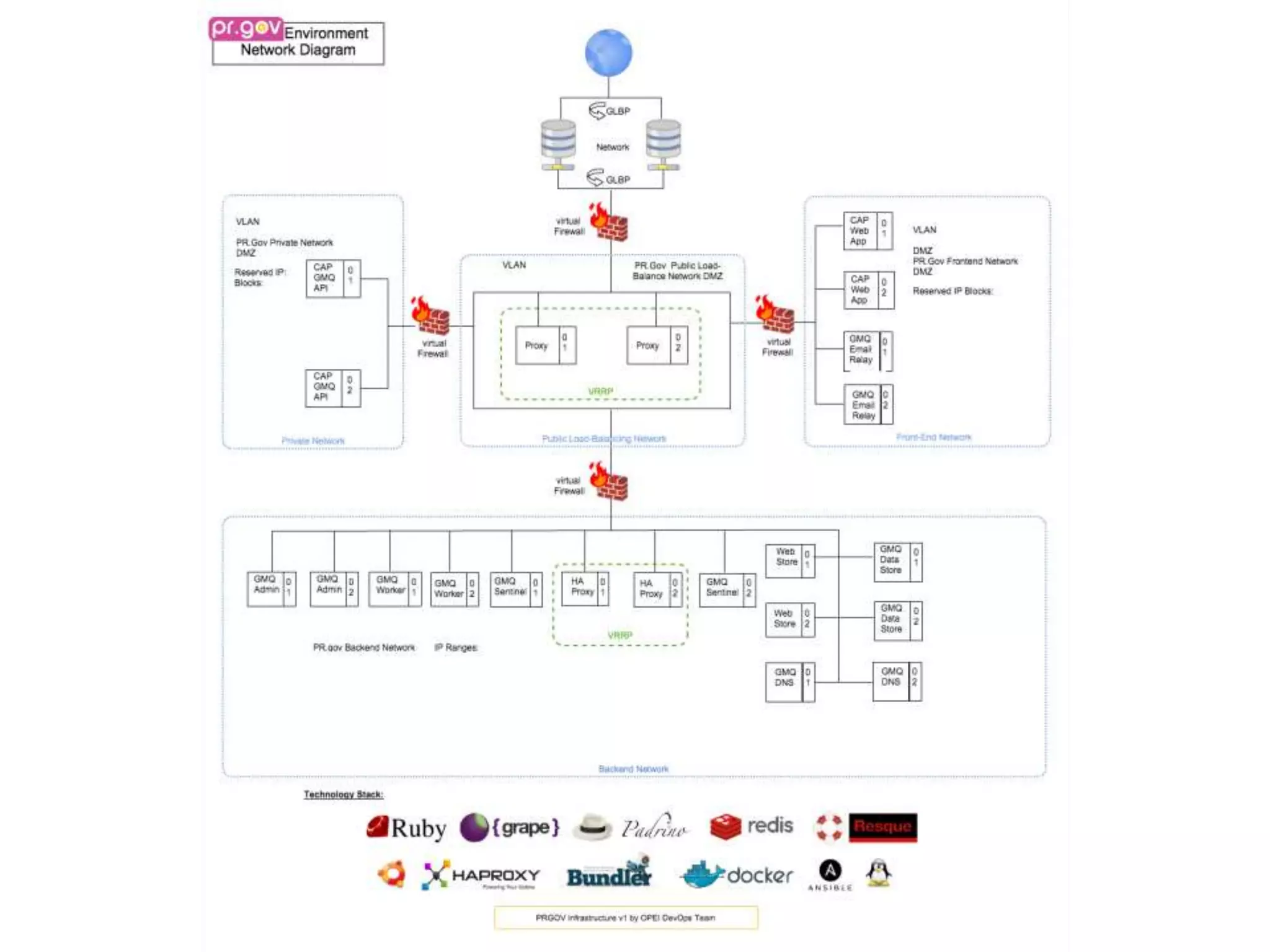
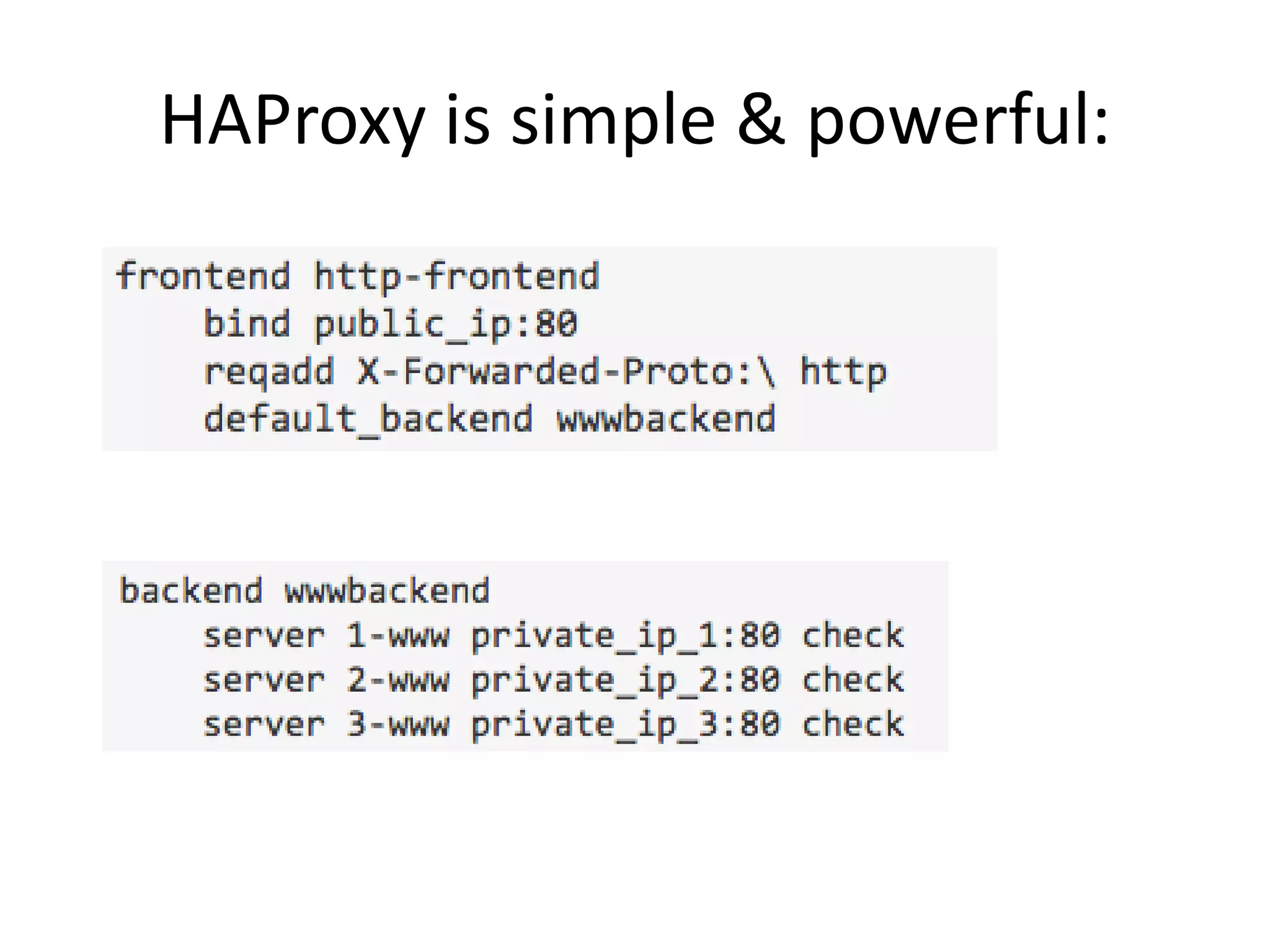
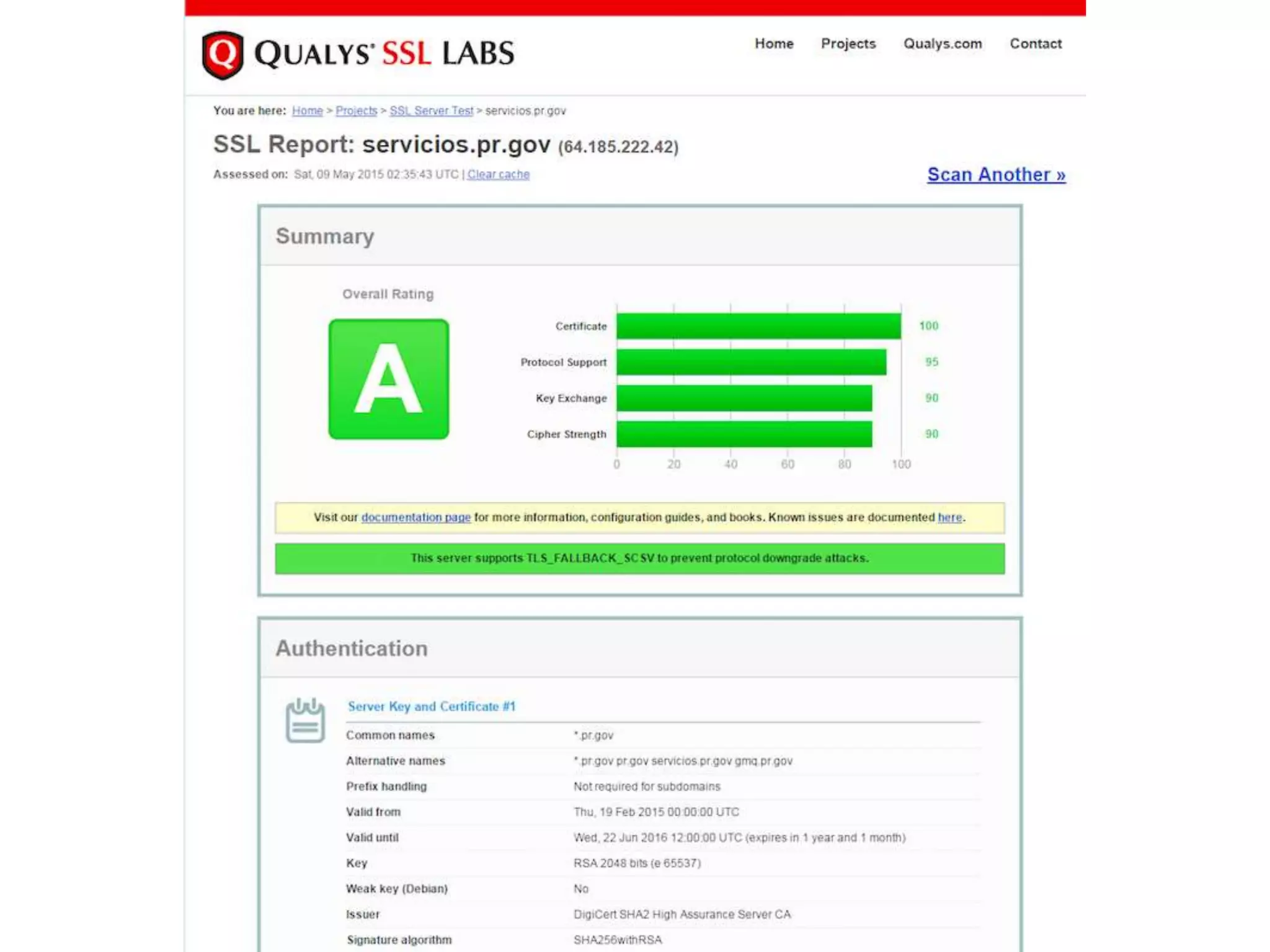
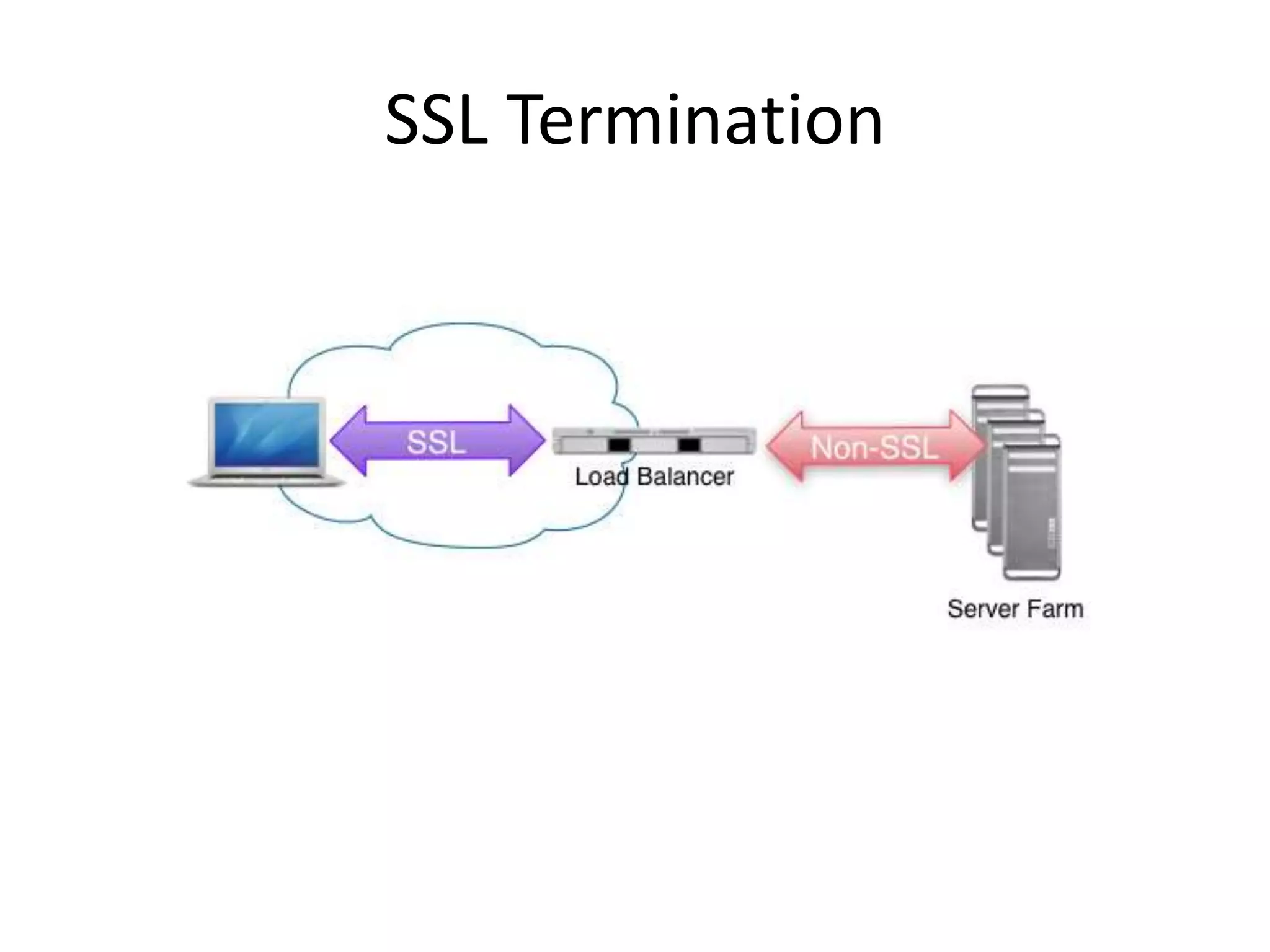
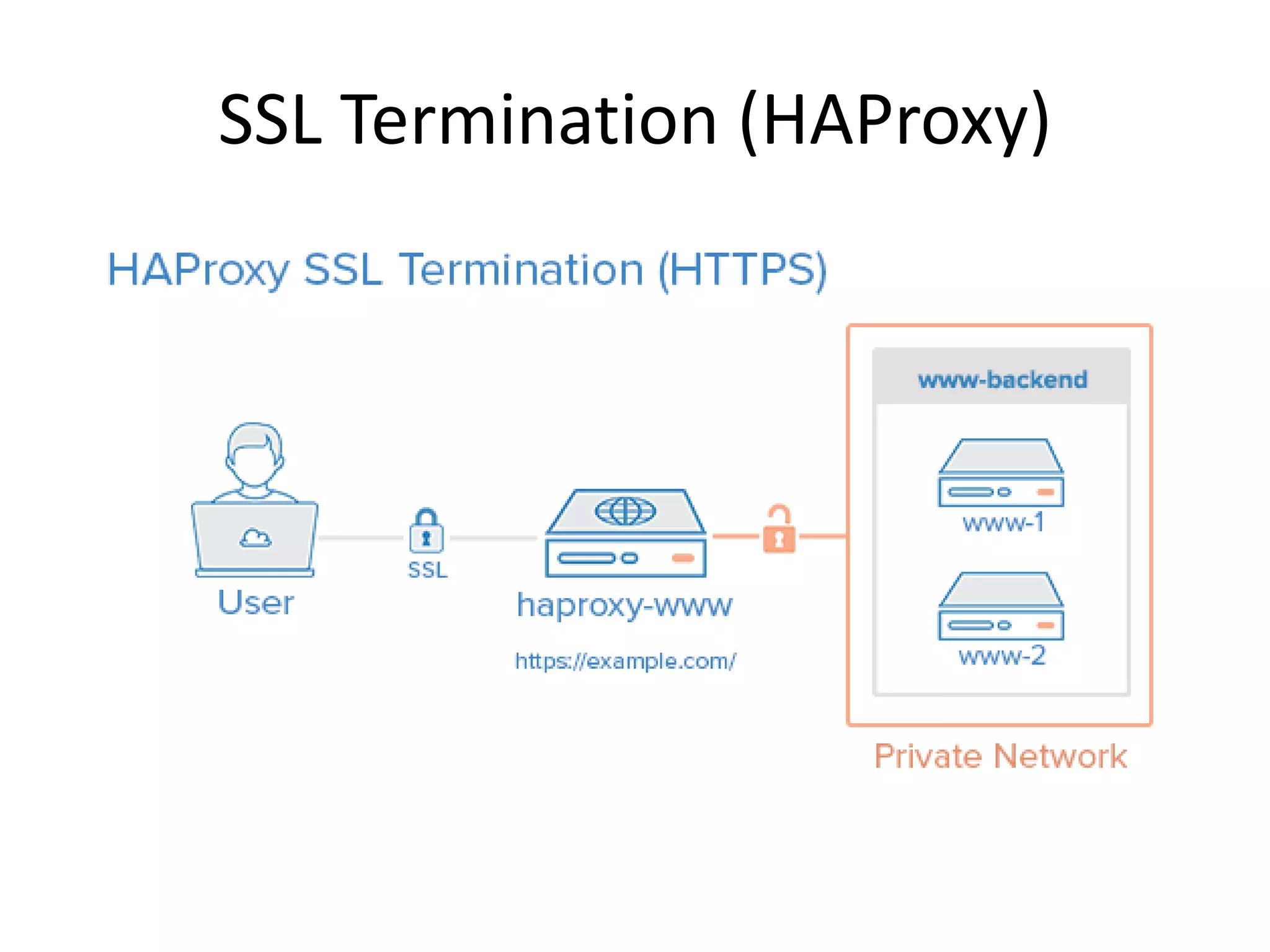
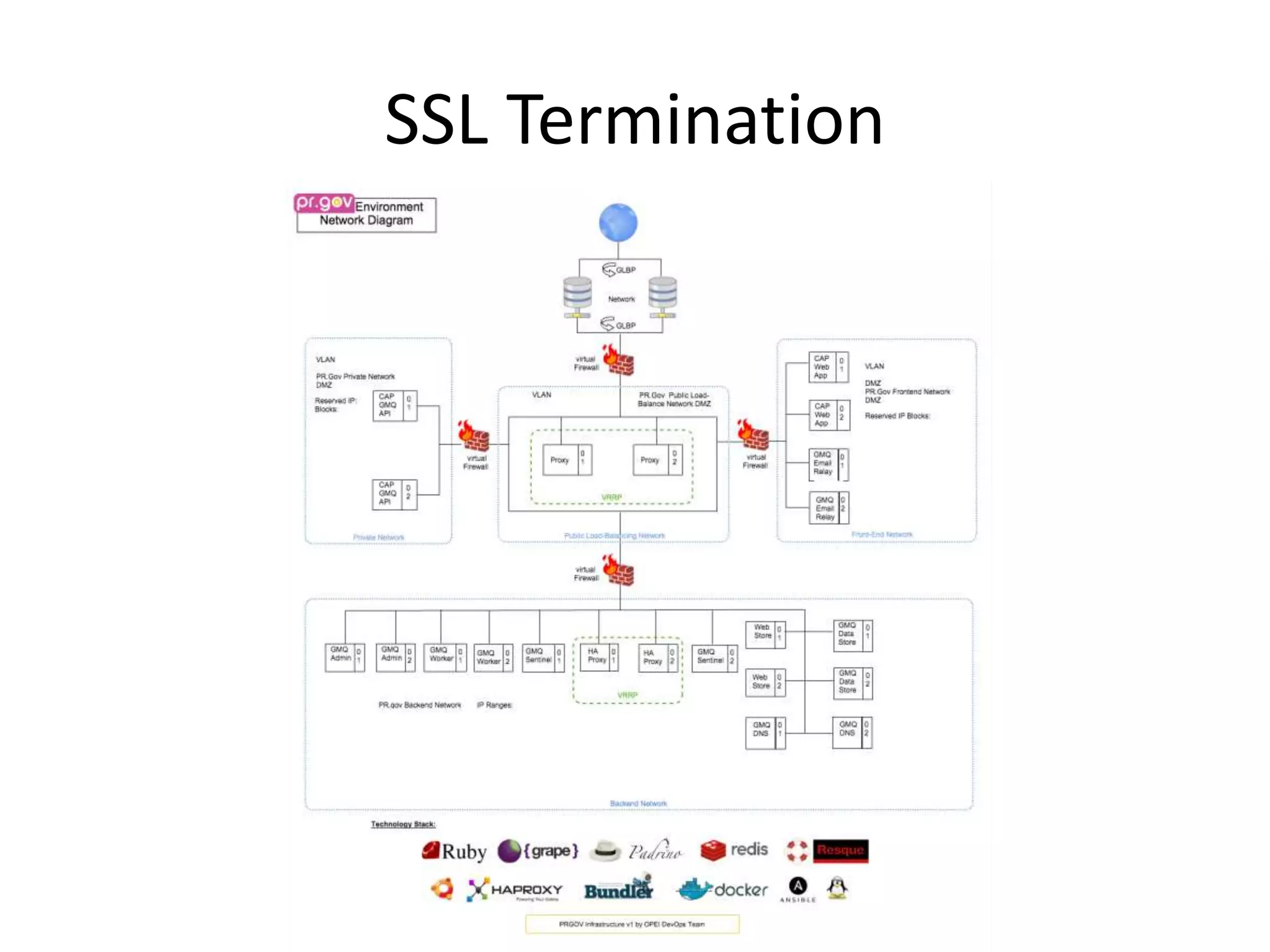
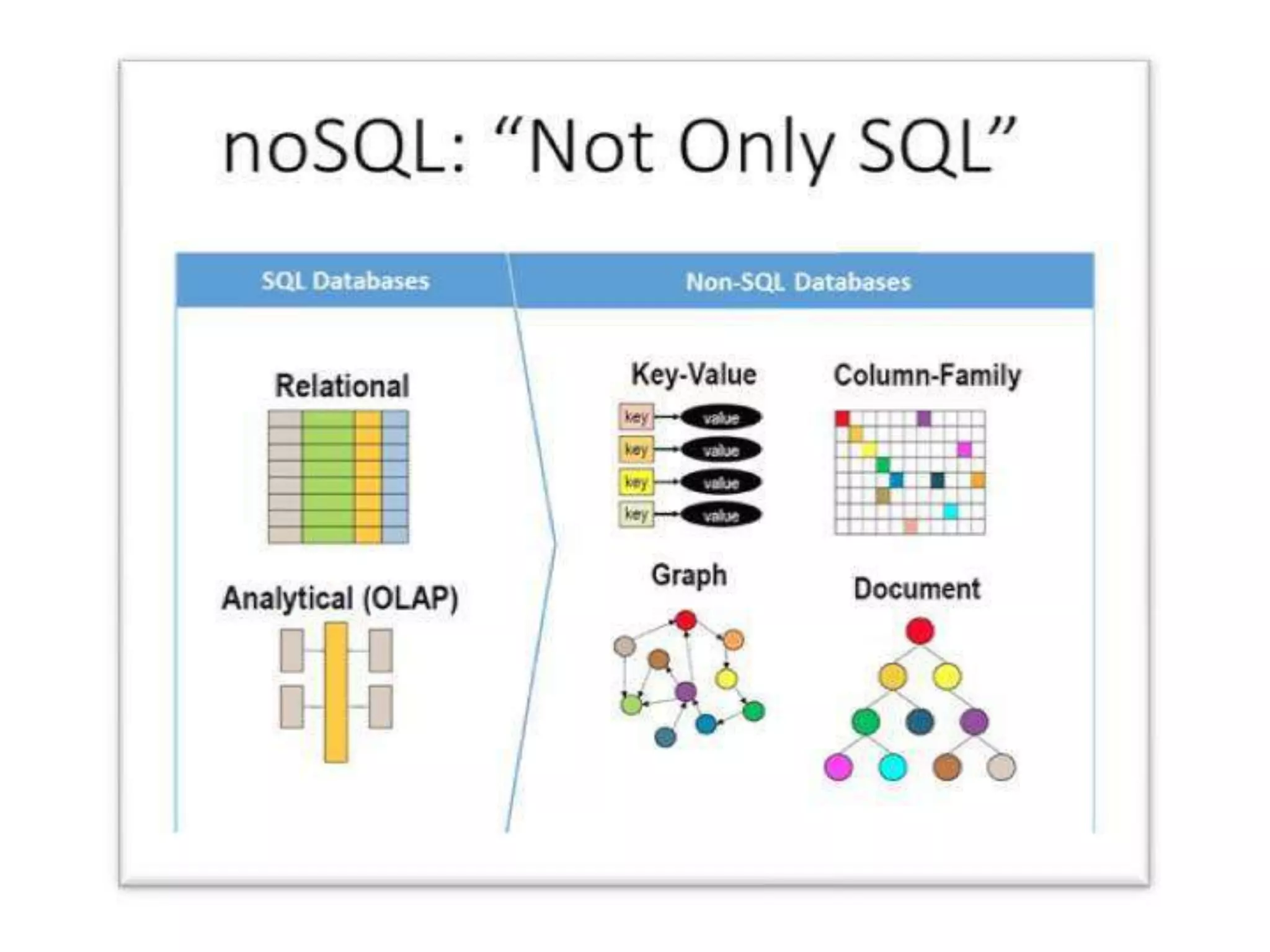
