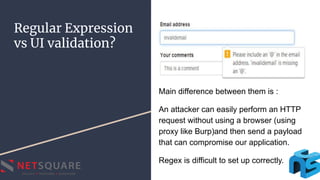
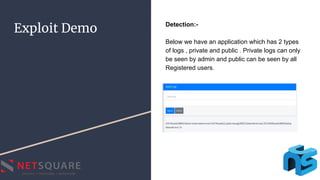
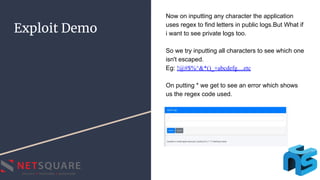
Regular Expression Injection occurs when an attacker supplies malicious input that modifies the intended regular expression in a way that breaks the program's specifications. This can impact control flow, leak information, or cause denial-of-service vulnerabilities. The document discusses regular expressions, how to find regular expression injection issues through error-based or blind injection techniques, demonstrates an example exploit, and provides mitigation strategies like input validation before using regular expressions and killing expressions that take too long.





![What is Regular
Expression?
/[w._+-]+@[w.-]+.[a-zA-Z]{2,4}/
Eg: elton@net-square.com
https://www.w3schools.com/jsref/jsref_obj_regexp.asp](https://image.slidesharecdn.com/regularexpression-200521083758/85/Regular-Expression-Injection-6-320.jpg)



![How do we find it?
Mostly like all injections we find it
with help of methods such as
A.Error Based
B.Blind Based [Fairly new]
Error-based is an in-band Injection
technique that relies on error
messages thrown by the server to
obtain information about the structure
of the regex.
Blind-Based is injection technique
that relies on time take to respond by
the server based on input.](https://image.slidesharecdn.com/regularexpression-200521083758/85/Regular-Expression-Injection-11-320.jpg)

![Mitigation ● Input validation/sanitization should
be done and then sent to regex.
String sanitized = subject.replaceAll("[ + * / ]");
Pattern regex = Pattern.compile(sanitized);
● If a regular expression takes too
long, kill it at once, and inform the
user that the regular expression
was taking too long.](https://image.slidesharecdn.com/regularexpression-200521083758/85/Regular-Expression-Injection-15-320.jpg)

