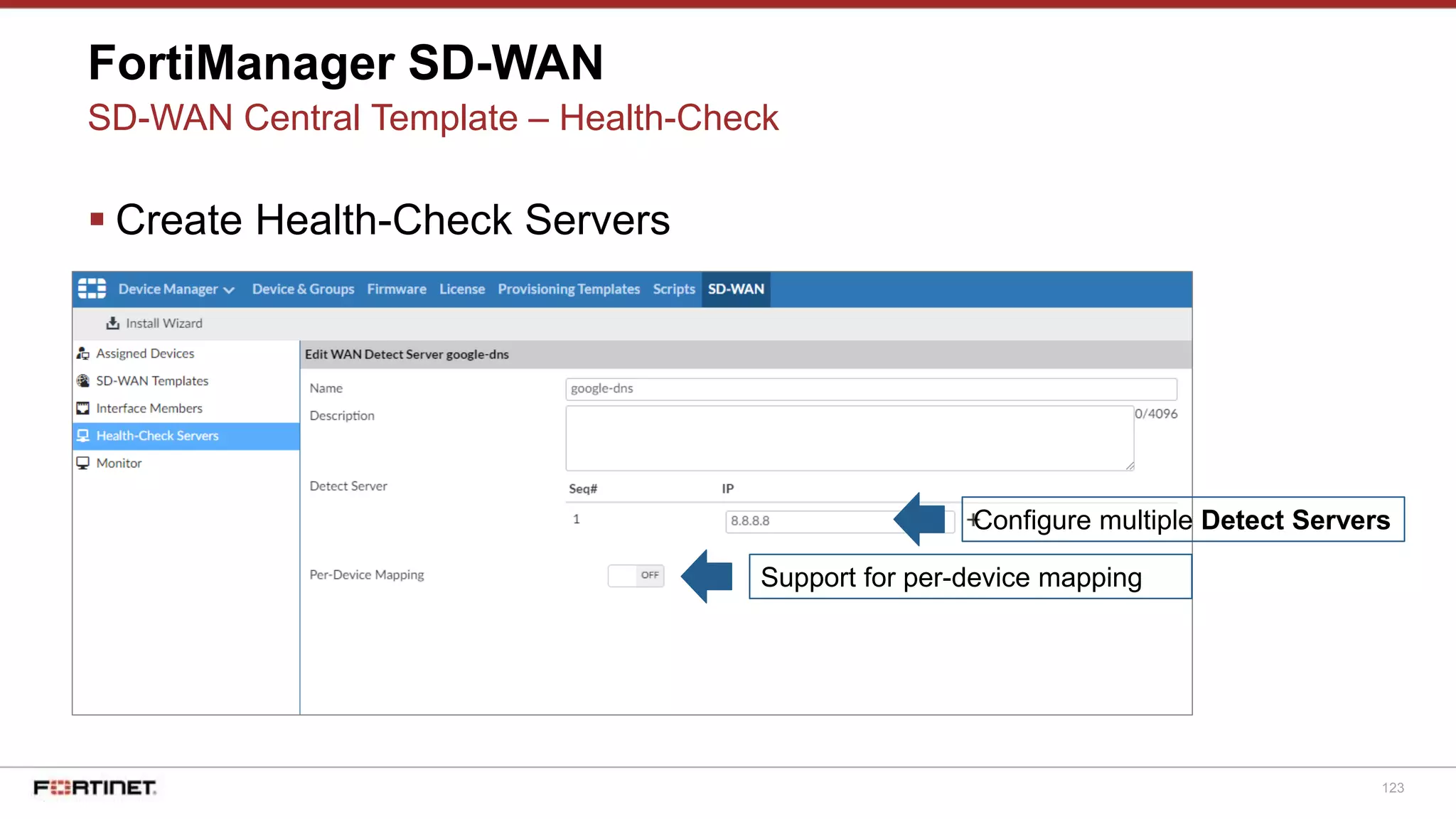
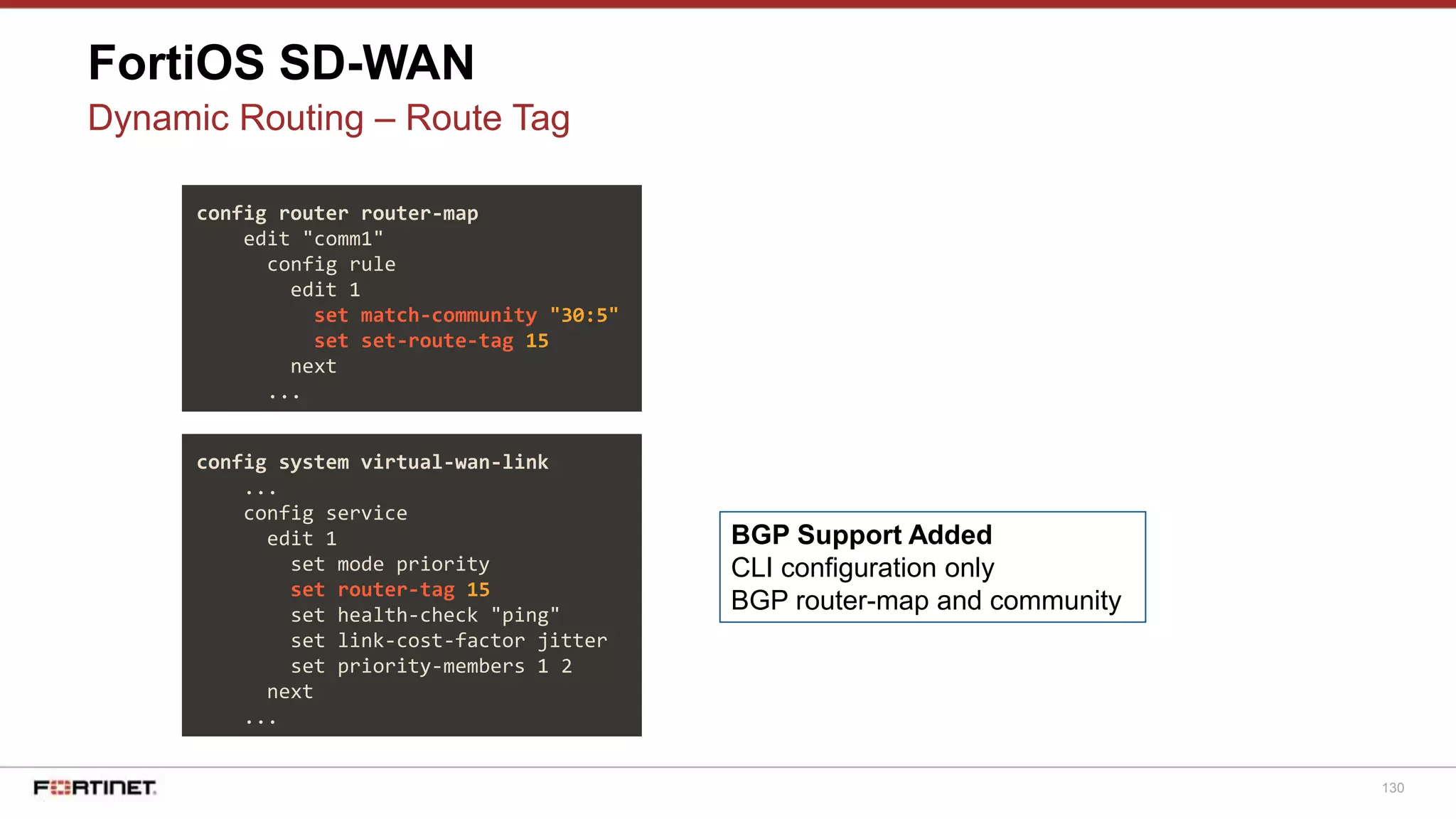
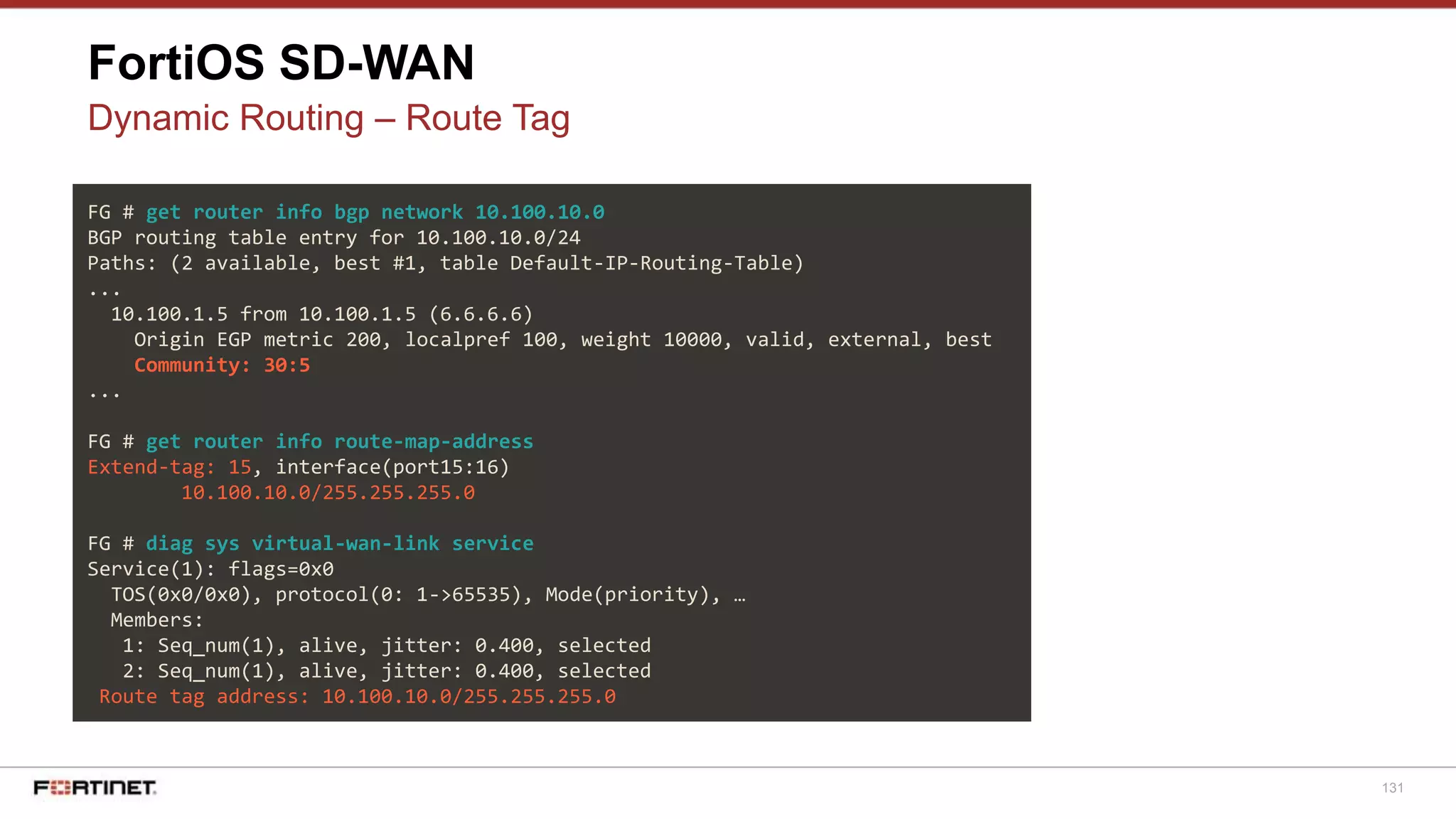
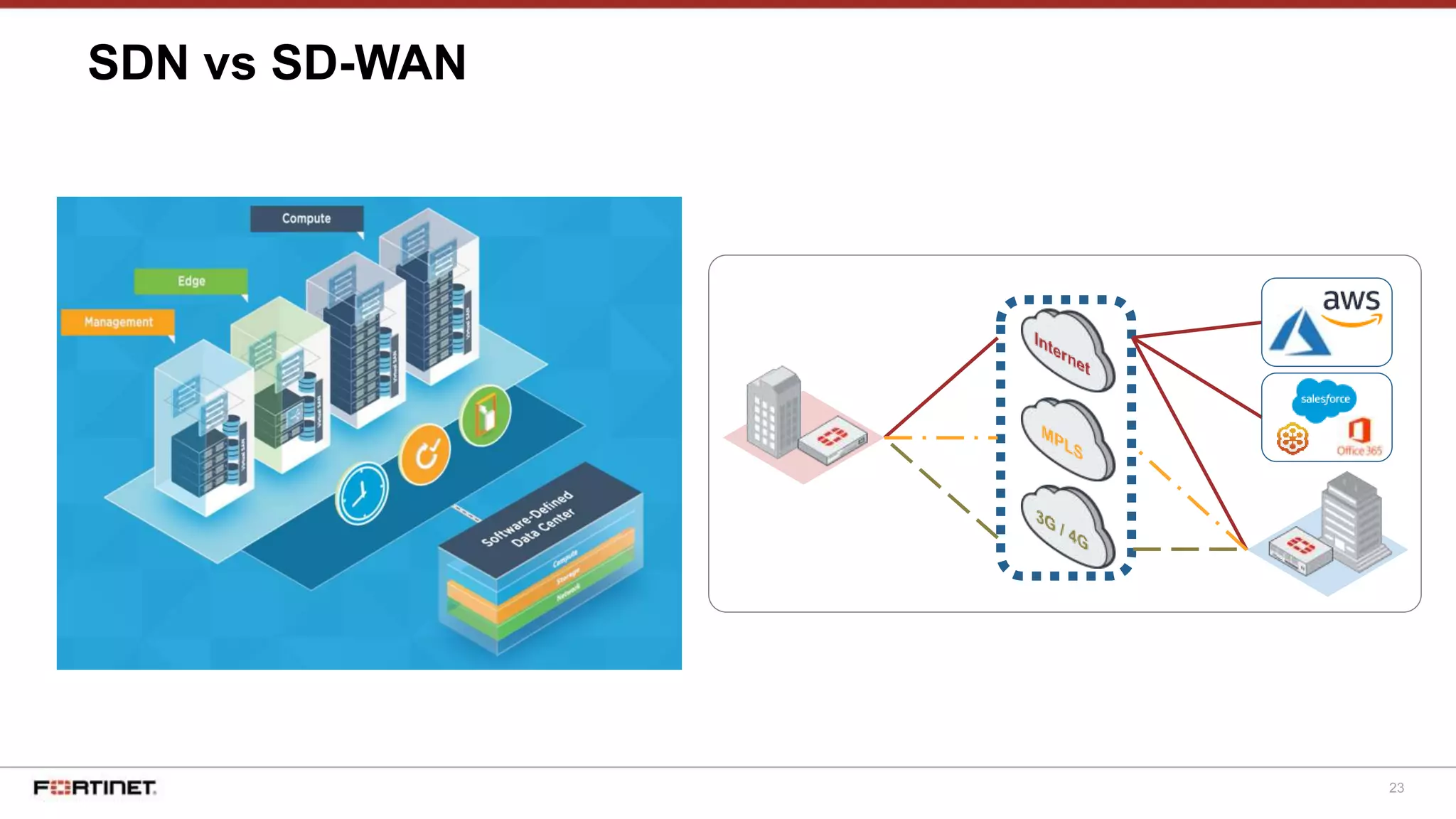
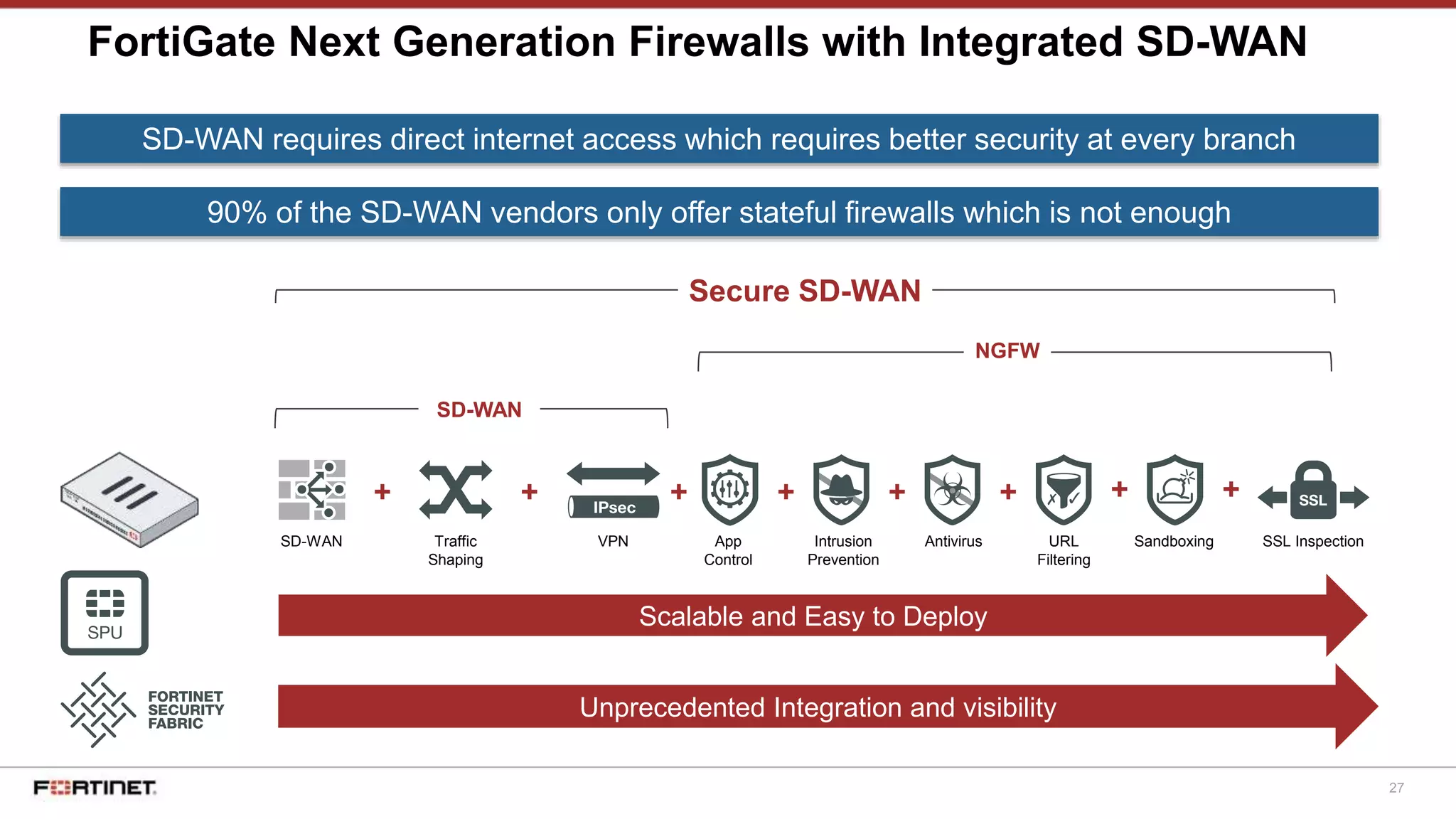
