Embed presentation
Downloaded 86 times




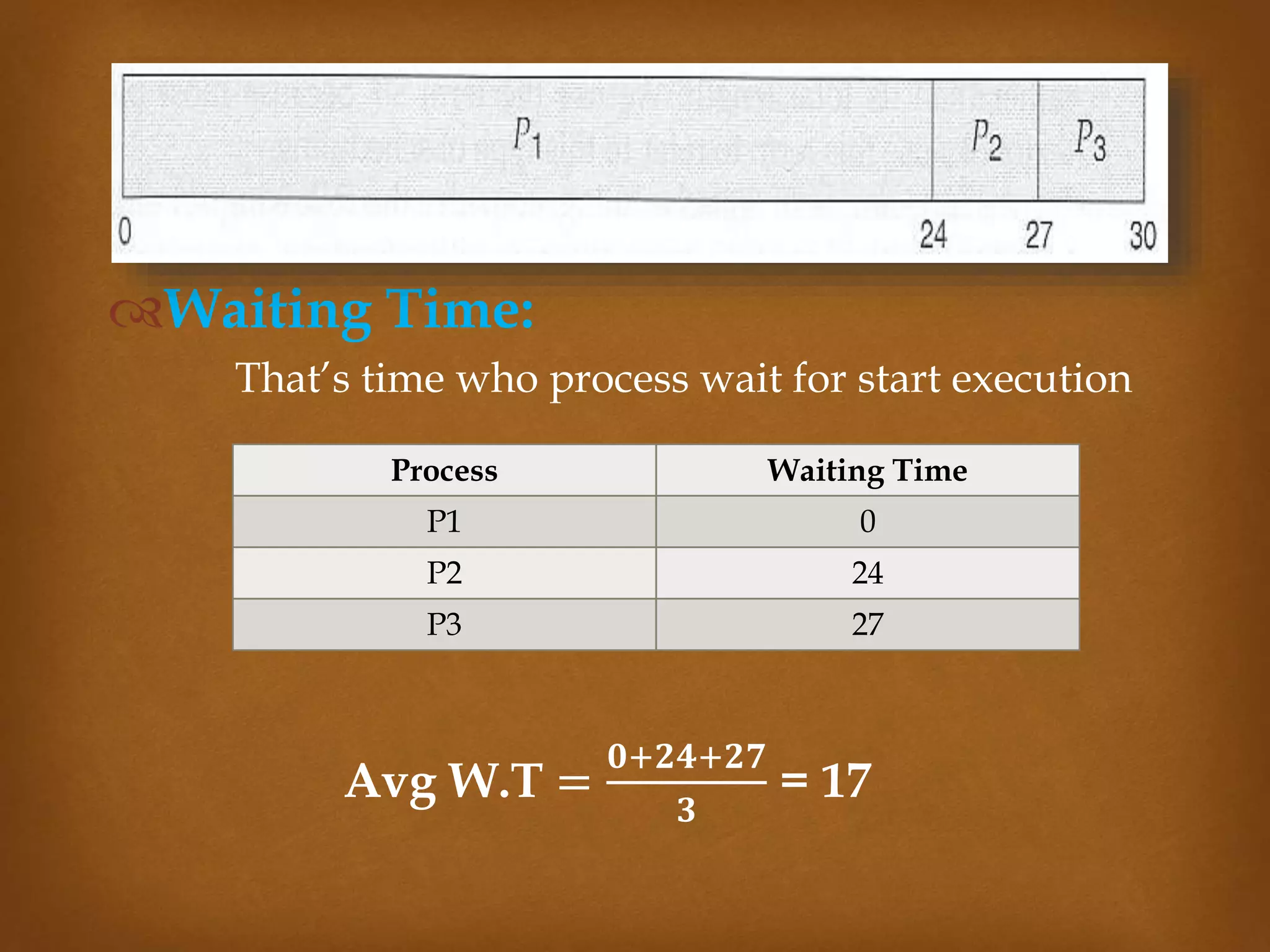

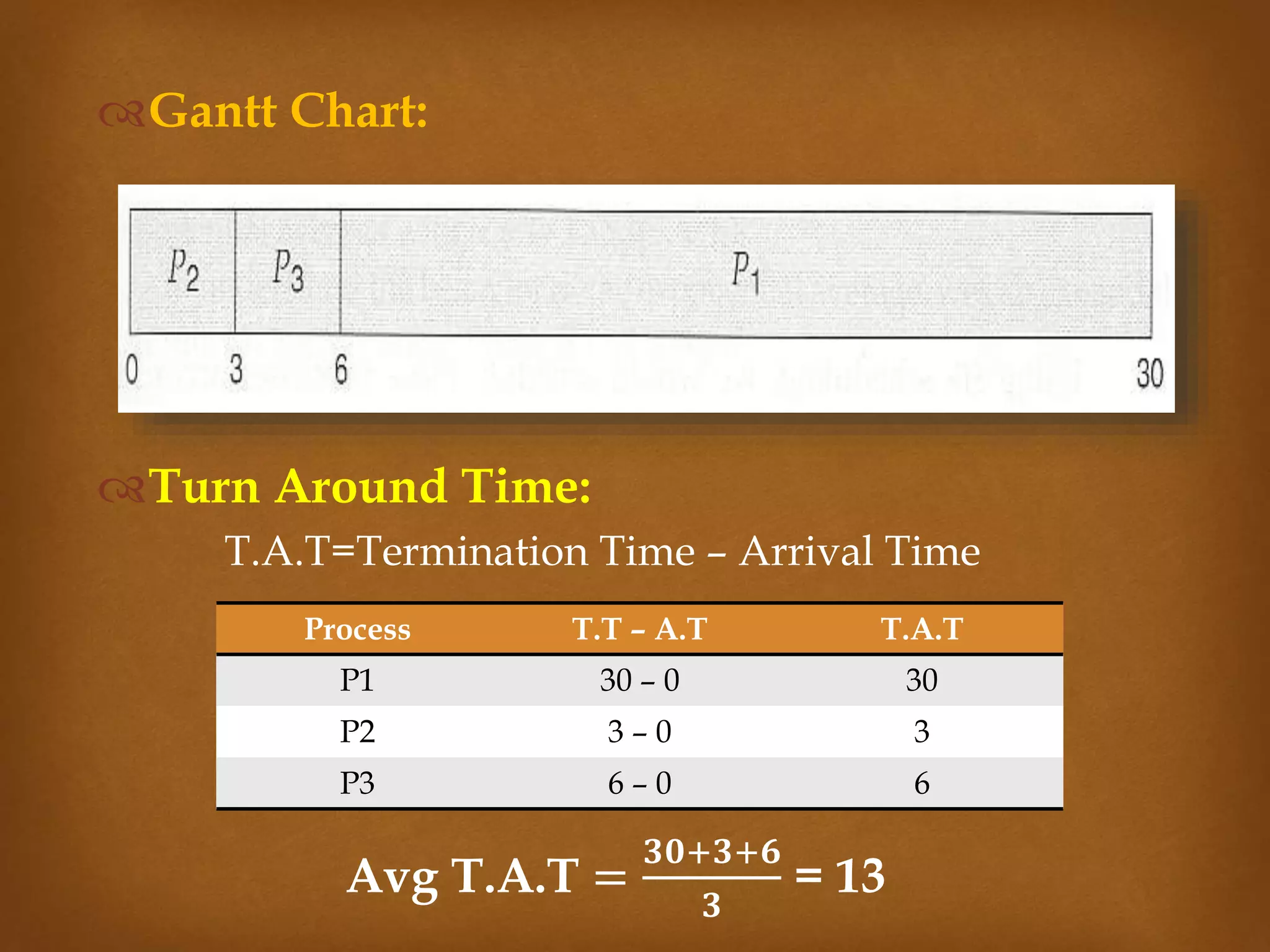
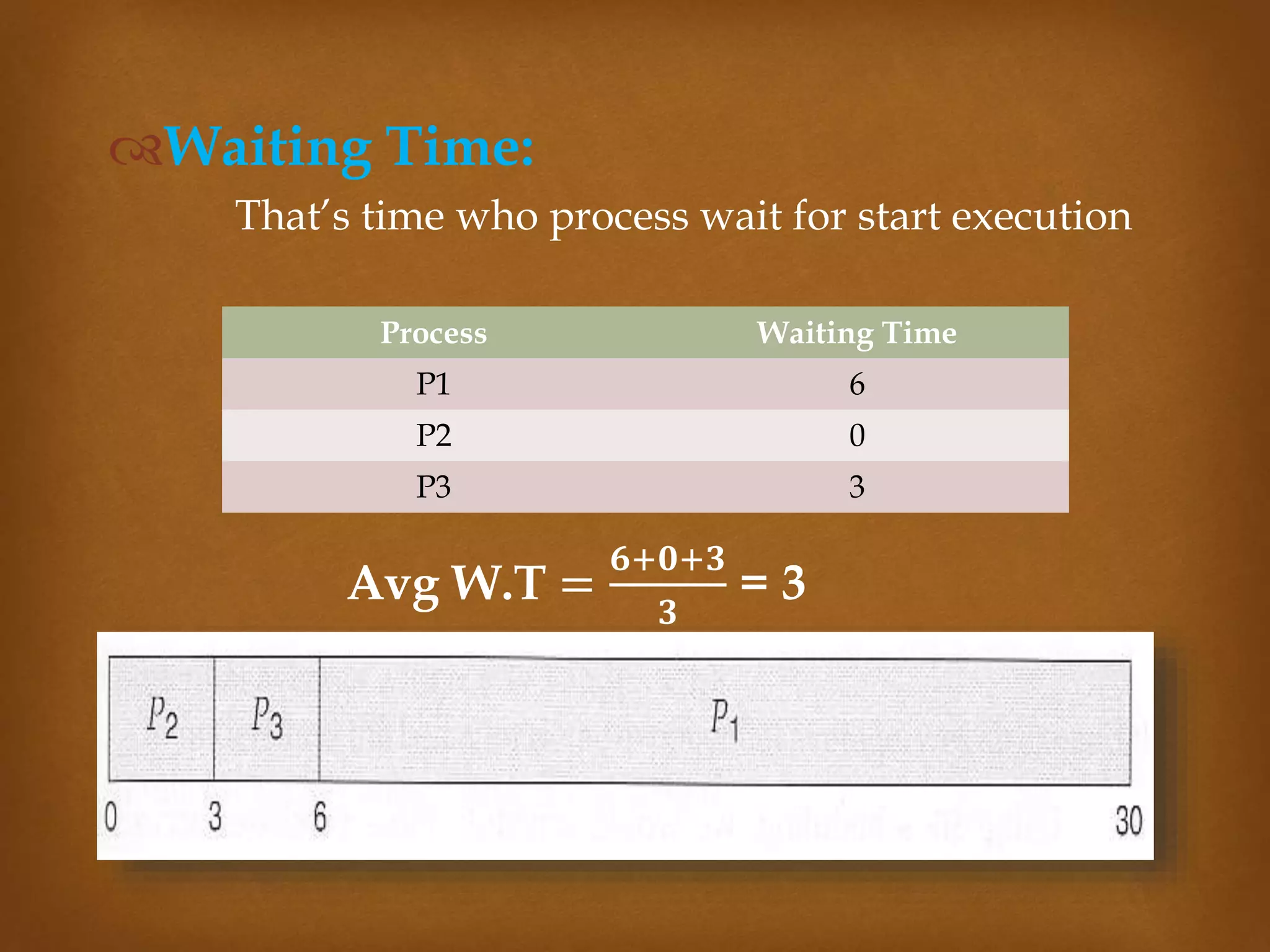