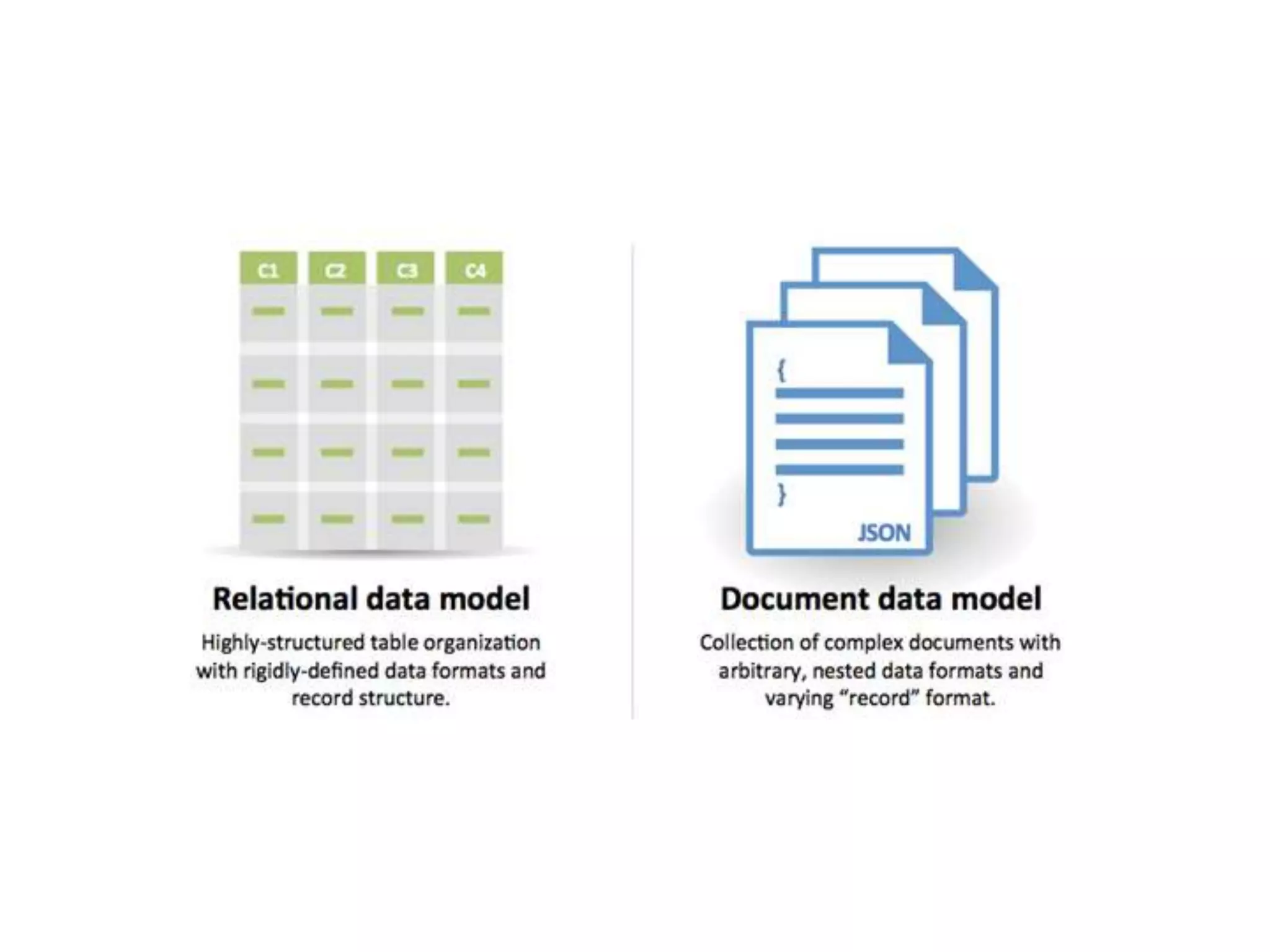
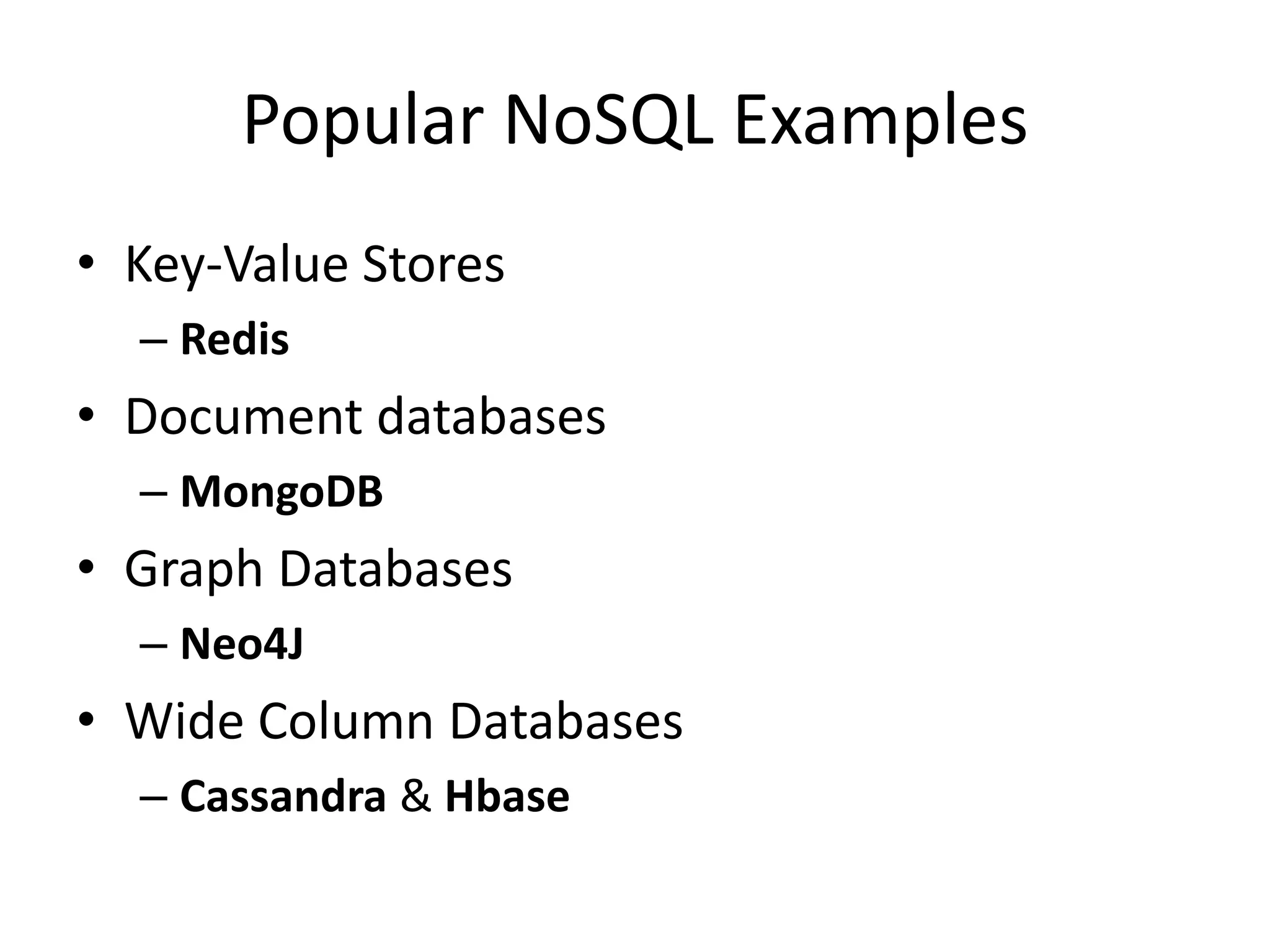
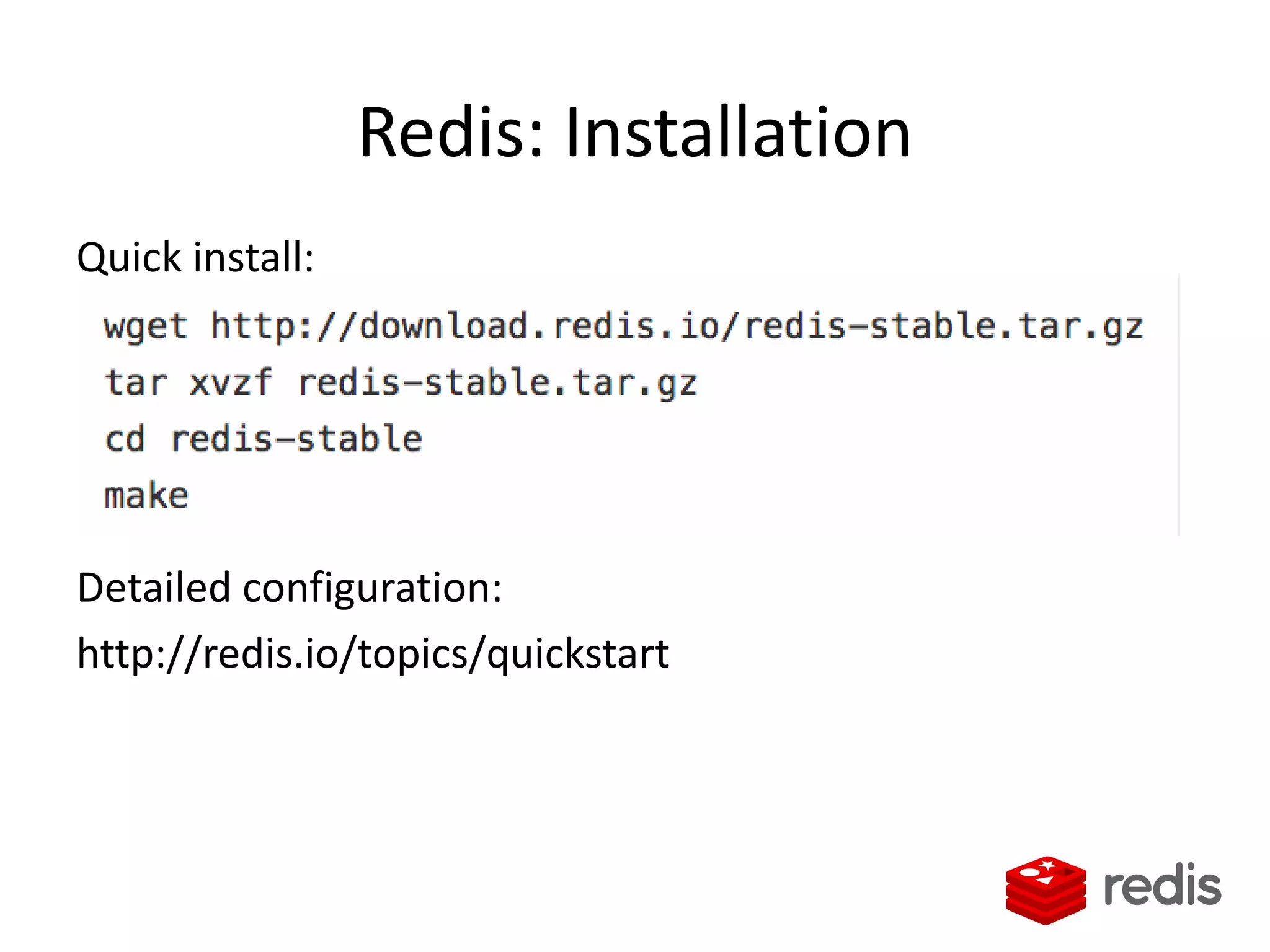
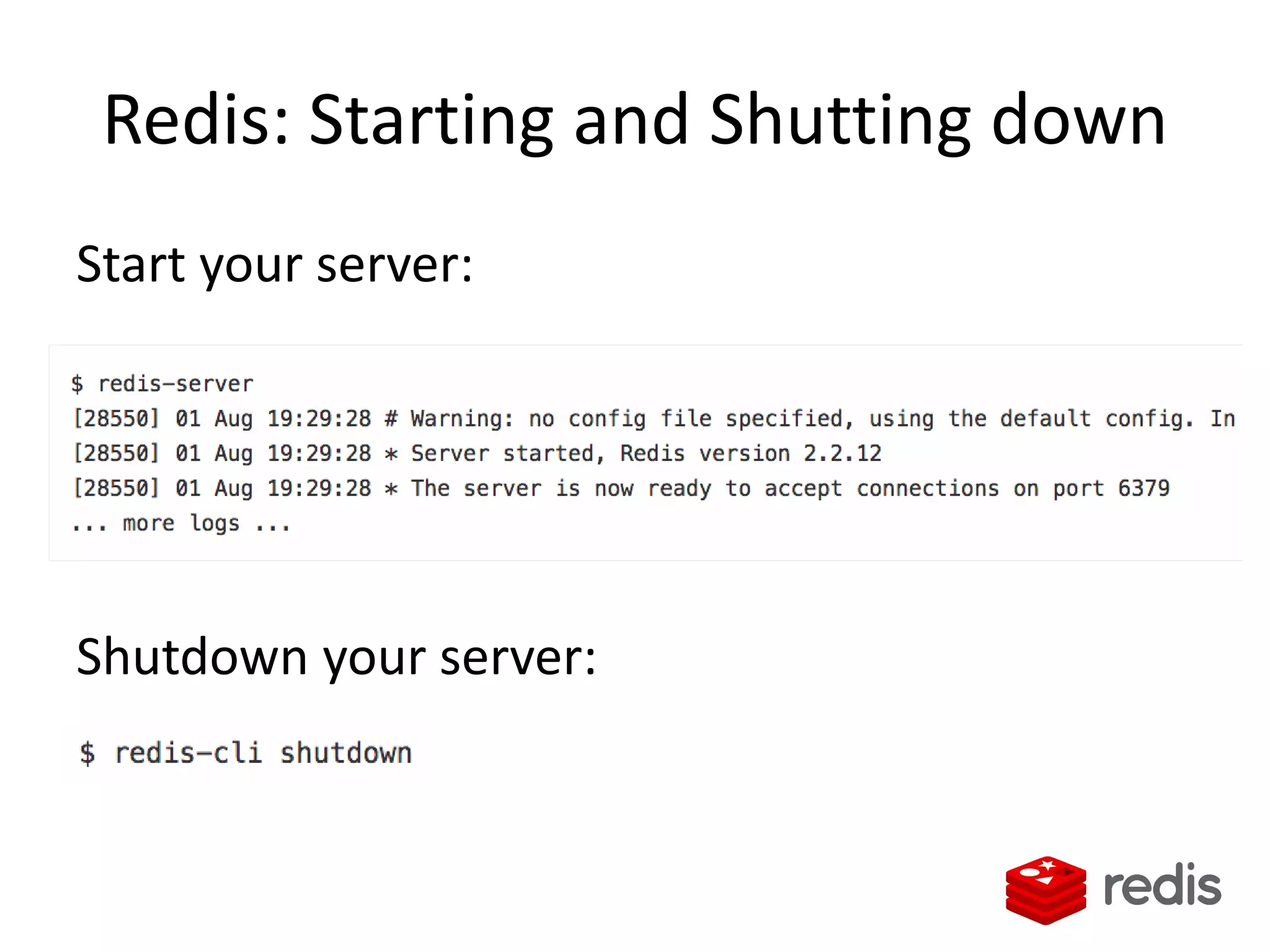
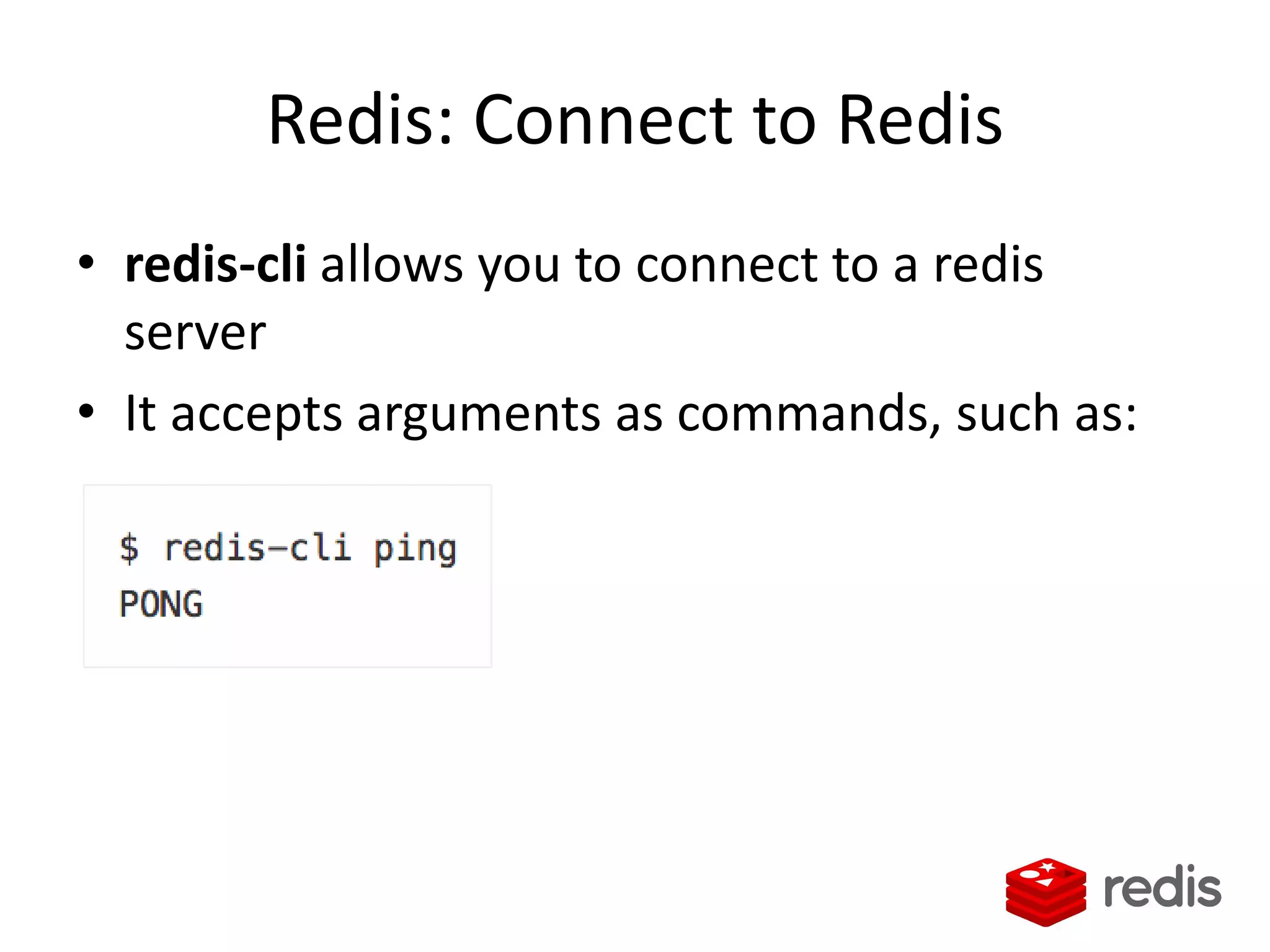
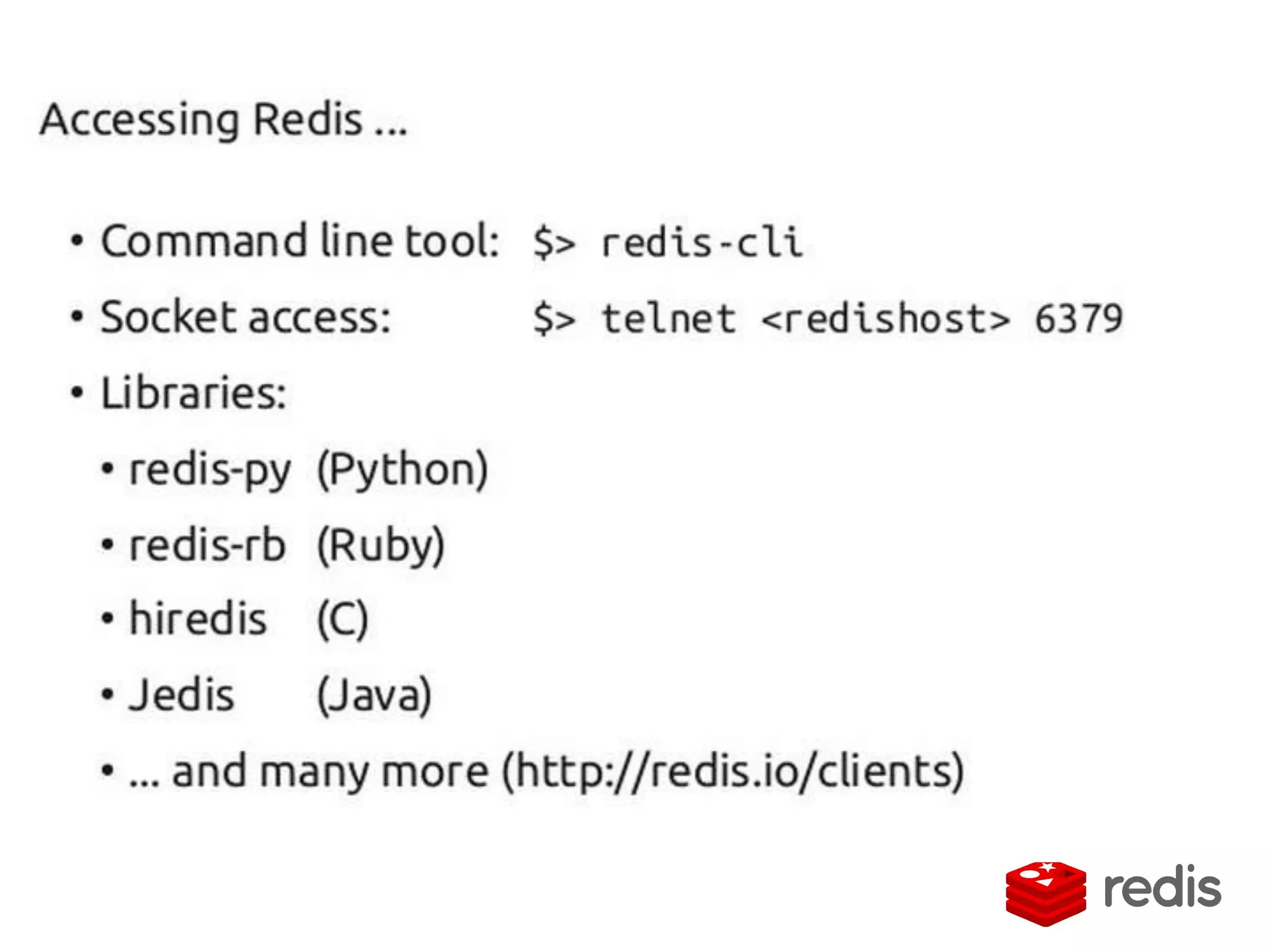
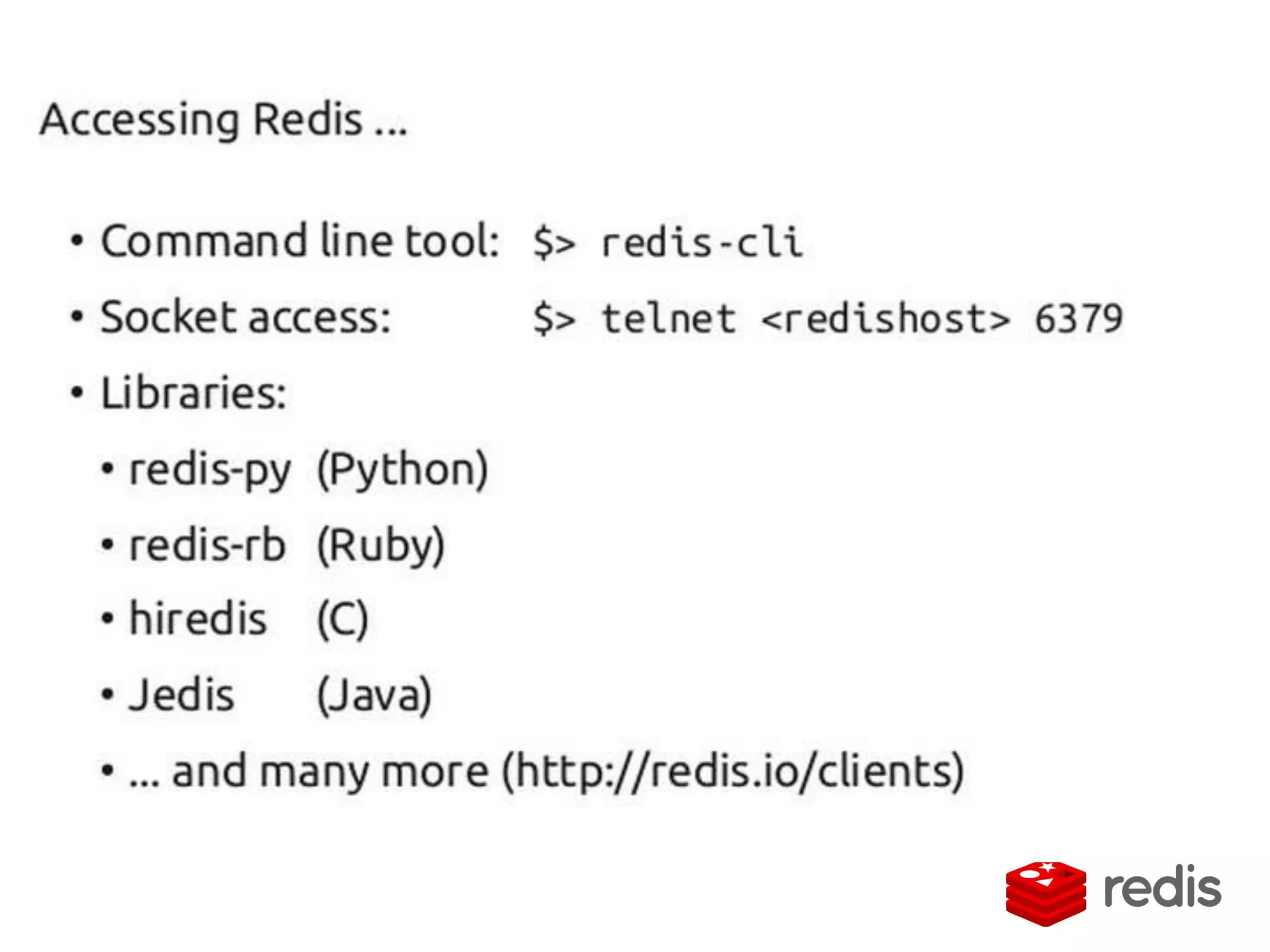
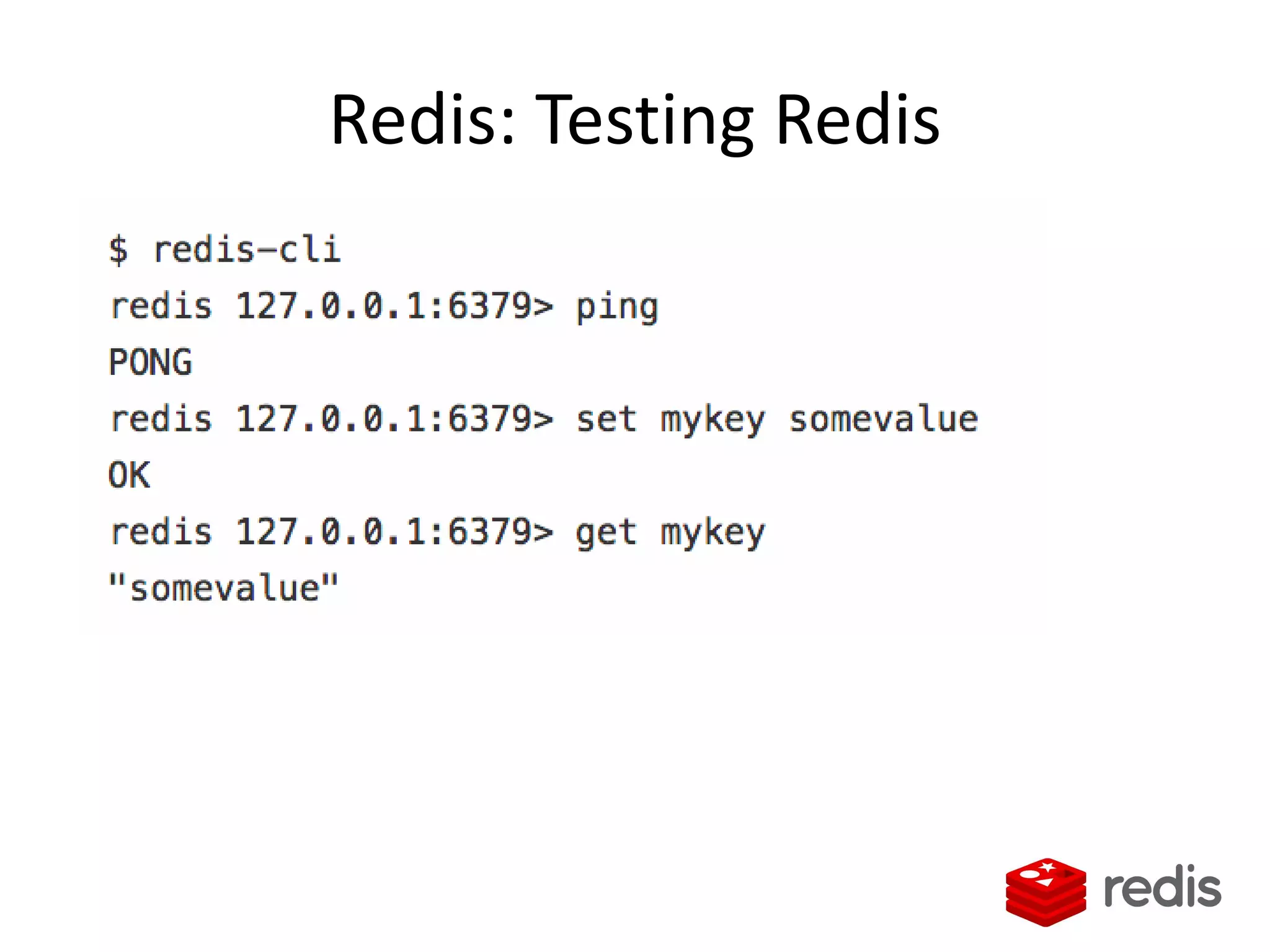