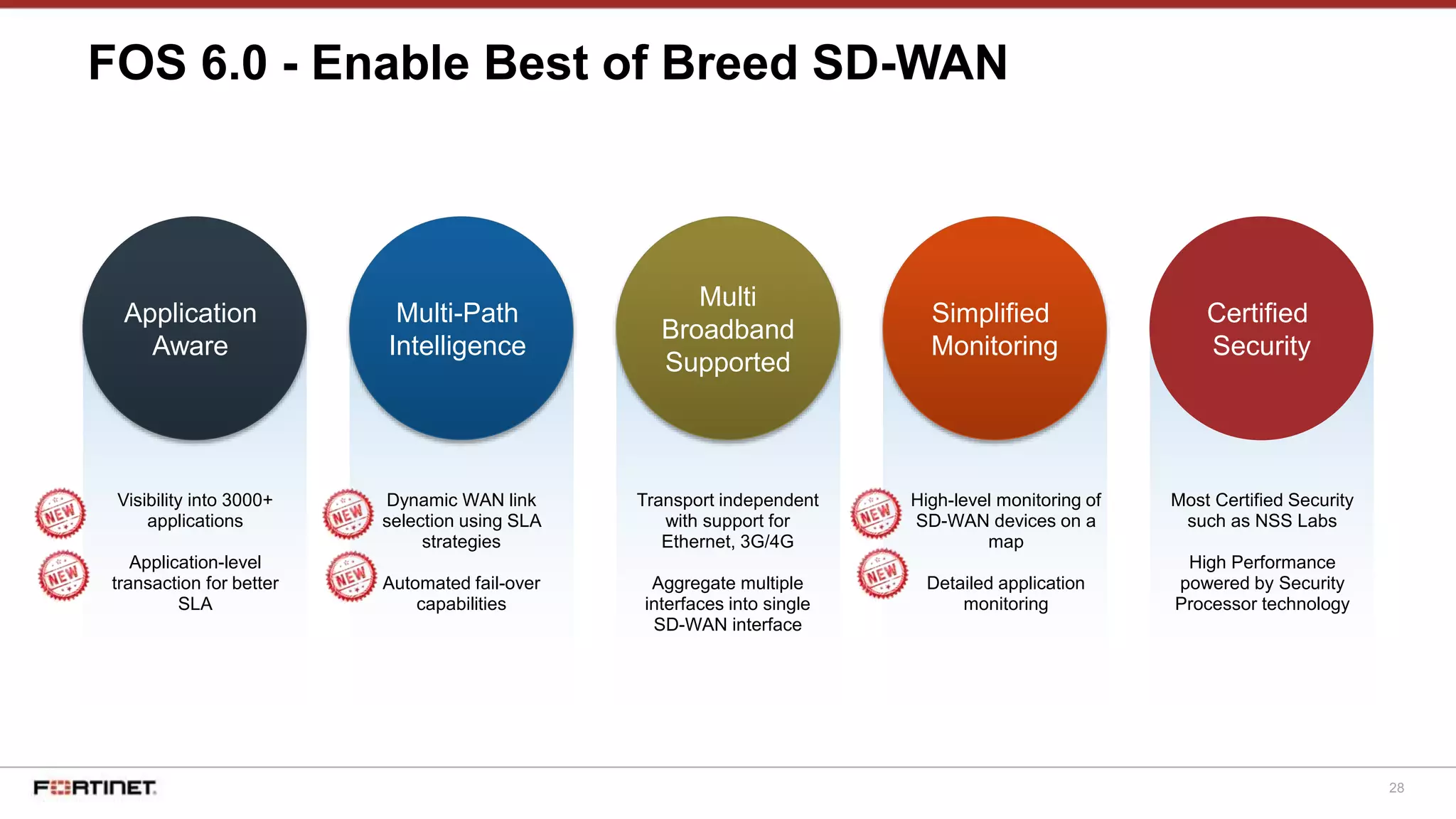
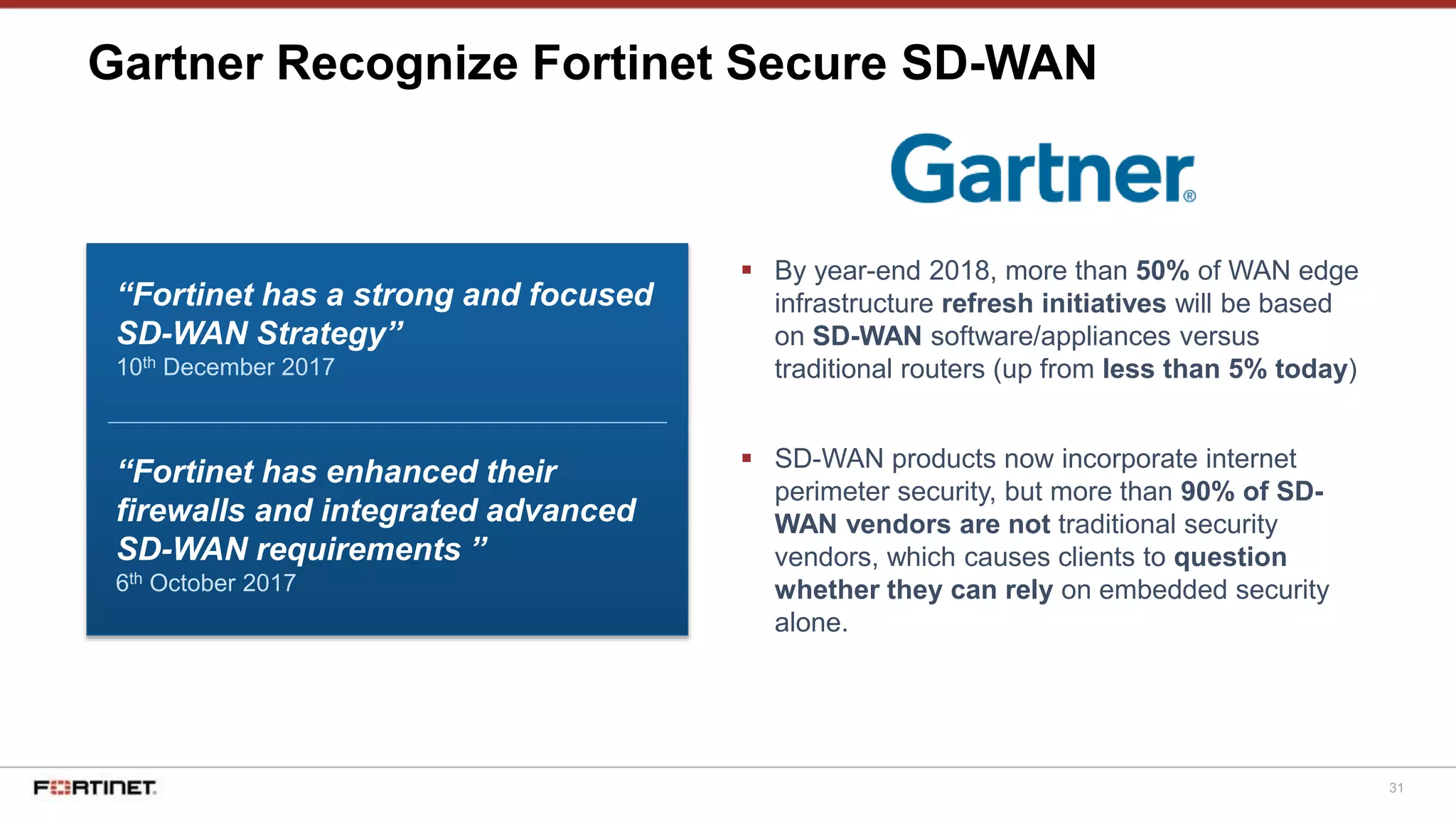
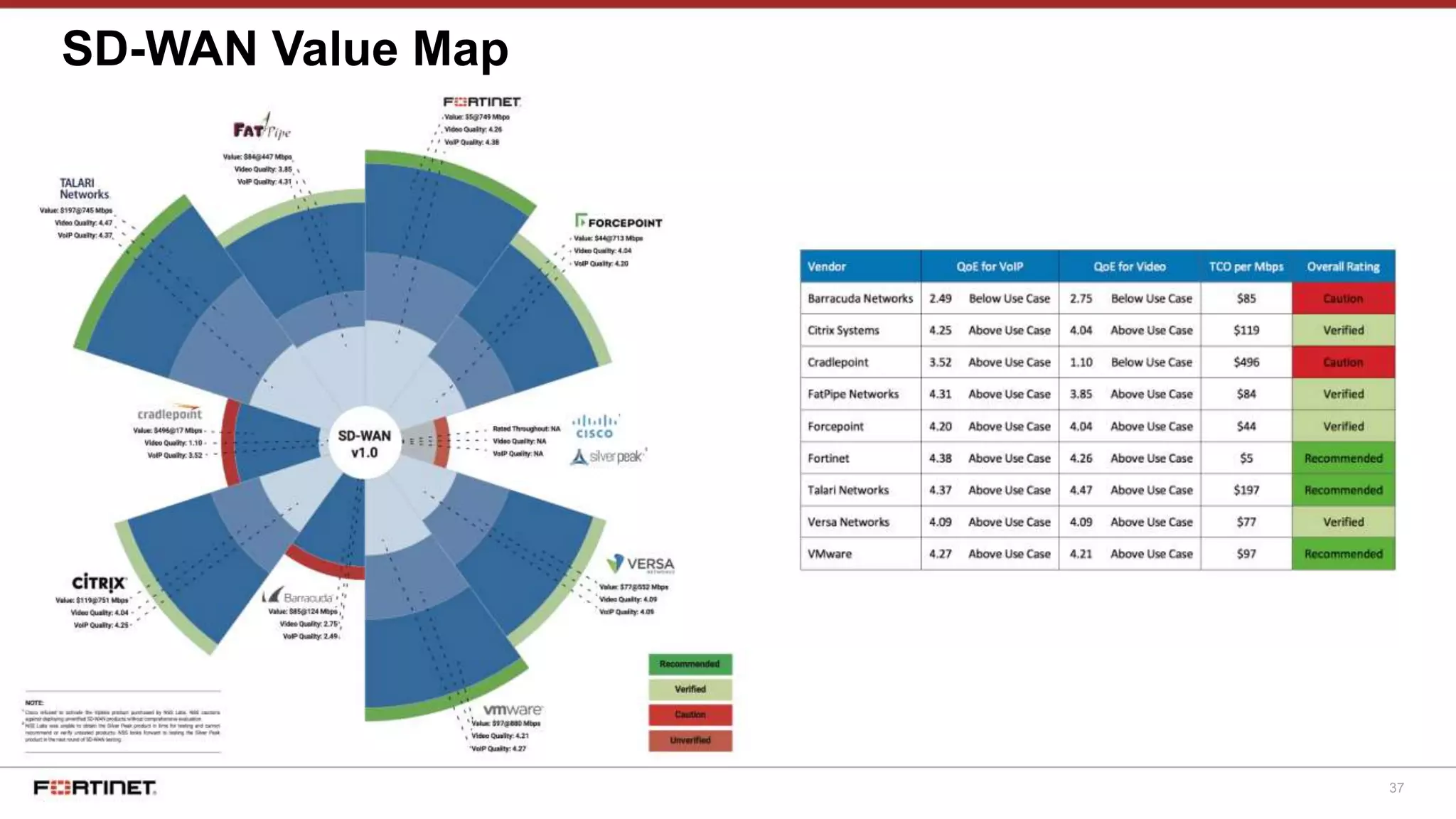
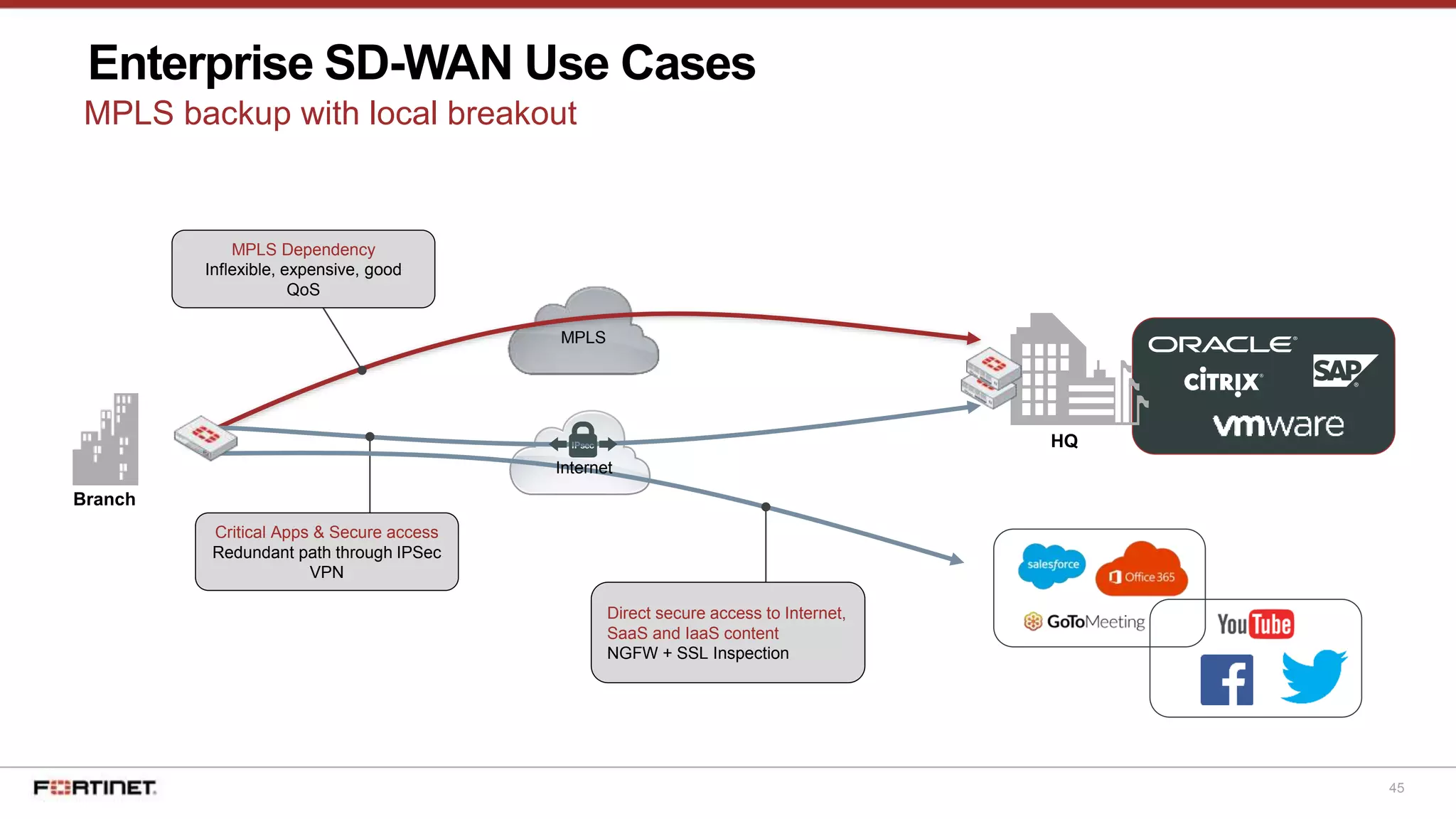
