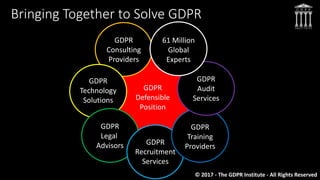
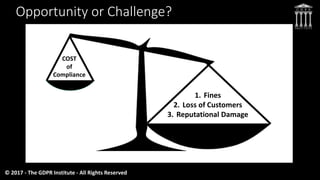
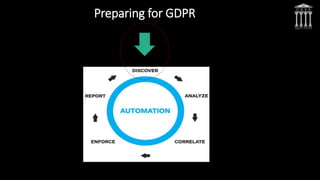
The document discusses key aspects of preparing for and complying with the EU General Data Protection Regulation (GDPR), which goes into effect on May 25, 2018. It outlines some of the major changes and requirements introduced by the GDPR, including its expanded territorial reach, new obligations for data processors, strengthened consent requirements, increased penalties for non-compliance, and the role of supervisory authorities. The document emphasizes that organizations must conduct assessments, secure resources and budgets, and implement technologies and processes to ensure they have a defensible position and are prepared to address the challenges and opportunities created by the GDPR.