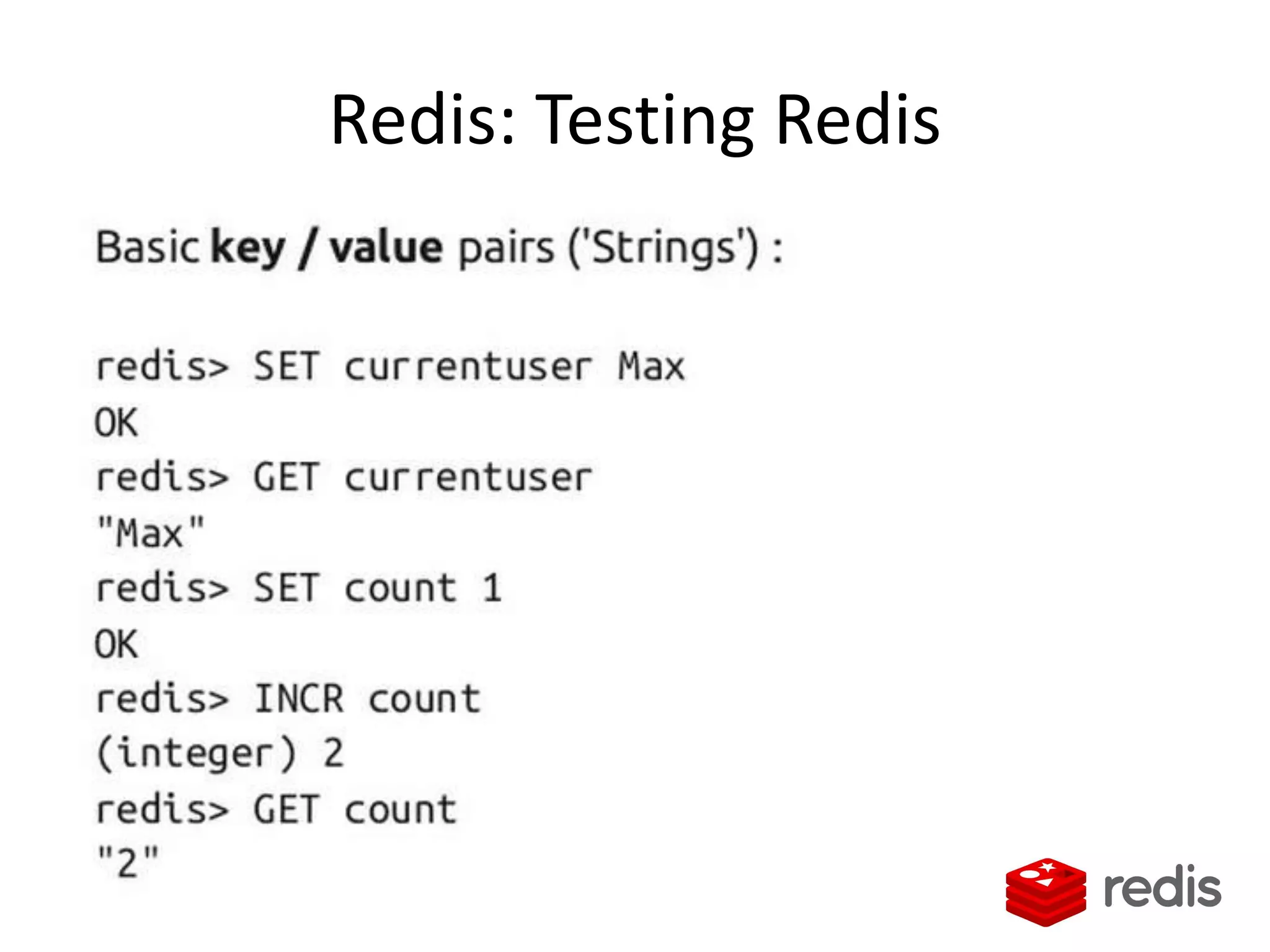
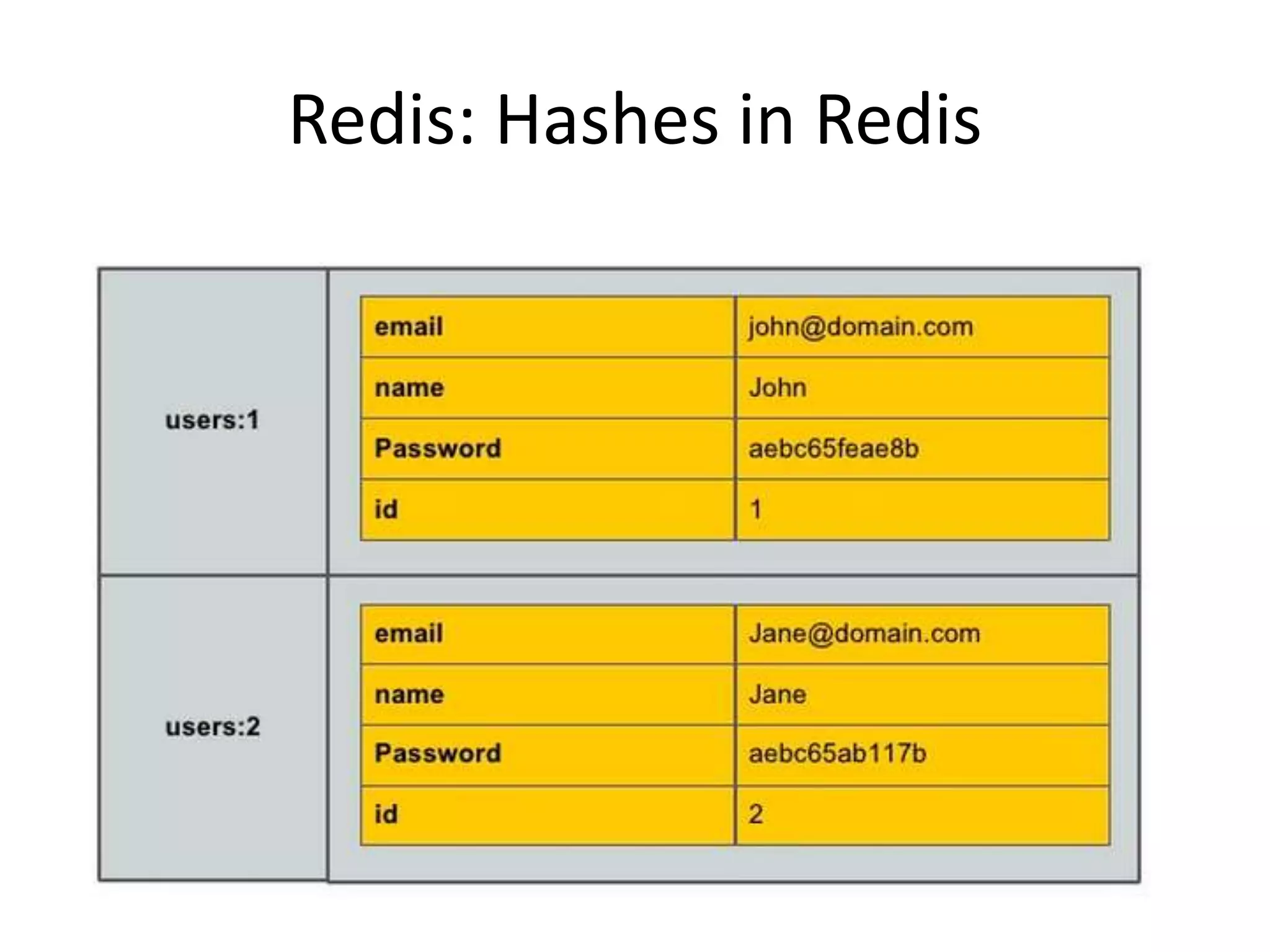
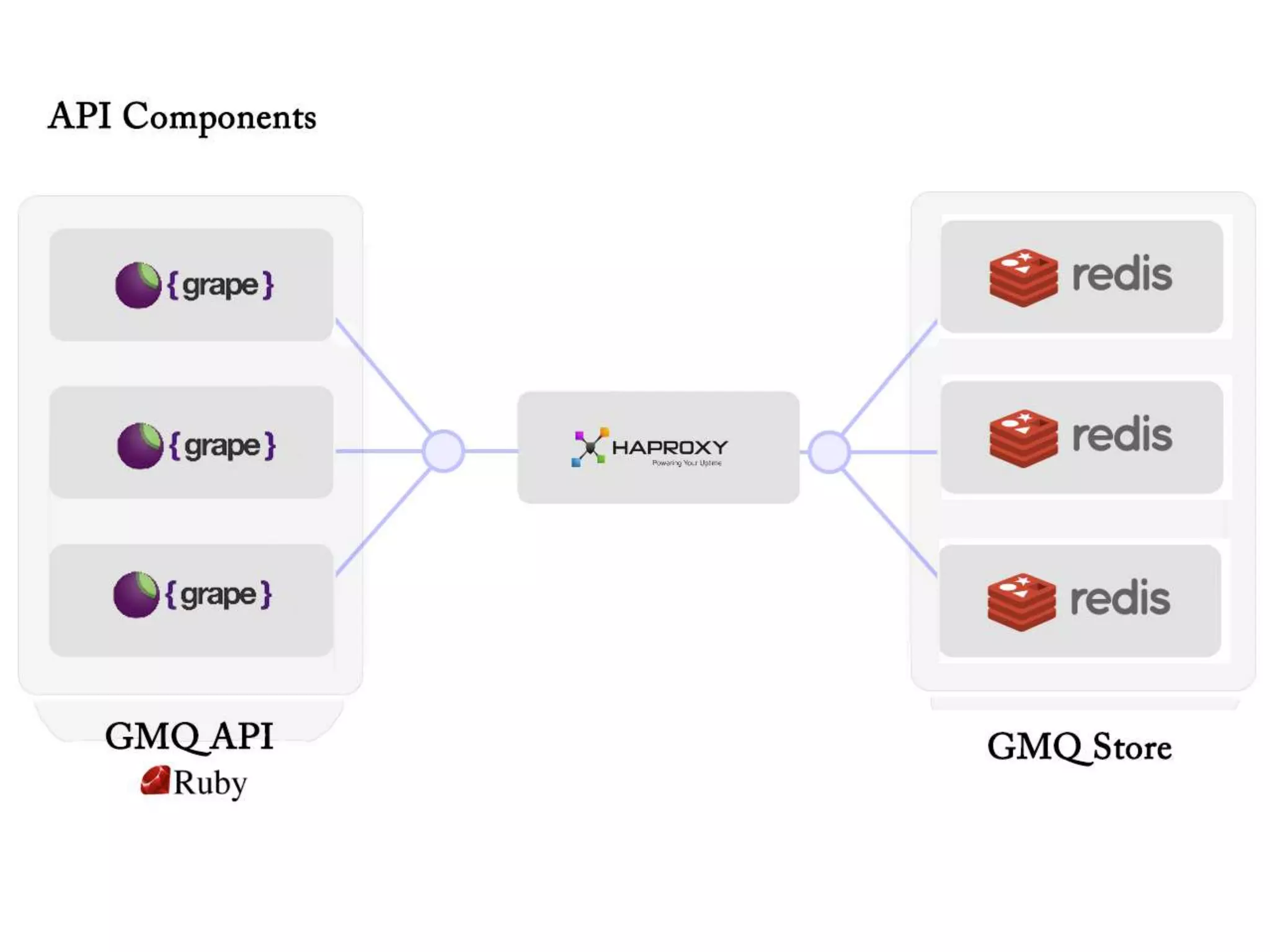
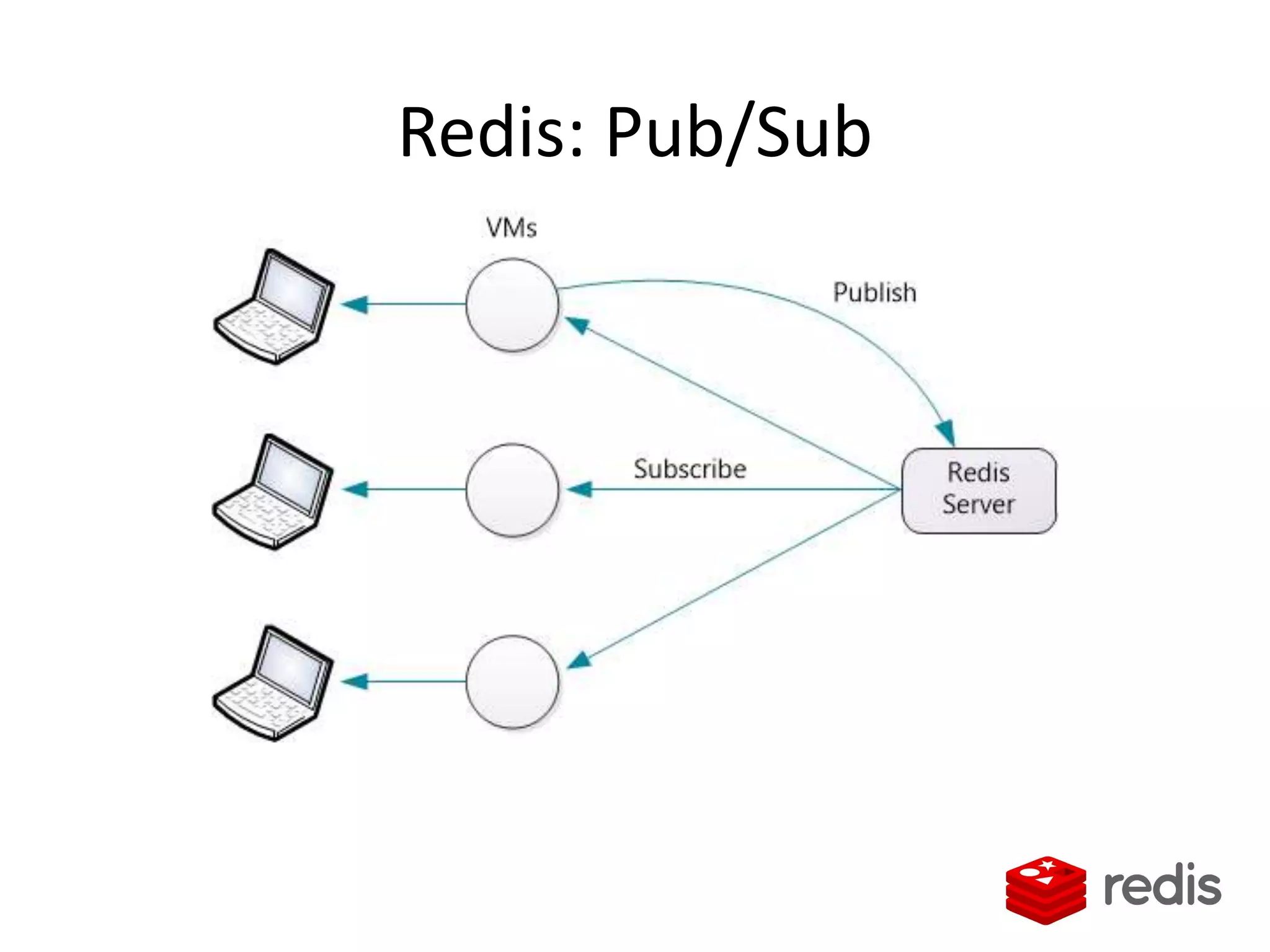
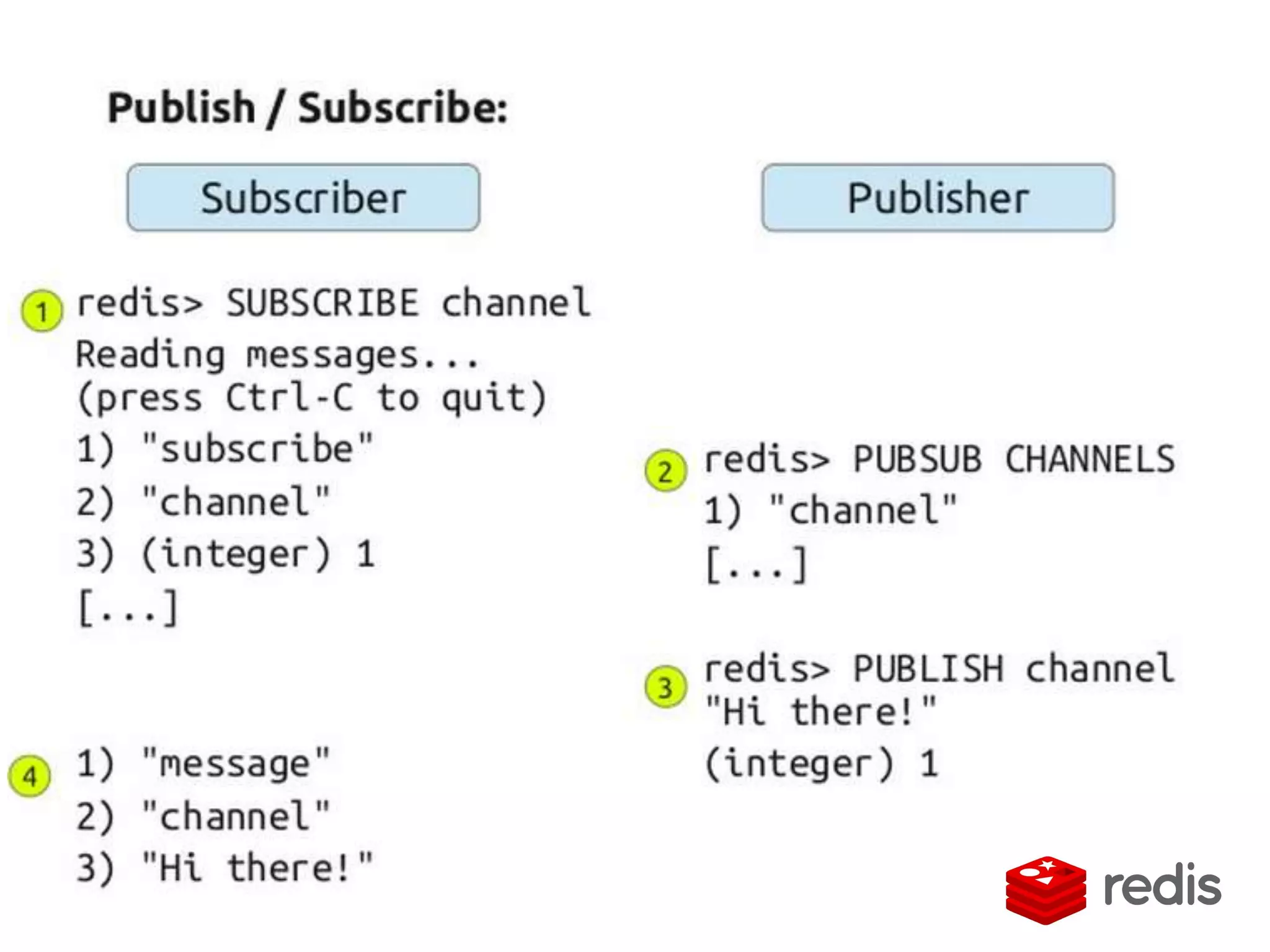
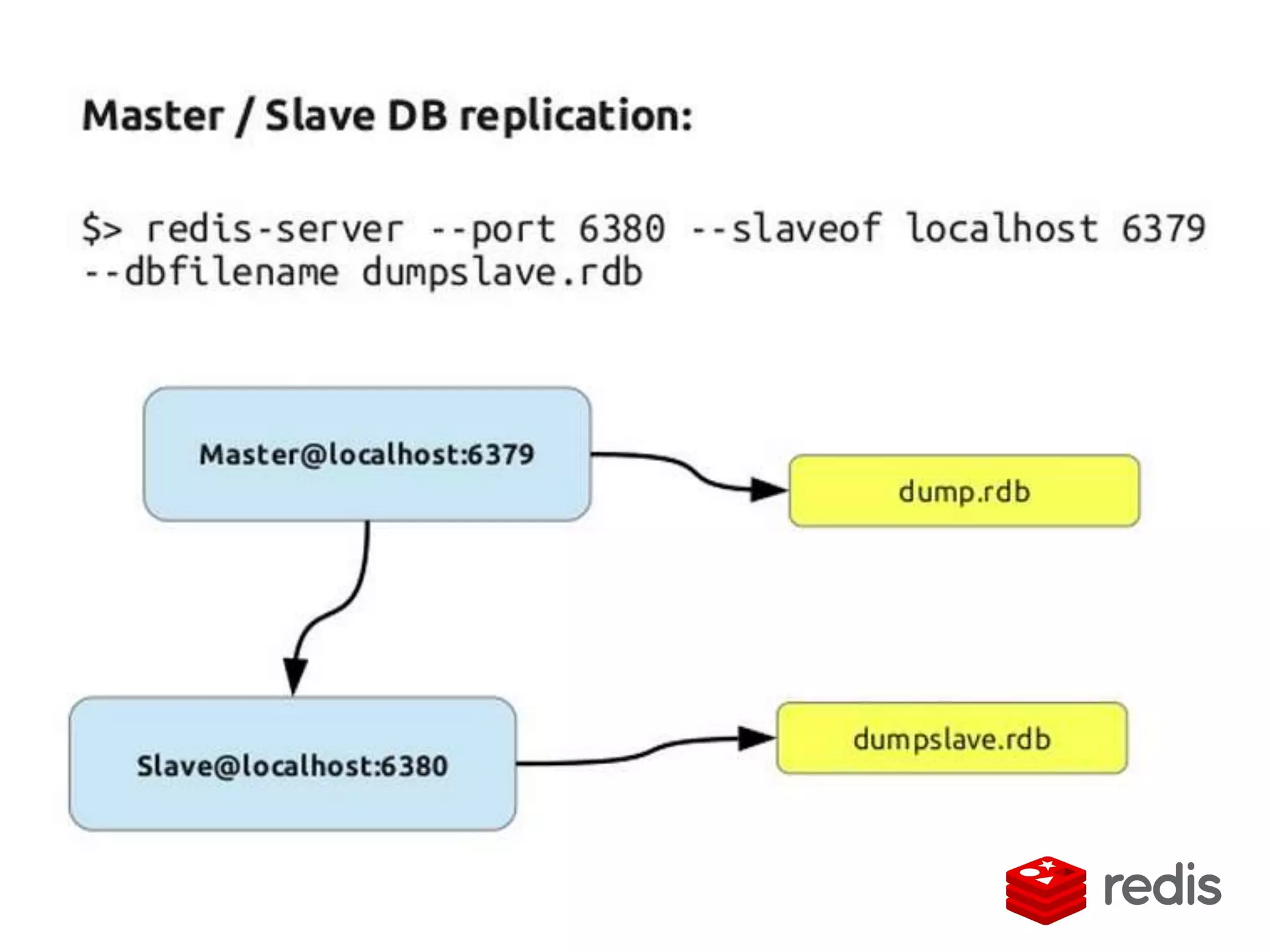
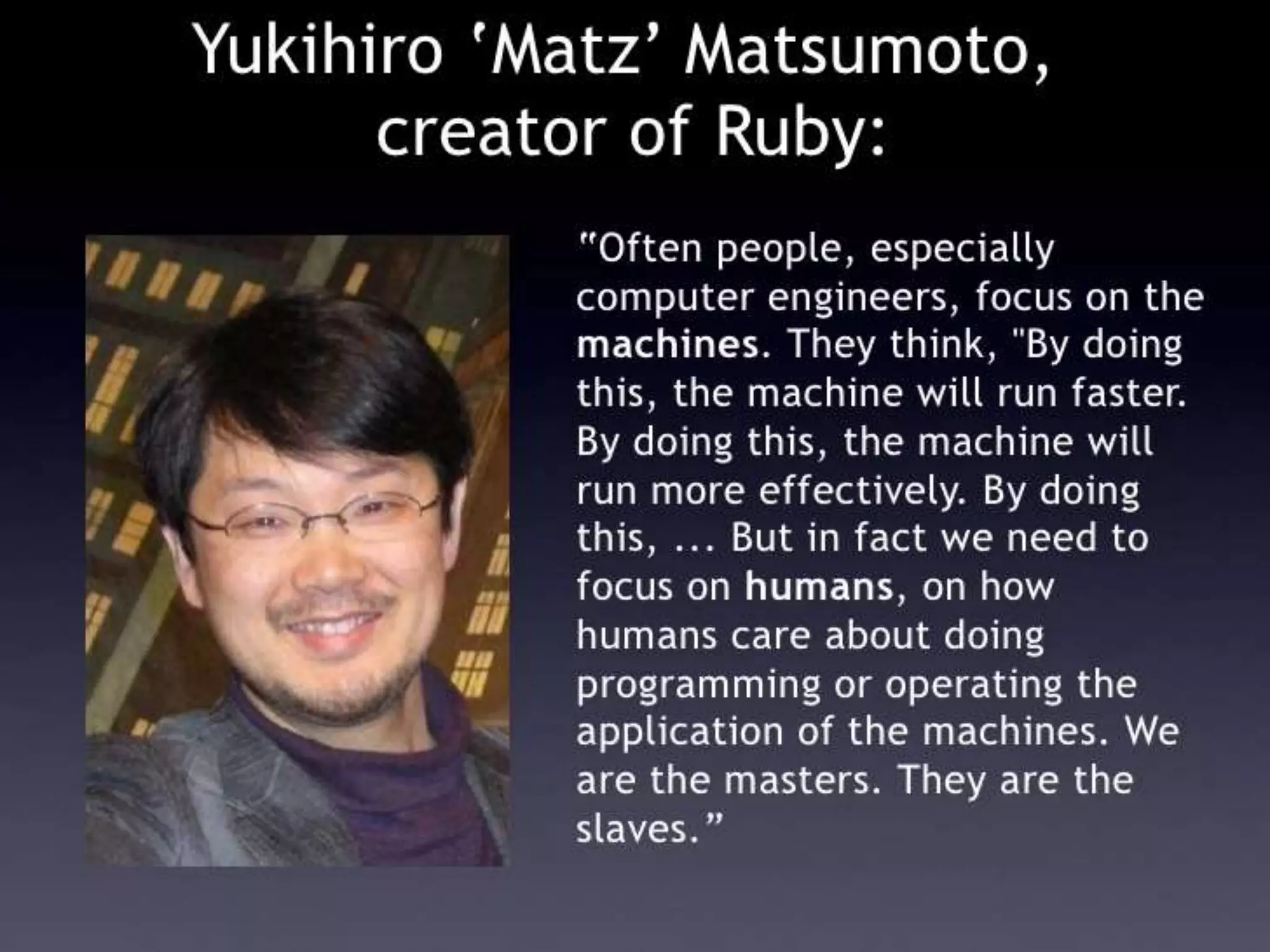