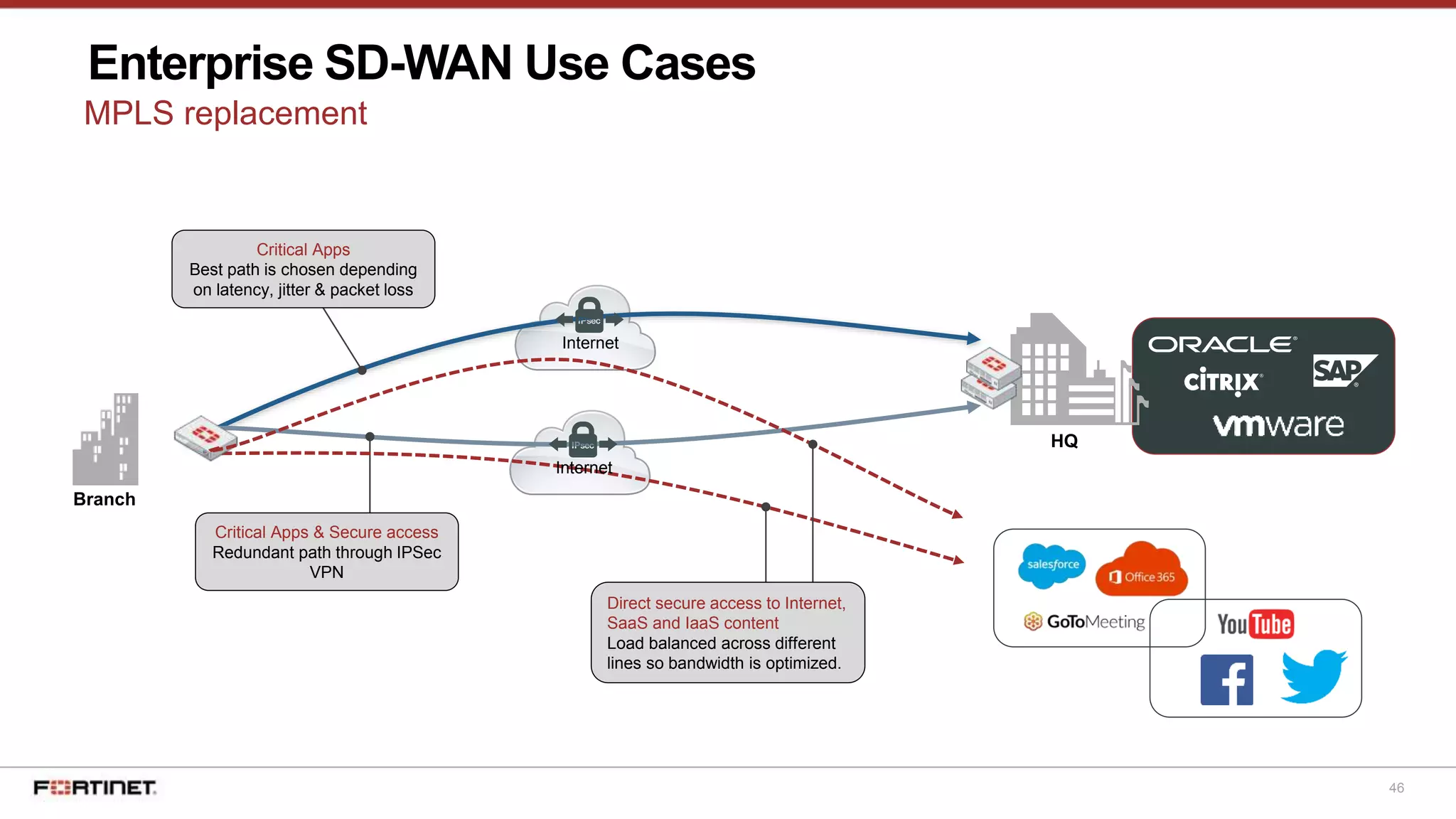
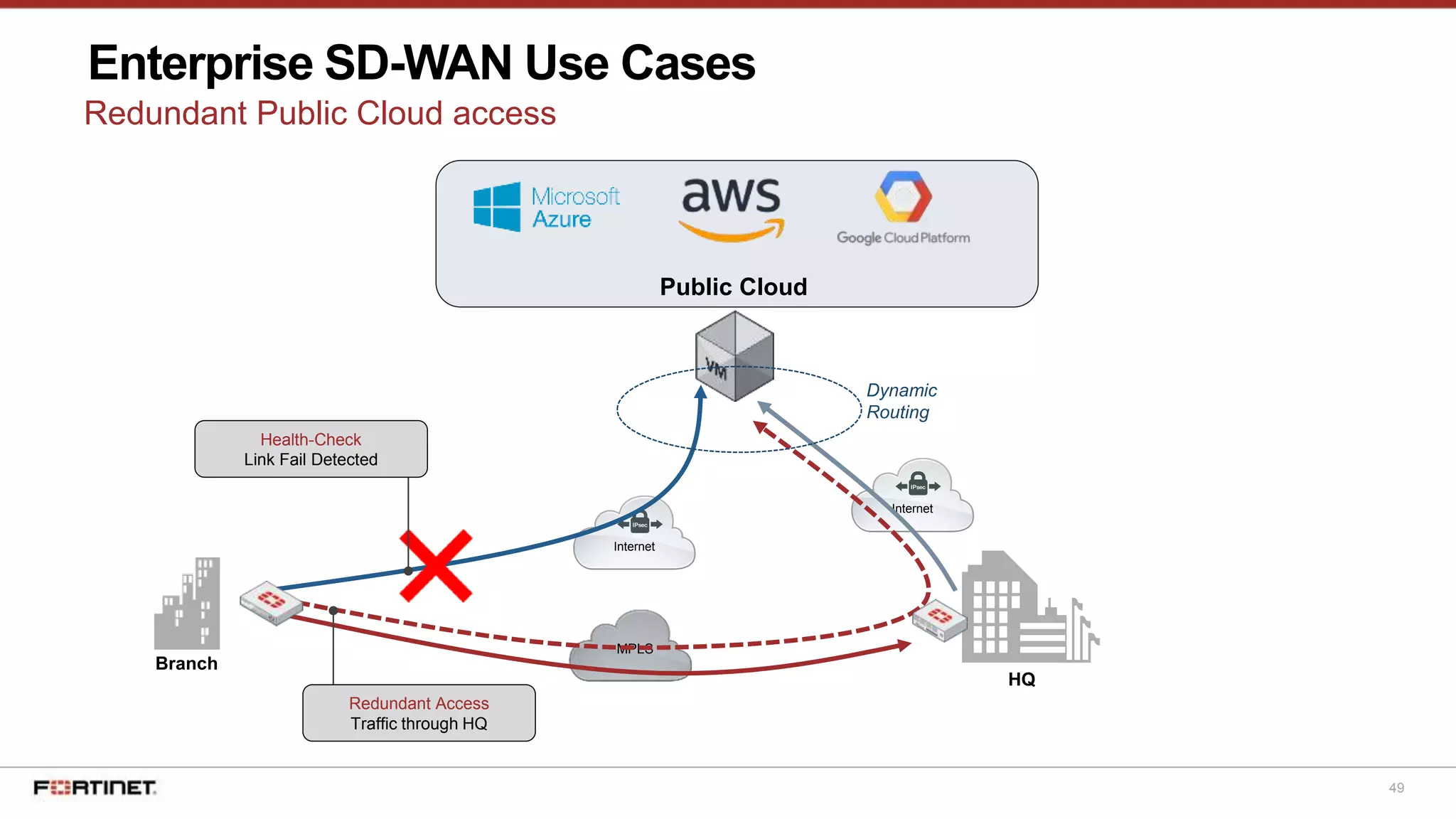
The document discusses Fortinet's Secure SD-WAN solution, including how it integrates next generation firewall capabilities into the SD-WAN architecture. It provides an overview of Fortinet's SD-WAN features such as application awareness, automated failover, simplified management, and high performance. The document also highlights how Fortinet's SD-WAN solution was recommended by NSS Labs for its security effectiveness, quality of experience, and total cost of ownership.






