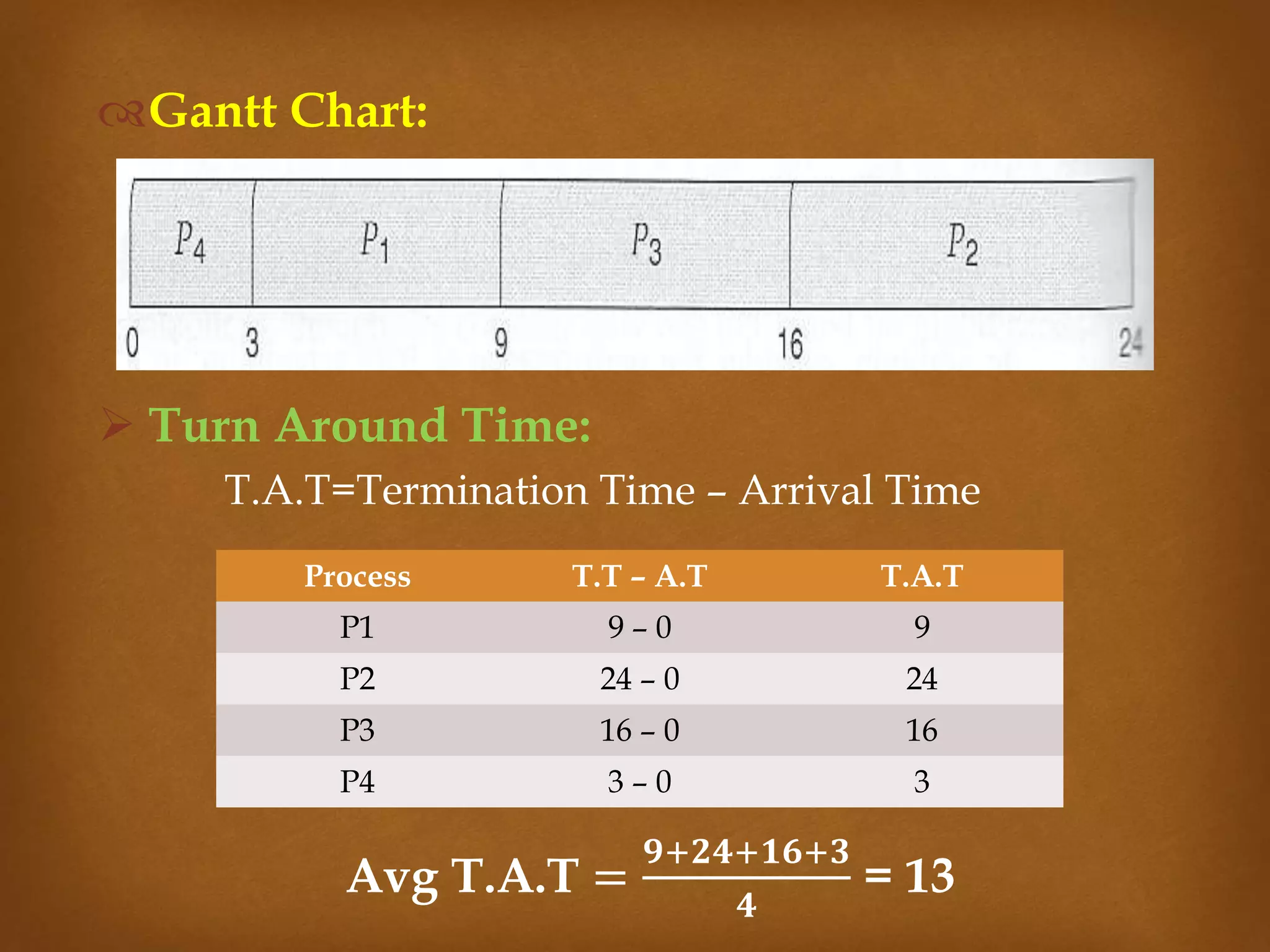
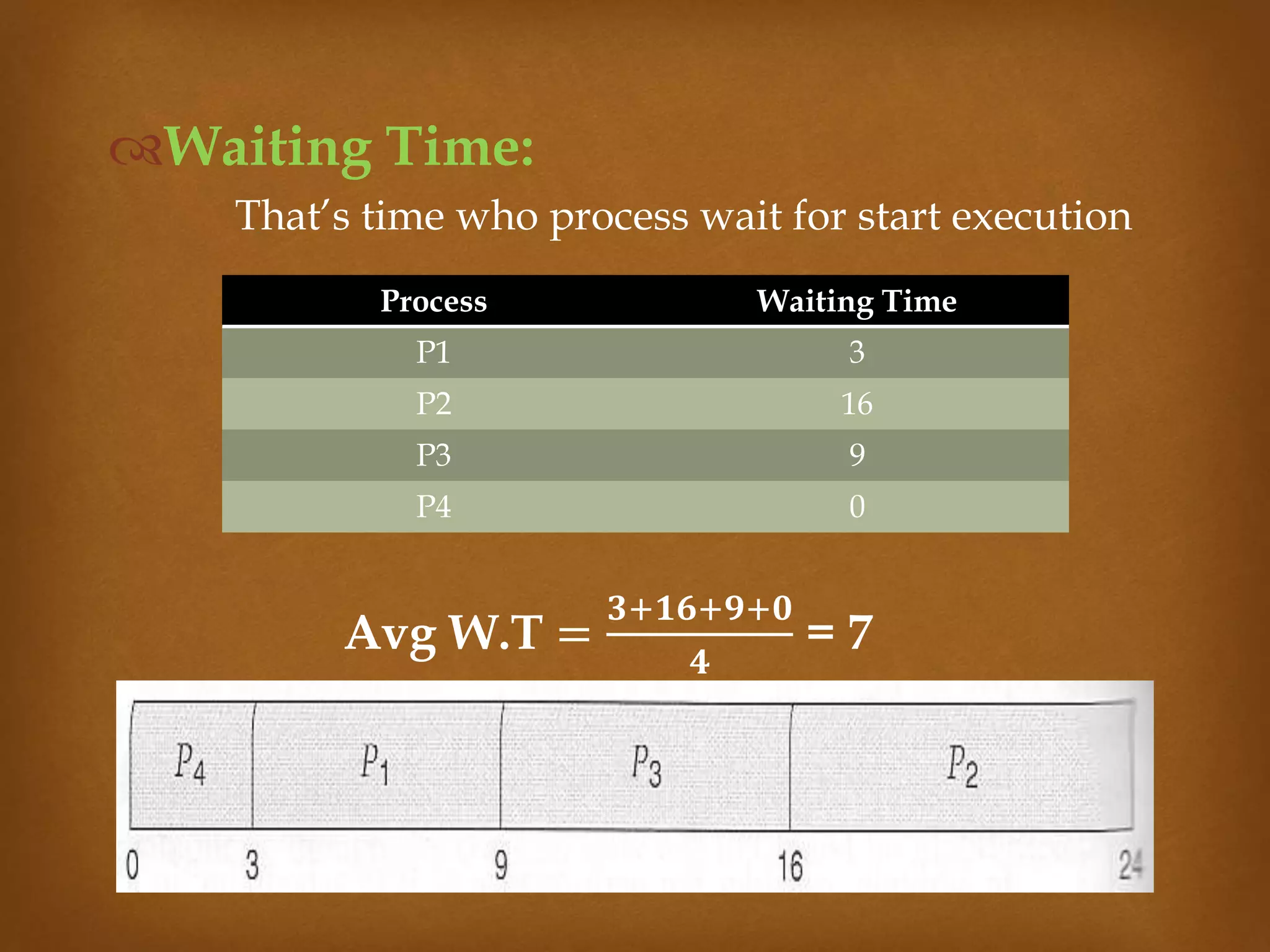


This document compares three CPU scheduling algorithms: first-come, first-served (FCFS); shortest job first (SJF); and preemptive FCFS. It provides examples of each with processes of different burst times and calculates their average turnaround times and waiting times. FCFS has the highest average turnaround time of 27 time units. Preemptive FCFS improves this to 13 time units by allowing short jobs to preempt longer jobs. SJF has the lowest average turnaround and waiting times of 13 and 7 time units respectively by always selecting the shortest job to run next.