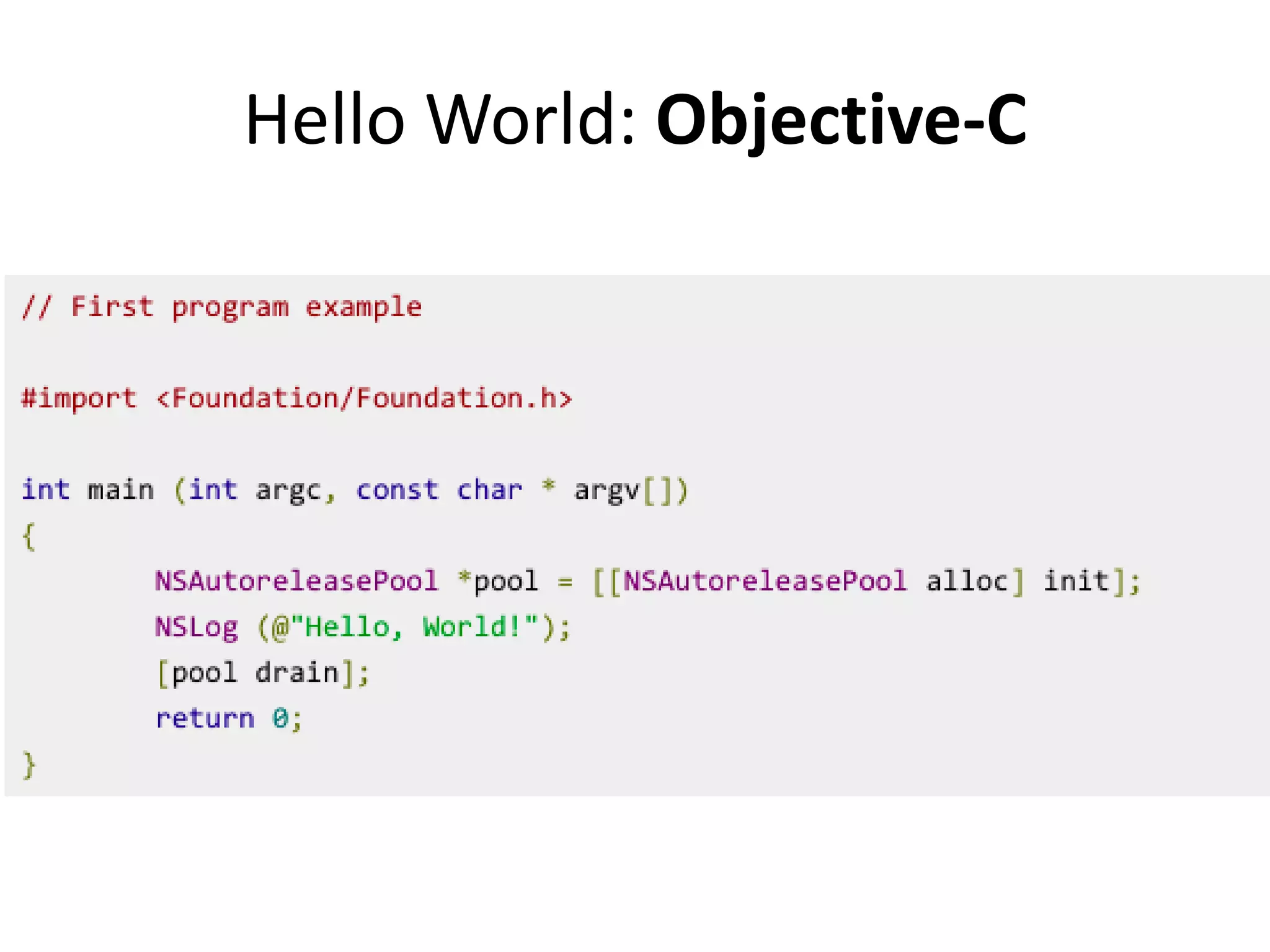
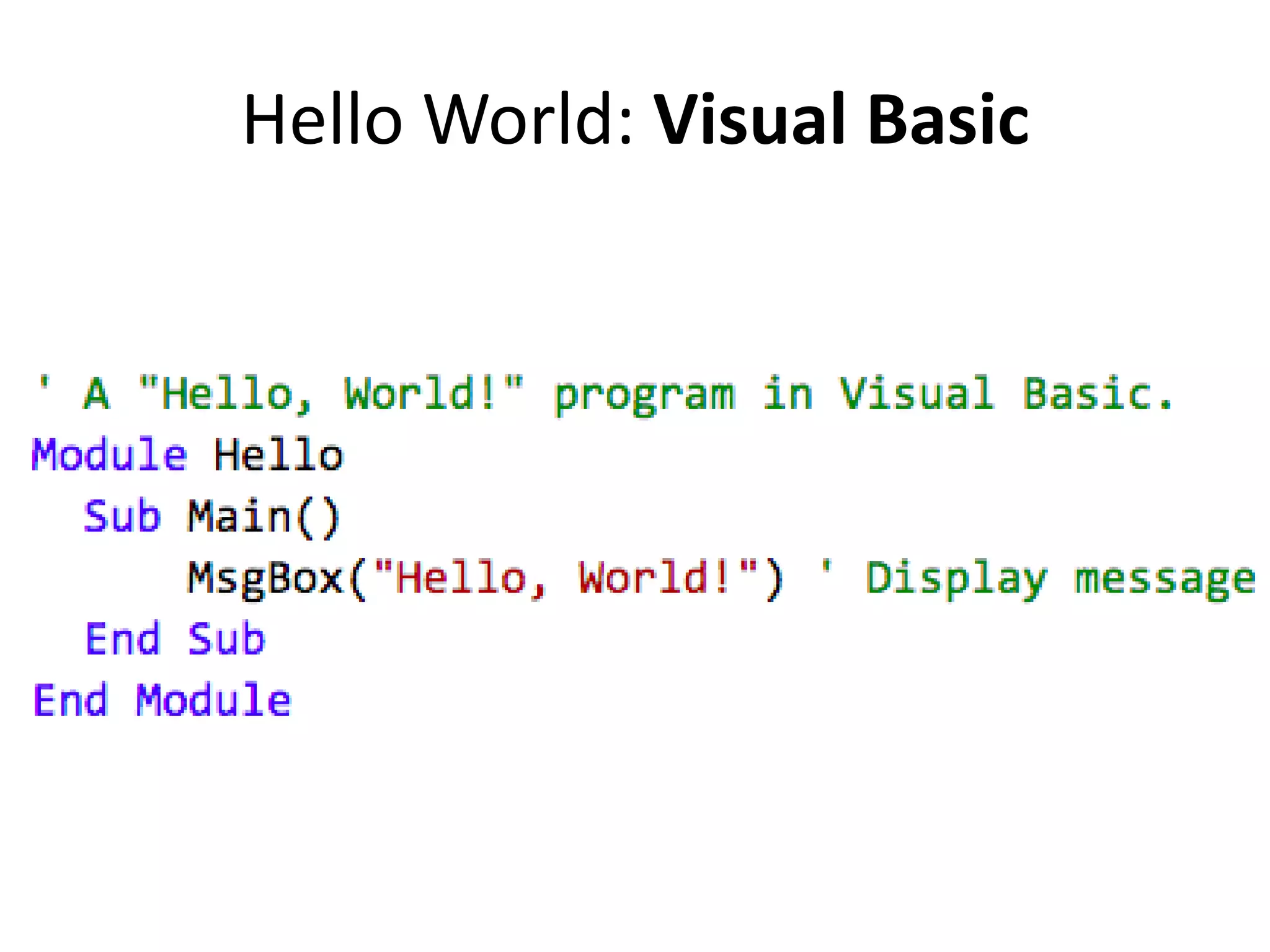
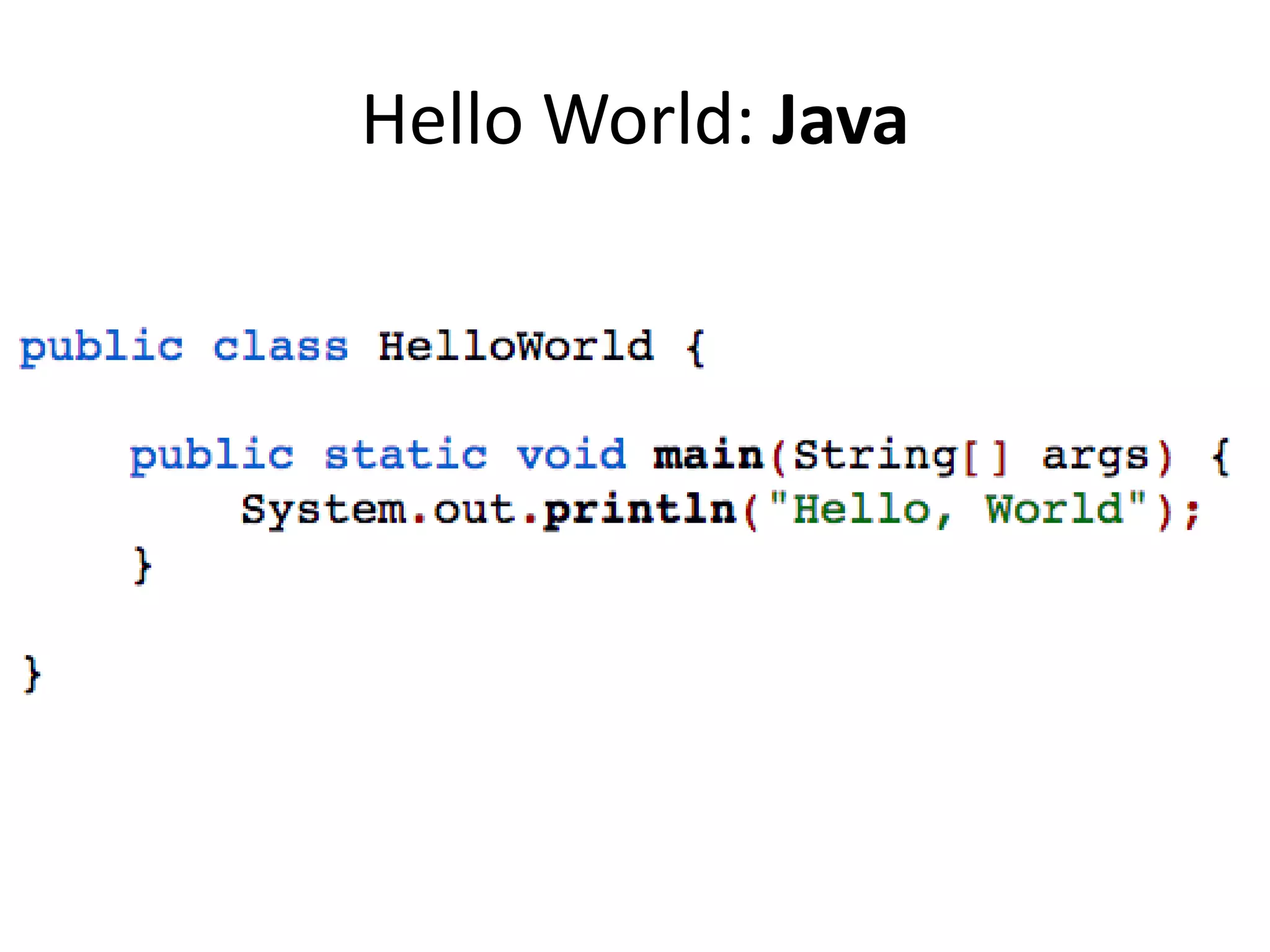
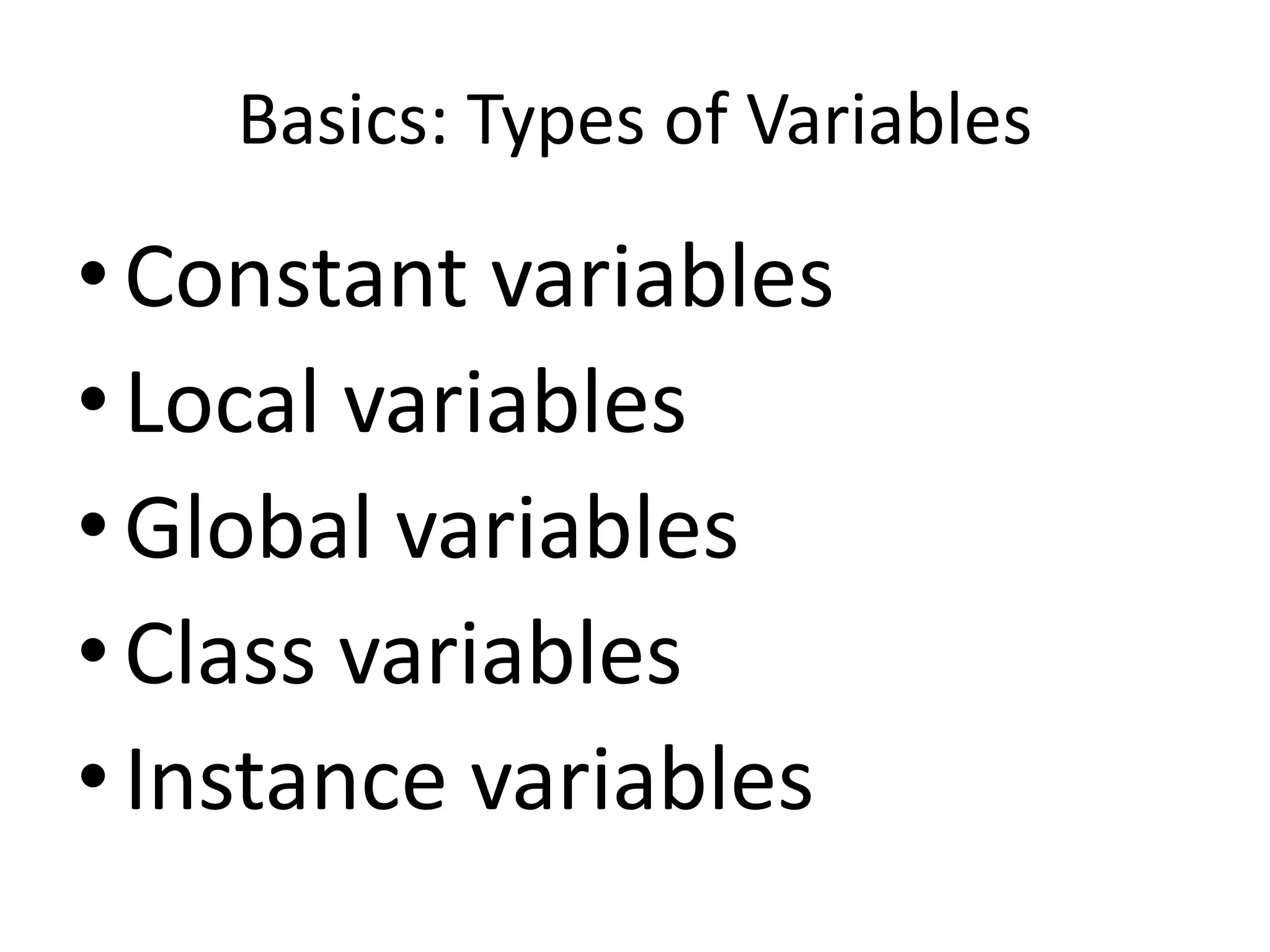
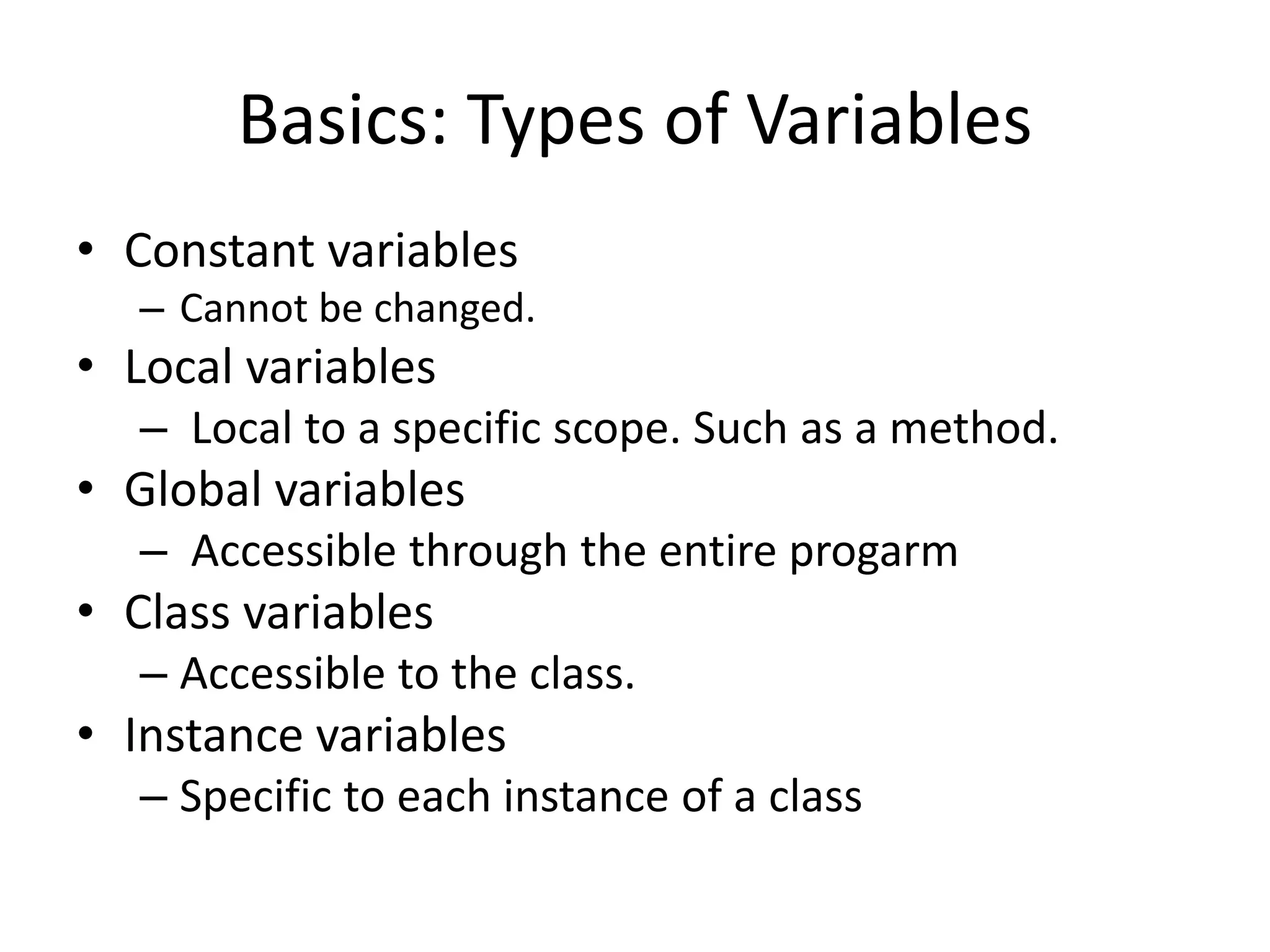
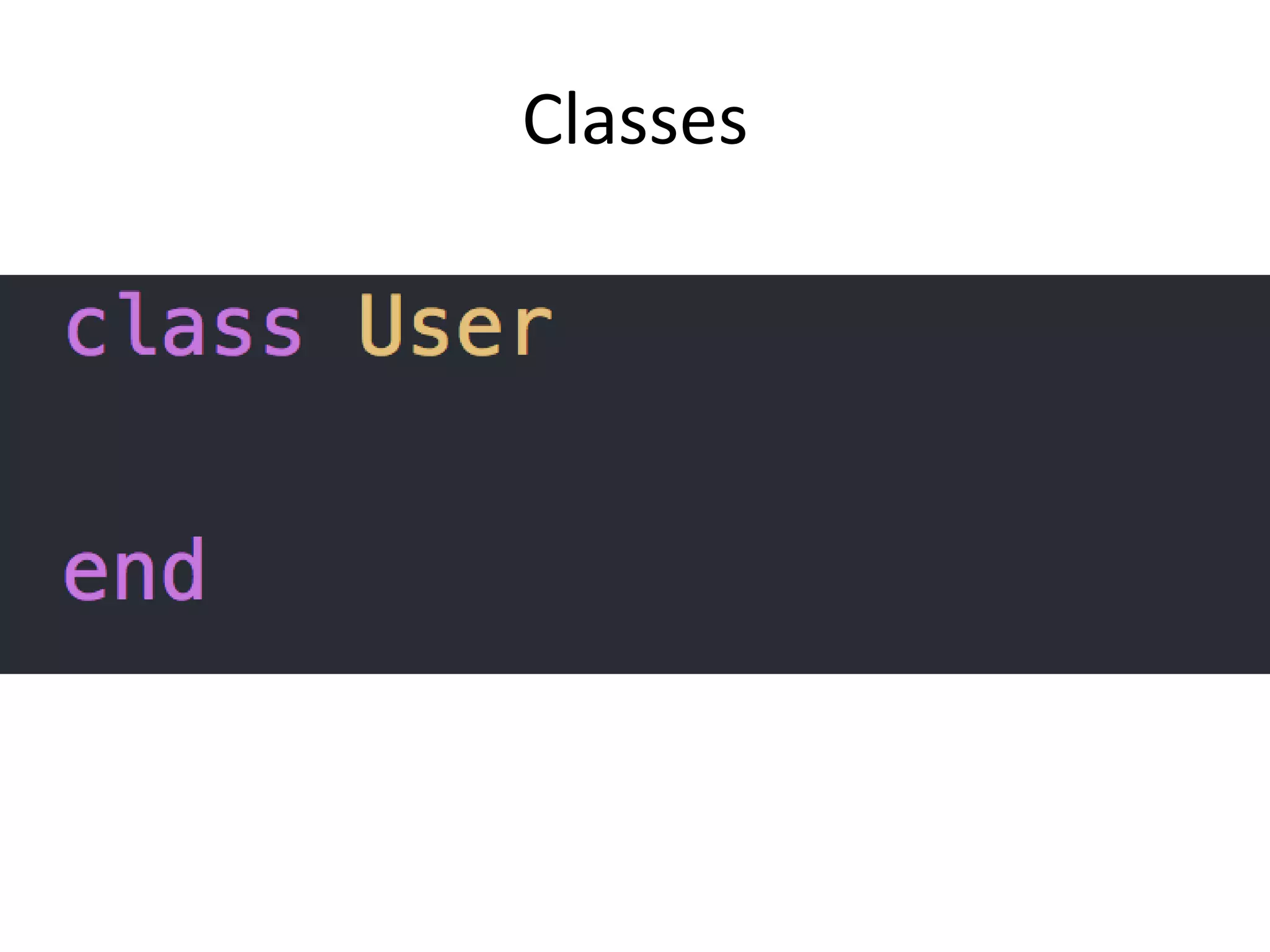
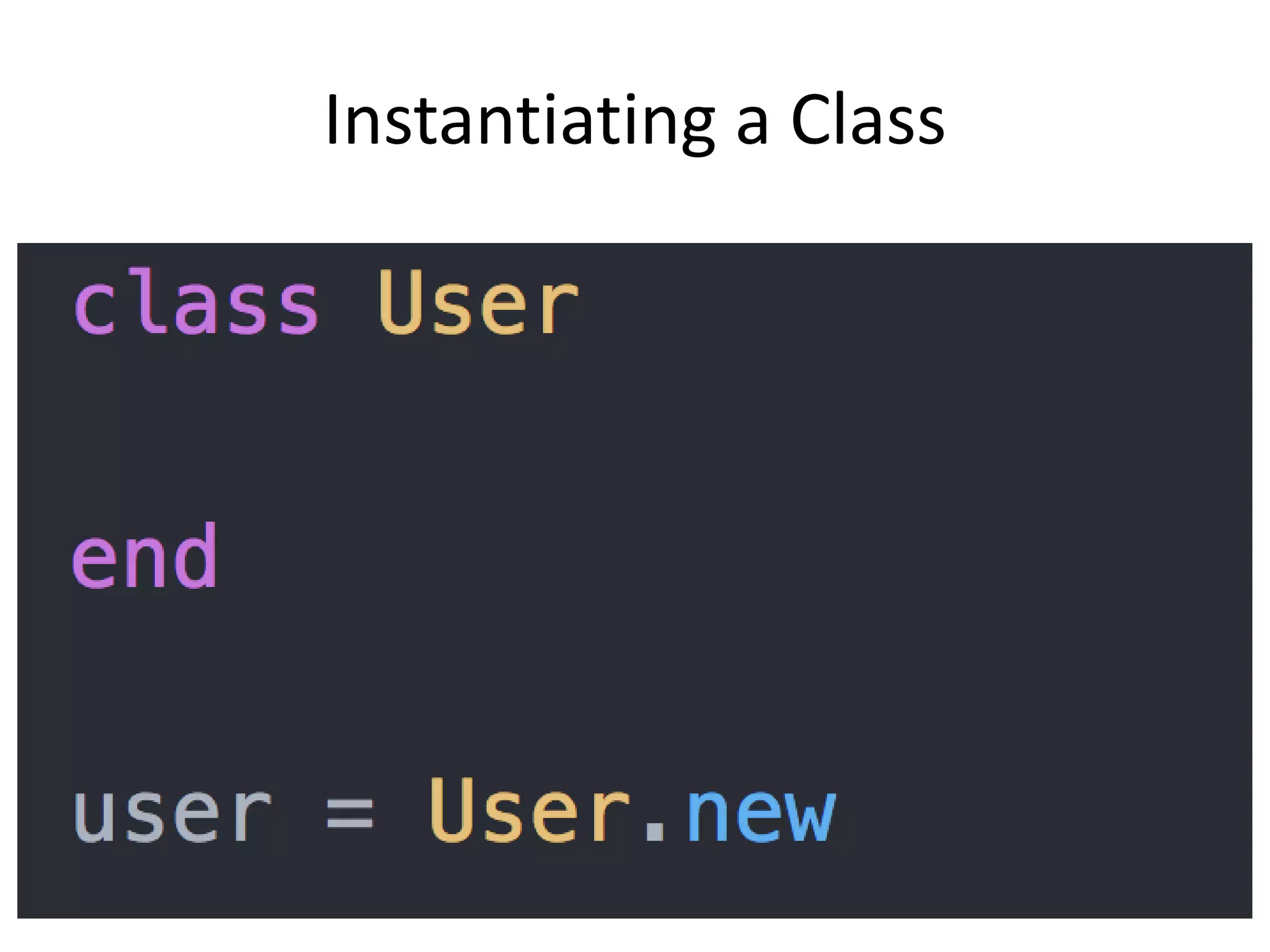
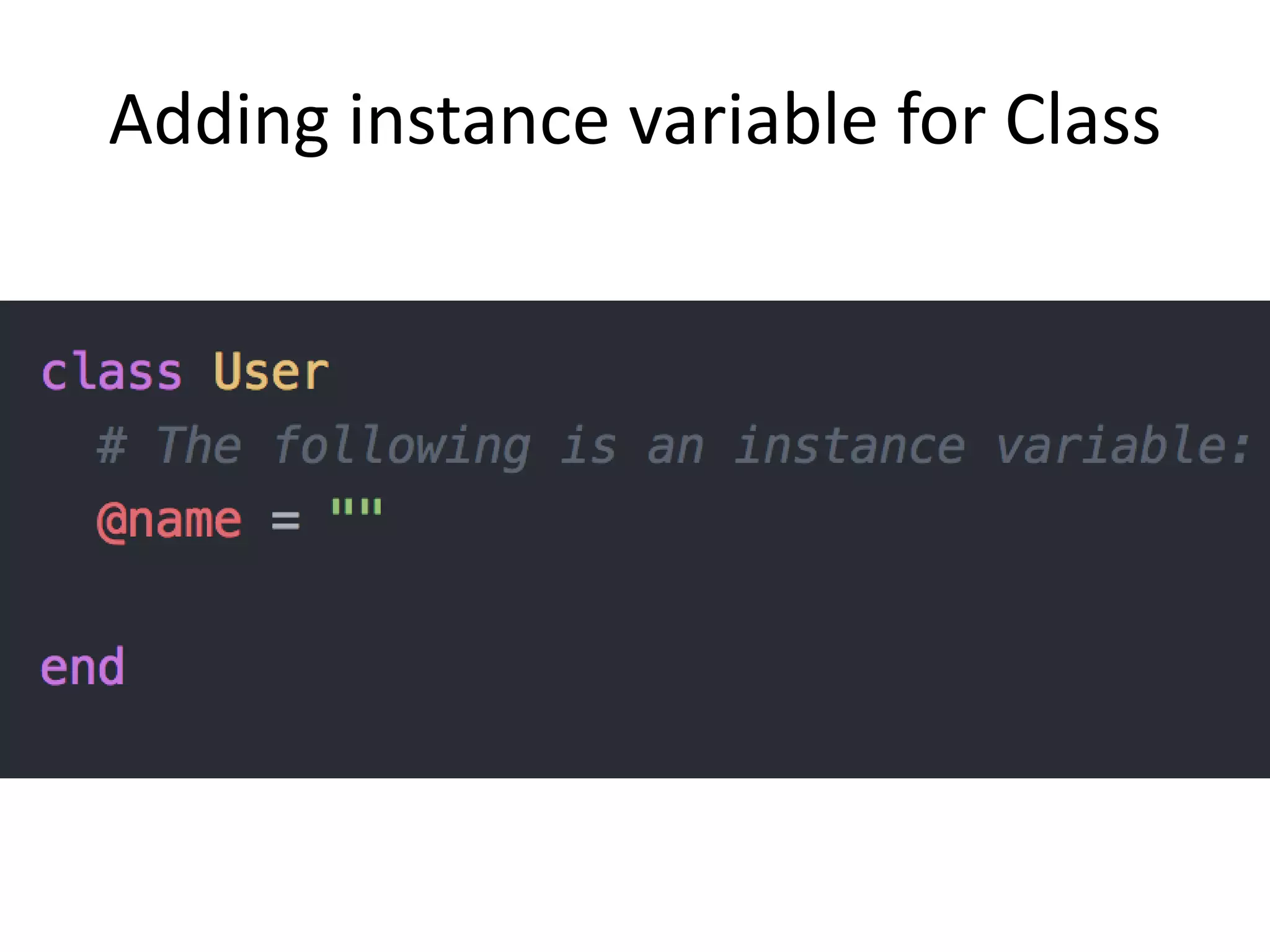