![55
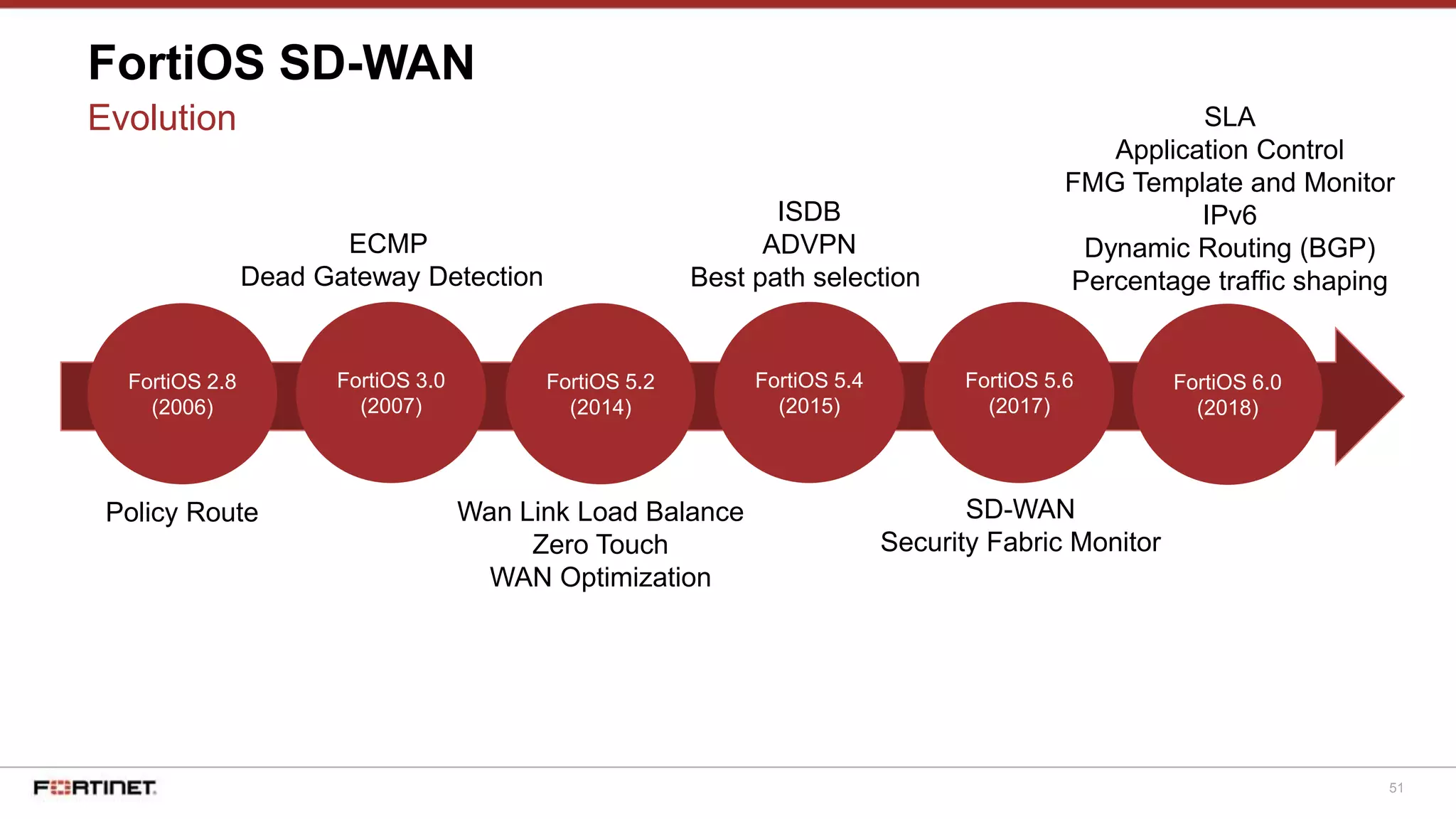
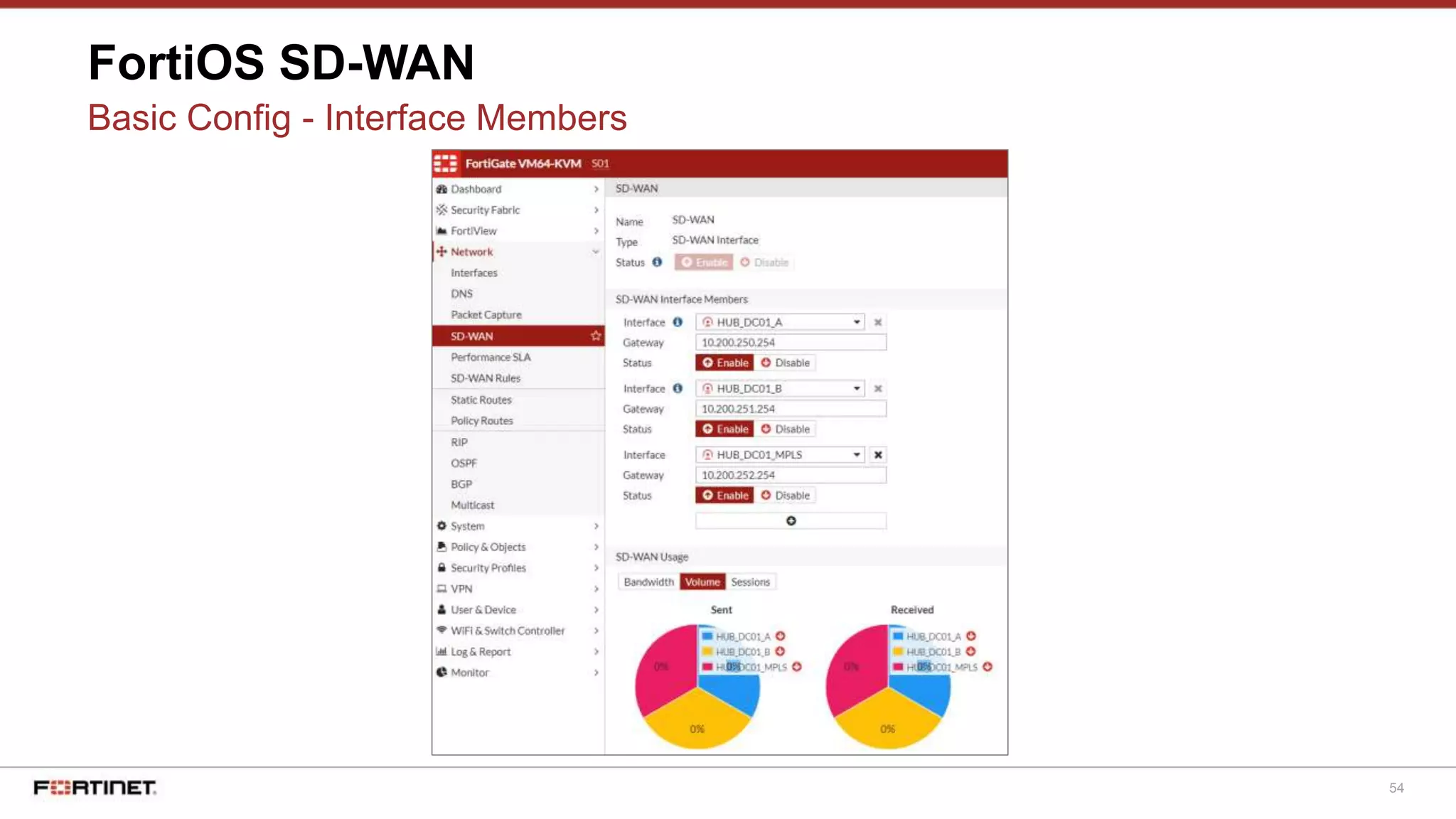
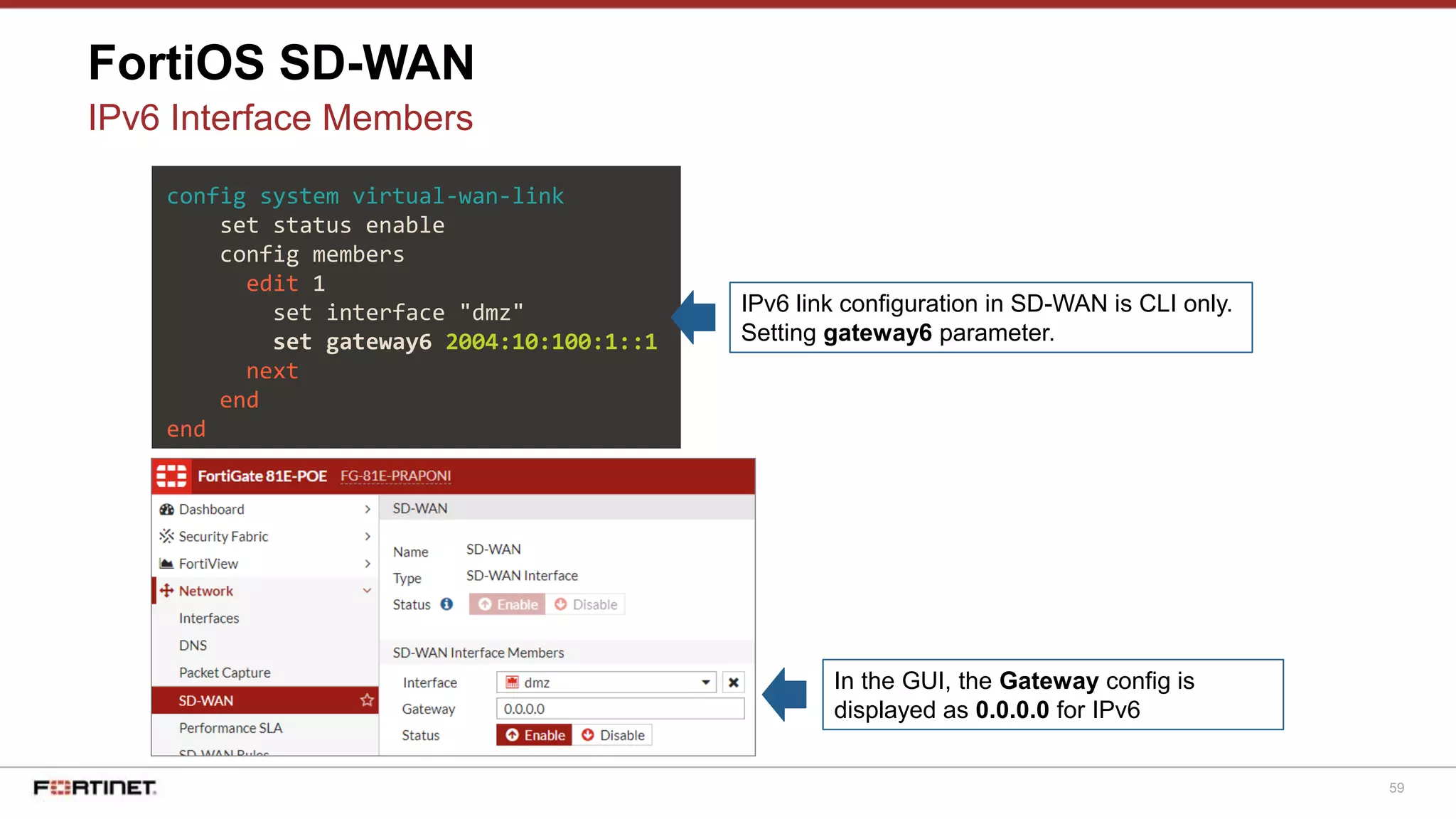
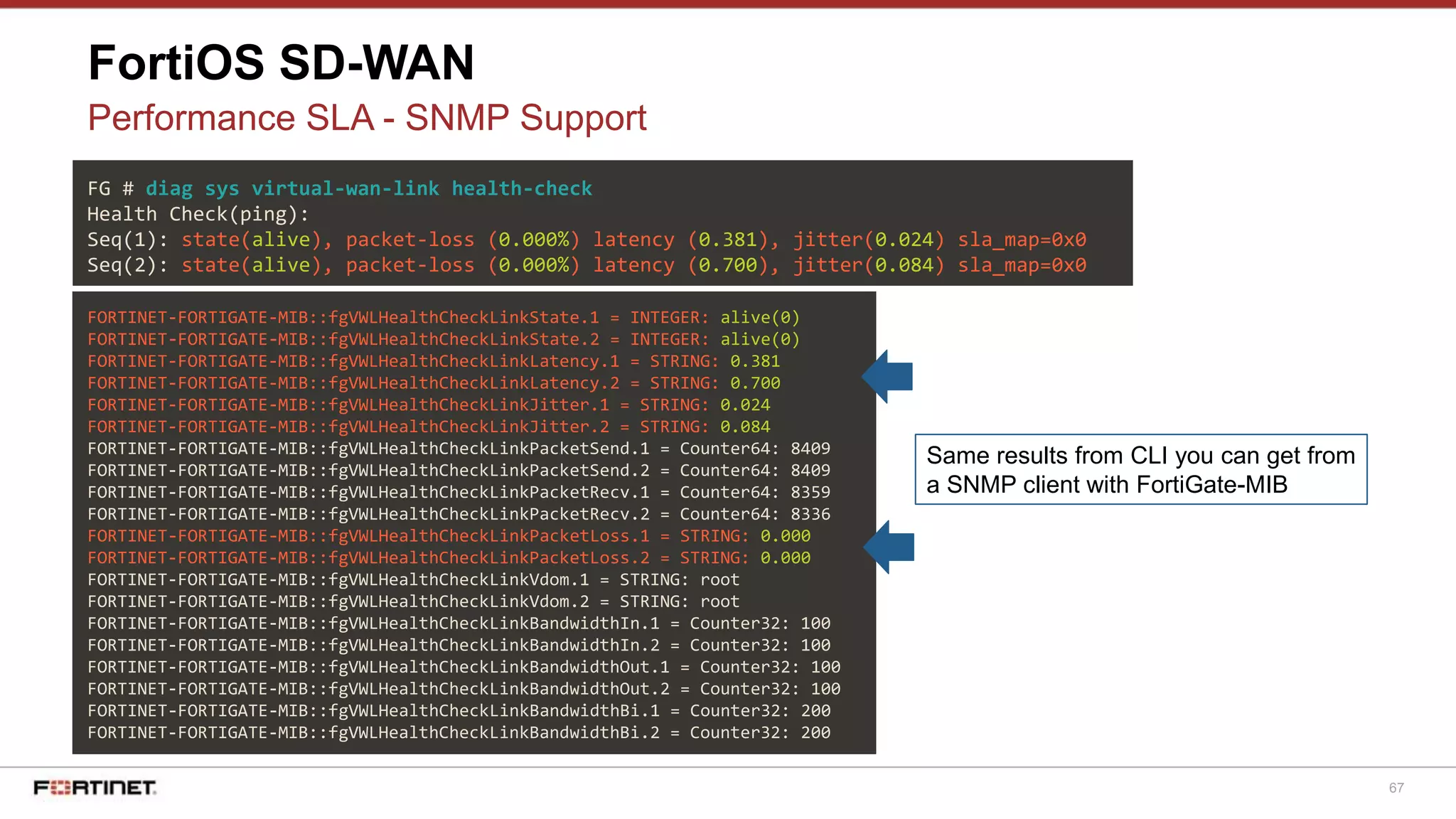
FortiOS SD-WAN
Basic Config - Static Routing
You need to add a route to SD-WAN interface to
install the SD-WAN interface in the routing table.
Load balancing algorithm will not work otherwise.
FG # get router info routing-table all
Routing table for VRF=0
