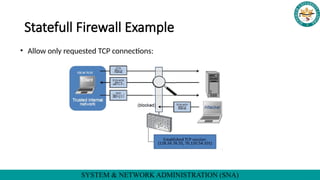
The document discusses firewalls in system and network administration, detailing how they protect networks from internet threats by filtering traffic based on predefined rules. It covers different firewall policies, including blacklist and whitelist approaches, and differentiates between stateless and stateful firewalls. The document also explains how stateful firewalls maintain connection records to manage legitimate sessions while enhancing security.