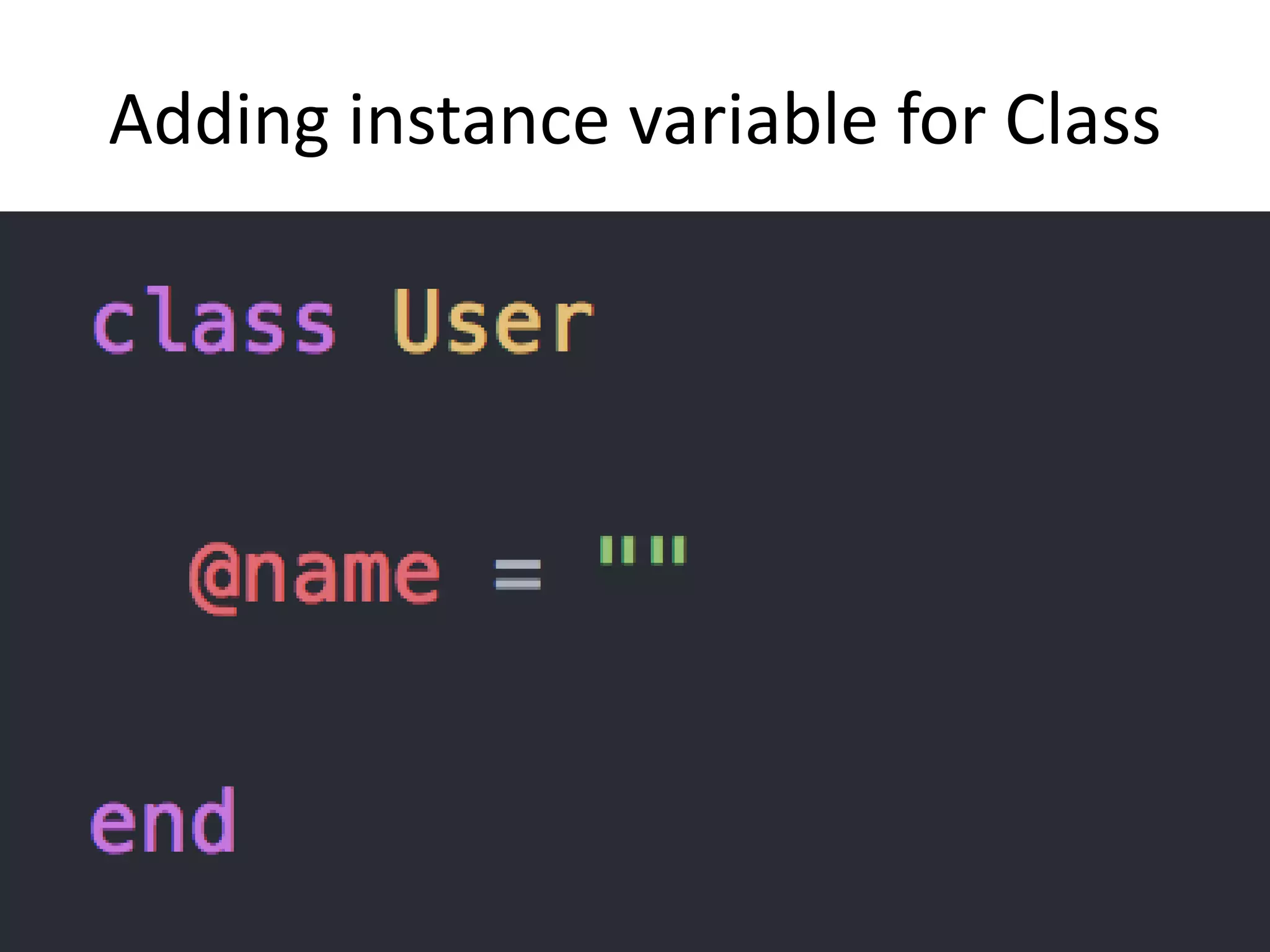
The document outlines a knowledge transfer presentation focusing on the new PR.gov infrastructure for the good standing certificate service. It covers various topics including modern digital service development, microservices architecture, application programming interfaces (APIs), load balancing using HAProxy, and high-availability measures with Keepalived. Participants are expected to engage in weekly presentations and Q&A sessions designed to familiarize them with the technologies and design principles underlying the system's architecture.