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
S* 0.0.0.0/0 [1/0] via 192.168.0.1, wan1, [0/55]
[1/0] via 200.225.196.247, ppp1, [0/3]
FortiGate automatically add
the Default Gateway
addresses from SD-WAN
interface configuration](https://image.slidesharecdn.com/securesd-wan-191219105029/75/Secure-sd-wan-50-2048.jpg)















































![115
FortiOS SD-WAN
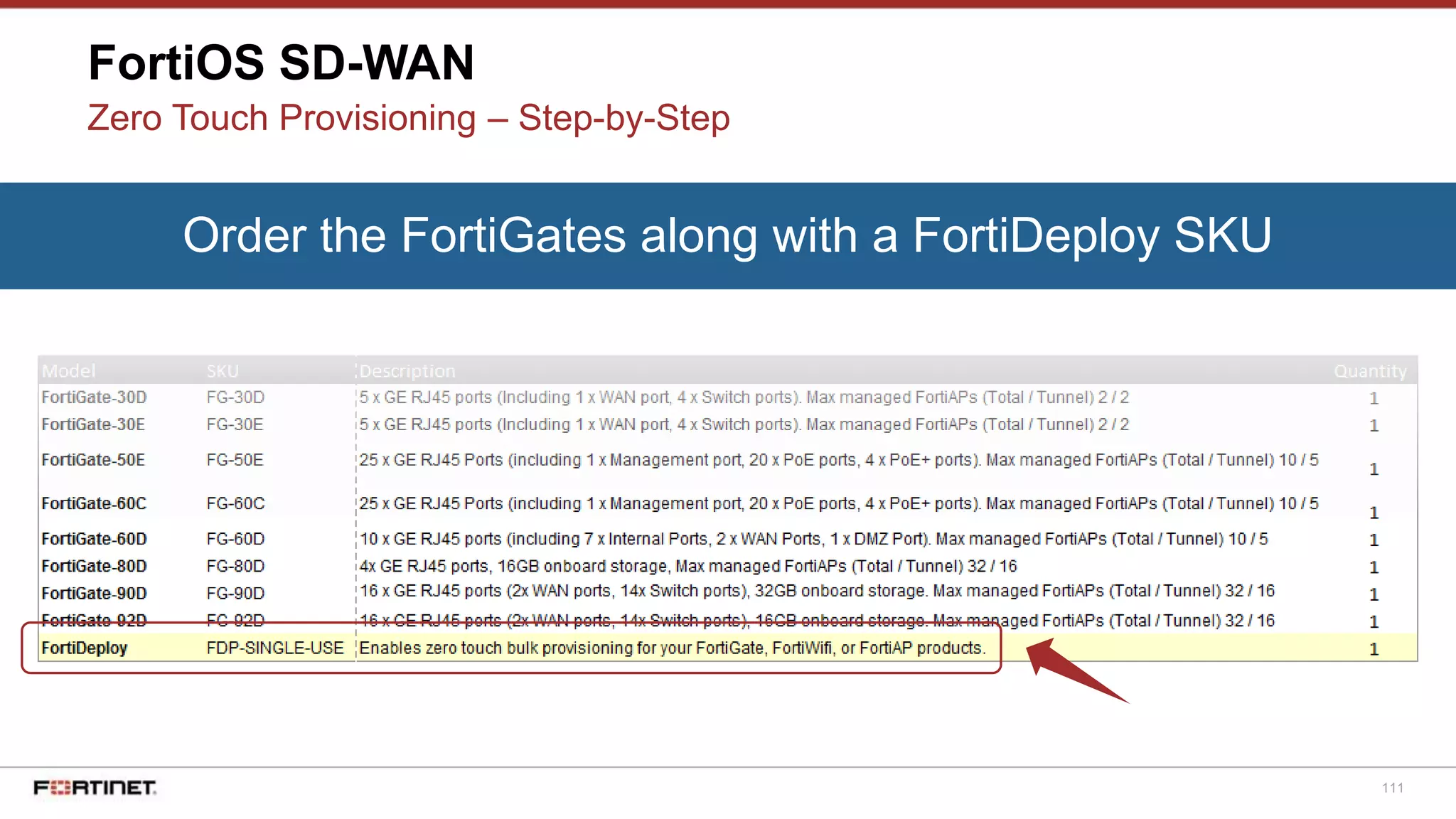
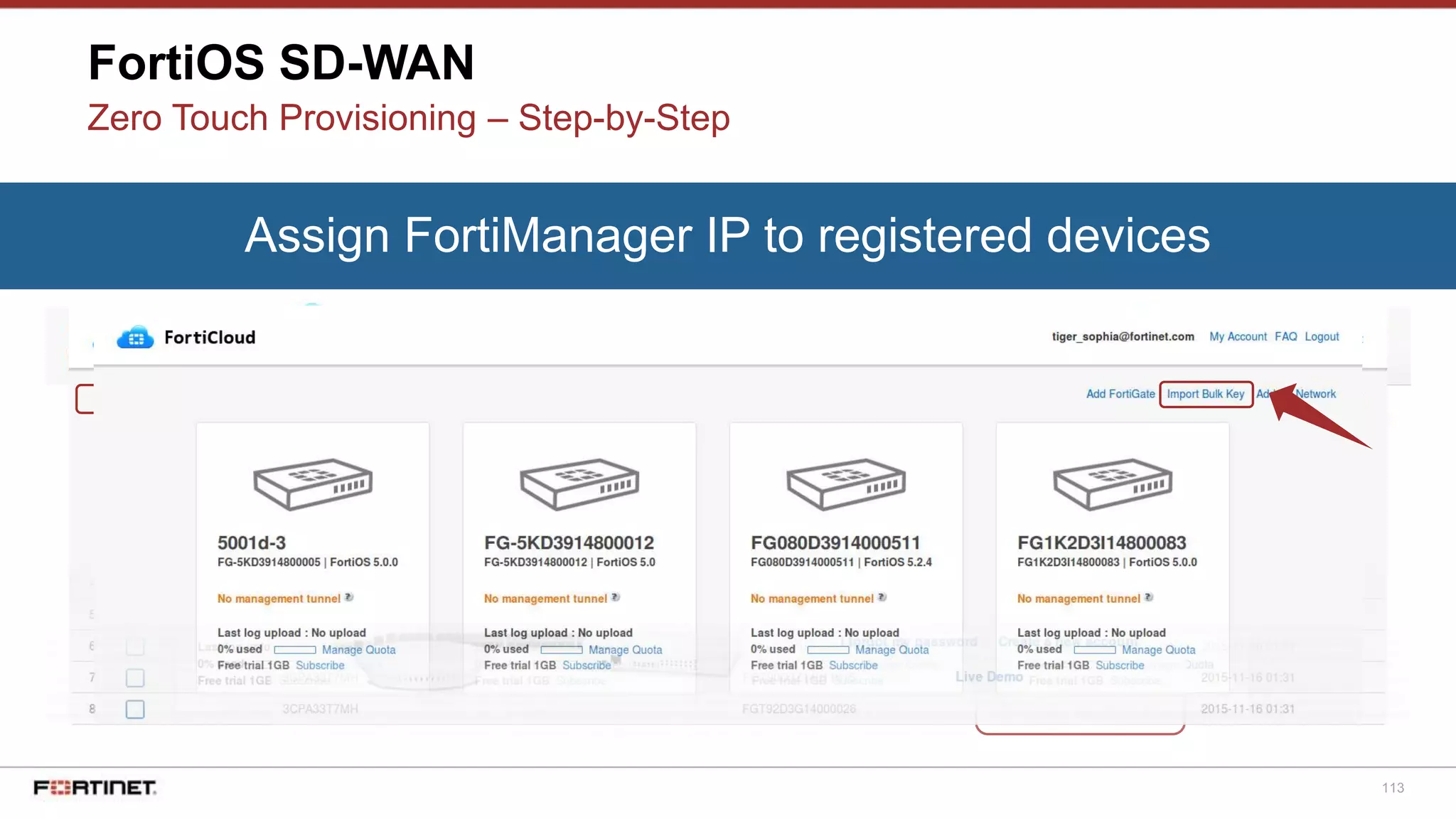
