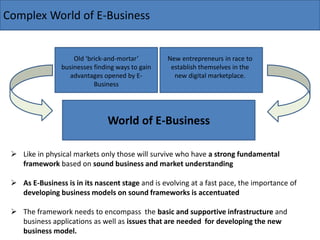
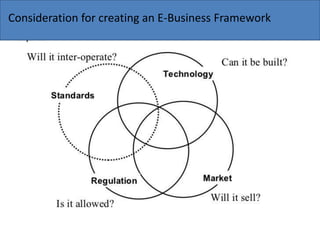
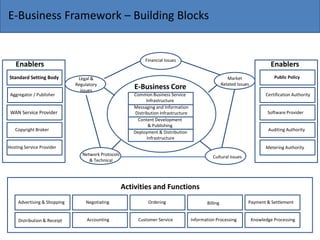
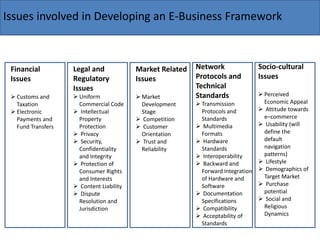
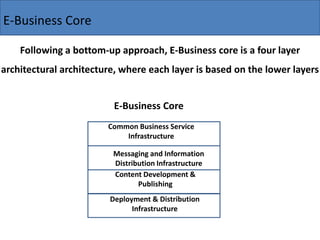
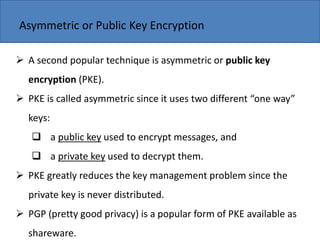
The document discusses the key components needed to develop an effective framework for e-business. It outlines several building blocks, including common business services like security, authentication, encryption, and payments. It also discusses important issues around legal/regulatory concerns, technical standards, and cultural factors. The core of an e-business framework involves layers for common services, messaging/information distribution, content development/publishing, and deployment infrastructure to support key activities such as advertising, ordering, billing, and customer service. Developing a strong framework is important for companies to succeed in the evolving digital marketplace.