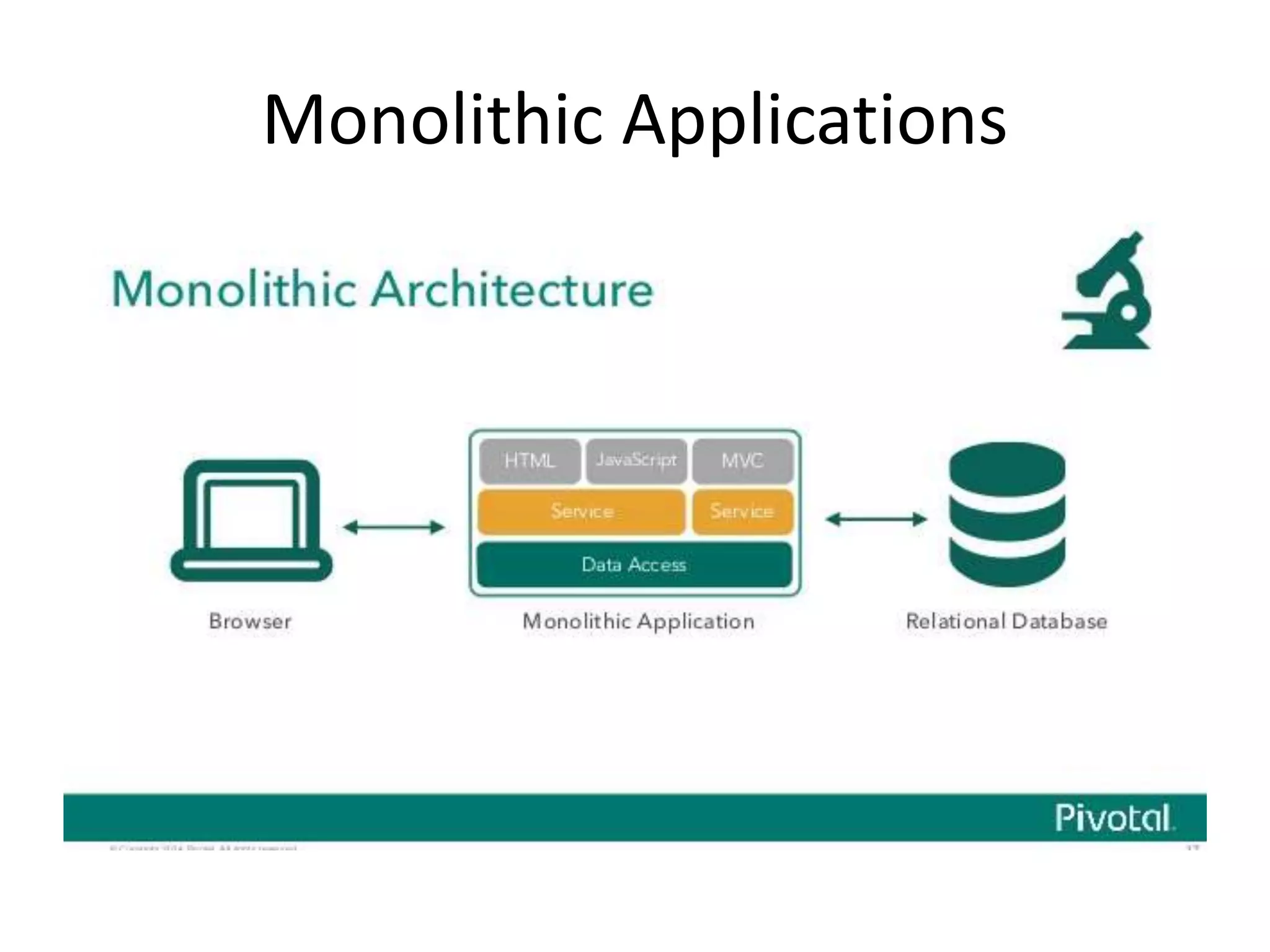
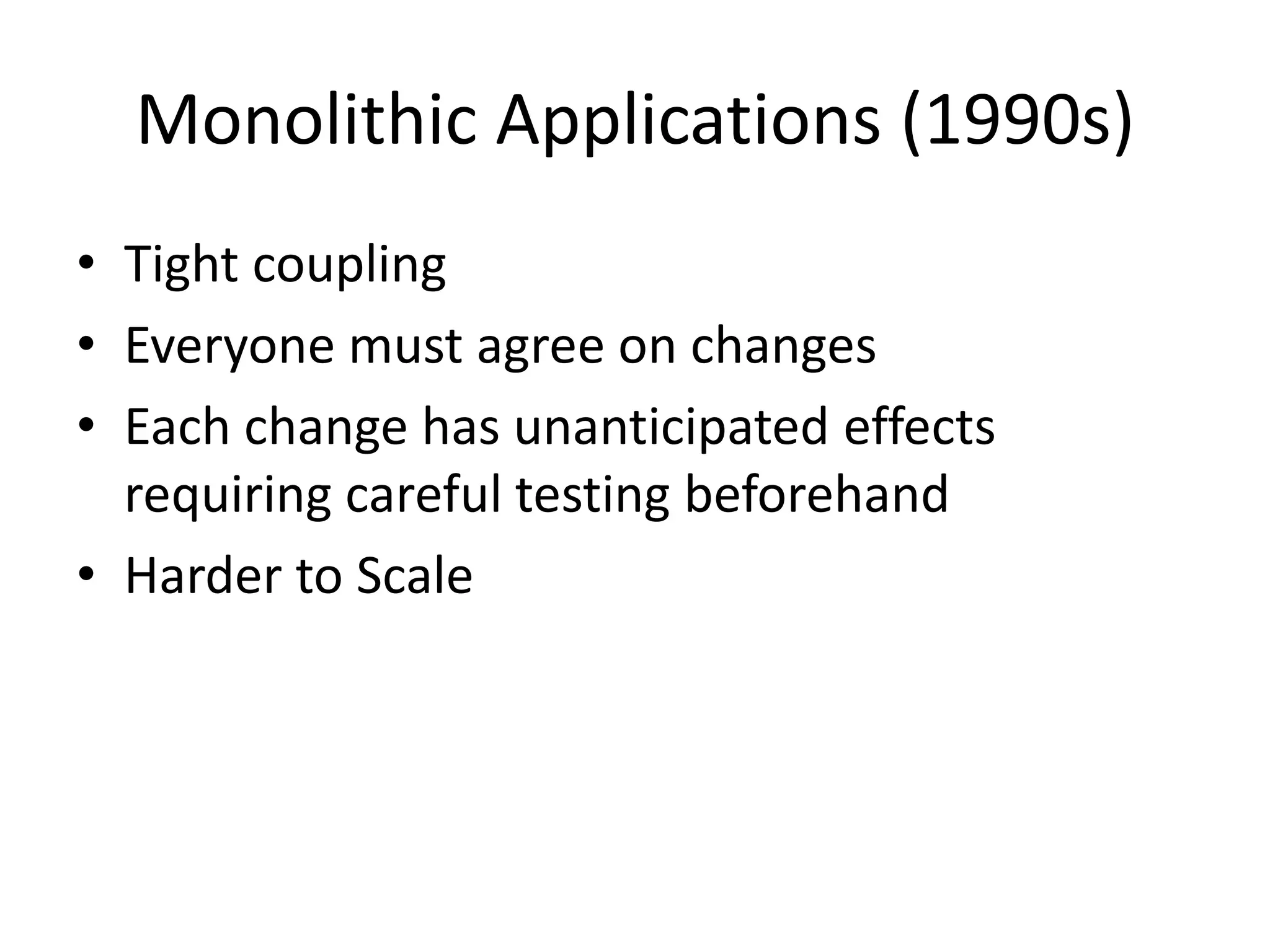
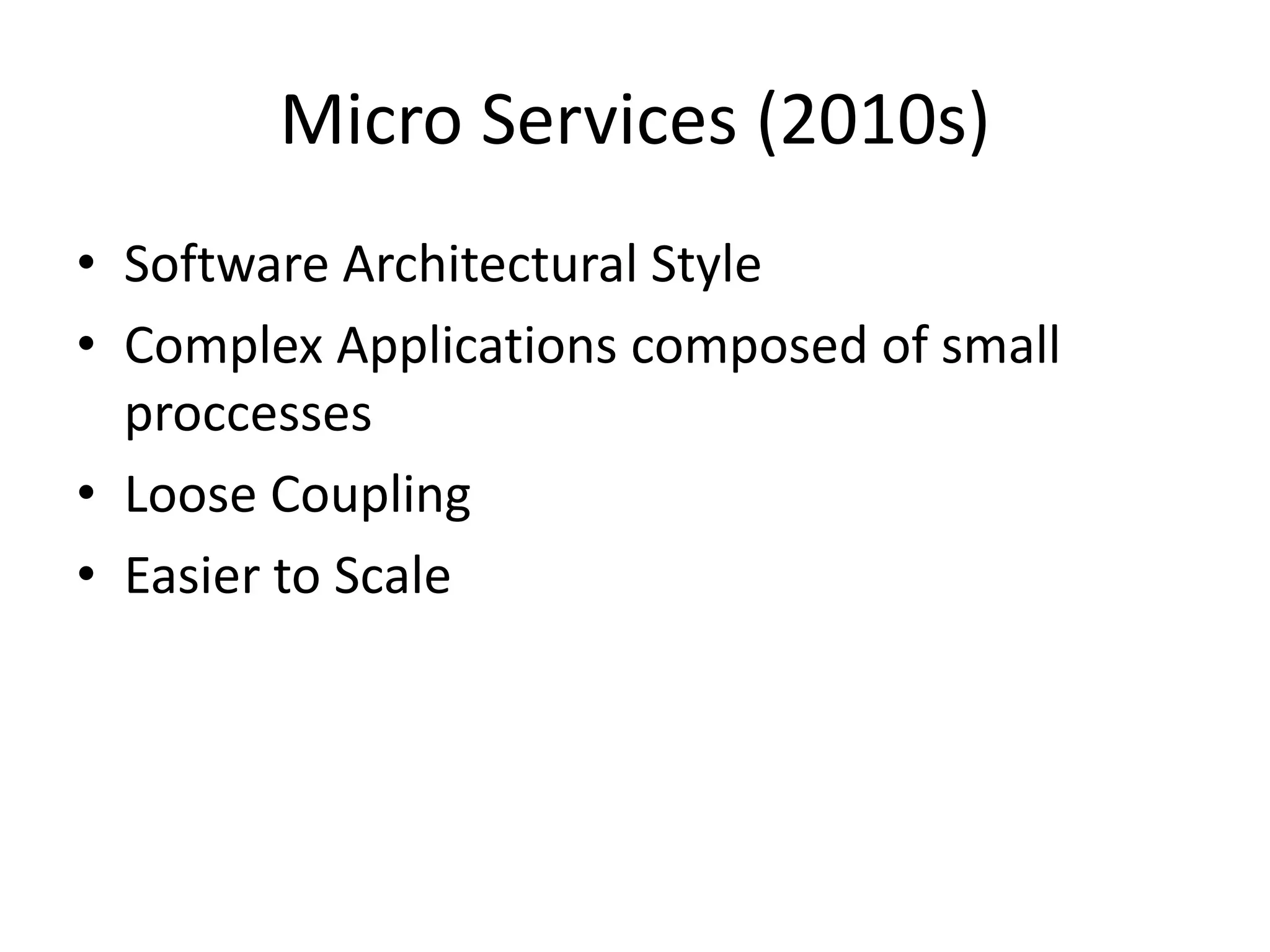




























































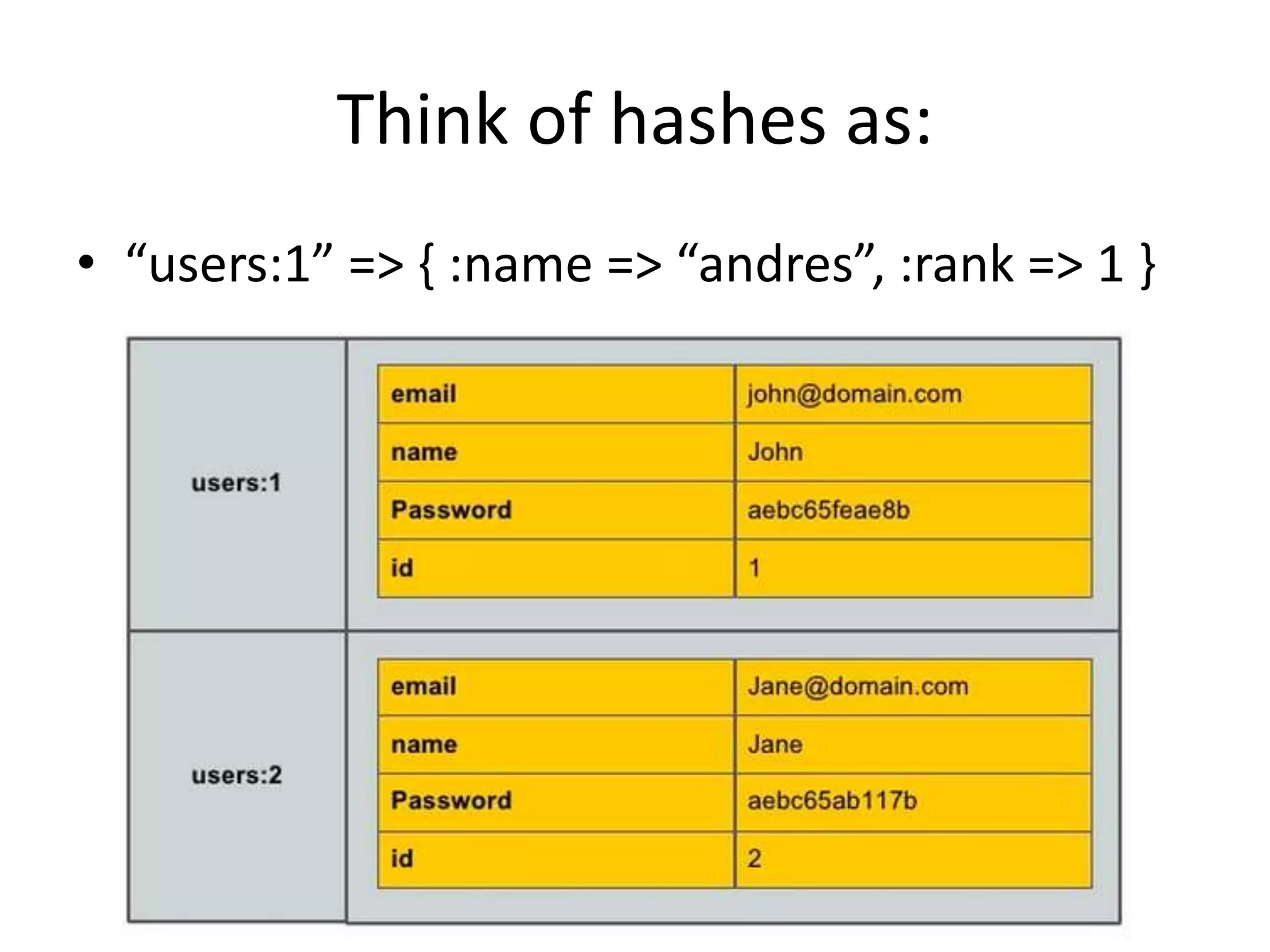
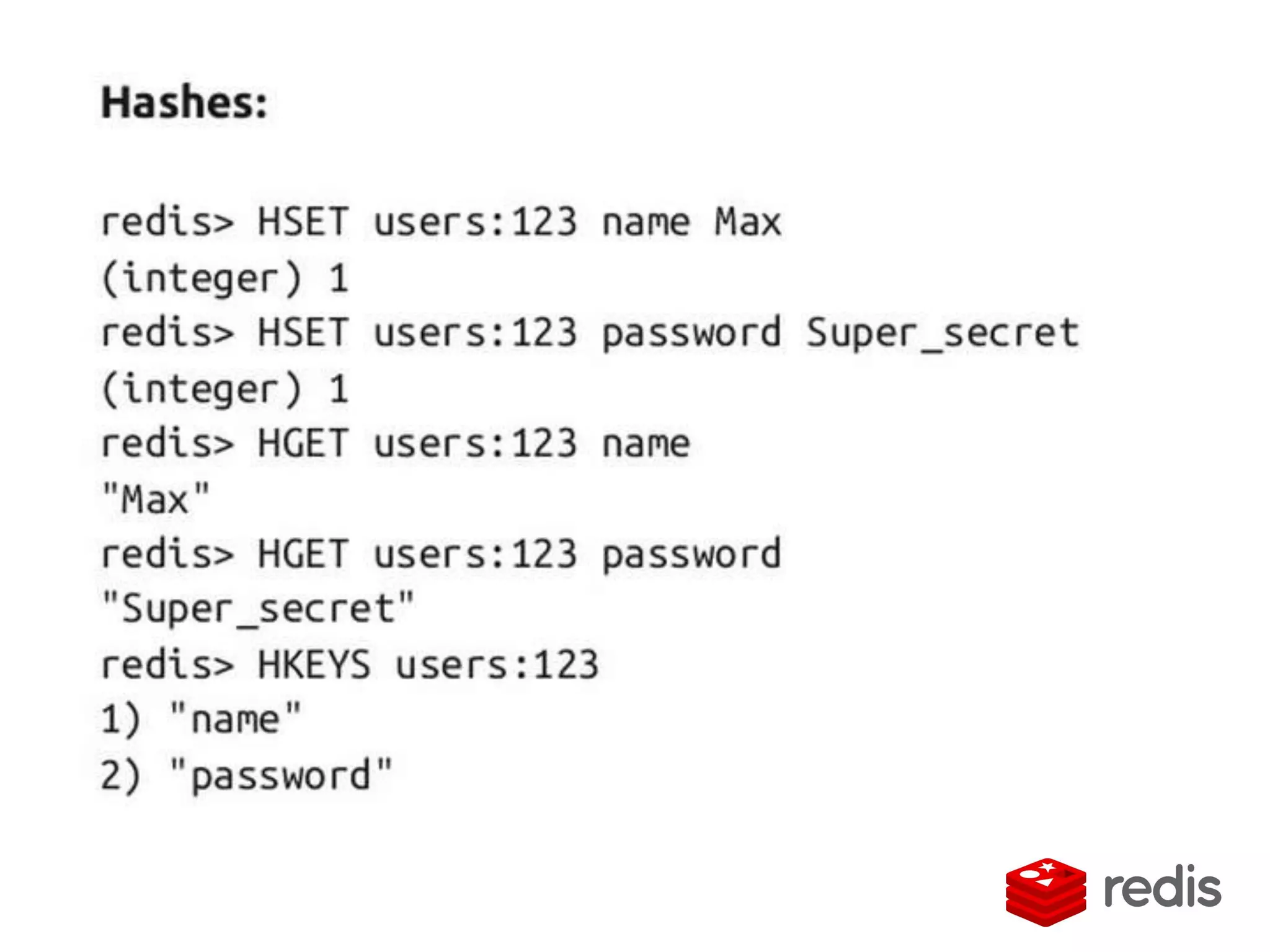
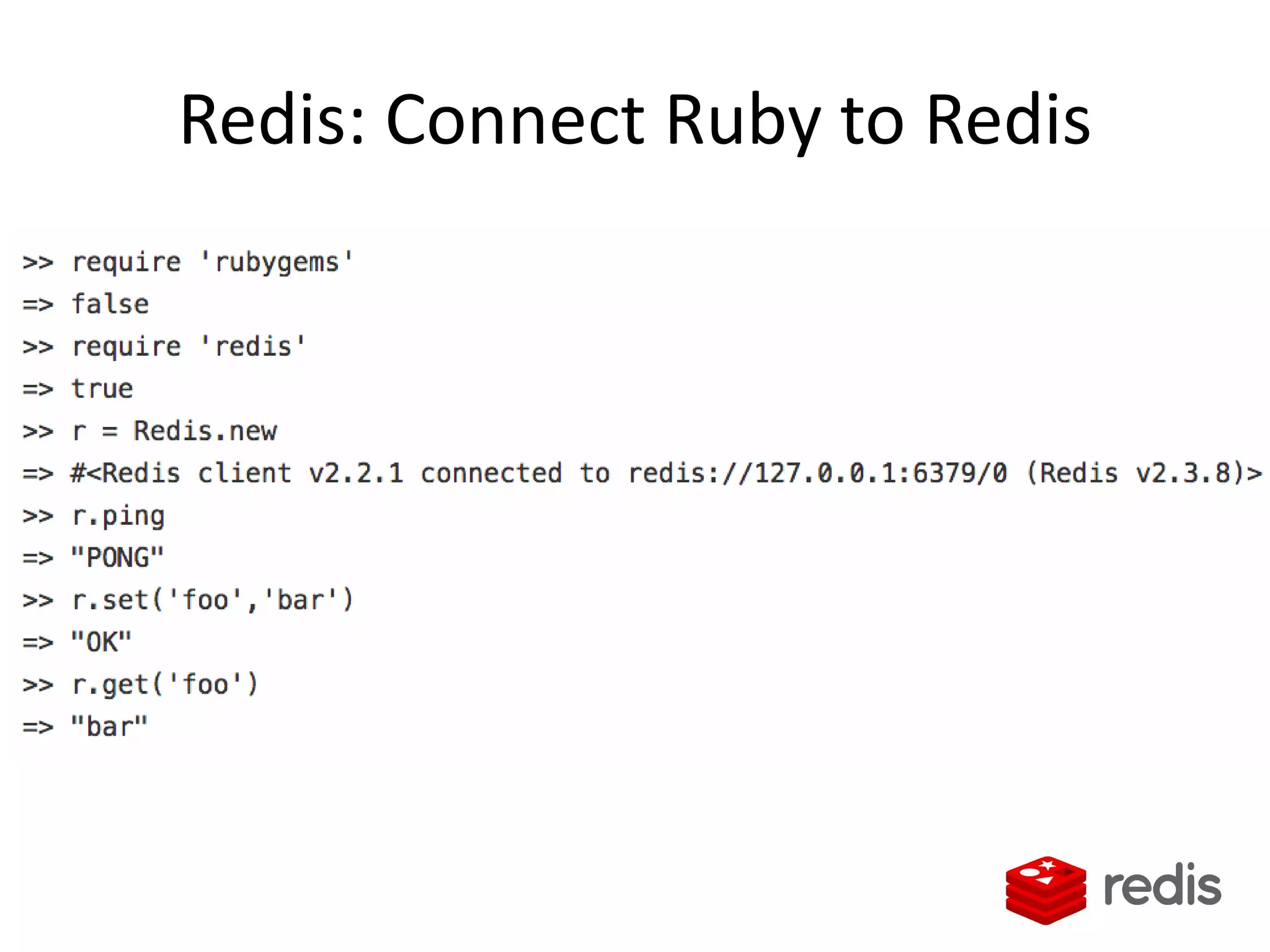
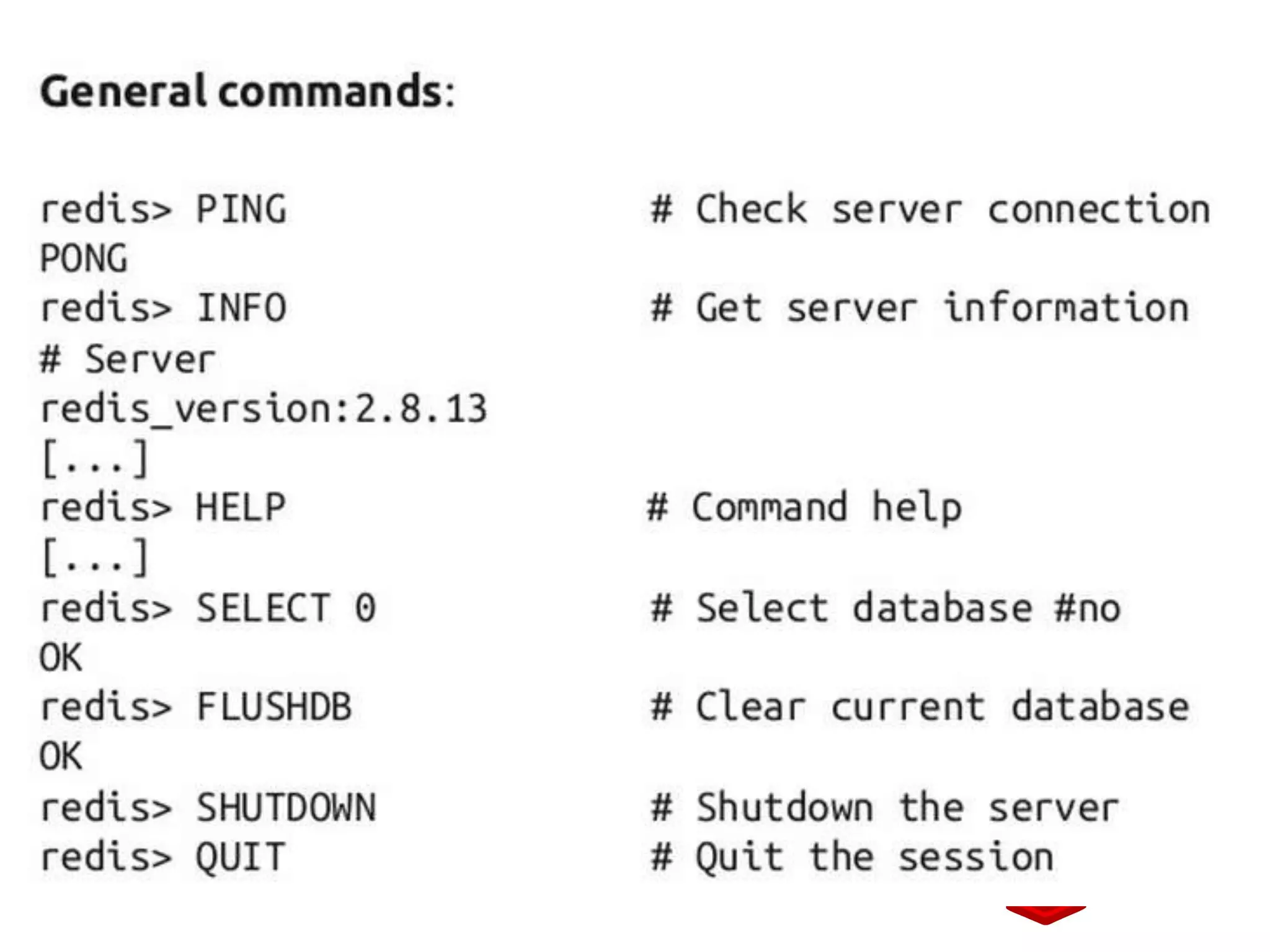











































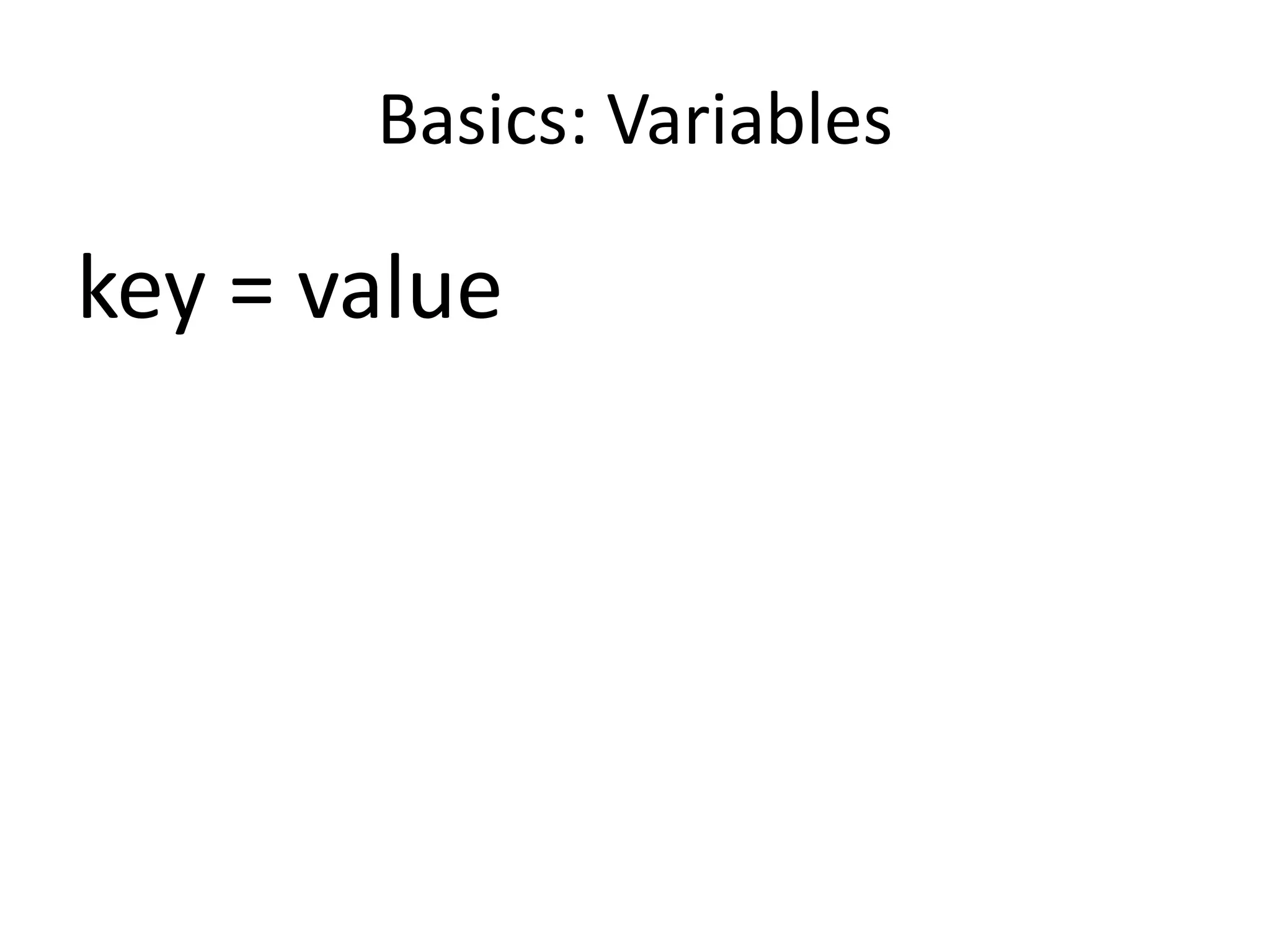

