Zero Touch Provisioning – Step-by-Step
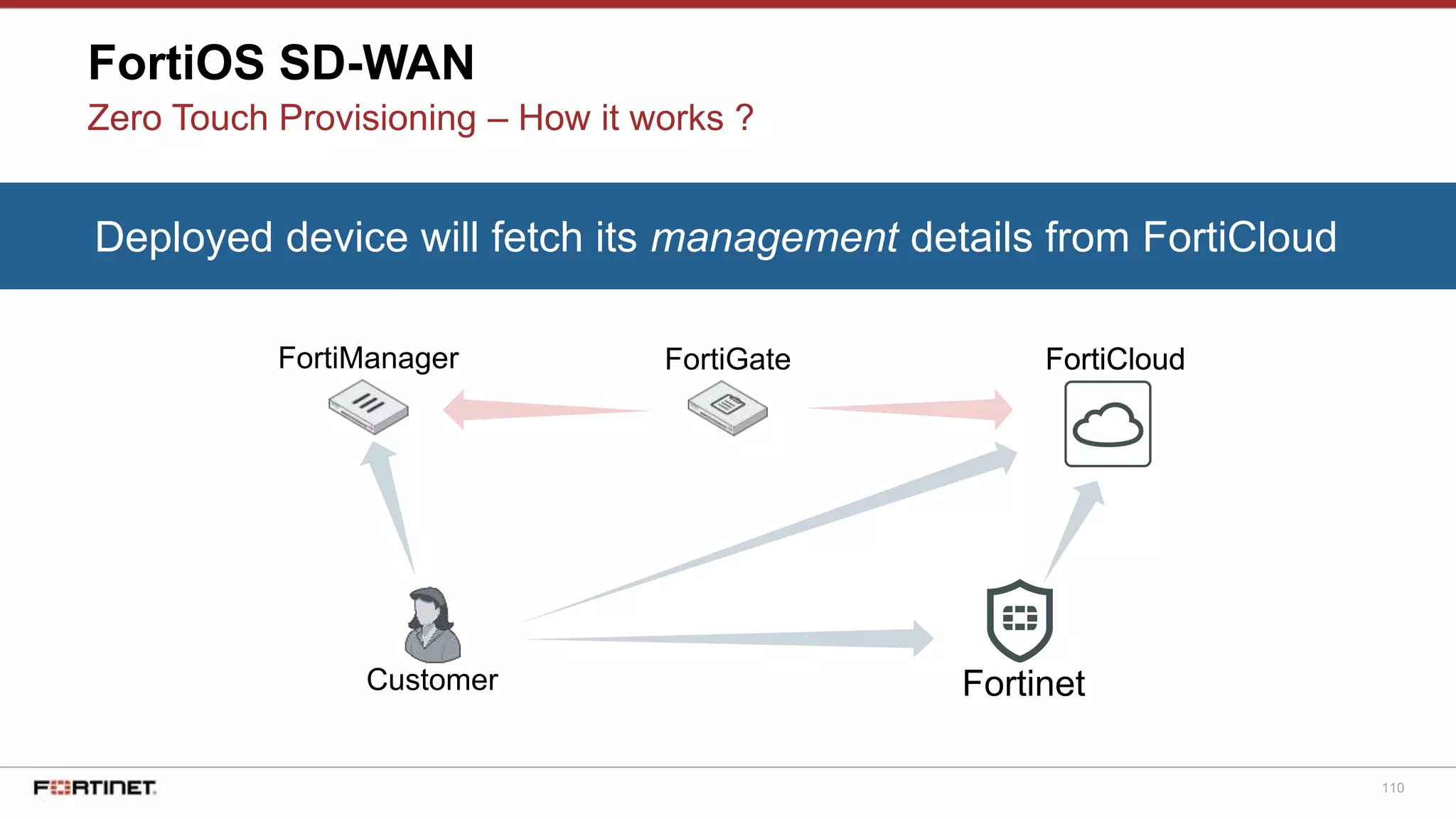
Deployed device will fetch its management details from FortiCloud
0: config system central-management
0: set type fortimanager
0: set fmg 192.168.194.62
0: set mode normal
0: config system fortiguard
0: set service-account-id "tiger_sophia@fortinet.com"
0: end
[...]
FG # diagnose debug cli 8
FG # diagnose debug enable
[...]](https://image.slidesharecdn.com/securesd-wan-191219105029/75/Secure-sd-wan-108-2048.jpg)