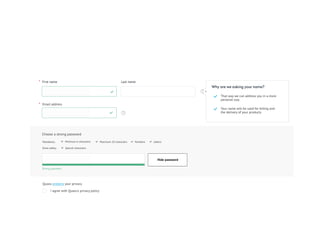
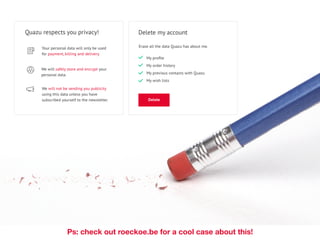
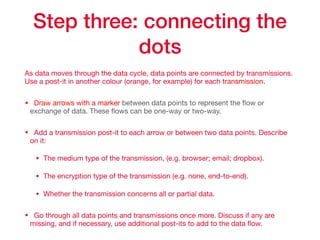
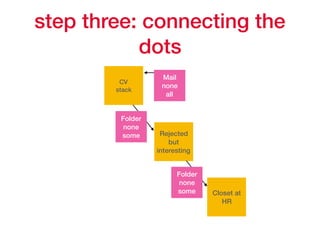
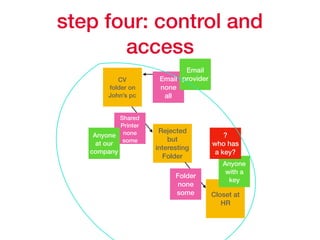
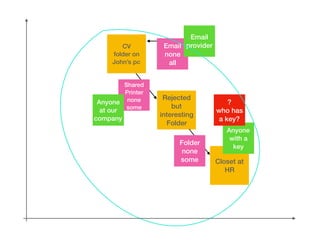
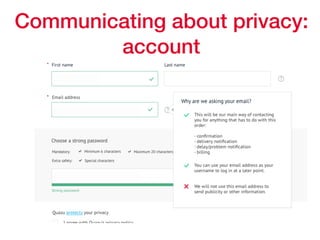
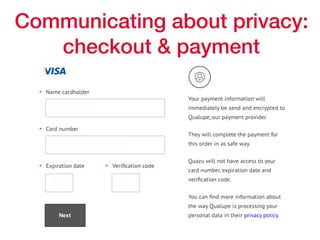
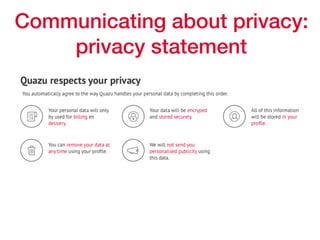
This document provides an overview of key concepts regarding the GDPR (General Data Protection Regulation) and best practices for compliance. It discusses the GDPR requirements around privacy, data protection principles, and data subject rights. It also covers topics like data flow mapping, privacy policies, consent, and data minimization. The document emphasizes the importance of understanding what personal data is, knowing what data you collect and how it flows, allowing users to access and delete their data, and fixing privacy policies to be clear and understandable for users.