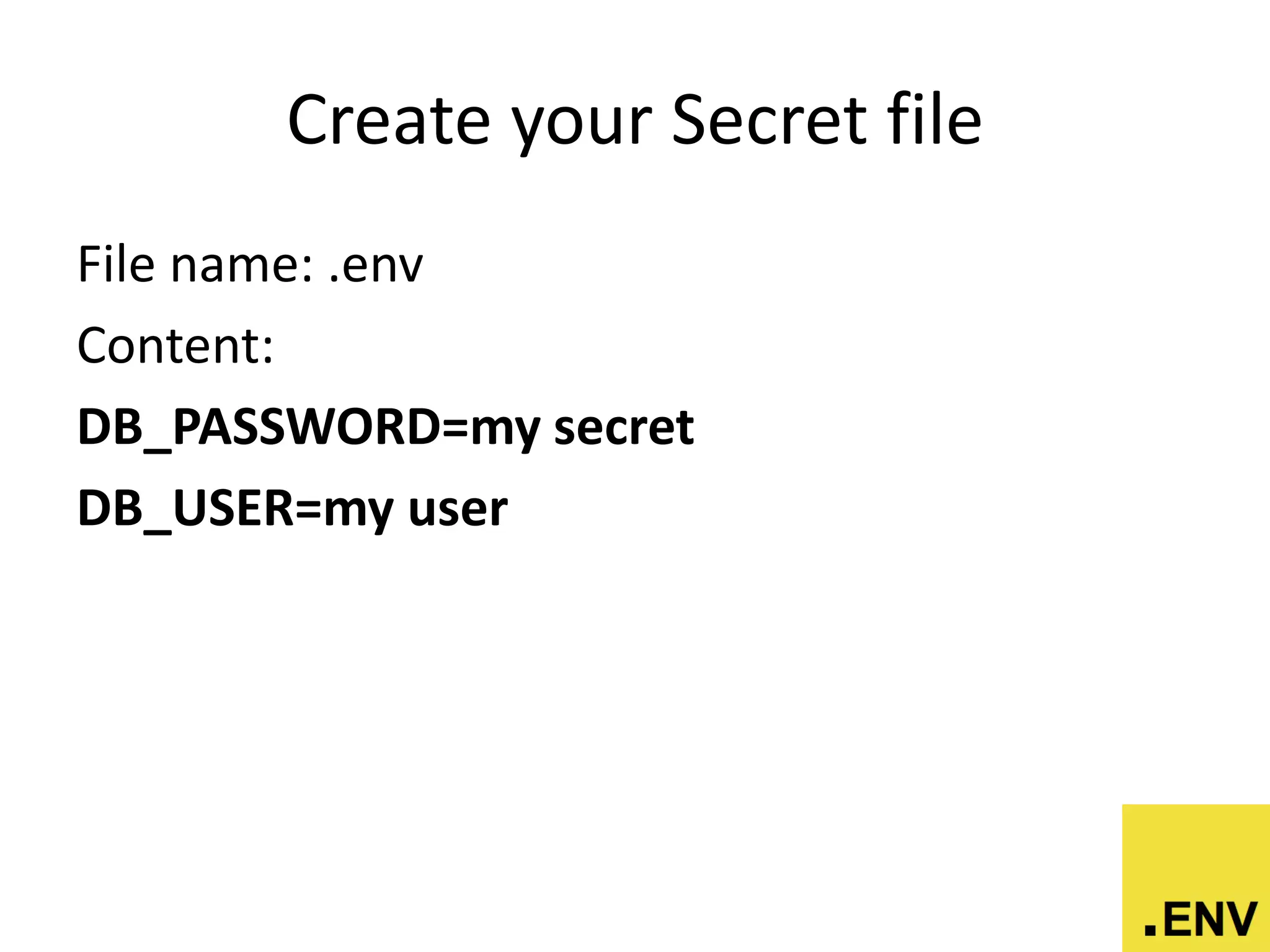
![Accesing the value
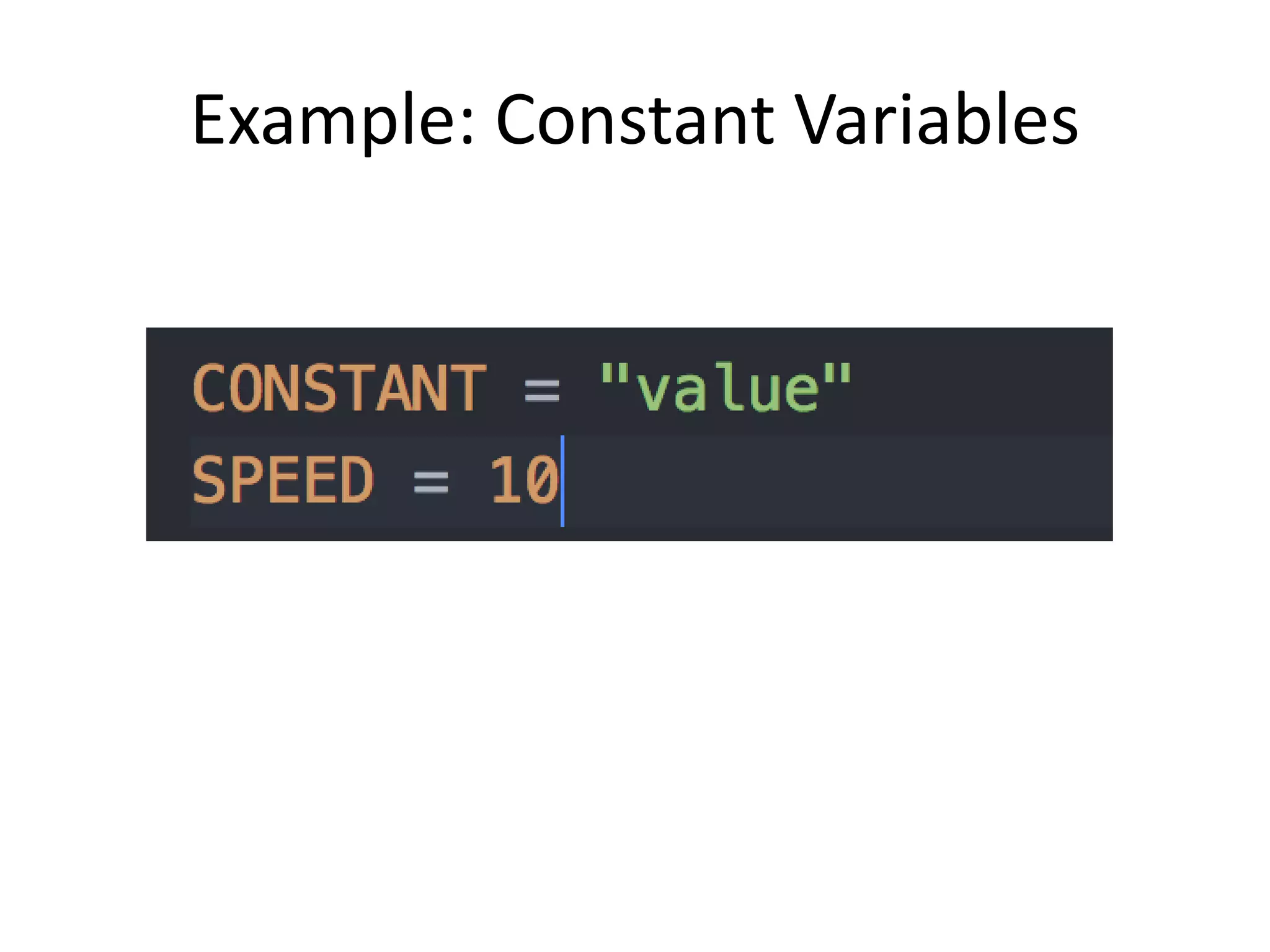
require ‘dotenv’
Dotenv.load
puts ENV[“DB_PASSWORD”]
# outputs: ‘my secret’](https://image.slidesharecdn.com/goodstandingcertificateknowledgetransferpresentationbyandrescolon-150914204342-lva1-app6891/75/Building-Modern-Digital-Services-on-Scalable-Private-Government-Infrastructures-using-Open-Source-Technologies-for-Public-Service-271-2048.jpg)