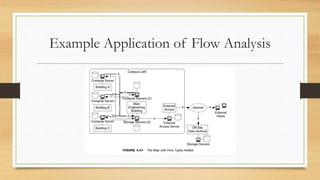
The document discusses network flow analysis for requirements specification. It describes identifying different types of flows based on common attributes like source/destination. Flows are modeled based on patterns like client-server, peer-to-peer etc. An example network is analyzed to identify 4 types of flows between computing and storage devices. Flow maps are created to visualize priority and performance needs of different flows to help with network design and capacity planning.